
The Fortify could be a static application security testing (SAST) giving utilized by development teams and security professionals to research the ASCII text file for security vulnerabilities.

It reviews code and helps developers determine, prioritize, and resolve problems with less effort and in less time.
Interview Questions and Answers:-
- What is Fortify and how does it work?
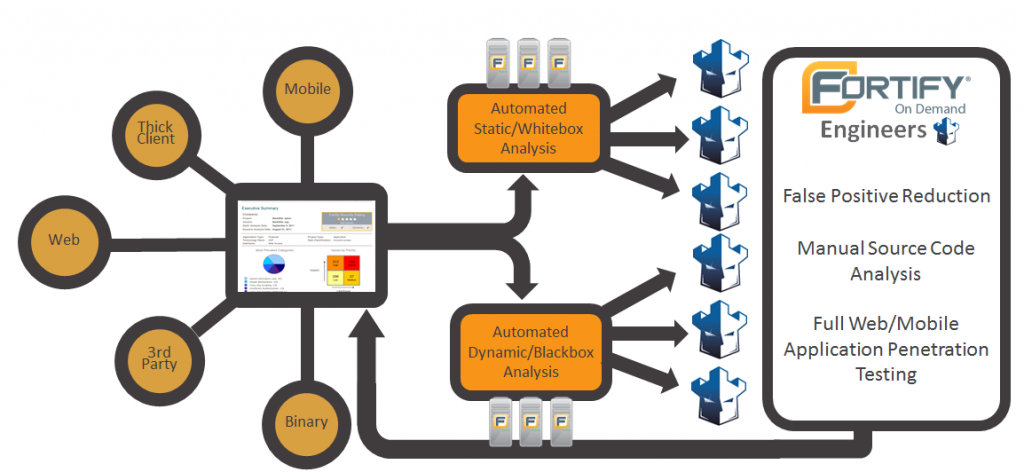
Fortify Software Security Center: An AppSec platform that enables organizations to automate an application security program. It provides management, development, and security teams a way to work together to triage, track, validate, and manage software security activities.
2. What is Fortify used for?
Fortify SCA is a static application security testing (SAST) offering used by development groups and security professionals to analyze the source code for security vulnerabilities. It reviews code and helps developers identify, prioritize, and resolve issues with less effort and in less time.
3. Is Fortify free?
Basic access to Fortify is free for everyone – all the time. The subscription cost for Fortify Premium allows us to maintain and continually improve Fortify.
4. Does Fortify scan XML?
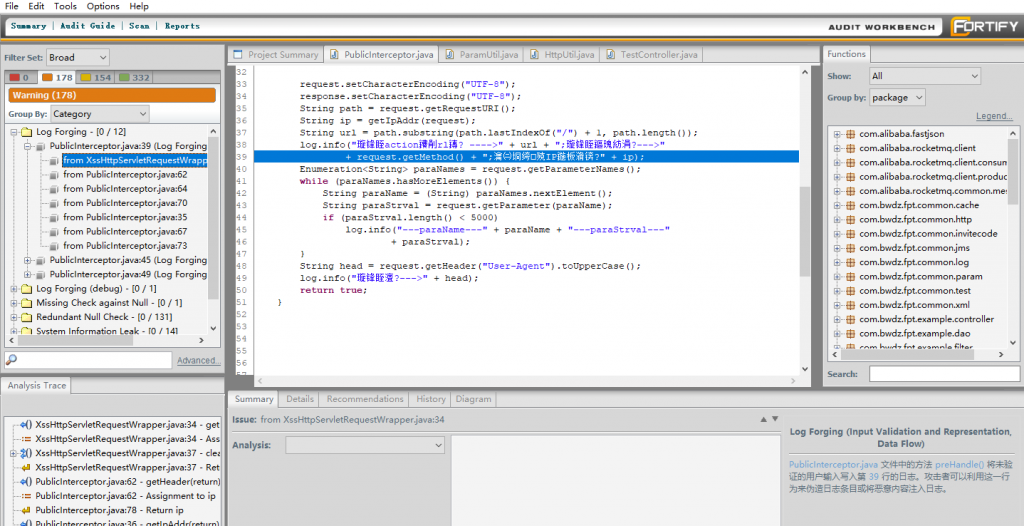
We have been used HP Fortify Scanner to scan our application for vulnerabilities. … xml format and zip it up and attach it to the scanner and do an automated scan.
