What is Azure Active Directory?

Azure Active Directory (AAD) is a cloud-based identity and access management (IAM) service provided by Microsoft. It provides a wide range of features and capabilities for managing user identities, securing access to applications and resources, and enhancing overall security within Azure and other Microsoft services.
Azure Active Directory’s flexibility and robust set of features make it a valuable tool for managing identity and access in the cloud, enhancing security, and improving the user experience across a wide range of applications and services within the Azure ecosystem and beyond.
Top 10 use cases of Azure Active Directory:
Here are the top 10 use cases of Azure Active Directory:
- User Authentication: Azure AD serves as an identity provider, allowing users to sign in securely to various applications and services using their Azure AD credentials.
- Single Sign-On (SSO): Implement SSO to enable users to access multiple applications with a single set of credentials, simplifying access management and improving user experience.
- Multi-Factor Authentication (MFA): Enhance security by requiring users to provide additional authentication factors, such as a mobile app or a text message code, in addition to their password.
- Identity and Access Management (IAM): Use Azure AD to manage user identities, roles, and access permissions to Azure resources, ensuring the principle of least privilege.
- Application Access Control: Control access to specific applications based on user roles and policies, allowing administrators to enforce security and compliance standards.
- Conditional Access Policies: Define and enforce access policies that consider user, device, location, and risk factors, providing granular control over access.
- Guest Access: Collaborate securely with external partners, customers, and vendors by inviting them as guest users to access your organization’s resources.
- Password Management: Implement self-service password reset and change policies to reduce the administrative burden on IT teams and improve user productivity.
- Identity Protection: Detect and respond to suspicious sign-in activities and potential security risks using Azure AD’s identity protection capabilities.
- Integration with SaaS Applications: Seamlessly integrate Azure AD with a wide range of Software as a Service (SaaS) applications, such as Office 365, Salesforce, and more, for secure access and identity management.
- Identity Federation: Establish trust relationships with other identity providers (e.g., on-premises Active Directory) to enable secure authentication and access to resources.
- Device Management: Enforce security policies on devices accessing your organization’s resources, including mobile devices and computers.
- Audit and Compliance: Monitor user activity, access, and sign-in events to track changes and ensure compliance with security policies and regulations.
- Application Proxy: Securely publish on-premises web applications for remote access without exposing them directly to the internet.
- Azure AD B2B Collaboration: Collaborate with external organizations by allowing their users to access your resources while maintaining control over access and permissions.
What are the feature of Azure Active Directory?
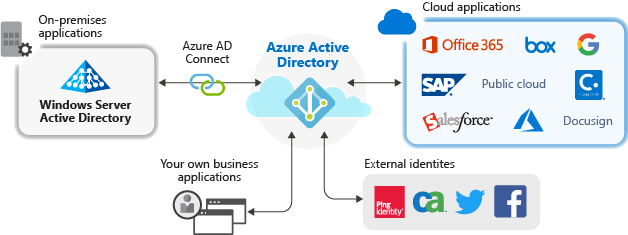
Azure Active Directory (Azure AD) is a comprehensive cloud-based identity and access management service offered by Microsoft. It provides a wide range of features and capabilities for managing user identities, securing access to applications and resources, and enhancing overall security within Azure and other Microsoft services. Here are the key features of Azure Active Directory, along with an overview of how it works and its architecture:
Key Features of Azure Active Directory:
- Identity Management: Azure AD enables you to create and manage user identities, groups, and roles, ensuring that the right users have access to the right resources.
- Single Sign-On (SSO): Implement SSO to allow users to sign in once and access multiple applications without the need to enter credentials repeatedly.
- Multi-Factor Authentication (MFA): Enhance security by requiring users to provide additional authentication factors, such as a mobile app or a text message code, in addition to their password.
- Conditional Access Policies: Define access policies based on user attributes, device state, location, and more, ensuring that access is granted based on specific conditions.
- Application Proxy: Securely publish on-premises web applications for remote access without exposing them directly to the internet.
- Guest Access: Collaborate securely with external partners, customers, and vendors by inviting them as guest users to access your organization’s resources.
