
1. What is Skipfish?
Skipfish is a web application security scanner.
2. What is the purpose of Skipfish?
The purpose of Skipfish is to identify vulnerabilities in web applications.
3. How does Skipfish work?
Skipfish works by sending requests to a web application and analyzing the responses for vulnerabilities.
4. What are some common vulnerabilities that Skipfish can detect?
Some common vulnerabilities that Skipfish can detect include SQL injection, cross-site scripting (XSS), and file inclusion vulnerabilities.
5. How can you use Skipfish to improve web application security?

You can use Skipfish to identify vulnerabilities in your web application and then take steps to fix them.
6. What are some best practices for using Skipfish?
Some best practices for using Skipfish include running it on a test environment, using it in conjunction with other security tools, and regularly updating it.
7. What is the difference between a vulnerability and an exploit?
A vulnerability is a weakness in a system that can be exploited by an attacker. An exploit is a tool or technique used to take advantage of a vulnerability.
8. What is a SQL injection vulnerability?
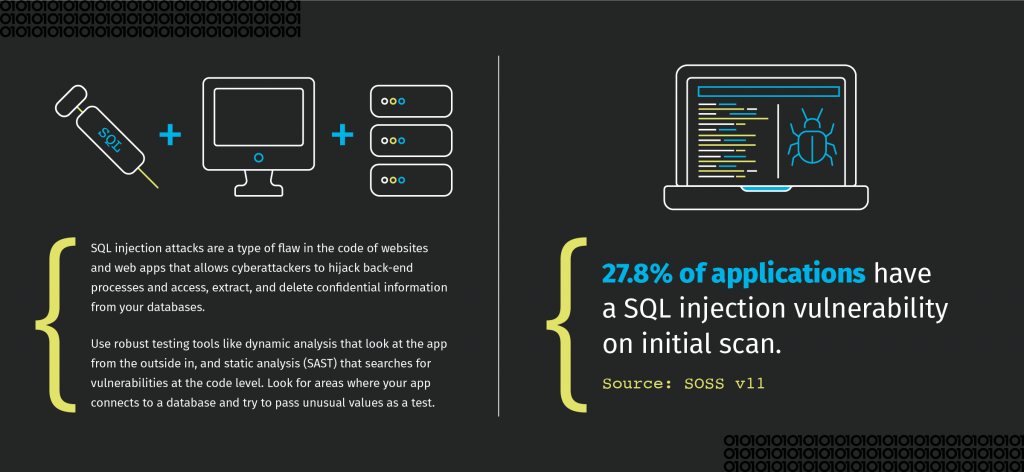
A SQL injection vulnerability is a type of vulnerability that allows an attacker to execute SQL commands on a web application’s database.
9. What is cross-site scripting (XSS)?
Cross-site scripting (XSS) is a type of vulnerability that allows an attacker to inject malicious code into a web application.
10. What is a file inclusion vulnerability?
A file inclusion vulnerability is a type of vulnerability that allows an attacker to include files from a remote server on a web application.
11. What is a buffer overflow vulnerability?
A buffer overflow vulnerability is a type of vulnerability that allows an attacker to overwrite memory in a program and execute arbitrary code.
12. What is a denial of service (DoS) attack?
A denial of service (DoS) attack is an attack that attempts to make a web application unavailable to its users.
13. What is a distributed denial of service (DDoS) attack?
A distributed denial of service (DDoS) attack is a type of DoS attack that uses multiple computers to overwhelm a web application.
14. What is a man-in-the-middle (MitM) attack?
A man-in-the-middle (MitM) attack is an attack that intercepts communication between two parties.
15. What is a phishing attack?
A phishing attack is an attack that attempts to trick a user into giving away sensitive information, such as passwords or credit card numbers.
16. What is a social engineering attack?
A social engineering attack is an attack that uses psychological manipulation to trick a user into giving away sensitive information.