5. How do I run a fortify scan locally?
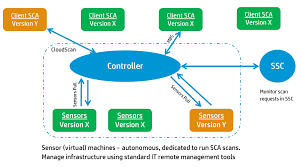
Run a locally installed version of Fortify Static Code analyzer on the currently opened project to create an FPR. Open the FPR in Fortify Audit Workbench to view the results. Run a remote translation and scan using Fortify Scan Central. You can upload the results to Fortify Software Security Center.
6. What is the difference between SonarQube and fortify?
Fortify essentially classifies the code quality issues in terms of its security impact on the solution. While Sonarqube is more of a Static code analysis tool which also gives you like “code smells,” though Sonarqube also lists out the vulnerabilities as part of its analysis.
7. Is fortify SAST or DAST?
About Micro Focus Web Inspect
Micro Focus Fortify Web Inspect is a dynamic application security testing (DAST) tool that identifies application vulnerabilities in deployed web applications and services.
8. What is the difference between Sonarqube and fortify?
Fortify essentially classifies the code quality issues in terms of its security impact on the solution. While SonarQube is more of a Static code analysis tool which also gives you like “code smells,” though SonarQube also lists out the vulnerabilities as part of its analysis.
9. What are the main components of Fortify?
- Fortify
- Fortify. Application Security. Build software resilience for modern development from a partner you can trust. …
- Integration Ecosystem.
- Marketplace.
- Software Composition Analysis.
- Software Security Center.
- Static Code Analyzer.
- WebInspect.
10. What is Fortify on Demand?
HP Fortify on Demand is a Security-as-a-Service (SaaS) testing solution that allows any organization to test the. security of software quickly, accurately, affordably, and without any software to install or manage.
11. What is Fortify in Skyrim?
Fortify is a spell effect of the Restoration school of magicka in The Elder Scrolls V: Skyrim that temporarily increases the value of the one or more target’s statistics. In Skyrim, this effect is available in the form of potions and enchantments.
12. Is Fortify open source?
Summary. Both Fortify and GitLab Ultimate offer open source component scanning along with Static and Dynamic Application Security Testing. … The Fortify RASP product, Application Defender, is limited to Java and. Net applications.
13. Does Fortify scan Cobol?
Fortify SCA already supports a specific (outdated) version of COBOL: IBM Enterprise COBOL for z/OS 3.4. 1 with CICS, IMS, DB2, and IBM MQ. We are in the process of expanding and updating the COBOL coverage.
14. What is fortify in Jenkins?
Fortify on Demand is a Software as a Service (SaaS) solution that enables your organization to build and expand a Software Security Assurance program easily and quickly. The Fortify on Demand Jenkins Plugin enables users to upload code directly from Jenkins for Static Application Security Testing (SAST).
15. What is fortify in software development?
Fortify Software Security Center
It automates key processes of developing and deploying secure applications. It helps you resolve software vulnerabilities integrating vulnerability analysis across the entire software life cycle—from development to QA testing and even deployed applications.
16. Does Fortify scan shell script?
No, Fortify does not support shell scripts. The closest support would be scanning python.
17. How do I create a Fortify report?
From the Audit Workbench, generate your report and under the ‘Results Outline’ panel Open up the Listings section and then uncheck the Limit number of issues in each group setting if checked. Show activity on this post.
