What is CyberSponse?

CyberSponse is a security orchestration, automation, and response (SOAR) platform designed to help organizations streamline their security operations and incident response processes. It provides a range of features and capabilities to enhance security incident management and response.
CyberSponse’s capabilities are designed to enhance the efficiency and effectiveness of security operations teams by automating repetitive tasks, accelerating incident response times, and providing a unified platform for incident management and collaboration.
Top 10 use cases of CyberSponse:
Here are the top 10 use cases of CyberSponse:
- Incident Triage and Enrichment: Quickly assess incoming security alerts and incidents, enrich them with contextual information, and prioritize them based on their severity and impact.
- Playbook Automation: Create and customize playbooks that define automated workflows for incident response. Playbooks guide analysts through response processes and automate repetitive tasks.
- Incident Workflow Management: Centralize incident tracking, management, and collaboration to ensure that security incidents are addressed promptly and effectively.
- Alert Management: Collect and consolidate alerts from multiple security tools and sources, reducing alert fatigue and facilitating coordinated responses.
- Orchestration of Security Tools: Orchestrate actions and responses across a wide range of security tools, technologies, and systems to ensure a coordinated incident response.
- Threat Intelligence Integration: Integrate with threat intelligence feeds and platforms to automatically correlate and enrich incident data with relevant threat context and indicators.
- Automated Response: Automate incident response actions, allowing predefined tasks and workflows to be executed in response to security incidents.
- Custom Integrations: Create custom integrations and connectors to integrate CyberSponse with specific security tools and systems, ensuring compatibility with existing infrastructure.
- Machine Learning and AI: Leverage machine learning and artificial intelligence to assist with threat detection, decision-making, and anomaly detection within incident response workflows.
- Incident Reporting and Documentation: Generate incident reports and maintain detailed records of incident response activities for compliance, analysis, and post-incident review.
- Case Management: Group related incidents into cases, track investigation progress, and maintain detailed incident records for comprehensive incident management.
- User and Entity Behavior Analytics (UEBA) Integration: Integrate with UEBA solutions to monitor and detect anomalous user and entity behaviors.
What are the feature of CyberSponse?
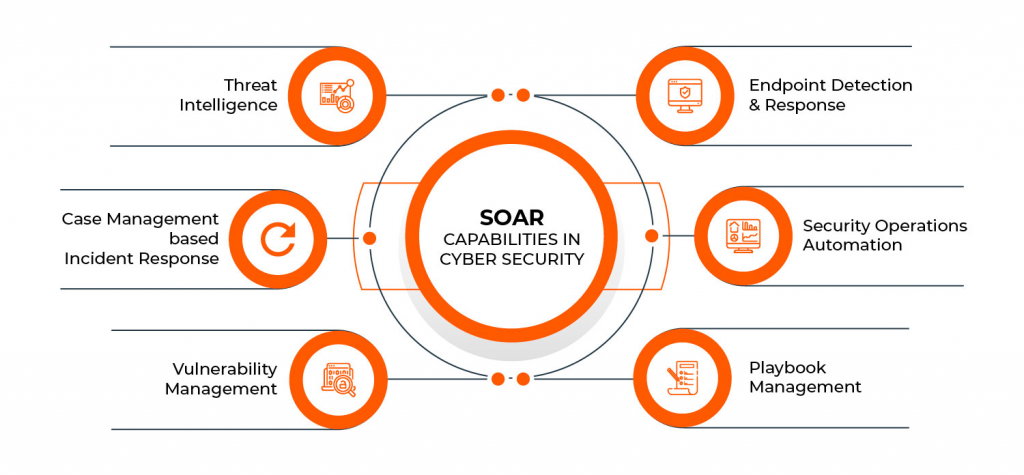
CyberSponse is a security orchestration, automation, and response (SOAR) platform with a range of features and capabilities designed to enhance security incident management and response. Here are the key features of CyberSponse:
1. Incident Triage and Enrichment:
- CyberSponse allows security teams to quickly assess the severity and context of incoming incidents by aggregating and enriching data from various sources.
- It provides contextual information, such as threat intelligence feeds, asset information, and historical data, to aid in incident prioritization.
2. Playbook Automation:
- Users can create custom playbooks that define step-by-step workflows for automating incident response processes.
- Playbooks can include a combination of automated actions, decision points, and manual tasks.
3. Incident Workflow Management:
- The platform offers a centralized incident management interface for tracking, managing, and documenting incidents throughout their lifecycle.
- Workflow management tools help ensure that incidents are addressed efficiently and consistently.
4. Alert Management:
- CyberSponse centralizes alerts from various security tools and sources, reducing alert fatigue and providing a unified view of security incidents.
- It supports the deduplication and correlation of alerts to avoid redundancy.
5. Orchestration of Security Tools:
- The platform orchestrates actions and responses across a wide range of security tools, systems, and technologies, promoting coordination in incident response efforts.
- Integration with third-party security solutions is a fundamental feature.
6. Threat Intelligence Integration:
- CyberSponse integrates with threat intelligence feeds and platforms to automatically enrich incident data with relevant threat context, indicators of compromise (IOCs), and known attack patterns.
7. Automated Response:
- Security teams can automate incident response actions, including containment, remediation, and notification, based on predefined playbooks and decision logic.
8. Custom Integrations:
- Users can create custom integrations and connectors to link CyberSponse with their specific security tools, ensuring compatibility with their existing technology stack.
9. Machine Learning and AI:
- The platform leverages machine learning and artificial intelligence capabilities to assist with threat detection, decision-making, and anomaly detection within incident response workflows.
10. Incident Reporting and Documentation:
– CyberSponse provides tools for generating detailed incident reports and maintaining comprehensive records of incident response activities.