- Self-Service Password Reset: Empower users to reset their own passwords and manage their accounts, reducing the burden on IT support.
- Azure AD B2B and B2C: Extend your identity management to external organizations (B2B) and customer-facing applications (B2C) while maintaining control over access.
- Identity Protection: Detect and respond to suspicious sign-in activities and potential security risks using Azure AD’s identity protection capabilities.
- Role-Based Access Control (RBAC): Define and enforce access permissions based on roles and responsibilities within your organization.
- Azure AD Connect: Synchronize on-premises Active Directory with Azure AD to ensure a unified identity experience for users.
- Security Reports and Analytics: Monitor user activity, access events, and sign-in activities to track changes and ensure compliance with security policies and regulations.
How Azure Active Directory works and Architecture?
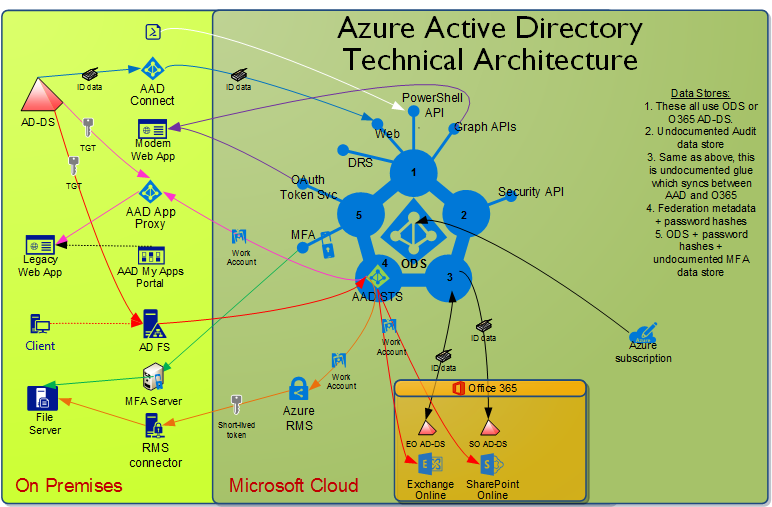
Azure Active Directory works by providing a central identity and access management platform in the cloud. Here’s an overview of how it operates:
- Identity Creation: Azure AD allows administrators to create and manage user identities, groups, and roles within the Azure AD directory.
- Authentication: Users can sign in to Azure AD-protected resources using their credentials, including usernames and passwords.
- Single Sign-On (SSO): SSO enables users to access multiple applications and services with a single set of credentials, improving user experience and reducing password fatigue.
- Multi-Factor Authentication (MFA): Users may be required to provide additional authentication factors for increased security, such as a one-time code sent to a mobile app.
- Conditional Access Policies: Policies are defined to control access based on specific conditions, such as user location, device state, and risk level.
- Application Integration: Azure AD integrates with a wide range of Microsoft and third-party applications, enabling secure access and identity management.
Azure Active Directory’s architecture is designed to provide scalability, reliability, and security. It comprises several key components:
- Azure AD Directory: This is the core component that stores user identities, groups, roles, and access policies.
- Azure AD Authentication Services: These services handle user authentication and SSO capabilities.
- Azure AD Graph API: Provides programmatic access to Azure AD for administration and management tasks.
- Azure AD Connect: A tool that synchronizes on-premises Active Directory with Azure AD to ensure consistent identities and passwords.
- Azure AD Application Proxy: Allows secure remote access to on-premises applications.
- Security and Compliance Center: A management interface for monitoring and enforcing security policies.
- Reporting and Monitoring: Azure AD provides reporting and analytics capabilities to track user activities and security events.
Azure Active Directory’s architecture is designed to provide a secure and scalable identity and access management solution for organizations, whether they are using Azure services, third-party applications, or a hybrid environment that combines on-premises and cloud resources. It plays a critical role in ensuring secure access to resources and enhancing overall security posture.
How to Install Azure Active Directory?