18. What languages can fortify scan?
Fortify SCA supports 27+ programming languages including newly added languages such as Kotlin and Go Language. Latest language support includes Java 14, Lombok, MSBuild 16.6, XCode up to 11.7, ECMA Script 2019 and 2020, TypeScript 3.9 and 4.0, Kotlin 1.3.
19. How do I fortify scan in eclipse?
Fortify scanning in Eclipse over maven projects
Install the Maven Fortify plugin.
Added Maven fortify Plugin details in my application pom.
Ran translate and scan commands. It generated fpr files under the projects.
20. How do I fix a fortify scan error?
There are a few options:
You can mark those issues as “No an issue” in your FPR report file, and merge future scan to the baseline audit review. The same issue won’t show up again in the merged file. …
I think you can also add a close session statement in the finally block. This would execute only if an exception occurs.
21. Which Analyzer inspects fair timeout of a user in a specific session in fortify?
Configuration Analyzer inspects the fair timeouts for the user in the specific session of web applications.
22. What is Security Testing?
Security testing can be considered as the most important in all types of software testing. Its main objective is to find vulnerabilities in any software (web or networking) based application and protect their data from possible attacks or intruders.
As many applications contain confidential data and need to be protected from being leaked. Software testing needs to be done periodically on such applications to identify threats and to take immediate action on them.
23. What is “Vulnerability”?
Vulnerability can be defined as the weakness of any system through which intruders or bugs can attack the system.
If security testing has not been performed rigorously on the system then chances of vulnerabilities get increased. Time to time patches or fixes is required to prevent a system from the vulnerabilities.
24. What is Intrusion Detection?
Intrusion detection is a system which helps in determining possible attacks and deal with it. Intrusion detection includes collecting information from many systems and sources, analysis of the information and finding the possible ways of the attack on the system.
Intrusion detection checks the following:
Possible attacks
Any abnormal activity
Auditing the system data
Analysis of different collected data, etc.
25. What is “SQL Injection”?
SQL Injection is one of the common attacking techniques used by hackers to get critical data.
Hackers check for any loophole in the system through which they can pass SQL queries, bypass the security checks, and return back the critical data. This is known as SQL injection. It can allow hackers to steal critical data or even crash a system.
SQL injections are very critical and need to be avoided. Periodic security testing can prevent this kind of attack. SQL database security needs to be defined correctly and input boxes and special characters should be handled properly.
26. List the attributes of Security Testing?
There are following seven attributes of Security Testing:
- Authentication
- Authorization
- Confidentiality
- Availability
- Integrity
- Non-repudiation
- Resilience
27 What is XSS or Cross-Site Scripting?
XSS or cross-site scripting is a type of vulnerability that hackers used to attack web applications.
It allows hackers to inject HTML or JAVASCRIPT code into a web page that can steal the confidential information from the cookies and returns to the hackers. It is one of the most critical and common techniques which needs to be prevented.
28. What are the SSL connections and an SSL session?
SSL or Secured Socket Layer connection is a transient peer-to-peer communications link where each connection is associated with one SSL Session.
SSL session can be defined as an association between client and server generally created by the handshake protocol. There are a set of parameters defined and it may be shared by multiple SSL connections.
29. What is “Penetration Testing”?
Penetration testing is on security testing which helps in identifying vulnerabilities in a system. A penetration test is an attempt to evaluate the security of a system by manual or automated techniques and if any vulnerability found, testers use that vulnerability to get deeper access to the system and find more vulnerabilities.
The main purpose of this testing is to prevent a system from any possible attacks. Penetration testing can be done in two ways –White Box testing and Black box testing.
In white-box testing, all the information is available with the testers whereas in black box testing, testers don’t have any information and they test the system in real-world scenarios to find out the vulnerabilities.
30. Why “Penetration Testing” is important?
Penetration testing is important because-
- Security breaches and loopholes in the systems can be very costly as the threat of attack is always possible and hackers can steal important data or even crash the system.
