What is Anchore?

Anchore is a container security and compliance platform that helps organizations discover, analyze, and enforce security and compliance policies for containerized applications and images. It ensures that container images are free from vulnerabilities and meet security and compliance standards before they are deployed.
Anchore is a valuable tool for organizations adopting containerization and microservices architectures. It ensures that container images are secure and compliant, reducing the risk of security breaches and compliance violations in containerized environments.
Top 10 use cases of Anchore:
Here are the top 10 use cases of Anchore:
- Container Image Scanning: Anchore scans container images for known vulnerabilities, malware, and configuration issues, providing a detailed analysis of the security posture of the images.
- Vulnerability Management: It helps organizations prioritize and remediate vulnerabilities in container images by providing severity ratings and recommendations for mitigation.
- Compliance Assessment: Anchore assesses container images for compliance with security standards and best practices, such as CIS Docker Benchmark and NIST 800-190.
- Integration with CI/CD Pipelines: Organizations can integrate Anchore into their continuous integration and continuous deployment (CI/CD) pipelines to automate security and compliance checks at build time.
- Policy Enforcement: Anchore allows organizations to define custom security and compliance policies and enforce them across container images, ensuring that only images meeting specified criteria are deployed.
- Image Trust and Assurance: It provides trust and assurance for container images by verifying their content, origins, and signatures, helping ensure that only trusted images are deployed.
- Container Registry Scanning: Anchore can scan container images stored in container registries, such as Docker Hub or Amazon ECR, to ensure that only secure and compliant images are used.
- Real-time Monitoring: Organizations can set up real-time monitoring and alerts for container image vulnerabilities and compliance violations, allowing for rapid response to issues.
- Container Runtime Protection: Anchore can integrate with container orchestration platforms like Kubernetes to provide runtime protection and validation of container images in production environments.
- Custom Policy Creation: Users can create custom security and compliance policies tailored to their organization’s specific requirements and industry standards.
- DevSecOps Integration: Anchore supports the DevSecOps approach by enabling security and compliance checks throughout the development lifecycle, promoting a culture of security within development teams.
- API and CLI Access: Anchore provides APIs and command-line interfaces (CLIs) for automation and integration with other security and monitoring tools.
- Image Lifecycle Management: It helps organizations manage the entire lifecycle of container images, from creation and scanning to deployment and retirement.
- Historical Analysis: Anchore maintains a historical record of container image scans and assessments, enabling organizations to track changes in image security and compliance over time.
What are the feature of Anchore?
Anchore is a container security and compliance platform that helps organizations ensure the security and compliance of containerized applications and images. It provides a range of features to scan, analyze, and enforce security policies for container images. Here are the key features of Anchore, along with an overview of how it works and its architecture:
Key Features of Anchore:
- Container Image Scanning: Anchore scans container images to identify known vulnerabilities, malware, and configuration issues.
- Vulnerability Assessment: It provides a detailed analysis of vulnerabilities found in container images, including severity ratings, affected packages, and recommended fixes.
- Compliance Checks: Anchore checks container images for compliance with security standards and best practices, including CIS Docker Benchmark and NIST 800-190.
- Policy-Based Scanning: Organizations can define custom security and compliance policies and enforce them during image scanning.
- Integration with CI/CD Pipelines: Anchore can be integrated into continuous integration and continuous deployment (CI/CD) pipelines to automate security checks during image builds.
- Custom Policies and Whitelists: Users can create custom security policies and whitelists to tailor image scanning and compliance checks to their specific requirements.
- Container Registry Scanning: It can scan container images stored in container registries, ensuring that only secure and compliant images are used in deployments.
- Real-time Monitoring: Anchore supports real-time monitoring and alerts for vulnerabilities and compliance violations in container images.
- Image Trust and Assurance: It verifies the trustworthiness of container images by checking their content, origins, and digital signatures.
- Container Runtime Integration: Anchore can integrate with container orchestration platforms like Kubernetes to provide runtime protection and validation of container images in production environments.
- Historical Analysis: Anchore maintains a historical record of image scans, allowing organizations to track changes in image security and compliance over time.
How Anchore works and Architecture?
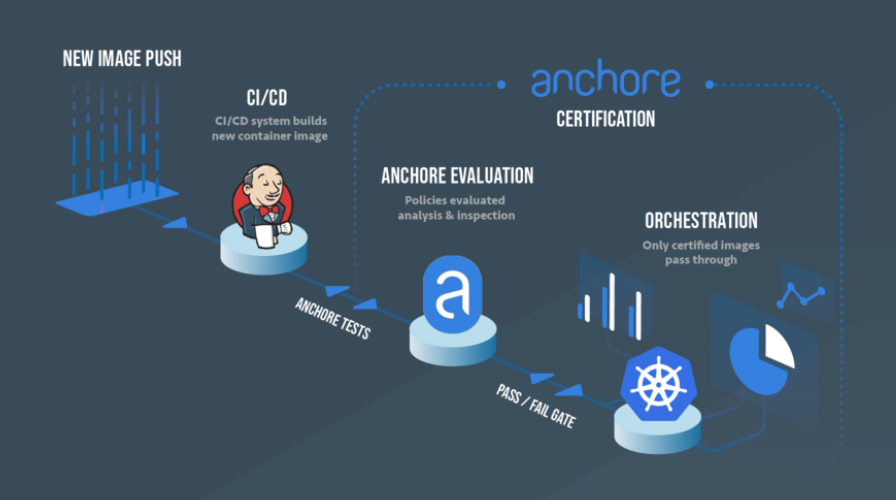
- Image Ingestion: Anchore ingests container images from various sources, such as container registries or CI/CD pipelines.
