AWS Security Fundamentals
Overview
About Me

DevOps@RajeshKumar.XYZ
Course Overview
- Overview of AWS Security Capability
- Delegating Access to the Control Panel
- Encrypting and Controlling Access to S3 and Instances
- Logging and Auditing Access and Actions
- Putting It All Together
Amazon Web Services (AWS) Fundamentals for System Administrators
Module Overview
- Introduction to Acme Developers
- AWS security audit check-list
- Compare AWS security capability to traditional enterprise security
- The business drivers for cloud security
Scenario
- Acme Developers
- Migrating existing infrastructure to AWS
- Publically traded company Sarbanes and Oxley (SOX) reporting and auditing
Introduction to Acme Developers
Security Audit Checklist
https://d0.awsstatic.com/whitepapers/compliance/
AWS_Auditing_Security_Checklist.pdf
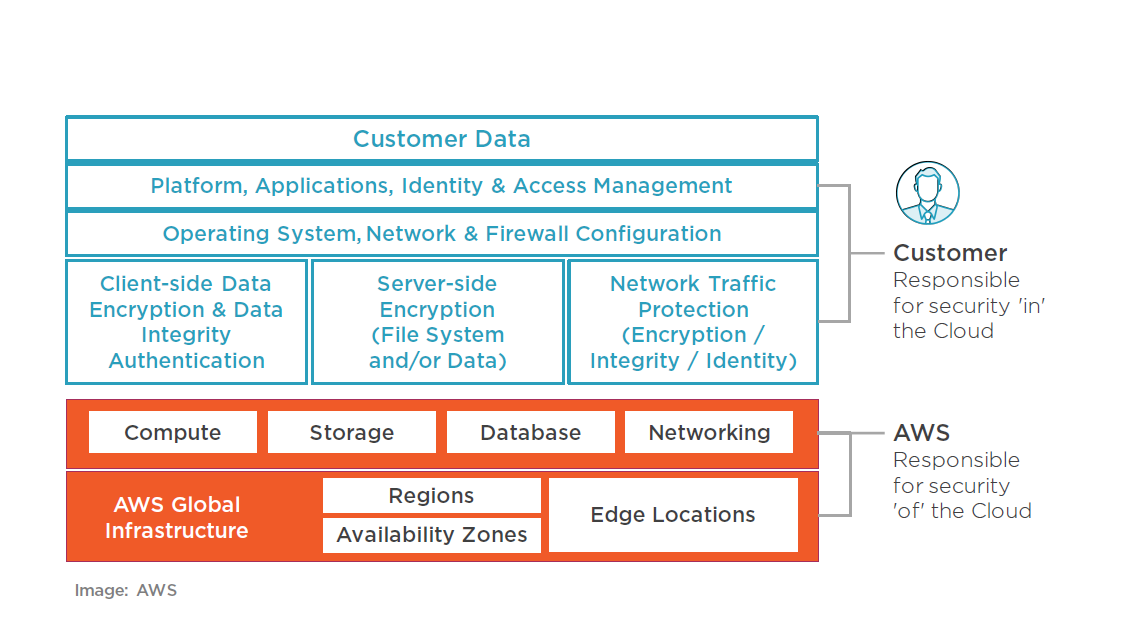
AWS Cloud provides infrastructure compliance
ISO 27001, SOC, PCI Data Security Standard, FedRAMP, and many more
AWS' compliance doesn’t mean YOU are compliant!
Shared Responsibility
Governance
- Who
- What
- When
- Where
Network Configuration
Network isolation via virtual private cloud(VPC)
- Similar to virtualized networks in traditional virtualized environments
- Completely software-defined
Asset Configuration Management
What do you have and how is it managed
- AWS manages the physical infrastructure
- You are respsonsible for configuration and patch management for the VM settings and OS
- AWS control panel & IAM has the tools to support policy
Logical Access Control
Amazon's Identity and Access Management (IAM)
Remote Access
- VPN
- Direct Connect
- Security Groups
Data Encryption
Data at rest
S3 object storage
Data in motion
VPN, HTTPS, SSL
SecurityLogging and Monitoring
AWS manages the physical access
- Bio-locks
- Physical locality
- Access control
The customer is responsible for the VPC
- Configuring & monitoring and
consuming Network & OS logs
- Monitoring IAM logs
Disaster Recovery
AWS has multiple regions and availability zones
- Replication is available
- S3 has several service levels for integrity
The customer is responsible to designing
for availablity and DR
- DR takes some design considerations
- Recovery Point Objective (RPO) &
Recovery Time Objectives (RTO)
Inherited Controls
- Physical Access
- Data center locality
- Employee qualifications and certifications
- Data center availability
Review
Introduction to Acme Developers
AWS security audit check-list
- Shared responsibility
Compare AWS security capability to traditional enterprise security
- AWS provides a foundation to equal or
best on-premises technical security capability
Access Control
Amazon Web Services (AWS) Fundamentals for System Administrators
Module Overview
- Overview of Identity Access Manager (IAM)
- Creating users and groups
- Assigning and testing rights
IAM is free
Comparable to Active Directory
Provides granular access to AWS resources
- Control Panel
- API calls
- Instances
- S3 Objects
- Databases
IAM is extensible
- AD integration
Eventual Consistency
Scenario
Sarah needs to deploy Scenario a new AWS instance
Shared Responsibility

