What is Cybereason?

Cybereason is an American cybersecurity technology organization situated in 2012. They provide a comprehensive endpoint protection platform focused on preventing, detecting, and responding to advanced cyber threats. Here’s a breakdown:
What they do:
- Endpoint Protection: Provides antivirus, endpoint detection and response (EDR), and multi-layered defense against modern threats.
- Extended Attack Surface Protection: Secures identities, workspaces, and cloud environments.
- Security Operations Optimization: Offers threat hunting, managed detection and response (MDR), and incident response services.
Key features:
- AI-powered detection: Leverages machine learning and behavioral analysis to identify suspicious activity and prevent attacks.
- Automated response: Takes instant action to contain threats and minimize damage.
- Comprehensive visibility: Provides a unified view of your entire security posture across endpoints, networks, and cloud environments.
- Threat intelligence: Offers insights into the latest cyber threats and attacker tactics.
- Intuitive interface: Makes it easy for security teams to manage and investigate threats.
Top 10 use cases of Cybereason?
Top 10 Use Cases for Cybereason:
- Preventing Zero-day Attacks: Automatically detect and block sophisticated, never-before-seen threats.
- Stopping Ransomware: Quickly identify and contain ransomware outbreaks before they encrypt data.
- Hunting Advanced Threats: Proactively search for hidden threats lurking within your network.
- Incident Response: Rapidly respond to security incidents and minimize damage.
- Endpoint Protection: Secure endpoints against malware, phishing, and other attacks.
- Cloud Security: Extend protection to cloud environments like AWS and Azure.
- Identity Security: Secure user identities and prevent unauthorized access.
- Threat Intelligence: Gain insights into the latest cyber threats and trends.
- EDR & XDR Integration: Integrate with existing security tools for a unified view.
- Managed Security Services: Offload security operations to experienced Cybereason experts.
Overall, Cybereason offers a powerful and versatile security platform for organizations of all sizes. Whether you’re looking to prevent zero-day attacks, stop ransomware, or improve your overall security posture, Cybereason can help.
What are the feature of Cybereason?
Cybereason boasts a range of impressive features designed to combat modern cyber threats. Following is a breakdown of some key highlights:
1. Multi-layered Endpoint Protection:
- NGAV (Next-Generation Anti-Virus): Employs multiple anti-malware engines and behavior analysis to detect and block known and unknown threats, including ransomware, zero-day attacks, and fileless malware.
- EDR (Endpoint Detection and Response): Provides real-time visibility into endpoint activity, identifying suspicious behavior and enabling rapid response to potential threats.
- Endpoint Controls: Granular control over USB devices, network connections, and application execution to harden endpoints and reduce the attack surface.
- Anti-Exploit: Employs virtual patching and memory protection techniques to prevent attackers from exploiting software vulnerabilities.
2. Extended Attack Surface Protection:
- Identity Security: Protects against identity-based attacks by securing user access and credentials.
- Workspace Security: Secures endpoints regardless of location or device, including desktops, laptops, mobile devices, and cloud workstations.
- Security Command Center: Provides a unified view of all security events across the entire IT environment.
3. Security Operations Optimization:
- Threat Hunting: Proactive approach to uncover hidden threats through advanced analytics and human expertise.
- MDR (Managed Detection and Response): 24/7 threat monitoring and response by Cybereason security experts, freeing up internal resources.
- Incident Response: Rapid and effective response to security incidents to minimize damage and restore operations.
- Digital Forensics & IR: Investigates security incidents to identify the root cause and prevent future occurrences.
4. Additional Features:
- Machine Learning & AI: Cybereason leverages advanced AI and machine learning algorithms to power its detection and response capabilities.
- Automated Remediation: Automates threat response actions to neutralize threats quicker and minimize human intervention.
- Intuitive UI & UX: User-friendly interface allows security teams to easily manage and investigate threats.
- Threat Intelligence: Provides access to Cybereason’s rich repository of threat intelligence to stay ahead of attackers.
Overall, Cybereason’s features stand out for their comprehensiveness, automation capabilities, and focus on AI-powered defense. They offer a robust solution for organizations seeking to protect against today’s sophisticated cyber threats.
