What is Anomali?

Anomali is a cybersecurity platform that specializes in threat intelligence. It provides organizations with tools and services to help them effectively manage and utilize threat intelligence data for improving their cybersecurity defenses.
Anomali is designed to help organizations effectively operationalize threat intelligence, making it a valuable tool for security teams aiming to stay ahead of cyber threats and improve their overall cybersecurity posture. However, the specific use cases and capabilities may vary depending on the edition and deployment of Anomali being used by the organization.
Top 10 use cases of Anomali:
Here are the top 10 use cases of Anomali:
- Threat Intelligence Aggregation: Anomali collects, aggregates, and normalizes threat intelligence data from various sources, including open-source feeds, commercial providers, and internal sources, to provide a comprehensive view of the threat landscape.
- Threat Detection and Prioritization: It uses threat intelligence to detect and prioritize threats by correlating incoming threat data with an organization’s existing security events and logs. This helps security teams focus on the most critical threats.
- Incident Response: Anomali assists organizations in responding to security incidents by providing contextual information about threats, including indicators of compromise (IOCs), tactics, techniques, and procedures (TTPs), and suggested response actions.
- Vulnerability Management: The platform integrates threat intelligence into vulnerability management processes, helping organizations identify and prioritize vulnerabilities that are actively being exploited or targeted by threat actors.
- Phishing Detection: Anomali helps organizations detect and mitigate phishing attacks by identifying phishing-related indicators and providing real-time alerts about phishing campaigns.
- Threat Hunting: Security teams can use Anomali to proactively hunt for threats within their network by leveraging threat intelligence data to search for anomalous or suspicious activity.
- Malware Analysis: The platform supports the analysis of malware by providing information on malware families, their behavior, and associated indicators. This helps organizations understand and respond to malware threats effectively.
- Security Information and Event Management (SIEM) Enhancement: Anomali can be integrated with SIEM solutions to enhance their threat detection and alerting capabilities by providing context and threat intelligence data.
- Custom Threat Feeds: Organizations can create custom threat feeds tailored to their specific needs and infrastructure. Anomali enables the creation, management, and sharing of these custom feeds.
- Security Orchestration and Automation: Anomali can be integrated with security orchestration and automation platforms (SOAR) to automate response actions based on threat intelligence. This accelerates incident response and reduces manual intervention.
What are the feature of Anomali?
Anomali is a comprehensive threat intelligence platform that offers a range of features to help organizations manage, analyze, and operationalize threat intelligence data effectively. While the specific features and capabilities may vary based on the version and edition of Anomali being used, here are some of the key features commonly associated with Anomali:
Key Features of Anomali:
- Threat Intelligence Aggregation: Anomali collects and aggregates threat intelligence data from various sources, including open-source feeds, commercial providers, and internal sources. It normalizes this data for consistency and analysis.
- Threat Intelligence Enrichment: The platform enriches threat intelligence data with contextual information, such as indicators of compromise (IOCs), threat actors, tactics, techniques, and procedures (TTPs), and associated vulnerabilities.
- Custom Threat Feeds: Anomali allows organizations to create custom threat intelligence feeds tailored to their specific needs and infrastructure. Users can manage and share these feeds with others.
- Threat Detection and Correlation: Anomali correlates incoming threat intelligence data with an organization’s existing security events and logs to detect and prioritize threats effectively.
- Incident Response: The platform supports incident response efforts by providing contextual information about threats and suggested response actions. It helps organizations take prompt and appropriate actions in the event of a security incident.
- Vulnerability Management Integration: Anomali integrates threat intelligence into vulnerability management processes, helping organizations identify and prioritize vulnerabilities actively being targeted by threat actors.
- Phishing Detection: Anomali aids in the detection and mitigation of phishing attacks by identifying phishing-related indicators and providing real-time alerts about phishing campaigns.
- Threat Hunting: Security teams can use Anomali to proactively hunt for threats within their network. The platform helps in searching for anomalous or suspicious activity based on threat intelligence data.
