What is CloudTrail?
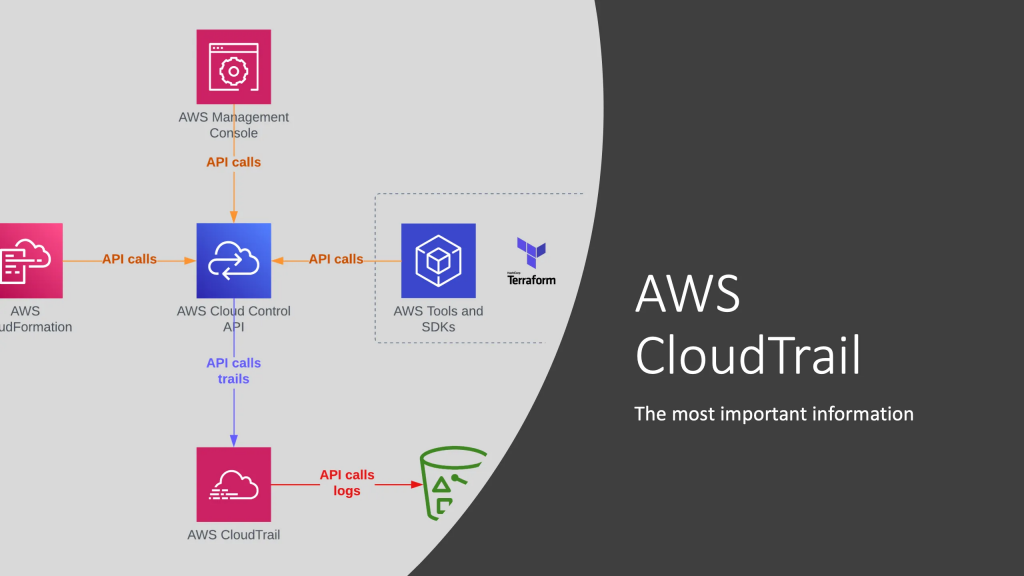
AWS CloudTrail is a service provided by Amazon Web Services (AWS) that records and monitors API calls and activity within an AWS account. It provides detailed event logs and trails that help organizations track user activity, troubleshoot issues, maintain compliance, and enhance security in their AWS environments.
AWS CloudTrail is a fundamental service for maintaining visibility and accountability within AWS environments, enhancing security postures, and ensuring compliance with various regulations and standards. It provides a detailed trail of AWS API activity that can be essential for both security and operational purposes.
Top 10 use cases of CloudTrail:
Here are the top 10 use cases of AWS CloudTrail:
- Security Monitoring: CloudTrail helps organizations monitor AWS accounts for suspicious or unauthorized activities, such as unauthorized access attempts or changes to security groups.
- Auditing and Compliance: It assists in auditing AWS resources and maintaining compliance with industry-specific regulations and standards, such as HIPAA, PCI DSS, and SOC 2.
- Incident Investigation: CloudTrail logs provide a historical record of API calls, allowing organizations to investigate security incidents, breaches, and unauthorized changes.
- Identity and Access Management (IAM) Analysis: Organizations can use CloudTrail logs to analyze IAM activities, including user and role creations, permission changes, and access key usage.
- Resource Changes: CloudTrail records changes to AWS resources, such as EC2 instances, S3 buckets, and RDS databases, making it easier to track modifications and configurations.
- Monitoring and Alerting: CloudTrail can be integrated with AWS CloudWatch to create custom alerts and notifications based on specific API activity or patterns.
- Security Information and Event Management (SIEM) Integration: CloudTrail logs can be sent to SIEM solutions like AWS Security Hub or third-party SIEM tools to correlate AWS activity with other security events.
- Forensics and Root Cause Analysis: In the event of a security incident or operational issue, CloudTrail logs can be invaluable for performing forensics and identifying the root cause.
- User and Administrator Activity Tracking: CloudTrail helps organizations track user and administrator actions, including logins, resource creations, and changes to security policies.
- Operational Insights: CloudTrail provides insights into operational activities, helping organizations understand how resources are being used and optimized.
- Policy Verification: Organizations can use CloudTrail logs to verify that AWS Identity and Access Management (IAM) policies are correctly configured and applied.
- Automation and Scripting Analysis: It helps organizations monitor and track the execution of AWS Lambda functions, AWS Step Functions, and other automated processes.
What are the feature of CloudTrail?
AWS CloudTrail is a service that provides visibility into user and resource activity within your AWS account. It records AWS Management Console actions, AWS CLI commands, and AWS SDK calls, capturing data about who made the call, what service was called, what the request was, and more. Here are the key features of AWS CloudTrail, along with an overview of how it works and its architecture:
Key Features of AWS CloudTrail:
- Logging and Monitoring: CloudTrail logs and monitors all AWS account activity, including API calls made via the AWS Management Console, AWS CLI, AWS SDKs, and other AWS services.
- Comprehensive Event Data: It captures detailed event data, including information about the user or role that made the API call, the time of the call, the source IP address, and more.
- Audit Trail: CloudTrail creates an audit trail of all API activity, providing a historical record that can be used for auditing, compliance, and security investigations.
- Encryption: CloudTrail encrypts log files at rest using Amazon S3 server-side encryption. It also supports data encryption in transit.
- Log File Integrity: It ensures the integrity of log files by digitally signing each log entry. This helps detect tampering or unauthorized access to log data.
- Log File Storage: CloudTrail stores log files in an Amazon S3 bucket, allowing organizations to retain log data for long-term analysis and compliance requirements.
- Integration with CloudWatch: CloudTrail can be integrated with Amazon CloudWatch for real-time monitoring and alerting based on specific events or patterns in the log data.
