What is BigID?

BigID is a data privacy and protection platform that focuses on data discovery, classification, and governance. It uses advanced data intelligence and machine learning algorithms to help organizations identify and manage their sensitive data. BigID enables businesses to comply with data privacy regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), and strengthen data security measures.
Top 10 use cases of BigID:
- Data Discovery and Inventory: BigID helps organizations discover and inventory sensitive and personal data across various data sources and repositories.
- Data Classification: It automatically classifies and categorizes data based on its sensitivity, enabling better data governance and privacy management.
- GDPR Compliance: BigID aids in GDPR compliance by identifying and managing personal data, providing subject access requests (SAR) support, and monitoring data usage.
- CCPA and Data Privacy Compliance: It assists in complying with CCPA and other data privacy regulations by giving organizations visibility into consumer data and their rights.
- Data Mapping and Data Flow Analysis: BigID offers data mapping and data flow analysis to track data movement and understand data relationships.
- Data Access Control: It helps enforce access controls based on data sensitivity and ensures data is only accessible to authorized users.
- Data Breach Response: BigID facilitates data breach response by quickly identifying the scope and impact of data breaches.
- Data Protection Impact Assessments (DPIA): It aids in conducting DPIAs to assess and mitigate privacy risks associated with data processing activities.
- Data Retention Management: BigID assists in managing data retention policies and ensuring compliance with data retention requirements.
- Third-Party Risk Management: It helps organizations assess and manage third-party data risks by identifying sensitive data shared with external parties.
What are the feature of BigID?
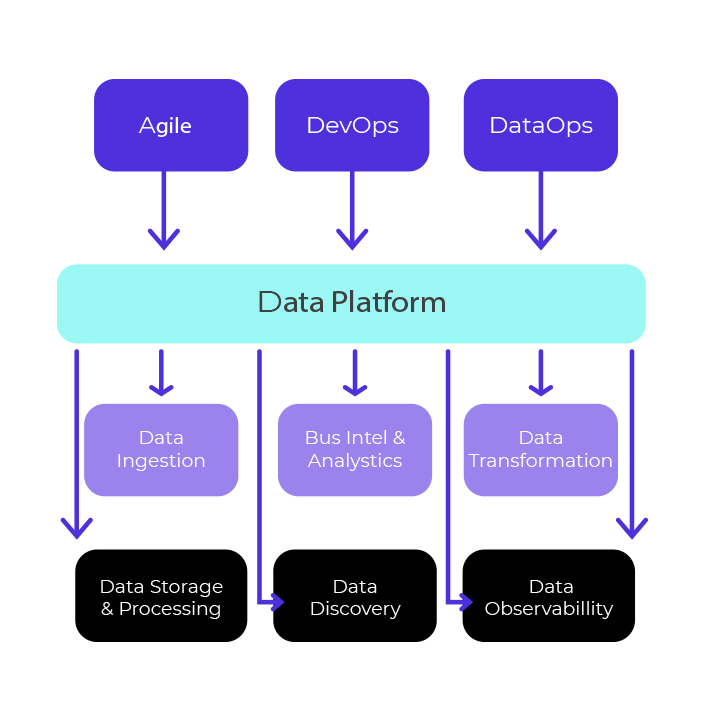
- Data Discovery and Inventory: Automatically discover, classify, and inventory sensitive data across on-premises and cloud environments.
- Data Classification: Classify data based on sensitivity and apply appropriate data protection measures.
- Data Intelligence and Profiling: Use machine learning algorithms for data intelligence and profiling to understand data relationships and attributes.
- Data Mapping and Data Flow Analysis: Map data flows and track data movement across systems.
- Data Access Control: Enforce access controls based on data sensitivity.
- Data Rights Management: Facilitate data subject rights management and respond to data subject access requests (SAR).
- Data Privacy Compliance: Aid in compliance with GDPR, CCPA, and other data privacy regulations.
- Data Breach Response: Detect and investigate data breaches to understand the scope and impact.
- Data Retention Management: Manage data retention policies and ensure compliance with retention requirements.
- Third-Party Risk Assessment: Assess third-party data risks and monitor data shared with external parties.
How BigID works and Architecture?
