What is AWS IAM?

AWS Identity and Access Management (IAM) is a web service provided by Amazon Web Services (AWS) that allows organizations to manage user identities and control access to AWS resources and services. IAM provides a wide range of features and capabilities for securing your AWS environment.
AWS IAM’s capabilities are designed to help organizations secure their AWS resources, implement the principle of least privilege, and manage user access effectively. It’s a fundamental component of AWS security, ensuring that only authorized users and services can access and interact with AWS resources.
Top 10 use cases of AWS IAM:
Here are the top 10 use cases of AWS IAM:
- User and Group Management: Create and manage AWS user accounts and groups to control who can access AWS resources and services.
- Fine-Grained Access Control: Define and enforce access policies that specify which actions users and groups can perform on specific AWS resources.
- Multi-Factor Authentication (MFA): Enhance security by requiring users to provide an additional authentication factor (e.g., a hardware token or a mobile app) when signing in.
- Temporary Security Credentials: Issue temporary security credentials (IAM roles) to grant short-term access to resources, reducing the risk of long-term credential exposure.
- Programmatic Access: Generate access keys for programmatic access to AWS resources through the AWS Command Line Interface (CLI) or SDKs.
- Identity Federation: Federate user identities with external identity providers (IdPs) such as Active Directory, LDAP, or SAML for single sign-on (SSO) access to AWS.
- AWS Service Integration: Define IAM roles that allow AWS services, such as EC2 instances or Lambda functions, to securely access other AWS resources.
- Cross-Account Access: Grant permissions for users or services in one AWS account to access resources in another AWS account, facilitating resource sharing and collaboration.
- Resource-Level Permissions: Enforce fine-grained access control by specifying which resources within a service can be accessed and what actions can be performed on them.
- Access Auditing and Monitoring: Monitor user activity and access events using AWS CloudTrail and AWS Config, and receive detailed logs and reports for auditing and compliance purposes.
- Identity-Based Policies: Create policies based on user identities, allowing you to grant or restrict access to resources based on user roles or attributes.
- Role Switching: Users with the necessary permissions can assume IAM roles temporarily, providing secure access to resources without sharing long-term credentials.
What are the feature of AWS IAM?
Key Features of AWS IAM:
- User and Group Management: Create and manage IAM users and groups with distinct access credentials and permissions.
- Access Control Policies: Define and attach JSON-based access policies to IAM users, groups, and roles to specify what actions they can perform on AWS resources.
- Role-Based Access Control: Assign roles to AWS resources, such as EC2 instances or Lambda functions, and grant them temporary permissions, enabling secure interactions.
- Multi-Factor Authentication (MFA): Enable MFA to add an extra layer of security by requiring users to provide a second authentication factor when signing in.
- Temporary Security Credentials: Issue temporary security credentials (IAM roles) to grant short-term access to resources, reducing the risk of long-term credential exposure.
- Identity Federation: Federate identities from external identity providers (IdPs) using protocols like SAML, allowing for single sign-on (SSO) access to AWS.
- Programmatic Access: Generate access keys for programmatic access to AWS resources through the AWS CLI, SDKs, or third-party tools.
- Password Policies: Set and enforce password policies to enhance password security for IAM users.
- Access Analyzer: Analyze access policies for potential unintended resource exposures and provide recommendations for policy improvement.
- Access Auditing and Monitoring: Use AWS CloudTrail and AWS Config to monitor and log user activity and resource access, facilitating auditing and compliance efforts.
- Policy Simulation: Test the effects of access policies without affecting actual resources to ensure the desired level of access control.
- Cross-Account Access: Grant permissions for users or services in one AWS account to access resources in another AWS account, facilitating resource sharing and collaboration.
- Resource-Level Permissions: Enforce fine-grained access control by specifying which resources within a service can be accessed and what actions can be performed on them.
How AWS IAM works and Architecture?
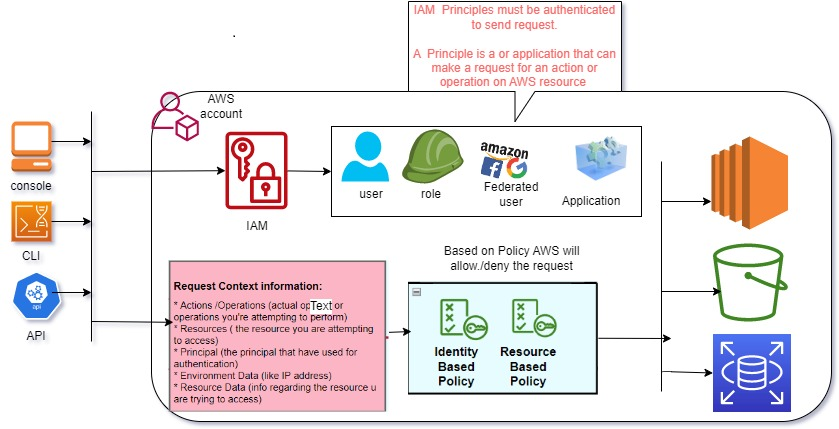
- User Authentication: IAM users and roles authenticate by providing their access credentials (usernames and passwords) or by assuming roles through federated identity providers.
- Access Policies: Access policies are JSON-based documents attached to IAM users, groups, and roles. They define what actions are allowed or denied on specific AWS resources.
