History & Origin of Fortify
Gartner and Magic Quadrant are registered trademarks of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Micro Focus. * The Fortify brand was recognized as a Magic Quadrant Leader 8 times over the years under HP, HPE and currently under Micro Focus.
2021 Gartner Magic Quadrant for Application Security Testing highlights:
Read the 2021 Gartner Magic Quadrant or Application Security Testing report today.
What is Fortify
Fortify Software, later known as Fortify Inc., is a California-based software security vendor, founded in 2003 and acquired by Hewlett-Packard in 2010 to become part of HP Enterprise Security Products. Since 2017, Fortify’s products have been owned by Micro Focus.
Machine Learning for Auditing
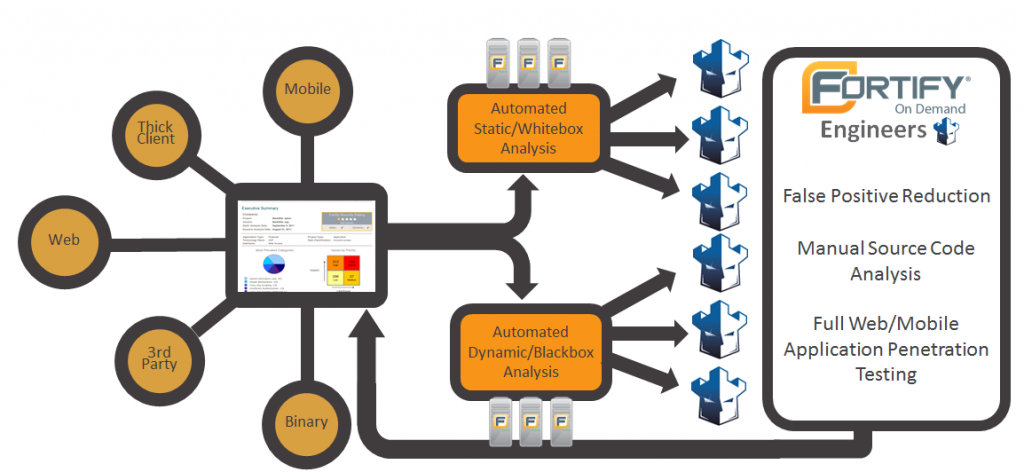
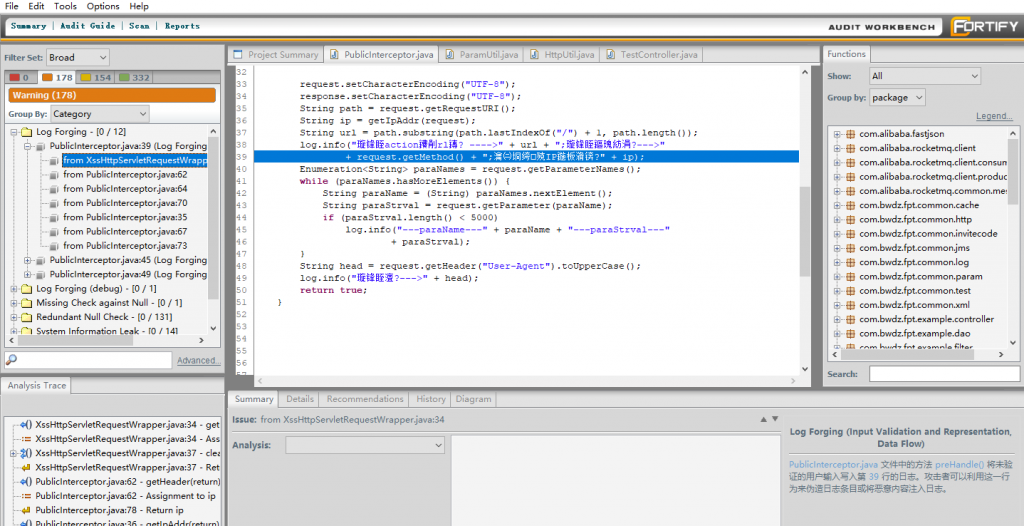
Fortify’s application security as a service offering (Fortify on Demand) runs thousands of static, dynamic, and mobile scans per week, scanning billions of lines of code. Fortify on Demand takes customer application source code, runs the scan, then (as a value added service) passes these raw scan results to a team of expert auditors who are subject matter experts. These auditors identify and prioritize the noteworthy findings while removing the noise from the results. Consequently, Fortify on Demand customers receive actionable results and can primarily focus on fixing the most critical issues. The Fortify Audit Assistant service uses machine learning algorithms to feed off the hundreds of millions of anonymous audit decisions from Fortify on Demand experts. These decision models are actively used and developed for Fortify on Demand, but are also technologies that can be automatically applied on-prem to Fortify Static Code Code Analyzer results by using Audit Assistant. This innovative and patent-pending technology has been made available to Fortify customers for the past five years.

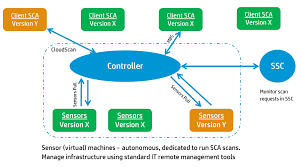
How Fortify works aka Fortify architecture?
Data Flow This analyzer detects potential vulnerabilities that involve tainted data (user-controlled input) put to potentially dangerous use. The data flow analyzer uses global, inter-procedural taint propagation analysis to detect the flow of data between a source (site of user input) and a sink (dangerous function call or operation). For example, the data flow analyzer detects whether a user-controlled input string of unbounded length is being copied into a statically sized buffer, and detects whether a user controlled string is being used to construct SQL query text.
Control Flow This analyzer detects potentially dangerous sequences of operations. By analyzing control flow paths in a program, the control flow analyzer determines whether a set of operations are executed in a certain order. For example, the control flow analyzer detects time of check/time of use issues and uninitialized variables, and checks whether utilities, such as XML readers, are configured properly before being used.
Structural This detects potentially dangerous flaws in the structure or definition of the program. For example, the structural analyzer detects assignment to member variables in Java servlets, identifies the use of loggers that are not declared static final, and flags instances of dead code that will never be executed because of a predicate that is always false.
Semantic This analyzer detects potentially dangerous uses of functions and APIs at the intra-procedural level. Basically a smart GREP.
Configuration This analyzer searches for mistakes, weaknesses, and policy violations in an application’s deployment configuration files.
Buffer This analyzer detects buffer overflow vulnerabilities that involve writing or reading more data than a buffer can hold.
Work

This technique analyzes every feasible path that execution and data can follow to identify and remediate vulnerabilities. To process code, Fortify SCA works much like a compiler—which reads source code files and converts them to an intermediate structure enhanced for security analysis.
Use case of Fortify
Use Cases Solutions ideal for






- Mastering Qualitative Research: The Role of Focus Groups in Data Collection - July 11, 2024
- What is robots ops? - July 10, 2024
- 5 Effective Online Learning Strategies for DevOps Professionals - July 4, 2024