- Malware Analysis Support: Anomali assists in the analysis of malware by providing information on malware families, behavior, and associated indicators. This information helps organizations understand and respond to malware threats effectively.
- Integration with Other Security Solutions: Anomali can be integrated with various security solutions, including SIEM (Security Information and Event Management), IDS/IPS (Intrusion Detection System/Intrusion Prevention System), and SOAR (Security Orchestration, Automation, and Response) platforms to enhance their capabilities with threat intelligence.
How Anomali works and Architecture?
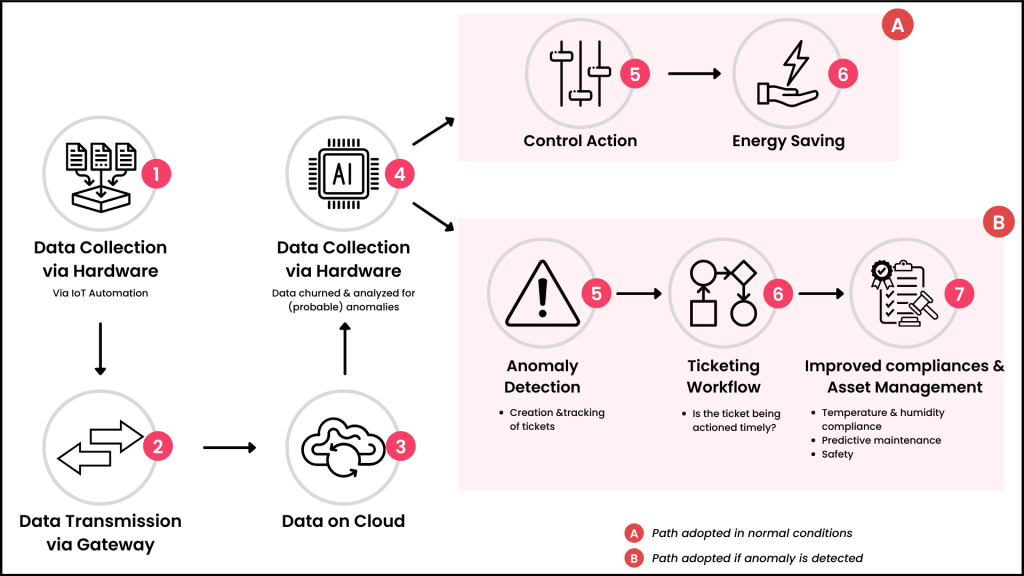
Anomali’s architecture and functionality can be summarized in the following steps:
- Data Collection: Anomali collects threat intelligence data from various sources, including open-source feeds, commercial providers, and internal sources. It also collects internal logs and security event data from the organization’s infrastructure.
- Normalization and Enrichment: The collected data is normalized to ensure consistency, and contextual information is added to enrich the threat intelligence. This includes information about threat actors, tactics, IOCs, and more.
- Storage and Management: Anomali stores and manages threat intelligence data in a centralized repository. It can store historical data, allowing organizations to analyze trends and patterns over time.
- Correlation and Analysis: The platform correlates incoming threat intelligence data with the organization’s existing security events and logs. It analyzes this data to detect and prioritize threats based on their relevance and impact.
- Alerting and Reporting: Anomali generates alerts and provides real-time notifications about detected threats. It also offers reporting and visualization capabilities to help security teams understand and communicate the threat landscape effectively.
- Integration: Anomali can be integrated with other security solutions, such as SIEM, IDS/IPS, and SOAR platforms, to enhance their threat detection and response capabilities with threat intelligence.
- Incident Response: In the event of a security incident, Anomali provides contextual information about the threat, including suggested response actions, helping security teams respond promptly and effectively.
- Custom Threat Feeds: Organizations can create and manage custom threat intelligence feeds to meet their specific requirements and share threat data with partners or industry peers.
Anomali’s architecture is designed to facilitate the collection, enrichment, analysis, and operationalization of threat intelligence data to improve an organization’s cybersecurity posture. The specifics of the architecture may vary based on deployment options, such as on-premises or cloud-based, and the organization’s specific requirements.