17. What is a brute force attack?
A brute force attack is an attack that attempts to guess a password by trying every possible combination.
18. What is a rainbow table?
A rainbow table is a precomputed table of hashes that can be used to quickly crack passwords.
19. What is encryption?
Encryption is the process of converting data into a form that cannot be read without a key.
20. What is decryption?
Decryption is the process of converting encrypted data back into its original form.
21. What is a hash function?
A hash function is a function that takes input data and produces a fixed-size output, called a hash.
22. What is a salt?
A salt is a random value that is added to a password before it is hashed, to make it more difficult to crack.
23. What is a certificate authority (CA)?
A certificate authority (CA) is an organization that issues digital certificates, which are used to verify the identity of a website.
24. What is a digital certificate?
A digital certificate is a file that contains information about the identity of a website and the public key used for encryption.
25. What is SSL?
SSL (Secure Sockets Layer) is a protocol for encrypting data sent over the internet.
26. What is TLS?
TLS (Transport Layer Security) is a successor to SSL, used for encrypting data sent over the internet.
27. What is a firewall?
A firewall is a network security system that monitors and controls incoming and outgoing network traffic.
28. What is an intrusion detection system (IDS)?
An intrusion detection system (IDS) is a system that monitors network traffic for signs of unauthorized access or malicious activity.
29. What is an intrusion prevention system (IPS)?
An intrusion prevention system (IPS) is a system that monitors network traffic and takes action to prevent unauthorized access or malicious activity.
30. What is a honeypot?
A honeypot is a decoy system designed to attract attackers and gather information about their methods.
31. What is a vulnerability scanner?
A vulnerability scanner is a tool that scans a network or web application for vulnerabilities.
32. What is a penetration test?
A penetration test is a simulated attack on a network or web application, designed to identify vulnerabilities and test the effectiveness of security measures.
33. What is a security audit?
A security audit is a review of an organization’s security policies and procedures, designed to identify weaknesses and recommend improvements.
34. What is a risk assessment?
A risk assessment is an evaluation of the potential risks to an organization’s assets, such as data or infrastructure.
35. What is a security policy?
A security policy is a set of rules and guidelines that govern the use and protection of an organization’s assets.
36. What is a security incident?
A security incident is an event that violates an organization’s security policies or compromises its assets.
37. What is a security breach?
A security breach is an incident in which an attacker gains unauthorized access to an organization’s assets.
38. What is a security incident response plan?
A security incident response plan is a set of procedures for responding to security incidents, designed to minimize damage and restore normal operations.
39. What is a disaster recovery plan?
A disaster recovery plan is a set of procedures for recovering from a catastrophic event, such as a natural disaster or cyber attack.
40. What is a business continuity plan?
A business continuity plan is a set of procedures for maintaining essential business operations in the event of a disruption.
41. What is a security awareness program?
A security awareness program is a program designed to educate employees about security risks and best practices.
42. What is two-factor authentication?
Two-factor authentication is a security measure that requires users to provide two forms of identification, such as a password and a fingerprint.
43. What is multi-factor authentication?
Multi-factor authentication is a security measure that requires users to provide multiple forms of identification, such as a password, a fingerprint, and a security token.
44. What is a security token?
A security token is a physical device that generates a one-time password for use in two-factor authentication.
45. What is a password manager?
A password manager is a tool that stores and manages passwords for multiple accounts.
46. What is a virtual private network (VPN)?
A virtual private network (VPN) is a network that uses encryption to secure communication over the internet.
47. What is a proxy server?
A proxy server is a server that acts as an intermediary between a client and a server, often used for security or performance reasons.
48. What is a sandbox?
A sandbox is a virtual environment used for testing software or executing untrusted code.
49. What is a rootkit?
A rootkit is a type of malware that is designed to hide its presence on a system and give an attacker privileged access.
50. What is a backdoor?
A backdoor is a hidden method of accessing a system, often used by attackers to maintain access after a successful compromise.
Related video:
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

