What is DeployHub?

DeployHub is a software supply chain security platform designed to address the challenges of securing and managing open-source and third-party software within your software applications.
DeployHub works by gathering and aggregating critical data about the components (e.g., libraries, frameworks) used in your applications. This includes information like:
- Provenance: Origin and history of the component.
- SBOMs: Software Bill of Materials, detailing all dependencies.
- CVEs: Known vulnerabilities associated with the component.
- Versions: Information about different versions and their security risks.
- Inventory: Where the components are used within your applications and deployed environments.
By centralizing this data, DeployHub provides insights and capabilities for:
- Identifying security risks: Proactively scan for vulnerabilities and dependencies within your software supply chain.
- Managing open-source usage: Track and assess the risks associated with open-source components you use.
- Ensuring compliance: Meet regulatory requirements like Executive Order 14028 for generating application-level SBOMs.
- Optimizing deployments: Improve security and manage vulnerabilities across entire development and deployment pipelines.
- Automating tasks: Streamline vulnerability detection, patching, and remediation processes.
Top 10 use cases of DeployHub?
Top 10 Use Cases of DeployHub:
- Secure software development: Integrate DeployHub into your CI/CD pipeline to identify and address security risks early in the development process.
- Minimize open-source risk: Gain visibility into potential vulnerabilities within commonly used open-source libraries and frameworks.
- Meet compliance requirements: Generate Application-Level SBOMs (Software Bill of Materials) to comply with regulations like Executive Order 14028.
- Track version vulnerabilities: Stay informed about newly discovered vulnerabilities and their impact on your software versions.
- Improve incident response: Quickly identify affected components and implement remediation actions when security incidents occur.
- Optimize patch management: Prioritize patching efforts based on risk and impact of vulnerabilities within your applications.
- Automate security checks: Set up automated workflows for vulnerability scanning, alerting, and patch management.
- Enhance governance and control: Define policies and restrictions around open-source component usage for better control within your organization.
- Improve collaboration: Share security insights and knowledge across development, security, and operations teams.
- Reduce attack surface: Proactively address vulnerabilities and minimize the exposure of your applications to potential attacks.
These are just some of the many potential use cases for DeployHub. Its specific value will depend on your organization’s needs and security posture.
What are the feature of DeployHub?
DeployHub empowers you to manage and secure your software supply chain through a rich set of features:
Vulnerability Management:
- Comprehensive scanning: Scans across various sources (repositories, containers, binaries) for vulnerabilities in open-source and third-party components.
- Prioritization and scoring: Analyzes and scores vulnerabilities based on severity, exploitability, and impact, aiding in prioritizing remediation efforts.
- Continuous monitoring: Tracks newly discovered vulnerabilities and their relevance to your used components, keeping you informed.
- Vulnerability intelligence: Provides insights into exploitability, affected versions, and available patches.
Open-Source Management:
- Inventory and tracking: Creates an inventory of all open-source components used in your applications and tracks their versions across environments.
- License compliance: Helps ensure compliance with open-source license terms and conditions.
- Risk assessment: Analyzes the security risks associated with specific open-source components based on factors like license type, development activity, and vulnerability history.
- Alternative suggestions: Recommends less risky alternatives for identified high-risk open-source components.
Software Bill of Materials (SBOM) Generation:
- Automatic SBOM generation: Generates comprehensive SBOMs (Software Bill of Materials) for your applications, detailing all dependencies and their versions.
- Compliance support: Assists in meeting SBOM generation requirements for regulations like Executive Order 14028.
- Customization: Offers options to tailor SBOM content and format to your specific needs.
- Integration with other tools: Enables integration with various security and compliance tools for seamless workflows.
Deployment Pipeline Integration:
- CI/CD integration: Integrates with CI/CD pipelines to perform vulnerability scanning and risk assessment as part of the development process.
- Automated workflows: Enables triggering automated actions based on scan results, such as alerting, blocking deployments, or initiating remediation.
- Version control: Provides visibility into vulnerabilities within different versions of components, aiding in informed deployment decisions.
- Patch management: Assists in identifying and prioritizing affected components for patching to address vulnerabilities.