Review
Introduction to IAM
IAM is extensible
Demonstration of IAM configuration
- Creating users & groups
- Access Keys
- Logging in as a user
- Validating user rights
Encrypting & Controlling Access to S3
Module Overview
Understanding S3 encryption options
Controlling access to S3 data
AWS Key Management System (KMS)
- Client Master Key (CMK)
- Encryption Key
Server-side Encryption
- Server-side encryption with AWS Managed Keys (SSE-S3)
- Server-side encyption with KMSManaged Keys (SSE-KMS)
- Server-side encryption with customer provided Keys (SSE-C)
Server-side encryption with Amazon S3 Managed Keys (SSE-S3)
- Simple AWS managed encryption
- Key are auto generated and storage by Amazon
- AES-256 encryption of keys and data
- No additional charge
Server-side encryption with AWS KMSManaged Keys (SSE-KMS)
- Uses customer master keys (CMKs) to encrypt data
- IAM is used for a key management system (KMS)
- Increased auditing capability
- Leveraged when for organizations with strong key management policies
Client-side encryption
- Encryption is performed on the client side
- Client is any consumer of S3 storage including EC2
AWS KMS-managed Customer Master Key
Client-side encryption Master Key
- AWS CAN'T RECOVER YOUR KEYS
Review
Keys!!!
- CMK & encyrption
- Key management
Encrypting data
- Using SSE-S3 & SSE-KMS
Administering KMS & encryption via the control panel are limited
Controlling access using IAM & encryption
Logging and Auditing Access and Actions
Module Overview
- Understanding AWS compliance portfolio
- Logging rights and access with the console
|
|
|
|---|
Shared Responsibility

Scenario:
Acme is considering accepting credit card payments. Larry is tasked with examining AWS controls for auditing access controls for PCI certification.
The point of audits is to verify configuration.
While AWS's infrastructure is PCI certified, what tools are available to Larry to provide to auditors?
- AWS PCI compliance package via NDA
- API rights similator
- AWS CloudTrail
CloudTrail characteristics
- Trails can be created for all or a single region
- Logs are stored on a S3 bucket
- Logs are encrypted via SSE-S3 or KMS
- Latency of approximately 15 mins of API call
Review
- AWS provides a strong compliance foundation
- Shared responsibility
- CloudTrail is powerful auditing
Putting It All Together
Module Overview
- Put it all together
- Review original use case
- Highlight AWS' security capability vs. on premises options
- Review key learnings
Introduction to Acme Developers

Audit Checklist
- Governance
- Network configuration
- Asset configuration management
- Logical access control
- Data encryption
- Security logging and monitoring
- Disaster recovery
- Inherited control
Shared Responsibility

Summary
- AWS security capability
- Delegating access to the Control Panel
- Encrypting and controlling access to S3 and instances
- Logging and auditing access
Questions

