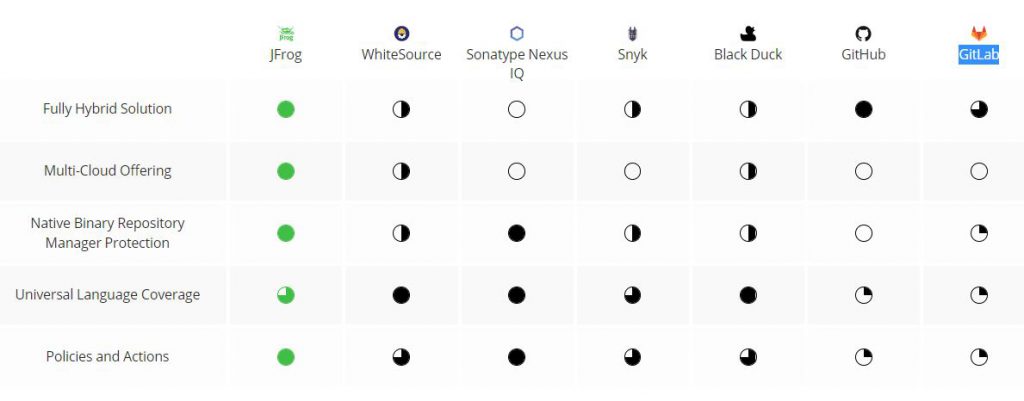
Sonatype Nexus IQ
Nexus IQ Server is a policy engine powered by precise intelligence on open source components. It provides a number of tools to improve component usage in your software supply chain, allowing you to automate your processes and achieve accelerated speed to delivery while also increasing product quality.
Snyk
SNYK is an open source security platform for finding out vulnerabilities in source code of an application. … Just like an antivirus scans your device and finds out the threats ,in the same way it scans your source code and provides vulnerabilities
JFrog XRay
JFrog Xray is a universal software composition analysis (SCA) solution that natively integrates with Artifactory, giving developers and DevSecOps teams an easy way to proactively identify vulnerabilities on open source and license compliance violations, before they manifest in production releases.
JFrog Xray scans your artifacts, builds and Release Bundles for OSS components being used, and detects security vulnerabilities and licenses in your software components. The results of this scan are then displayed across the JFrog Platform.
WhiteSource
WhiteSource automates the entire process of open source component selection, approval and management, including detection and remediation of security and compliance issues. It integrates with all stages of your software development lifecycle (SDLC) to alert in real time and help you fix issues faster and easier.
Black Duck
Black Duck® software composition analysis (SCA) helps teams manage the security, quality, and license compliance risks that come from the use of open source and third-party code in applications and containers.
Black Duck is used to set and enforce open-source policies and integrate open-source management into DevOps environments. Black Duck helps security and development teams identify and mitigate open-source-related risks across application portfolios.
GitHub Security
GitHub Security Report security issues, share security knowledge and grow with the community. Contribute to open source code scanning queries written by GitHub and leading security researchers.
- https://github.com/features/security
GitLab
GitLab can check your application for security vulnerabilities including:
- Unauthorized access.
- Data leaks.
- Denial of service attacks.
Statistics and details on vulnerabilities are included in the merge request. Providing actionable information before changes are merged enables you to be proactive.
GitLab also provides high-level statistics of vulnerabilities across projects and groups:
The Security Dashboard provides a high-level view of vulnerabilities detected in your projects, pipeline, and groups.
The Threat Monitoring page provides runtime security metrics for application environments. With the information provided, you can immediately begin risk analysis and remediation.
- What is Mobile Virtual Network Operator? - April 18, 2024
- What is Solr? - April 17, 2024
- Difference between UBUNTU and UBUNTU PRO - April 17, 2024