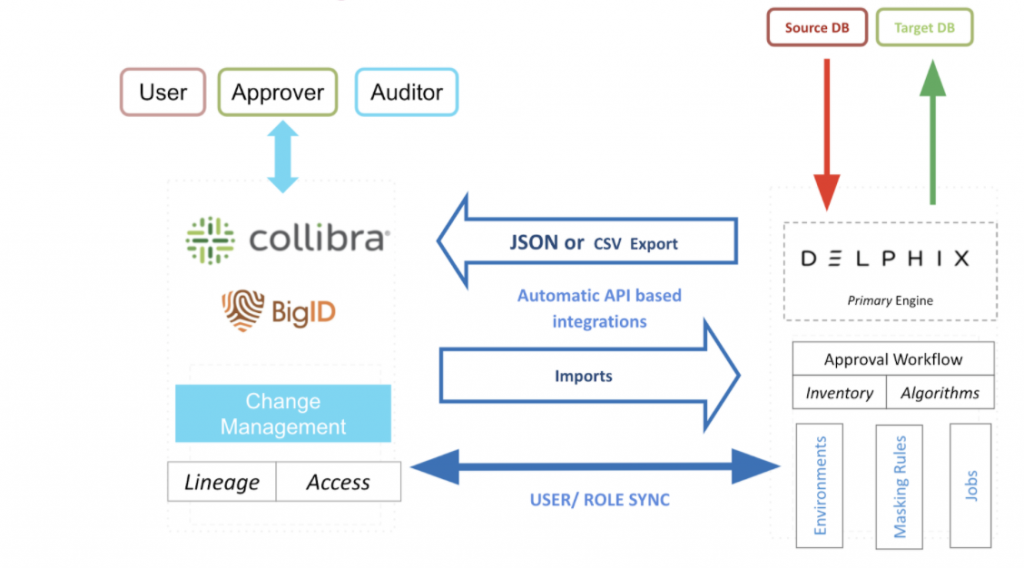
BigID uses a combination of data intelligence, machine learning, and data correlation techniques to identify and manage sensitive data. It typically follows a data pipeline architecture:
- Data Collection: BigID connects to various data sources, including databases, file systems, cloud storage, and data warehouses, to collect data.
- Data Intelligence and Profiling: It uses machine learning algorithms to profile data and understand data relationships and attributes.
- Data Classification: BigID classifies data based on sensitivity, such as personally identifiable information (PII) or financial data.
- Data Mapping and Data Flow Analysis: It maps data flows to track data movement across systems and understand data relationships.
- Data Access Control: BigID enforces access controls based on data sensitivity and ensures data is only accessible to authorized users.
How to Install BigID?
The installation of BigID can vary based on the deployment model chosen (on-premises or cloud-based) and the specific version you are installing. This is the typical installation steps for BigID might include:
- Contact BigID: Reach out to BigID’s sales team or visit their website to request access to the product.
- Select Deployment Model: Choose between an on-premises deployment or a cloud-based deployment.
- Prepare the Environment: Ensure that your system meets the hardware and software requirements specified by BigID.
- Install the Software: Follow the installation instructions provided by BigID to install the software.
- Configuration: Configure the BigID platform based on your organization’s requirements, including data sources and data privacy policies.
- Integration: Integrate BigID with your existing data repositories and applications.
For the latest and most accurate installation instructions, refer to BigID’s official documentation.
Basic Tutorials of BigID: Getting Started
Below is a step-by-step basic tutorial to get you started with BigID:

Step-by-Step Basic Tutorial of BigID:
Step 1: Obtain Access to BigID:
- Contact BigID or their authorized sales representative to obtain access to the BigID platform.
- Once you have the necessary credentials, log in to the BigID web application using a supported web browser.
Step 2: Connect Data Sources:
- Connect the data sources that you want BigID to scan for sensitive data. Data sources can include databases, file systems, cloud storage, data warehouses, etc.
- Configure the necessary authentication and authorization settings for each data source.
Step 3: Run Data Discovery and Profiling:
- Start a data discovery and profiling scan on the connected data sources.
- BigID will automatically analyze the data and identify potentially sensitive information based on patterns and algorithms.
Step 4: Review and Classify Data:
- Review the results of the data discovery and profiling scan in the BigID interface.
- Classify the sensitive data identified by applying relevant data labels or tags.
Step 5: Define Data Privacy Policies:
- Define data privacy policies based on regulatory requirements (e.g., GDPR, CCPA) and internal data governance needs.
- Set up rules to automatically tag or mask sensitive data based on the policies.
Step 6: Monitor Data Access and Usage:
- Utilize BigID’s monitoring capabilities to track data access and usage across the organization.
- Receive alerts and notifications for potential privacy or security incidents.
Step 7: Respond to Subject Access Requests (SARs):
- Use BigID to fulfill data subject access requests (SARs) by locating and extracting personal data related to the requesting individuals.
- Ensure compliance with data subject rights requirements.
Step 8: Data Breach Response:
- In the event of a data breach, leverage BigID’s data intelligence to quickly assess the scope and impact of the breach.
- Take necessary remediation actions to secure the data and mitigate potential harm.
Step 9: Data Retention Management:
- Implement data retention policies in BigID to manage data lifecycle and comply with retention requirements.
- Identify and delete or archive data that is no longer needed.
Step 10: Continuous Improvement:
- Continuously monitor and improve data privacy practices based on BigID’s insights and recommendations.
- Keep BigID up-to-date with the latest data sources and privacy regulations.
For detailed tutorials and up-to-date guidance, refer to BigID’s official documentation, knowledge base, and training resources.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