- It is impossible to protect all the information all the time. Hackers always come with new techniques to steal important data and it is necessary for testers as well to perform periodical testing to detect the possible attacks.
- Penetration testing identifies and protects a system by the above-mentioned attacks and helps organizations to keep their data safe.
31. Name the two common techniques used to protect a password file?
Two common techniques to protect a password file is- hashed passwords and a salt value or password file access control.
List the full names of abbreviations related to Software security?
Abbreviations related to software security include:
- IPsec – Internet Protocol Security is a suite of protocols for securing Internet
- OSI – Open Systems Interconnection
- ISDN Integrated Services Digital Network
- GOSIP- Government Open Systems Interconnection Profile
- FTP – File Transfer Protocol
- DBA – Dynamic Bandwidth Allocation
- DDS – Digital Data System
- DES – Data -Encryption Standard
- CHAP – Challenge Handshake Authentication Protocol
- BONDING – Bandwidth On Demand Interoperability Group
- SSH – The Secure Shell
- COPS Common Open Policy Service
- ISAKMP – Internet Security Association and Key Management Protocol
- USM – User-based Security Model
- TLS – The Transport Layer Security
32. What is ISO 17799?
ISO/IEC 17799 is originally published in the UK and defines best practices for Information Security Management. It has guidelines for all organizations small or big for Information security.
33. List down some factors that can cause vulnerabilities?
Factors causing vulnerabilities are:
- Design flaws: If there are loopholes in the system that can allow hackers to attack the system easily.
- Passwords: If passwords are known to hackers they can get the information very easily. Password policy should be followed rigorously to minimize the risk of password steal.
- Complexity: Complex software can open doors on vulnerabilities.
- Human Error: Human error is a significant source of security vulnerabilities.
- Management: Poor management of the data can lead to the vulnerabilities in the system.
34. List the various methodologies in Security testing?
Methodologies in Security testing are:
- White Box- All the information are provided to the testers.
- Black Box- No information is provided to the testers and they can test the system in a real-world scenario.
- Grey Box- Partial information is with the testers and rest they have to test on their own.
35. List down the seven main types of security testing as per Open Source Security Testing methodology manual?
The seven main types of security testing as per the Open Source Security Testing methodology manual are:
- Vulnerability Scanning: Automated software scans a system against known vulnerabilities.
- Security Scanning: Manual or automated technique to identify network and system weaknesses.
- Penetration testing: Penetration testing is on the security testing which helps in identifying vulnerabilities in a system.
- Risk Assessment: It involves the analysis of possible risks in the system. Risks are classified as Low, Medium and High.
- Security Auditing: Complete inspection of systems and applications to detect vulnerabilities.
- Ethical hacking: Hacking is done on a system to detect flaws in it rather than personal benefits.
- Posture Assessment: This combines Security Scanning, Ethical Hacking and Risk Assessments to show an overall security posture of an organization.
36. What is SOAP and WSDL?
SOAP or Simple Object Access Protocol is an XML-based protocol through which applications exchange information over HTTP. XML requests are sent by web services in SOAP format then a SOAP client sends a SOAP message to the server. The server responds back again with a SOAP message along with the requested service.
Web Services Description Language (WSDL) is an XML formatted language used by UDDI. “Web Services Description Language describes Web services and how to access them”.
37. List the parameters that define an SSL session connection?
The parameters that define an SSL session connection are:
- Server and client random
- Server write MACsecret
- Client write MACsecret
- Server write key
- Client write key
- Initialization vectors
- Sequence numbers
38. What is file enumeration?
This kind of attack uses forceful browsing with the URL manipulation attack. Hackers can manipulate the parameters in URL string and can get the critical data which generally does not open for the public such as achieved data, old version or data which is under development.
39. List the benefits that can be provided by an intrusion detection system?
There are three benefits of an intrusion detection system.
