Are you looking to improve your security operations (SecOps)? One way to do so is by measuring your performance using SecOps metrics. But what exactly are these metrics, and how can they help you? In this article, we’ll dive deep into the world of SecOps metrics, exploring what they are, why they matter, and how you can use them to enhance your security operations.
What Are SecOps Metrics?
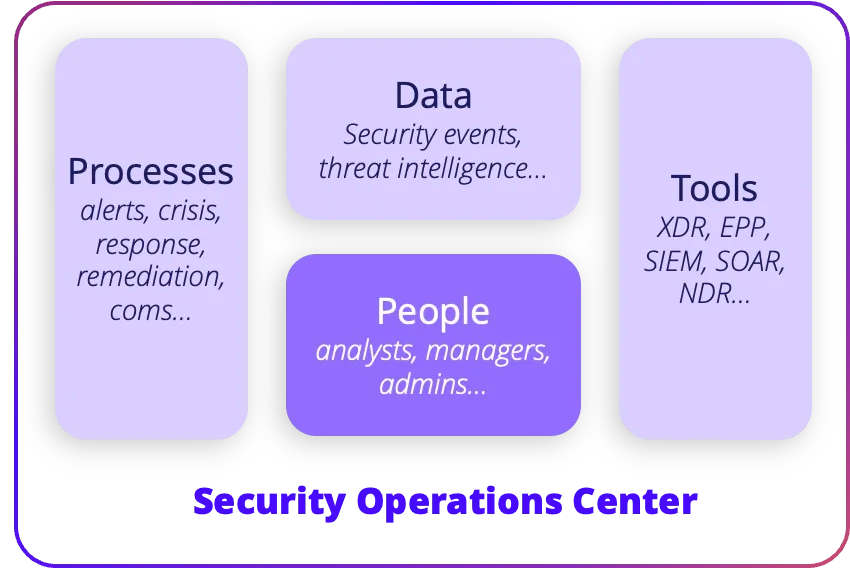
SecOps metrics are quantitative measurements that are used to evaluate the effectiveness of security operations. These metrics provide insights into various aspects of security operations, such as incident response, vulnerability management, and threat detection. By tracking these metrics over time, security teams can identify areas of improvement and make data-driven decisions to enhance their security posture.
Why Are SecOps Metrics Important?
SecOps metrics are essential because they help security teams to:
- Identify weaknesses and areas for improvement in their security operations
- Measure the effectiveness of their security controls and policies
- Monitor the progress of security initiatives over time
- Justify security investments to management
- Demonstrate compliance with regulatory requirements
Without SecOps metrics, security teams would be operating blindly, with no way to measure the effectiveness of their efforts. By tracking these metrics, security teams can identify trends and patterns, which can help them to proactively address potential threats and vulnerabilities.
Types of SecOps Metrics
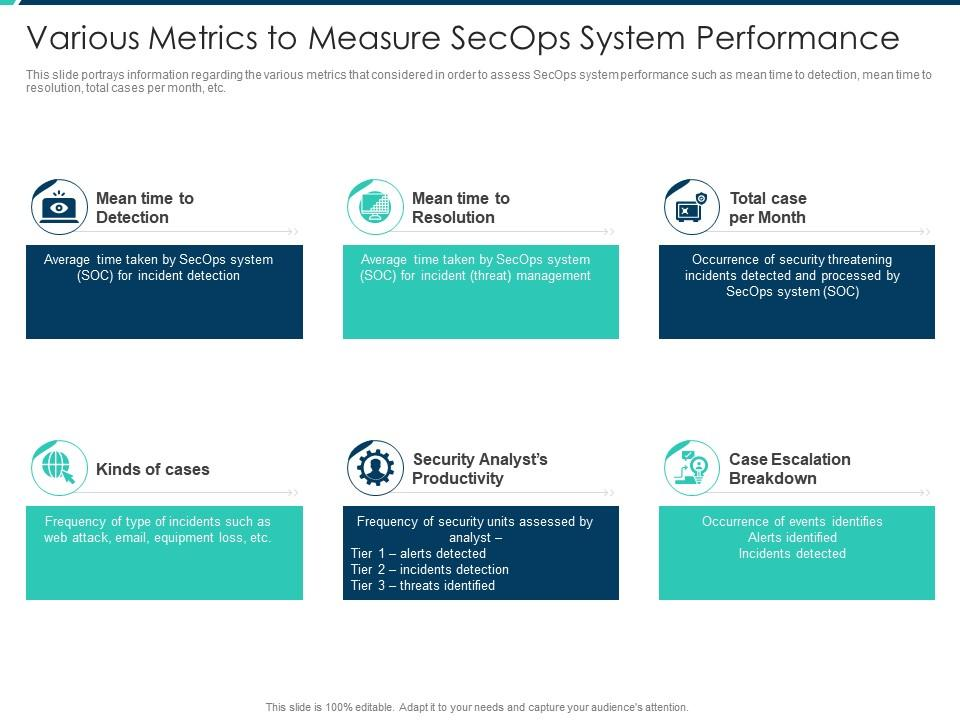
There are numerous SecOps metrics that security teams can track, depending on their specific goals and objectives. Some of the most common SecOps metrics include:
Incident Response Metrics
- Mean time to detect (MTTD): This metric measures the time it takes to detect a security incident from the moment it occurs.
- Mean time to resolve (MTTR): This metric measures the time it takes to resolve a security incident from the moment it is detected.
- False positives: This metric measures the number of incidents that are incorrectly identified as security incidents.
Vulnerability Management Metrics
- Vulnerability severity: This metric measures the severity of vulnerabilities identified in the environment.
- Vulnerability age: This metric measures the amount of time vulnerabilities have been present in the environment.
- Patching compliance: This metric measures the percentage of systems that have been patched within a specific timeframe.
Threat Detection Metrics
- Detection rate: This metric measures the percentage of threats detected by security controls.
- False negatives: This metric measures the number of threats that go undetected by security controls.
- Threat intelligence: This metric measures the effectiveness of threat intelligence in identifying and mitigating threats.
How to Use SecOps Metrics
To use SecOps metrics effectively, security teams should:
- Define clear goals and objectives for their security operations
- Identify the SecOps metrics that align with their goals and objectives
- Establish baseline measurements for each metric
- Track metrics over time
- Analyze metrics to identify areas of improvement
- Use metrics to make data-driven decisions about security operations
By following these steps, security teams can use SecOps metrics to continuously improve their security operations.
Conclusion
SecOps metrics are critical for measuring the effectiveness of security operations. By tracking incident response, vulnerability management, and threat detection metrics, security teams can identify areas of improvement and make data-driven decisions to enhance their security posture. To use SecOps metrics effectively, security teams should define clear goals and objectives, identify relevant metrics, establish baseline measurements, track metrics over time, and use metrics to make data-driven decisions. By doing so, security teams can continuously improve their security operations and protect their organizations from cyber threats.
- Building a DevOps Culture: Tips and Strategies - April 4, 2024
- Why Understanding DevOps Could Be Your Key To Success In The Music Industry - April 4, 2024
- Top Picks: The Best Laptops for Graphic Designers in 2024 - March 31, 2024