- Permissions Evaluation: When a user or role attempts to perform an action on an AWS resource, AWS IAM evaluates the access policies to determine whether the request should be allowed or denied.
- Temporary Credentials: IAM roles can issue temporary security credentials (access key, secret key, and session token) to users and services, granting them temporary access to resources.
- MFA Authentication: Multi-Factor Authentication (MFA) can be enabled for additional authentication security, requiring users to provide a second authentication factor, such as a time-based one-time password (TOTP).
IAM is a service provided by AWS and does not require a specific deployment or infrastructure on the customer’s side. It operates as a central identity and access management service within the AWS environment.
IAM’s architecture involves several key components:
- IAM Users and Groups: IAM users and groups are entities managed by IAM, representing human users, applications, or services that need access to AWS resources.
- Access Policies: Access policies are JSON documents that specify permissions. They can be attached to users, groups, or roles to define who can access what resources and actions.
- IAM Roles: IAM roles are similar to users but are intended for AWS services, applications, or EC2 instances that need temporary access to resources. Roles can also be assumed by trusted entities, such as users or services in other AWS accounts.
- Federated Identities: IAM supports identity federation with external identity providers (IdPs) using standards like SAML. Federated identities allow users to sign in to AWS using their existing corporate credentials.
- Temporary Security Credentials: IAM roles can issue temporary security credentials that are valid for a specific duration. These credentials are often used by EC2 instances and Lambda functions.
- Access Keys: IAM users can generate access keys (access key ID and secret access key) for programmatic access to AWS resources via the AWS CLI, SDKs, or third-party tools.
IAM’s architecture is designed to be highly scalable, secure, and integrated with various AWS services, enabling organizations to manage user access effectively and secure their AWS resources. It plays a crucial role in implementing security best practices and the principle of least privilege within AWS environments.
How to Install AWS IAM?
To install AWS IAM, you do not need to install any software on your computer. AWS IAM is a cloud-based service that is managed by Amazon Web Services (AWS).
To get started with AWS IAM, you will need to create an AWS account. Once you have created an AWS account, you can sign in to the AWS Management Console and navigate to the IAM service console.
From the IAM service console, you can create new IAM users, groups, and roles. You can also assign policies to IAM users, groups, and roles. Policies define the permissions that IAM users, groups, and roles have to access AWS resources.
To learn more about AWS IAM, please visit the AWS IAM documentation: https://docs.aws.amazon.com/IAM/latest/UserGuide/introduction.html
Some additional tips for using AWS IAM:
- Use IAM roles to grant permissions to AWS services. This is the recommended way to grant permissions to AWS services, as it allows you to manage permissions centrally and reduces the risk of over-privileging AWS services.
- Use IAM users and groups to grant permissions to individuals and teams.
- Use IAM policies to define the permissions that IAM users, groups, and roles have to access AWS resources.
- Use IAM conditions to restrict the permissions that IAM users, groups, and roles have to access AWS resources.
Basic Tutorials of AWS IAM: Getting Started

The following steps are the Basic Tutorials of AWS IAM:
1. Create an IAM user
- Sign in to the AWS Management Console and navigate to the IAM service console.
- In the navigation pane, click Users.
- Click Add User.
- Enter a user name and select the Programmatic access type.
- Click Next: Permissions.
- Select Attach existing policies directly.
- In the Filter policies box, type AdministratorAccess and select AWSAdministratorAccess from the list of policies.
- Click Next: Review.
- Review the user details and click Create User.
2. Create an IAM role
- Sign in to the AWS Management Console and navigate to the IAM service console.
- In the navigation pane, click Roles.
- Click Create role.
- Select Another AWS account and enter the account ID of the account that you want to create the role for.
- Click Next: Permissions.
- Select AWS service role and select the service that you want to create the role for.
- Click Next: Review.
- Review the role details and click Create role.
3. Assign an IAM policy to an IAM user or role
- Sign in to the AWS Management Console and navigate to the IAM service console.
- In the navigation pane, press Users or Roles.
- Select the IAM user or role that you want to assign the policy to.
- Click the Policies tab.
- Click Attach policy.
- Select the policy that you want to assign and click Attach policy.
4. Use an IAM user or role to access AWS resources
- To use an IAM user to access AWS resources, you will need to create an access key ID and secret access key for the user. You can do this from the IAM service console by clicking the Security credentials tab and then clicking Create access key.
- To use an IAM role to access AWS resources, you will need to assume the role. You can do this from the IAM service console by clicking the Roles tab and then clicking the role that you want to assume.
Example use case:
You want to create an IAM user to provide access to the Amazon Simple Storage Service (S3) service. You would first create an IAM user with the Programmatic access type. Then, you would attach the AmazonS3FullAccess policy to the IAM user. Once the policy is attached, you can use the IAM user’s access key ID and secret access key to access S3 resources.
Additional tips:
- Use IAM roles to grant permissions to AWS services. This is the recommended way to grant permissions to AWS services, as it allows you to manage permissions centrally and reduces the risk of over-privileging AWS services.
- Use IAM users and groups to grant permissions to individuals and teams.
- Use IAM policies to define the permissions that IAM users, groups, and roles have to access AWS resources.
- Use IAM conditions to restrict the permissions that IAM users, groups, and roles have to access AWS resources.
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024
- The Role of Big Data in Higher Education - April 28, 2024