To install Azure Active Directory (Azure AD), you will need a Microsoft account. Once you have a Microsoft account, you can follow these steps:
- First, Visit to the Azure portal and sign in with your Microsoft account.
- Press on the Azure Active Directory service.
- Click on the Create tenant button.
- Enter a name for your tenant and select a region.
- Click on the Create button.
Azure AD will be created and you will be redirected to the Azure AD dashboard.
Once you have created Azure AD, you can start adding users and groups. You can also start configuring Azure AD to integrate with your on-premises Active Directory domain.
Some additional steps that you may need to follow, depending on your configuration:
- If you are integrating Azure AD with your on-premises Active Directory domain, you will need to install Azure AD Connect.
- If you are using Azure AD for single sign-on (SSO), you will need to configure your applications to support SSO with Azure AD.
- If you are using Azure AD for multi-factor authentication (MFA), you will need to configure your users for MFA.
For more information on how to install and configure Azure AD, please see the following resources:
- Azure Active Directory documentation: https://learn.microsoft.com/en-us/azure/active-directory/
- Azure AD Connect documentation: https://github.com/microsoft/AADConnectConfigDocumenter
Please note that Azure AD is a paid service. However, there is a free tier that you can use to get started.
Basic Tutorials of Azure Active Directory: Getting Started
The following steps are the Basic Tutorials of FireEye Helix:
1. Create a new incident
- Log in to FireEye Helix.
- Click on the “Create New Incident” button.
- Fill the incident details, such as the name, description, and type.
- Click on the “Submit” button.
2. Assign the incident to a team
- Open the incident record.
- Click on the “Team” tab.
- Choose the team that you want to assign the incident to.
- Click on the “Submit” button.
3. Investigate the incident
The incident team will investigate the incident to determine the root cause and impact. This may include interviewing witnesses, collecting logs, and analyzing the affected systems. The incident team can use FireEye Helix’s incident investigation features, such as log analysis, intrusion detection, and forensic analysis.
4. Remediate the incident
Once the incident team has identified the root cause of the incident, they will take steps to remediate it. This may include removing malware, patching vulnerabilities, or restoring systems from backups. The incident team can use FireEye Helix’s incident response orchestration and automation features to automate common incident response tasks.
5. Recover from the incident
Once the incident has been remediated, the incident team will help the organization to recover from the incident and restore normal operations. This may include communicating with affected stakeholders, implementing additional security measures, and restoring business processes.
Additional tips for using FireEye Helix:
- Use incident playbooks to provide step-by-step instructions on how to respond to common security incidents.
- Apply reporting and analytics tools to track your incident response performance and identify areas for improvement.
- Apply threat intelligence and collaboration tools to share information about security incidents with other organizations.
Use case Example:
An organization is alerted to a potential malware infection on one of its servers. The organization’s security team uses FireEye Helix to create a new incident and assign it to the incident response team. The incident response team uses FireEye Helix to investigate the incident and determine that the server has been infected with ransomware. The incident response team uses FireEye Helix to remediate the incident, such as isolating the infected server and restoring the server from a backup. The incident response team also works with the company to implement additional security measures to hamper future ransomware infections.
FireEye Helix is a powerful tool that can help organizations to improve their incident response process. By following the steps in this tutorial, you can learn how to use FireEye Helix to create, manage, and respond to security incidents.
Creative response:
FireEye Helix is a security platform that helps you to protect your organization from a wide range of cyber threats. It is like a security team of highly trained experts who are constantly monitoring your organization’s networks and systems for signs of cyber threats. When they detect a threat, they immediately investigate and take steps to remediate it.
FireEye Helix can also automate many common security tasks, such as security incident response and threat intelligence sharing. This frees up your security team to focus on more strategic tasks, such as developing and implementing new security strategies.
If you are looking for a powerful and comprehensive security platform, FireEye Helix is a great choice.
- Degree Pursuit: Navigating the Path to Educational Excellence - July 4, 2024
- Why Is Studying English Important in a Business Environment? - July 4, 2024
- Top 10 Data Science Skills You Need in 2024 - July 3, 2024

