What is CipherCloud?

CipherCloud is an American software company offering cloud security solutions to businesses. It focuses on securing access to cloud applications, preventing data loss, and ensuring compliance with data privacy regulations.
Here’s a breakdown of its key offerings:
1. Cloud Access Security Broker (CASB):
- Provides visibility and control over cloud app usage.
- Enforces granular access controls and data loss prevention (DLP) policies.
- Detects and mitigates threats like malware and phishing attacks.
- Helps maintain compliance with GDPR, HIPAA, and other regulations.
2. Cloud Encryption Gateway:
- Encrypts sensitive data at rest and in transit to cloud applications.
- Leverages FIPS 140-2 compliant encryption algorithms for robust data protection.
- Maintains control over encryption keys for enhanced security.
3. Cloud Data Loss Prevention (DLP):
- Identifies and classifies sensitive data across cloud apps, email, and file repositories.
- Prevents unauthorized data exfiltration through various techniques like content inspection and tokenization.
- Simplifies compliance with data privacy regulations.
4. Adaptive Access Control:
- Analyzes user behavior and context to dynamically adjust access permissions.
- Provides continuous authentication and authorization based on real-time risk assessment.
- Minimizes the attack surface and protects against unauthorized access.
5. Secure Web Gateway (SWG):
- Filters internet traffic to block malware, phishing attacks, and malicious websites.
- Enforces web security policies and protects users from online threats.
- Provides secure remote access and content filtering for various devices.
6. Endpoint Protection Platform (EPP):
- Protects devices from malware, ransomware, and other threats.
- Offers antivirus, endpoint encryption, vulnerability management, and intrusion detection.
- Integrates with cloud security solutions for holistic protection.
Top 10 use cases of CipherCloud?
Top 10 Use Cases of CipherCloud:
- Secure access to cloud applications: Gain visibility and control over cloud app usage, user activity, and data flows.
- Prevent data loss and comply with regulations: Implement DLP to secure sensitive data, prevent exfiltration, and meet data privacy compliance requirements.
- Protect against malware and phishing attacks: Filter web traffic and block malicious websites and emails to safeguard users and data.
- Enable secure remote work: Provide safe access to internal resources for remote employees regardless of location or device.
- Secure endpoints and devices: Protect devices from malware, ransomware, and other threats, minimizing cybersecurity risks.
- Simplify security management: Consolidate various security tools into a single platform for centralized management and reporting.
- Improve user experience: Provide a seamless and secure user experience for accessing cloud applications and resources.
- Gain insights into cloud activity: Generate comprehensive reports and logs to track user behavior, identify threats, and improve security posture.
- Respond to security incidents: Streamline incident response with automated workflows and forensics tools for faster mitigation of threats.
- Maintain control over encryption keys: Leverage CipherCloud’s secure key management solution to ensure data privacy and compliance.
These are just a few examples, and CipherCloud can be tailored to meet various security needs across your organization. It can be an invaluable tool for securing your cloud environment, protecting sensitive data, and ensuring compliance with data privacy regulations.
What are the feature of CipherCloud?
CipherCloud offers a comprehensive suite of cloud security features, spanning across several key areas:
1. Cloud Access Security Broker (CASB):
- Visibility and Control: Gain deep insights into your cloud application usage, including user activity, data flows, and potential violations. Enforce access controls and granular permissions to manage and limit user access to different cloud apps and data.
- Data Loss Prevention (DLP): Identify and classify sensitive data across various cloud apps, email, and file repositories. Utilize content inspection, tokenization, and other techniques to prevent unauthorized data exfiltration and ensure compliance with data privacy regulations.
- Threat Protection: Employ advanced analytics and real-time detection to identify and mitigate threats like malware, phishing attacks, and insider threats across your cloud environment.
2. Cloud Encryption Gateway:
- Data Encryption: Encrypt data at rest and in transit to and from cloud applications with robust FIPS 140-2 compliant algorithms. Maintain complete ownership and control over encryption keys for enhanced security and key management.
3. Adaptive Access Control:
- Dynamic Access Management: Analyze user behavior and context (location, device, activity) to dynamically adjust access privileges in real-time. Continuously authenticate and authorize users based on risk assessment, minimizing attack surface and unauthorized access.