How to Install Anomali?
There are two ways to install Anomali:
- Cloud-based installation: Anomali ThreatStream is a cloud-based threat intelligence platform that can be installed in minutes. To install Anomali ThreatStream, you will need to create an account on the Anomali website and select the plan that best meets your needs. Once you have created an account, you will be able to access the Anomali ThreatStream web UI and start using the platform immediately.
- On-premises installation: Anomali ThreatStream can also be installed on-premises. To install Anomali ThreatStream on-premises, you will need to download the Anomali ThreatStream installation package from the Anomali website. Once you have downloaded the installation package, you can follow the instructions in the installation guide to install Anomali ThreatStream on your server.
Some additional tips for installing Anomali:
- Make sure that your server has enough resources allocated to it. Anomali ThreatStream is a resource-intensive application, so it is important to give it enough CPU, memory, and storage to run smoothly.
- If you are installing Anomali ThreatStream in a production environment, it is recommended to create a separate VLAN for the Anomali ThreatStream appliance. This will help to isolate the Anomali ThreatStream appliance from the rest of your network and improve security.
- It is also recommended to configure a firewall on the Anomali ThreatStream appliance to restrict access to only authorized users and IP addresses.
Once you have installed Anomali, you can start configuring it to monitor your network for security threats.
Basic Tutorials of Anomali: Getting Started
Following is the stepwise Basic Tutorials of Anomali ThreatStream:
1. Getting Started
- Log in to the Anomali ThreatStream web UI.
- Click the Help button in the top right corner of the page.
- Review the Getting Started section of the help documentation. This will give you a basic overview of Anomali ThreatStream and how to use it.
2. Configuring Anomali ThreatStream
Once you have a basic understanding of Anomali ThreatStream, you can start configuring it to monitor your network for security threats.
- Click the Configuration tab in the top navigation bar.
- Click the Sensors link in the left navigation pane.
- Click the Add Sensor button.
- Select the type of sensor that you want to add and click the Next button.
- Enter the required information for the sensor and click the Finish button.
Repeat steps 3-5 to add all of the sensors that you need to monitor your network.
3. Collecting Threat Intelligence
Once you have configured your sensors, you can start collecting threat intelligence. To collect threat intelligence, click the Threat Intelligence tab and then click the Collect button.
Anomali ThreatStream will start collecting threat intelligence from a variety of sources, including the Anomali ThreatStream Exchange, open-source threat feeds, and intelligence feeds from ISACs.
4. Analyzing Threat Intelligence
Once Anomali ThreatStream has collected threat intelligence, you can start analyzing it. To analyze threat intelligence, click the Analytics tab.
Anomali ThreatStream provides a variety of tools to help you analyze threat intelligence, including dashboards, reports, and search capabilities.
5. Automating Threat Intelligence Operations
You can also use Anomali ThreatStream to automate your threat intelligence operations. To automate your threat intelligence operations, click the Automation tab.
Anomali ThreatStream provides a variety of tools to help you automate your threat intelligence operations, including alerts, integrations, and playbooks.
Some additional tips for using Anomali ThreatStream:
- Use the Dashboards and Reports features to create custom dashboards and reports to visualize and analyze threat intelligence.
- Use the Search feature to search for specific threat intelligence indicators, such as IP addresses, URLs, and file hashes.
- Use the Alerts feature to create alerts that will notify you when Anomali ThreatStream detects new threat intelligence.
- Use the Integrations feature to integrate Anomali ThreatStream with other security tools, such as SIEMs and firewalls.
- Use the Playbooks feature to automate your threat intelligence response workflow.
Anomali ThreatStream is a powerful threat intelligence platform that can help you to protect your network from security threats. By following the steps above, you can learn how to install and configure Anomali ThreatStream, and start using it to monitor your network, collect threat intelligence, analyze threat intelligence, and automate your threat intelligence operations.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

