What is Digital Guardian?

Digital Guardian is a leading provider of data loss prevention (DLP) and data protection solutions. It helps organizations secure sensitive data wherever it resides, on endpoints, in the cloud, or on the network. Think of it as a vigilant watchdog, constantly monitoring and guarding your valuable information against unauthorized access, theft, or leakage.
Here’s a quick breakdown of Digital Guardian’s key features:
- Data discovery and classification: Identifies and classifies sensitive data across your entire IT infrastructure.
- Data loss prevention: Prevents unauthorized data transfers through various channels like email, web browsing, and file sharing.
- Threat detection and response: Alerts you to suspicious activities that might indicate data breaches or leaks.
- Endpoint protection: Secures data on laptops, desktops, and mobile devices.
- Cloud security: Extends data protection to cloud-based applications and storage.
- Compliance support: Helps organizations comply with data privacy regulations like GDPR and HIPAA.
Top 10 use cases of Digital Guardian?
Now, let’s dive into the top 10 use cases for Digital Guardian:
1. Preventing insider threats: Malicious or accidental data leaks by employees can be a major risk. Digital Guardian helps identify suspicious user behavior and block unauthorized data transfers.
2. Securing sensitive data: Financial records, customer information, intellectual property – Digital Guardian protects your most valuable data from unauthorized access and exfiltration.
3. Cloud data protection: Moving data to the cloud doesn’t mean sacrificing security. Digital Guardian extends its protection to cloud applications and storage platforms.
4. Compliance with data privacy regulations: GDPR, HIPAA, and other regulations require strict data protection measures. Digital Guardian helps organizations comply with these regulations and avoid hefty fines.
5. Endpoint data loss prevention: Data breaches often happen through endpoints like laptops and mobile devices. Digital Guardian secures data on these devices and prevents unauthorized transfers.
6. Protecting intellectual property: Trade secrets, designs, and other confidential information are vital for businesses. Digital Guardian helps prevent unauthorized access and theft of your intellectual property.
7. Secure collaboration: Sharing data with partners and customers is crucial, but it also introduces risks. Digital Guardian helps ensure secure collaboration without compromising data security.
8. Incident investigation and response: Data breaches happen, but how you respond is key. Digital Guardian helps investigate incidents quickly and effectively to minimize damage and prevent future occurrences.
9. Data encryption: Encrypting sensitive data at rest and in transit adds an extra layer of security. Digital Guardian offers various encryption options to meet your specific needs.
10. Data visibility and reporting: Gaining insights into your data usage and potential risks is crucial for effective data protection. Digital Guardian provides comprehensive reports and dashboards to help you stay informed.
By implementing Digital Guardian, organizations can gain peace of mind knowing their valuable data is protected against a wide range of threats.
What are the feature of Digital Guardian?
Digital Guardian is a leading data protection platform that safeguards sensitive information across your entire IT infrastructure. It acts like a vigilant watchtower, constantly monitoring and guarding your valuable data against all sorts of threats. Here’s a closer look at the key features that make Digital Guardian a powerful data security solution:
1. Deep Data Discovery and Classification:
- Uncover the hidden gems: Digital Guardian scans your endpoints, network, and cloud environments to identify and classify all sensitive data, whether it’s in structured files like spreadsheets or unstructured formats like emails and chat logs.
2. Granular Data Loss Prevention (DLP):
- Build a security fence: Define customized policies to protect your data from unauthorized access, exfiltration, and leakage through various channels like email, web browsing, file sharing, and even printing.
3. Advanced Threat Detection and Response:
- Be the first to know: Digital Guardian analyzes user activity and data movement to detect suspicious behavior that might indicate data breaches, insider threats, or malware infections.
4. Comprehensive Endpoint Protection:
- Secure every device: Guard sensitive data on laptops, desktops, and mobile devices with encryption, endpoint DLP, and granular access controls.
5. Robust Cloud Data Security:
- Extend your fortress to the cloud: Digital Guardian seamlessly integrates with popular cloud platforms like AWS, Microsoft Azure, and Google Cloud Platform to protect your data in the cloud.
6. Compliance Made Easy:
- Stay ahead of the curve: Digital Guardian helps you comply with data privacy regulations like GDPR, HIPAA, and PCI DSS by providing pre-built compliance policies and reports.
7. Enhanced User Experience:
- Security without sacrifice: Digital Guardian’s user-friendly interface and automated workflows ensure data protection without hindering user productivity.
8. Scalability and Flexibility:
- Adapt to your needs: Digital Guardian is highly scalable and adaptable, catering to small businesses, large enterprises, and everything in between.
9. Powerful Analytics and Reporting:
- Gain insights, make informed decisions: Get real-time visibility into your data security posture with detailed reports and dashboards that track user activity, data transfers, and potential threats.