4. Secure Web Gateway (SWG):
- Web Traffic Filtering: Block malicious websites, malware, phishing attacks, and unwanted content like gambling or social media to protect users from online threats and ensure safe browsing.
- Secure Remote Access: Enable secure access to internal resources for remote employees, regardless of location or device. Provide content filtering and secure connectivity for various devices.
5. Endpoint Protection Platform (EPP):
- Endpoint Security: Safeguard devices from malware, ransomware, zero-day threats, and other vulnerabilities. This includes features like antivirus, endpoint encryption, vulnerability management, and intrusion detection.
6. Additional Features:
- Centralized Management: Consolidate all security tools and cloud app access management into a single platform for simplified administration, reporting, and audit trails.
- Compliance Management: Streamline compliance with data privacy regulations like GDPR, HIPAA, PCI DSS, and others with automated assessments and reporting tools.
- Incident Response: Enhance incident response with automated workflows, forensics tools, and threat containment capabilities to quickly mitigate security breaches.
- User Education and Training: Equip users with security awareness training and education to promote safer cloud usage and minimize human error risks.
Tip: CipherCloud offers a modular approach, allowing you to choose the features that best suit your specific security needs and budget.
How CipherCloud works and Architecture?
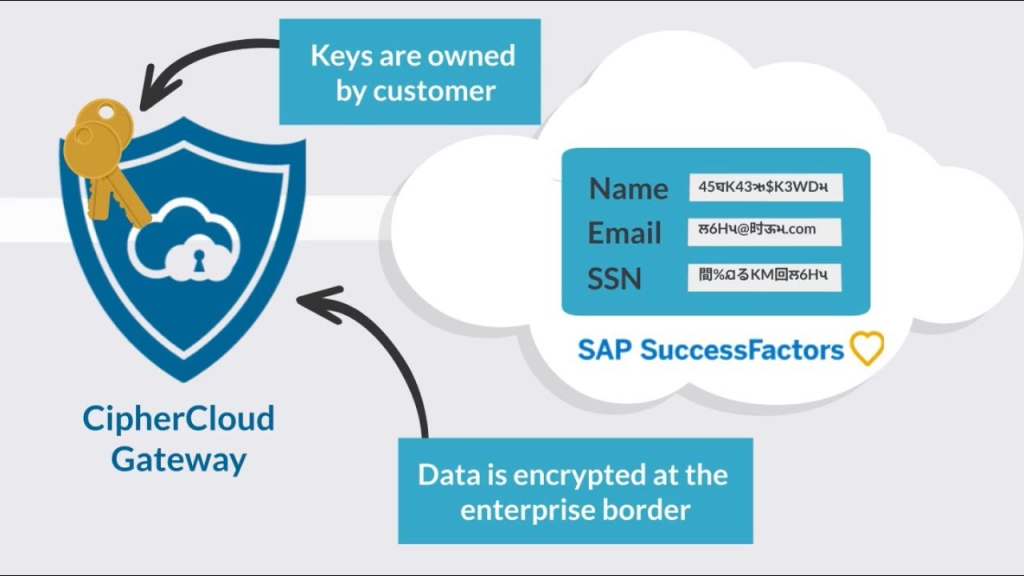
Here’s a breakdown of how CipherCloud works and its architectural strengths:
1. Global Deployment:
- CipherCloud operates through a globally distributed network of data centers strategically located around the world. This ensures low latency and optimal performance for users regardless of their location.
- Each data center houses core components like DLP engines, malware scanners, access control modules, and encryption servers.
2. Cloud Application Visibility and Control:
- Users access cloud applications through the CipherCloud platform, which acts as a secure gateway and proxy.
- The platform intercepts traffic and performs various security checks:
- DLP: Scans data for sensitive information and applies configured policies to prevent leaks.
- Threat Detection: Analyzes traffic for malware, phishing attempts, and other threats.
- Access Control: Enforces granular access controls based on user roles, location, device, and context.
- Data Encryption: Encrypts sensitive data at rest and in transit using FIPS 140-2 compliant algorithms.
3. Continuous Monitoring and Adaptive Access:
- CipherCloud continuously monitors user activity and analyzes context to dynamically adjust access permissions.
- This includes factors like location, device type, unusual activity patterns, and potential security threats.