How Cybereason works and Architecture?
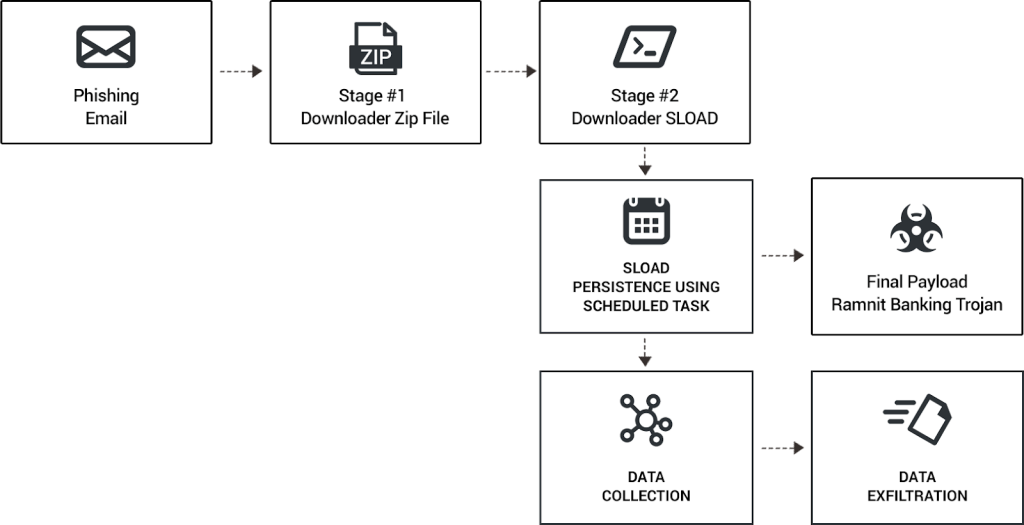
Cybereason’s capabilities are powered by a sophisticated architecture designed for efficient threat detection, response, and containment. Following is a breakdown of how it works:
1. Data collection and ingestion:
- Agents installed on endpoints and other devices continuously collect security data (logs, event data, system changes, file changes).
- Cybereason Connect acts as an intermediary, collecting and pre-processing data from various sources before sending it to the platform.
2. Analysis and detection:
- The Cybereason Defense Platform performs real-time analysis of the ingested data using multiple layers of defense:
- Next-generation antivirus: Scans for known malware signatures and suspicious file behavior.
- Behavior-based analytics: Identifies abnormal activity indicating potential threats, even zero-day attacks.
- Machine learning algorithms: Analyze patterns and relationships across all data to uncover sophisticated threats.
- Global Threat Intelligence: Continuously updates the platform with the latest threat information from trusted sources.
3. Visualization and investigation:
- The platform presents a unified view of security events through an intuitive dashboard and timeline.
- Analysts can investigate suspected threats in detail, examining related events, files, and network activity across all affected devices.
4. Response and remediation:
- Cybereason offers automated and manual response options:
- Automated actions: Quarantines infected devices, blocks malicious domains and IPs, and terminates suspicious processes.
- Manual actions: Security teams can take further actions based on their investigation, such as isolating specific endpoints, rolling back changes, or contacting affected users.
5. Continuous improvement:
- Cybereason automatically learns and adapts based on new data and emerging threats.
- Threat intelligence updates and improved machine learning models continuously enhance the platform’s detection and response capabilities.
Key architectural components:
- Agents: Lightweight agents residing on endpoints and devices perform local data collection and initial threat analysis.
- Cybereason Connect: Acts as a gateway for data intake and normalization, preparing data for ingestion by the platform.
- Detection Server: Performs real-time analysis of data using machine learning, threat intelligence, and behavioral algorithms.
- Central Console: Provides a unified view of security events, threat investigations, and response options.
- Global Threat Intelligence Server: Aggregates and analyzes threat data from various sources to keep the platform updated on the latest threats.
Overall, Cybereason’s architecture combines real-time data analysis, advanced threat detection methods, and intuitive visualization tools to empower security teams to effectively prevent, detect, and respond to cyber threats.
How to Install Cybereason it?