10. Continuous Innovation:
- Stay ahead of the game: Digital Guardian is constantly evolving with new features, integrations, and threat detection capabilities to keep your data secure against the latest cyber threats.
With these powerful features, Digital Guardian gives you peace of mind knowing your data is protected wherever it lives. Whether you’re a small business or a large enterprise, Digital Guardian can help you secure your sensitive information and comply with data privacy regulations.
How Digital Guardian works and Architecture?
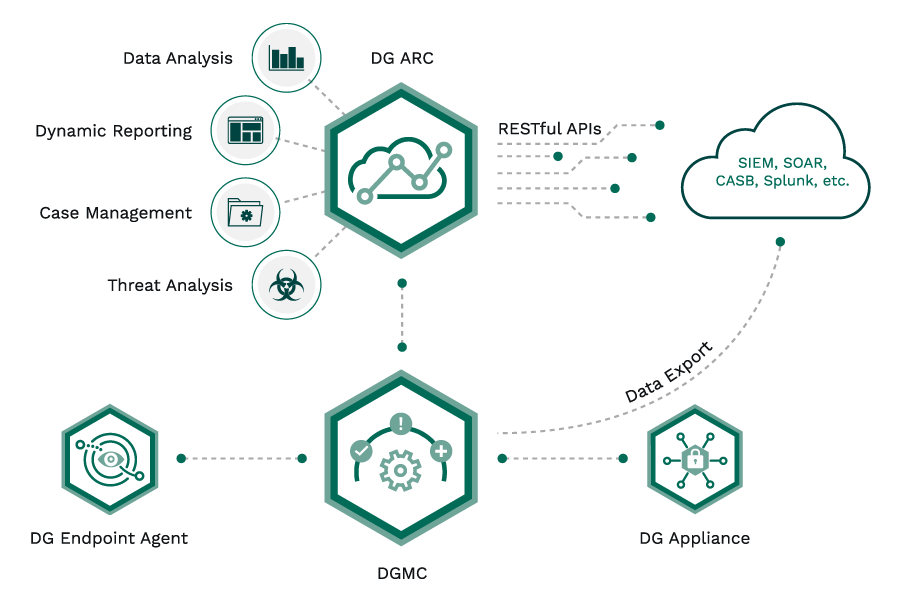
Digital Guardian’s impressive data protection capabilities stem from a carefully designed architecture and intelligent workflows. Following is a breakdown of how it works:
1. Data Discovery and Classification:
- Agents and sensors: Installed on endpoints, network devices, and cloud platforms, these components scan data at rest and in transit, identifying sensitive information based on pre-defined policies and algorithms.
- Data fingerprinting: Advanced algorithms analyze file content and metadata to identify specific data types like personally identifiable information (PII), financial data, intellectual property, etc.
- Machine learning: Continuously learns from new data patterns and user behavior to improve accuracy and efficiency in identifying sensitive data.
2. Data Loss Prevention (DLP):
- Real-time monitoring: Digital Guardian tracks user activity and data movement across your network, constantly vigilantly watching for potential violations of your DLP policies.
- Content inspection: Analyzes the content of emails, messages, and files in transit, looking for keywords, patterns, and indicators of sensitive data being transferred unauthorizedly.
- Preventive actions: Based on your policies, Digital Guardian can block data transfers, encrypt files, or alert administrators to suspicious activity.
3. Threat Detection and Response:
- User and entity behavior analytics (UEBA): Analyzes user activity logs and other data points to detect anomalies and suspicious patterns that might indicate malicious intent or insider threats.
- Advanced malware detection: Utilizes various techniques like sandboxing and machine learning to identify and stop malware infections before they harm your data.
- Incident response: Provides tools and workflows to investigate security incidents, contain threats, and minimize damage.
4. Endpoint Protection:
- Data encryption: Encrypts sensitive data at rest and in transit to prevent unauthorized access even if devices are lost or stolen.
- Application control: Blocks access to unauthorized applications that could be used to exfiltrate data.
- Granular access controls: Defines who can access specific data on endpoints and what actions they can perform.
5. Cloud Data Security:
- Cloud workload protection platform (CWPP): Integrates with major cloud platforms to extend DLP controls and threat detection capabilities to cloud environments.
- Data encryption in the cloud: Encrypts sensitive data stored in the cloud to ensure its security even from cloud provider access.
- Cloud data leak prevention: Monitors cloud activity for unauthorized data transfers and potential breaches.
Overall Architecture:
- Client-server architecture: Agents and sensors on endpoints and network devices report to a central server that manages data security policies, processes data, and triggers actions.
- Modular design: Different components like DLP, threat detection, and endpoint protection can be deployed independently or together as needed for a tailor-made security solution.