– Documentation features support compliance and post-incident analysis.
11. Case Management:
– Group related incidents into cases, allowing for better organization, tracking, and analysis of incidents with common attributes or characteristics.
How CyberSponse works and Architecture?
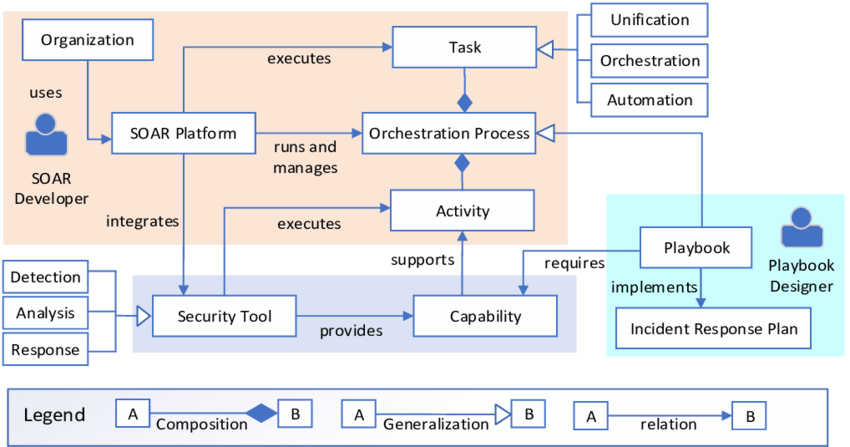
CyberSponse’s architecture and workflow can be summarized as follows:
Components:
- CyberSponse Core: The central component manages playbooks, integrations, and incident data.
- Connectors: Connectors are pre-built integrations with various security tools, technologies, and services, allowing users to connect CyberSponse with their existing security infrastructure.
- Playbooks: Playbooks define the workflows and actions to be taken in response to security incidents. They can be created, customized, and executed based on specific use cases and needs.
Workflow:
- Alert Ingestion: CyberSponse ingests alerts and incidents from multiple sources, creating incident records in its central platform.
- Playbook Execution: Playbooks are executed in response to incidents, orchestrating actions and responses across connected security tools and systems.
- Automation: Automated tasks within playbooks help triage, investigate, and respond to incidents, reducing manual effort.
- Human Decision Points: Playbooks can include human decision points where analysts can make critical decisions or provide additional input.
- Reporting and Documentation: CyberSponse offers reporting and documentation features to create detailed incident reports and maintain a historical record of incidents.
- Integration: The platform integrates seamlessly with security tools, threat intelligence feeds, and external data sources to enrich and automate incident response.
CyberSponse’s architecture and features are designed to enhance incident response capabilities by automating repetitive tasks, improving the coordination of actions across security tools, and providing a unified platform for incident management and collaboration.
How to Install CyberSponse?
To install CyberSponse, you must first have a Google Cloud Platform (GCP) project. Once you have a GCP project, you can follow these steps to install CyberSponse:
- Go to the CyberSponse website and click on the “Get Started” button.
- Press on the “Create a new account” button.
- Enter your GCP project ID and click on the “Next” button.
- Select the CyberSponse features that you want to install and click on the “Next” button.
- Review the installation details and click on the “Install” button.
CyberSponse will be installed in your GCP project. You can access CyberSponse by going to the CyberSponse website: https://cybersponse.com/ and clicking on the “Login” button.
Some additional tips for installing CyberSponse:
- Make sure that you have the required permissions to create and manage GCP projects.
- If you are installing CyberSponse in a production environment, it is recommended to create a test environment first to test the installation process.
- You can also contact CyberSponse support for assistance with installing CyberSponse.
Basic Tutorials of CyberSponse: Getting Started

The following steps are the Basic Tutorials of CyberSponse:
1. Create a new incident
- Log in to CyberSponse.
- Press on the “Create New Incident” button.
- Enter the incident details, such as the name, description, and type.
- Click on the “Submit” button.
2. Assign the incident to a team
- Open the incident record.
- Click on the “Team” tab.
- Select the team that you want to assign the incident to.
- Click on the “Submit” button.
3. Investigate the incident
The incident team will investigate the incident to determine the root cause and impact. This may involve collecting logs, interviewing witnesses, and analyzing the affected systems. The incident team can use CyberSponse’s incident investigation features, such as log analysis, intrusion detection, and forensic analysis.
4. Remediate the incident
Once the incident team has identified the root cause of the incident, they will take steps to remediate it. This may involve patching vulnerabilities, removing malware, or restoring systems from backups. The incident team can use CyberSponse’s incident response orchestration and automation features to automate common incident response tasks.
5. Recover from the incident
Once the incident has been remediated, the incident team will help the organization to recover from the incident and restore normal operations. This may involve communicating with affected stakeholders, implementing additional security measures, and restoring business processes.
Additional tips for using CyberSponse:
- Use incident playbooks to provide step-by-step instructions on how to respond to common security incidents.
- Use reporting and analytics tools to track your incident response performance and identify areas for improvement.
- Use threat intelligence and collaboration tools to share information about security incidents with other organizations.
Use case Example:
An organization is alerted to a potential malware infection on one of its servers. The organization’s security team uses CyberSponse to create a new incident and assign it to the incident response team. The incident response team uses CyberSponse to investigate the incident and determine that the server has been infected with ransomware. The incident response team uses CyberSponse to remediate the incident, such as isolating the infected server and restoring the server from a backup. The incident response team also works with the organization to implement additional security measures to prevent future ransomware infections.
CyberSponse is a powerful tool that can help organizations to improve their incident response process. By following the steps in this tutorial, you can learn how to use CyberSponse to create, manage, and respond to security incidents.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