- Adaptive access helps minimize the attack surface by granting least privilege based on real-time risk assessment.
4. Centralized Management and Reporting:
- CipherCloud provides a centralized management console for administrators to configure security policies, monitor user activity, and generate reports.
- This console offers visibility and control over the entire cloud environment from a single location.
- Compliance management tools automate assessments and reporting, simplifying adherence to data privacy regulations.
5. Scalability and Reliability:
- CipherCloud’s architecture is designed for automatic scaling and high availability.
- Resources can dynamically scale up or down based on usage patterns, ensuring optimal performance and cost efficiency.
- Data centers are geographically distributed and equipped with redundancy measures to minimize downtime and service disruptions.
Benefits of CipherCloud’s Architecture:
- Global Accessibility: Users around the world experience low latency and fast performance.
- Enhanced Security: Comprehensive security features protect against various threats and data leaks.
- Adaptive Access Control: Dynamically adjusting permissions minimizes attack surface and risks.
- Centralized Management: Simplified administration and compliance management.
- Scalability and Reliability: High availability and cost-effective resource utilization.
This information provides a basic understanding of how CipherCloud works and its architectural strengths.
How to Install CipherCloud it?
CipherCloud’s installation process depends on your chosen deployment model and desired features:
Deployment Models:
- Cloud-Based: Simplest and most common, requires no on-premise installation or hardware setup.
- Hybrid: Combines cloud services with on-premise components for greater control and customization.
Key Steps (Cloud-Based):
- Sign Up for CipherCloud:
- Create an account on CipherCloud’s website.
- Select the desired cloud apps you want to protect.
- Connect Users:
- Choose a connection method:
- Reverse proxy: Route traffic through CipherCloud’s servers.
- API integration: Integrate with cloud apps using their APIs.
- Agent-based: Install lightweight agents on user devices.
- Choose a connection method:
- Configure Policies:
- Access the CipherCloud management console.
- Define security policies for DLP, access control, encryption, and threat protection.
Additional Steps (Hybrid):
- Install on-premise components (gateways, servers) according to CipherCloud’s documentation.
- Configure network settings for secure communication between cloud and on-premise components.
CipherCloud Support:
- CipherCloud experts assist with deployment and configuration.
- Provide detailed deployment guides and documentation.
Additional Considerations:
- Technical Expertise: Assess your IT team’s skills for successful deployment.
- Integrations: Consider existing security tools for seamless integration.
- Compliance Requirements: Ensure CipherCloud aligns with your compliance needs.
Basic Tutorials of CipherCloud: Getting Started

CipherCloud is a cloud-based data security platform that offers a variety of features for encryption, key management, and access control. These tutorials will guide you through the basic steps of using CipherCloud to secure your data.
Before you begin:
- Make sure you have a CipherCloud account. You can register for a free trial or paid subscription.
- Download and install the CipherCloud Client on your computer.
Basic Tutorials:
- Uploading and Encrypting Files:
- Open the CipherCloud Client.
- Click on the “Upload” button and select the files you want to encrypt.
- Choose a “Cipher Policy” from the available options. This will determine the encryption algorithm and key strength used to protect your data.
- Click “Upload” to start the encryption process. The uploaded files will be stored securely in the CipherCloud platform.
- Sharing Encrypted Files:
- Go to the “My Files” section in the CipherCloud Client.
- Choose the file you want to share and press on the “Share” button.
- Put the email addresses of the people you want to share the file with.
- Optionally, you can set an expiration date for the shared file and/or require recipients to enter a password to access it.
- Click “Share” to send the encrypted file and sharing instructions to the recipients.
- Downloading and Decrypting Files:
- If you are the recipient of a shared file, you will receive an email with instructions on how to access it.
- Click on the link in the email and follow the prompts to download the encrypted file.
- You will need to enter the password provided by the sender to decrypt the file.
- Once decrypted, the file will be saved to your local computer.
- Managing Keys and Access Control:
- CipherCloud uses a key management system to ensure that only authorized users can access your data.
- You can view and manage your keys in the “Key Management” section of the CipherCloud Client.
- You can also set access control policies for your files and folders, specifying who can view, edit, or delete them.
These tutorials provide a basic overview of how to use CipherCloud to secure your data.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