- NIDS or Network Intrusion Detection
- NNIDS or Network Node Intrusion Detection System
- HIDS or Host Intrusion Detection System
40. What is HIDS?
HIDS or Host Intrusion Detection system is a system in which a snapshot of the existing system is taken and compared with the previous snapshot. It checks if critical files were modified or deleted then an alert is generated and sent to the administrator.
41. List down the principal categories of SET participants?
Following are the participants:
- Cardholder
- Merchant
- Issuer
- Acquirer
- Payment gateway
- Certification authority
42. Explain “URL manipulation”?
URL manipulation is a type of attack in which hackers manipulate the website URL to get the critical information. The information is passed in the parameters in the query string via HTTP GET method between client and server. Hackers can alter the information between these parameters and get the authentication on the servers and steal the critical data.
In order to avoid this kind of attack security testing of URL manipulation should be done. Testers themselves can try to manipulate the URL and check for possible attacks and if found they can prevent these kinds of attacks.
43. What are the three classes of intruders?
The three classes of intruders are:
- Masquerader: It can be defined as an individual who is not authorized on the computer but hacks the system’s access control and get access of authenticated user’s accounts.
- Misfeasor: In this case, user is authenticated to use the system resources but he misuses his access to the system.
- Clandestine user, It can be defined as an individual who hacks the control system of the system and bypasses the system security system.
44. List the component used in SSL?
Secure Sockets Layer protocol or SSL is used to make secure connections between clients and computers.
Below are the component used in SSL:
- SSL Recorded protocol
- Handshake protocol
- Change Cipher Spec
- Encryption algorithms
45. What is port scanning?
Ports are the point where information goes in and out of any system. Scanning of the ports to find out any loopholes in the system is known as Port Scanning. There can be some weak points in the system to which hackers can attack and get the critical information. These points should be identified and prevented from any misuse.
Following are the types of port scans:
- Strobe: Scanning of known services.
- UDP: Scanning of open UDP ports
- Vanilla: In this scanning, the scanner attempts to connect to all 65,535 ports.
- Sweep: The scanner connects to the same port on more than one machine.
- Fragmented packets: The scanner sends packet fragments that get through simple packet filters in a firewall
- Stealth scan: The scanner blocks the scanned computer from recording the port scan activities.
- FTP bounce: The scanner goes through an FTP server in order to disguise the source of the scan.
46. What is a Cookie?
A cookie is a piece of information received from a web server and stored in a web browser which can be read anytime later. A cookie can contain password information, What are the types of Cookies?
Types of Cookies are:
- Session Cookies – These cookies are temporary and last in that session only.
- Persistent cookies – These cookies stored on the hard disk drive and last till its expiry or manual removal of it.
47. What is a honeypot?
Honeypot is a fake computer system that behaves like a real system and attracts hackers to attack it. Honeypot is used to find out loopholes in the system and to provide a solution for these kinds of attacks.
48. List the parameters that define an SSL session state?
The parameters that define an SSL session state are:
- Session identifier
- Peer certificate
- Compression method
- Cipher spec
- Master secret
- Is resumable
49. Describe the Network Intrusion Detection system?
Network Intrusion Detection system generally is known as NIDS. It is used for the analysis of the passing traffic on the entire subnet and to match with the known attacks. If any loophole identified then the administrator receives an alert.
50. How to diff Fortify SCA scans?
We have Fortify SCA and we are setting up regular, automated scans of our source code. Our intention is to have an alert if there is an introduced security issue. Is there a way, perhaps using FPRUtility (or some other method) to accomplish this? Ultimately I prefer something that can be easily run from the command line, but if this can also be accomplished using the GUI then I would appreciate knowing how to do that as well.
Referral Video Source:-
- Mastering Qualitative Research: The Role of Focus Groups in Data Collection - July 11, 2024
- What is robots ops? - July 10, 2024
- 5 Effective Online Learning Strategies for DevOps Professionals - July 4, 2024


How can we integrate Fortify with azure CI CD pipelines with yaml.