- Multi-Region Support: It can capture API activity from multiple AWS regions, providing a unified view of account activity across regions.
- Custom Event Filters: Organizations can create custom event filters to focus on specific API calls, actions, or resources of interest.
- Data Insights: CloudTrail can be used in conjunction with AWS services like AWS Athena and AWS QuickSight to gain insights from log data through querying and visualization.
How CloudTrail works and Architecture?
- Data Collection: CloudTrail captures API calls and activity made within your AWS account. This includes actions taken in the AWS Management Console, AWS CLI commands, and AWS SDK calls.
- Log Delivery to S3: The log data is delivered to an Amazon S3 bucket that you specify during CloudTrail setup. The logs are encrypted and stored securely in S3.
- Log Integrity and Signature Verification: CloudTrail signs each log entry to ensure log file integrity. When you access log files, CloudTrail verifies the digital signatures.
- Access Control: Organizations can use AWS Identity and Access Management (IAM) policies to control who can access CloudTrail logs and configure logging.
- Integration with CloudWatch: Organizations can set up CloudWatch Alarms to monitor specific events or patterns in CloudTrail log data. This enables real-time alerting and notifications.
CloudTrail’s architecture involves several key components:
- Event Source: This is the AWS service or resource that generates API events. Examples include Amazon S3, EC2, Lambda, and IAM.
- CloudTrail: The CloudTrail service collects and records API events generated by event sources.
- Log Delivery: Log files are delivered to an Amazon S3 bucket specified during CloudTrail configuration. The logs are encrypted using Amazon S3 server-side encryption.
- AWS Management Console: Users can access CloudTrail log data through the AWS Management Console, AWS CLI, or AWS SDKs for analysis, auditing, and security investigations.
- Integration with CloudWatch: CloudTrail can be integrated with Amazon CloudWatch to enable real-time monitoring and alerting based on specific events.
AWS CloudTrail provides essential visibility into AWS account activity, ensuring accountability, aiding in compliance efforts, and enhancing security by allowing organizations to monitor and analyze user and resource interactions with AWS services.
How to Install CloudTrail?
To install CloudTrail, you need to create a trail. You can do this using the AWS Management Console, the AWS CLI, or the AWS SDK.
Using the AWS Management Console:
- Open the CloudTrail console.
- Choose Create trail.
- Enter a name for your trail.
- Choose the AWS account and Region where you want to create the trail.
- Choose the types of events that you want to log.
- Choose where you want to store your trail logs. You can store them in an S3 bucket, CloudWatch Logs, or Amazon Kinesis.
- Choose whether to encrypt your trail logs.
- Review your settings and then choose Create trail.
Using the AWS CLI:
- Install the AWS CLI.
- Run the following command:
aws cloudtrail create-trail --name <trail-name> --s3-bucket-name <s3-bucket-name>Using the AWS SDK:
- Install the AWS SDK for your programming language.
- Create a new CloudTrail client.
- Call the
create-trail()method.
Once you have created a trail, CloudTrail will begin logging events. You can view your trail logs in the CloudTrail console, CloudWatch Logs, or Amazon Kinesis.
Some additional tips for installing CloudTrail:
- You can create multiple trails. This can be useful if you want to log different types of events to different locations.
- You can enable or disable trails at any time.
- You can configure CloudTrail to retain your trail logs for up to two years.
- You can use CloudTrail Insights to analyze your trail logs and identify security risks.
Basic Tutorials of CloudTrail: Getting Started

The following steps are the basic tutorial of CloudTrail:
1. Create a trail:
- Open the CloudTrail console.
- Choose Create trail.
- Enter a name for your trail.
- Choose the AWS account and Region where you want to create the trail.
- Choose the types of events that you want to log.
- Choose where you want to store your trail logs. You can store them in an S3 bucket, CloudWatch Logs, or Amazon Kinesis.
- Choose whether to encrypt your trail logs.
- Review your settings and then choose Create trail.
2. View your trail logs:
Once you have created a trail, you can view your trail logs in the CloudTrail console, CloudWatch Logs, or Amazon Kinesis.
To view your trail logs in the CloudTrail console:
- Open the CloudTrail console.
- Choose Trails.
- Choose the name of the trail whose logs you want to view.
- Choose Event history.
To view your trail logs in CloudWatch Logs:
- Open the CloudWatch Logs console.
- Choose Log groups.
- Choose the name of the log group where your trail logs are stored.
- Choose Log streams.
- Choose the name of the log stream where your trail logs are stored.
To view your trail logs in Amazon Kinesis:
- Open the Amazon Kinesis console.
- Choose Streams.
- Choose the name of the stream where your trail logs are stored.
3. Analyze your trail logs:
You can use CloudTrail Insights to analyze your trail logs and identify security risks. CloudTrail Insights provides a variety of features, such as:
- Event search: Search for specific events in your trail logs.
- Event filtering: Filter your trail logs by event type, time range, and other criteria.
- Event grouping: Group similar events together to identify patterns.
- Event visualization: Visualize your trail logs to identify trends and anomalies.
To use CloudTrail Insights, open the CloudTrail console and choose Insights.
4. Use your trail logs to comply with regulations:
Many regulations require organizations to log certain types of activity. CloudTrail can help you comply with these regulations by logging all API calls made to your AWS account.
To use CloudTrail to comply with regulations, you can create a trail that logs all events. You can then use CloudTrail Insights to analyze your trail logs and identify events that may be relevant to your compliance requirements.
Additional tips:
- You can create multiple trails. This can be useful if you want to log different types of events to different locations.
- You can enable or disable trails at any time.
- You can configure CloudTrail to retain your trail logs for up to two years.
- You can use CloudTrail Alerts to notify you of specific events in your trail logs.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