Additional Features:
- Customizable dashboards and reports: Visualize scan results, track trends, and generate reports for stakeholders.
- Role-based access control: Manage user access and permissions for enhanced security.
- API access: Enables programmatic interaction with DeployHub for automation and integrations.
- Community and support: Offers access to community resources and dedicated support for users.
Note: Specific features and functionalities might vary depending on your chosen plan and deployment options (cloud, on-premises).
How DeployHub works and Architecture?
DeployHub helps you secure your software supply chain by providing visibility and insights into the components used in your applications. Here’s a breakdown of its overall workings and architecture:
Workflow:
- Data Collection:
- You integrate DeployHub with various sources like Git repositories, container registries, and deployment environments.
- DeployHub scans these sources to identify components (libraries, frameworks) used in your applications.
- It gathers information about each component, including:
- Provenance: Origin and history of the component.
- SBOMs: Software Bill of Materials, detailing all dependencies.
- CVEs: Known vulnerabilities associated with the component.
- Versions: Information about different versions and their security risks.
- Inventory: Where the components are used within your applications and deployed environments.
- Analysis and Processing:
- DeployHub processes the collected data to:
- Identify potential security risks based on vulnerabilities, license conflicts, and other factors.
- Score and prioritize risks based on their severity and impact.
- Track component versions and identify outdated or vulnerable ones.
- Generate SBOMs based on your application composition.
- DeployHub processes the collected data to:
- Actions and Alerting:
- Based on the analysis, DeployHub can:
- Trigger alerts for critical vulnerabilities or security risks.
- Provide recommendations for remediation actions, like patching or upgrading components.
- Integrate with your CI/CD pipelines to automatically block insecure deployments.
- Generate reports and dashboards for tracking security posture and trends.
- Based on the analysis, DeployHub can:
Architecture:
- Data Sources: Git repositories, container registries, build systems, deployment environments.
- Ingestion Layer: Collects and processes data from various sources.
- Security Hub: Analyzes data, identifies risks, and generates insights.
- Integrations: Connects with CI/CD pipelines, vulnerability databases, and other tools.
- User Interface: Provides access to reports, dashboards, and configuration options.
Key Concepts:
- Declarative Configuration: You define rules and policies for security checks and notifications.
- Continuous Monitoring: DeployHub continuously scans and analyzes your software supply chain.
- Risk-Based Prioritization: Focuses on addressing the most critical vulnerabilities first.
- Automation: Integrates with your existing workflows for seamless remediation.
Additional Notes:
- DeployHub offers various deployment options: cloud-based, on-premises, or hybrid.
- The specific architecture and functionalities might vary depending on your chosen deployment model.
How to Install DeployHub it?
So, let’s come to the point of DeployHub Pro installation. I can provide specific instructions based on your preferred installation method:
1. Installation on your own infrastructure:
a) On a Kubernetes cluster:
- Prepare your Kubernetes cluster: Ensure your cluster meets the system requirements specified on the DeployHub official site.
- Choose your installation method: You can either use Helm charts or the operator pattern.
- Helm charts: Follow the steps of artifacthub official site.
- Operator pattern: See the DeployHub official site for specific instructions.
- Configure DeployHub: Set up environment variables, user accounts, and other configurations as described in the documentation.
b) On a server:
- Choose your operating system: DeployHub Pro supports Ubuntu and CentOS/RHEL.
- Install prerequisites: Follow the platform-specific instructions on the site.
- Download and install: Get the installer from the DeployHub website and follow the installation steps.
- Configure DeployHub: Similar to the Kubernetes installation, set up environment variables, users, and other configurations.
2. Installation on a managed cloud platform:
DeployHub Pro offers pre-built packages for AWS, Azure, and GCP. These packages simplify the installation process:
- AWS: Follow the DeployHub official guide.
- Azure: Choose DeployHub site for better Instructions.
- GCP: See the DeployHub official site for specific steps
Note: These are general instructions, and the specific steps might vary depending on your environment and chosen option.