Installing Cybereason requires access to the Cybereason Defense Platform and administrative privileges on the target endpoints. Here’s a general guide:
1. Prepare your environment:
- Ensure you have a valid account and access to the Cybereason Defense Platform.
- Download the sensor installation file(s) from the platform using the System > Overview > Download Cybereason Installers section.
- Choose the appropriate platform (Windows, macOS, Linux) and sensor group (if applicable).
2. Install the sensor on a Windows device:
- Run the downloaded
.msifile. - Accept the license agreement and choose the installation directory (default recommended).
- Provide administrative credentials if prompted.
- Use the on-screen instructions and accomplish the installation.
- Restart the computer.
3. Install the sensor on a macOS device:
- Run the downloaded
.pkgfile. - Permit to the license agreement and use the on-screen instructions.
- Put your administrator password during the installation process.
- The sensor will automatically start running in the background.
4. Install the sensor on a Linux device:
- Use the command line to install the downloaded
.debor.rpmfile depending on your Linux distribution. - Follow the on-screen instructions or refer to the Cybereason documentation for specific Linux installation commands.
- Verify the sensor is running using the
cybereason-sensor statuscommand.
5. Verify the installation:
- Access the Cybereason Defense Platform and navigate to the System > Sensors section.
- The installed sensor should now be visible, showing its online status and version information.
These are general steps, and specific instructions might vary depending on your organization’s configuration and desired settings.
Basic Tutorials of Cybereason: Getting Started

Cybereason offers a robust endpoint protection platform (EPP) with advanced features to combat modern cyber threats. Here are some step-by-step basic tutorials to get you started:
1. Installing the Cybereason Sensor:
Requirements:
- Valid Cybereason Defense Platform account
- Administrative privileges on target endpoints
Steps:
- Download the Sensor: Log in to the Cybereason Defense Platform and navigate to System > Overview > Download Cybereason Installers. Choose the platform (Windows, macOS, Linux) and sensor group (if applicable).
- Install on Windows: Run the downloaded
.msifile. Accept the license agreement and choose the installation directory. Provide administrative credentials if prompted. Follow the on-screen instructions and restart the computer. - Install on macOS: Run the downloaded
.pkgfile. Permit to the license agreement and apply the on-screen instructions. Enter your administrator password during installation. The sensor will automatically start running. - Install on Linux: Use the command line to install the downloaded
.debor.rpmfile based on your distribution. Follow the on-screen instructions or refer to Cybereason documentation for specific commands. Verify the sensor is running usingcybereason-sensor status.
2. Exploring the Cybereason Dashboard:
Once the sensor is installed, access the Cybereason Defense Platform dashboard. Here’s a quick overview:
- Navigation bar: Provides access to key functionalities like System, Events, Investigations, Policies, Reports, Settings.
- Overview panel: Displays key security metrics like active detections, blocked processes, endpoint health, and vulnerability trends.
- Widgets: Customizable sections offering deeper insights into specific areas like threats, endpoints, investigations, and reports. Drag and drop to personalize your dashboard layout.
3. Basic Threat Hunting:
Cybereason’s Investigate tab empowers you to proactively search for suspicious activity.
- Go to Investigate: Click the Investigate tab in the navigation bar.
- Build a Search: In the search bar, enter keywords, indicators of compromise (IOCs), or filter by specific parameters like device name, process name, or source IP address.
- Explore Results: The search results display events matching your criteria. Analyze event details, timelines, and associated files for further investigation.
- Take Action: If you find suspicious activity, you can take actions like isolating the endpoint, blocking a file, or initiating an investigation workflow.
4. Managing Endpoint Policies:
Policies define security configurations and actions for your endpoints.
- Go to Policies: Click the Policies tab in the navigation bar.
- Browse Existing Policies: Review pre-defined policies or create custom ones by clicking New Policy.
- Configure Settings: Define settings like antivirus scanning, application control, device control, and response actions.
- Assign Policies to Groups: Select target endpoint groups for each policy application.
These are basic tutorials to get you familiar with Cybereason’s core functionalities. As you progress, explore the platform’s advanced features and leverage its full potential to secure your endpoints against evolving cyber threats.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