- Scanning and Analysis: The platform scans and analyzes the image for vulnerabilities, malware, and compliance issues based on predefined policies and checks.
- Vulnerability and Compliance Assessment: Anchore provides a report detailing the vulnerabilities and compliance status of the image, including severity ratings and recommended actions.
- Policy Enforcement: Organizations can enforce security and compliance policies during the scanning process to ensure images meet specified criteria.
- Alerting and Notifications: Anchore supports real-time monitoring and alerts for vulnerabilities and compliance violations, enabling organizations to take immediate action.
- Custom Policy Creation: Users can create custom security and compliance policies tailored to their organization’s needs and requirements.
Anchore’s architecture is designed to provide scalable and automated container image scanning and security assessment:
- Anchore Engine: This is the core component responsible for image scanning, analysis, and policy enforcement. It can be deployed as a standalone service or integrated into container registries, CI/CD pipelines, or container orchestration platforms.
- Policy Engine: The policy engine allows organizations to define custom security and compliance policies that align with their specific requirements.
- Scanning and Analysis: Anchore Engine performs scanning and analysis of container images, identifying vulnerabilities, malware, and compliance issues.
- Database: Anchore stores image metadata, vulnerabilities, compliance checks, and policy information in a database for historical analysis and reporting.
- API and CLI: Anchore provides APIs and command-line interfaces (CLIs) for automation, integration, and interaction with the platform.
- Integrations: Anchore can integrate with various tools and platforms, including container registries, CI/CD pipelines, container orchestration platforms, and security information and event management (SIEM) systems.
Anchore’s architecture is designed to provide comprehensive container image security and compliance capabilities, allowing organizations to secure their containerized applications throughout the development and deployment lifecycle. It helps organizations reduce security risks and ensure compliance in containerized environments.
How to Install Anchore?
To install Anchore, you need to meet the following requirements:
- Docker Engine >= 19.03.13
- Docker Compose >= 1.25.0
- Python 3.7+
Once you have met the requirements, you can install Anchore using the following steps:
- Clone the Anchore repository:
git clone https://github.com/anchore/anchore-engine.git- Change to the Anchore directory:
cd anchore-engine- Build the Anchore image:
docker-compose build anchore- Run the Anchore container:
docker-compose up -d anchoreAnchore will be running on port 8080. You can access Anchore at the following URL:
http://localhost:8080/anchoreYou can also install Anchore using the following command:
pip install anchoreThis will install the Anchore CLI. You can use the Anchore CLI to interact with the Anchore Engine.
Once you have installed Anchore, you can start using it to scan your images for vulnerabilities. To scan an image, run the following command:
anchore-cli scan <image-name>Anchore will scan the image for vulnerabilities and display a report of the findings.
Some additional tips for using Anchore:
- You can use Anchore to scan images from Docker Hub, Amazon ECR, or your own registry.
- You can configure Anchore to scan images automatically when they are pushed to your registry.
- You can integrate Anchore with your CI/CD pipeline to scan images as part of your build and deployment process.
Basic Tutorials of Anchore: Getting Started

The following are the steps of basic tutorial of Anchore:
1. Install Anchore:
Follow the instructions in my previous response to install Anchore.
2. Scan an image:
To scan an image, run the following command:
anchore-cli scan <image-name>
For example, to scan the nginx image from Docker Hub, you would run the following command:
anchore-cli scan nginx
3. View the scan results:
Once the scan is complete, you can view the results in the Anchore console or using the Anchore CLI.
To view the scan results in the Anchore console:
- Open the Anchore console at
http://localhost:8080/anchore. - Click Images.
- Click the name of the image that you scanned.
- Click Vulnerabilities.
To view the scan results using the Anchore CLI:
anchore-cli show image <image-name>
This will display a JSON object containing the scan results.
4. Fix the vulnerabilities:
Once you have viewed the scan results, you can fix the vulnerabilities in your image.
To fix a vulnerability, you need to update the image to use a newer version of the vulnerable package or to patch the vulnerability.
Once you have fixed the vulnerabilities, you can scan the image again to verify that the vulnerabilities have been fixed.
Additional tips:
- You can use Anchore to scan images from Docker Hub, Amazon ECR, or your own registry.
- You can configure Anchore to scan images automatically when they are pushed to your registry.
- You can integrate Anchore with your CI/CD pipeline to scan images as part of your build and deployment process.
- Anchore provides a variety of features to help you manage your vulnerabilities, such as:
- Vulnerability prioritization: Anchore prioritizes vulnerabilities based on their severity and impact.
- Vulnerability remediation: Anchore provides recommendations on how to fix vulnerabilities.
- Vulnerability tracking: Anchore tracks vulnerabilities over time so that you can see how your vulnerability posture is improving.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