Basic Tutorials of DeployHub: Getting Started
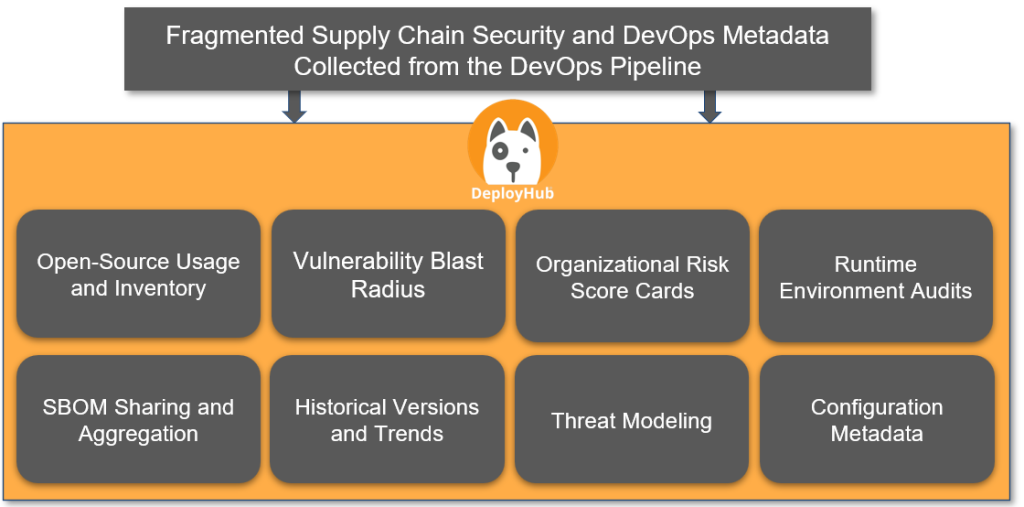
So, let’s begin with the step-by-step basic tutorials of DeployHub in that I’ll provide tutorials covering some fundamental aspects of DeployHub:
1. Creating and Setting Up a Project:
- Login: Access the DeployHub web interface and log in with your credentials.
- Create a Project: Press on the “Projects” tab and then “Generate Project.”
- Provide Project Details: Enter a project name, description, and optionally select a template.
- Configure Version Control: Link your project to your Git repository by providing the URL and credentials.
- Save and Access: Click “Save” to create the project, and it will be listed in the Projects tab.
2. Building and Configuring Pipelines:
- Open Project: Navigate to your project in the Projects tab.
- Create Pipeline: Click “Pipelines” and then “Create Pipeline.”
- Choose Pipeline Type: Select a template or create a custom pipeline. Common options include Basic CI/CD or Multi-Stage Pipelines.
- Add Stages: Define stages in your pipeline, such as “Build,” “Test,” and “Deploy.”
- Configure Tasks: Within each stage, define tasks like code checkout, building, running tests, and deploying to environments.
- Specify Artifacts: Choose which artifacts (e.g., built files) to pass between stages.
- Trigger Conditions: Set up triggers for automated pipeline execution (e.g., on code push, schedule).
- Save and Run: Save the pipeline configuration and optionally initiate a manual run.
3. Deploying Applications to Environments:
- Open Project: Access your project and navigate to the “Environments” tab.
- Create Environment: Click “Create Environment” and define name, server details, and deployment options.
- Link Pipeline: Select the pipeline you want to deploy to this environment.
- Deployment Strategy: Choose the deployment strategy (e.g., manual, automatic).
- Save and Deploy: Save the environment configuration and initiate a deployment if desired.
4. Managing Approvals and Workflows:
- Project Settings: Go to your project’s settings and navigate to the “Workflows” tab.
- Define Workflows: Create approval workflows for specific stages or deployments.
- Assign Approvers: Choose individuals or groups who need to approve before proceeding.
- Configure Conditions: Set conditions for when approvals are required (e.g., specific environments).
- Save and Activate: Save the workflow and activate it for your project.
5. Utilizing Features like Rollback and Audit Trails:
- Rollbacks: In the deployment history, locate the version you want to roll back to.
- Initiate Rollback: Click the “Rollback” button and confirm the action.
- Audit Trails: Access the “Audits” tab in your project to view historical events and user actions.
- Filter and Search: Filter audit trails by date, user, event type, or keyword.
These are basic steps, and specific functionalities might vary depending on your DeployHub version and configuration.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