- API integrations: Integrates with other security tools and data platforms to provide a holistic view of your security posture.
By combining comprehensive data discovery, powerful DLP, proactive threat detection, and robust endpoint protection, Digital Guardian offers a multi-layered approach to data security. Its modular architecture and intelligent workflows provide you with the flexibility and scalability to adapt to your specific needs and data security challenges.
How to Install Digital Guardian it?
Installing Digital Guardian involves several steps and can vary depending on your specific environment and desired implementation type. Following is a general overview of the process:
1. System Requirements:
- Ensure your environment meets the minimum system requirements for Digital Guardian software and agents. You can find these requirements on the Digital Guardian website or in their documentation.
- Identify the type of deployment you want: on-premises, cloud-hosted, or hybrid.
2. Download and Prepare Installation Files:
- Download the installation package from the Digital Guardian website or your authorized distributor.
- Extract the installation files and prepare any additional components like licenses and configuration files needed for your deployment.
3. Install Server Components:
- If deploying on-premises, install the Digital Guardian Management Console (DGMC) on a dedicated server within your network.
- Configure the DGMC server with relevant settings like database connection, license information, and user accounts.
4. Deploy Agents and Sensors:
- Install Digital Guardian agents on endpoints like laptops, desktops, and mobile devices. Choose the appropriate installation method for your operating system (e.g., manual, MSI package).
- Deploy sensors on network devices like firewalls and gateways to monitor data traffic and enforce DLP policies.
5. Configure Policies and Settings:
- Define data classification policies to identify and tag sensitive data within your environment.
- Set up DLP policies to prevent unauthorized data transfers based on your identified data types and channels (email, web, file sharing, etc.).
- Configure user roles and permissions within the DGMC for access control and security management.
6. Testing and Verification:
- Test your DLP policies and threat detection capabilities to ensure they function as intended and don’t disrupt legitimate workflows.
- Verify proper communication between agents, sensors, and the DGMC server.
7. Ongoing Management and Maintenance:
- Update Digital Guardian software and agents regularly to stay protected against the latest threats.
- Monitor DGMC reports and alerts for any suspicious activity or potential data breaches.
- Review and refine your DLP policies and configurations as needed to adapt to changing business needs and security risks.
Remember, installing Digital Guardian might require specialized expertise, especially for complex deployments or large environments. It’s recommended to consult with Digital Guardian support or an authorized partner for assistance if needed.
Basic Tutorials of Digital Guardian: Getting Started

Digital Guardian offers a robust suite of data protection tools, but getting started can seem daunting. Worry not! This guide will walk you through the essential steps of setting up and using Digital Guardian for basic data protection.
1. System Requirements and Preparation:
- Check system requirements: Ensure your hardware and software meet Digital Guardian’s minimum specifications. You can find these on their website or in the documentation.
- Choose Deployment Type: Decide whether you’ll use an on-premises server, cloud-hosted infrastructure, or a hybrid approach.
2. Download and Prepare Installation Files:
- Download Installation Package: Head to the Digital Guardian website or your distributor to download the installation package.
- Extract Files: Unzip the installation package and prepare any additional components like licenses and configuration files.
3. Install Server Components:
- On-premises: Install the Digital Guardian Management Console (DGMC) on a dedicated server within your network.
- Cloud-hosted: Follow Digital Guardian’s instructions for your chosen cloud platform (AWS, Azure, etc.).
- Configure DGMC: Set up database connections, license information, and user accounts within the DGMC.
4. Deploy Agents and Sensors:
- Install Agents: On endpoints like laptops and desktops, choose the appropriate installation method (manual, MSI package) based on your operating system.
- Deploy Sensors: Place sensors on network devices like firewalls and gateways to monitor data traffic and enforce DLP policies.
5. Configure Policies and Settings:
- Data Classification: Define policies to identify and tag sensitive data types (PII, financial data, intellectual property, etc.).
- DLP Policies: Set up rules to prevent unauthorized data transfers based on channels (email, web, file sharing) and content (keywords, patterns).
- User Roles and Permissions: Manage user access control and security within the DGMC.
6. Testing and Verification:
- Test DLP Policies: Run simulations to ensure policies function correctly and don’t disrupt legitimate workflows.
- Verify Communication: Confirm agents, sensors, and the DGMC communicate effectively.
7. Ongoing Management and Maintenance:
- Software Updates: Update Digital Guardian software and agents regularly for optimal protection.
- Monitor Reports and Alerts: Keep an eye on the DGMC for suspicious activity or potential data breaches.
- Review and Refine: Regularly assess and adjust your policies and configurations as needed.
Remember, implementing Digital Guardian might require technical expertise, especially for complex deployments. Contact Digital Guardian support or an authorized partner for assistance if needed.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

