What is Fortify?

Fortify is a comprehensive application security (AppSec) platform developed by Micro Focus. It empowers organizations to proactively identify and address vulnerabilities throughout the entire software development lifecycle (SDLC). Think of it as a security shield woven into the fabric of your development process, helping you build secure software from the ground up.
Fortify offers a suite of tools and services covering various aspects of AppSec:
- Static Application Security Testing (SAST): Analyzes source code for vulnerabilities like buffer overflows, cross-site scripting (XSS), and SQL injection.
- Dynamic Application Security Testing (DAST): Simulates real-world attacks to uncover vulnerabilities in running applications.
- Software Composition Analysis (SCA): Identifies and assesses security risks within third-party libraries and components used in your software.
- Interactive Application Security Testing (IAST): Provides real-time feedback to developers during their coding process, pinpointing potential vulnerabilities early on.
- Web Application Security Testing (WAST): Focuses on identifying vulnerabilities specific to web applications.
- Security Risk Management (SRM): Prioritizes vulnerabilities, tracks remediation progress, and reports on overall AppSec posture.
Top 10 use cases of Fortify?
Top 10 Use Cases of Fortify:
- Compliance and Regulations: Meet compliance requirements like PCI DSS, HIPAA, and GDPR by ensuring secure software practices.
- Reduce Breaches and Data Loss: Proactively identify and address vulnerabilities before they can be exploited by attackers.
- Shift Left Security: Integrate AppSec tools early in the SDLC to catch vulnerabilities early and save time and effort.
- DevSecOps Adoption: Foster collaboration between development and security teams for a unified approach to security.
- Improve Software Quality: Build secure and reliable software that reduces post-release security issues and maintenance costs.
- Third-Party Software Risk Management: Manage security risks associated with third-party libraries and components used in your software.
- Continuous Security Monitoring: Continuously monitor applications for vulnerabilities and suspicious activity for proactive protection.
- Automate Security Tasks: Automate repetitive security tasks like vulnerability scanning and reporting to improve efficiency.
- Improve Developer Security Awareness: Train and educate developers on secure coding practices and vulnerability identification.
- Measure and Report Security Posture: Track progress and demonstrate the effectiveness of your AppSec initiatives to stakeholders.
By leveraging Fortify’s capabilities, organizations can significantly enhance their security posture, build more secure software, and minimize the risk of costly security breaches.
Fortify is just one piece of the AppSec puzzle. It’s crucial to adopt a holistic approach to security that encompasses secure coding practices, security awareness training, and incident response planning.
What are the feature of Fortify?
Fortify boasts a comprehensive set of features across its various AppSec tools, catering to different aspects of software security:
Static Application Security Testing (SAST):
- Deep source code analysis: Scans all code sections (including libraries and frameworks) for vulnerabilities like buffer overflows, XSS, SQL injection, and insecure coding practices.
- Context-aware analysis: Considers the context of code usage to prioritize vulnerabilities based on potential impact and exploitability.
- Compliance mapping: Identifies vulnerabilities relevant to specific compliance requirements like PCI DSS or HIPAA.
- Customizable rules and patterns: Develop and integrate custom rules and patterns to address specific security concerns or industry standards.
- Integration with IDEs and CI/CD pipelines: Seamlessly integrate SAST scans into development workflows for early vulnerability detection.
Dynamic Application Security Testing (DAST):
- Black-box and gray-box scanning: Simulates real-world attack vectors like SQL injection, XSS, and CSRF to uncover exploitable vulnerabilities.
- Interactive and automated scanning: Conduct scans manually or schedule automated scans for continuous security monitoring.
- Session recording and replay: Record attack sessions and replay them to pinpoint vulnerability locations and demonstrate exploitability.
- API security testing: Dedicated capabilities for identifying vulnerabilities in web APIs.
- Integration with vulnerability management tools: Streamline vulnerability reporting and remediation workflow.
Software Composition Analysis (SCA):
- Comprehensive component identification: Automatically identify open-source, commercial, and internal libraries and components used in your software.
- Vulnerability database: Scans identified components against an extensive database of known vulnerabilities in third-party software.
- License compliance checks: Identify potential license violations associated with third-party components.
- Dependency management recommendations: Suggest alternative components or versions with fewer vulnerabilities or license conflicts.
- Integration with build and deployment processes: Integrate SCA checks into your development workflow to prevent vulnerable components from entering production.
Interactive Application Security Testing (IAST):
- Real-time feedback during coding: Provides instant alerts and guidance to developers as they write code, highlighting potential vulnerabilities and suggesting secure coding practices.
- Integration with IDEs: Integrates seamlessly with popular IDEs for a smooth and unobtrusive development experience.
- Language and framework support: Supports a wide range of programming languages and frameworks, enabling broad applicability.
- Customizable rules and feedback: Configure IAST rules and feedback to align with your specific security policies and coding standards.
- Proactive vulnerability detection: Helps developers prevent vulnerabilities from being introduced into code in the first place.
Additional Features:
- Centralized vulnerability management: Track, prioritize, and remediate vulnerabilities across all tools and applications.
- Reporting and dashboards: Generate detailed reports and visualize security posture through interactive dashboards.
- Integration with other security tools: Integrates with SIEM, SOAR, and other security platforms for comprehensive security orchestration.
- Scalability and customization: Adapts to organizations of all sizes and supports customization to meet specific security needs.
These features demonstrate Fortify’s commitment to providing a comprehensive and integrated AppSec platform. Whether you’re focused on SAST, DAST, SCA, IAST, or other aspects of security, Fortify offers powerful tools and capabilities to empower your security posture and build secure software.
How Fortify works and Architecture?
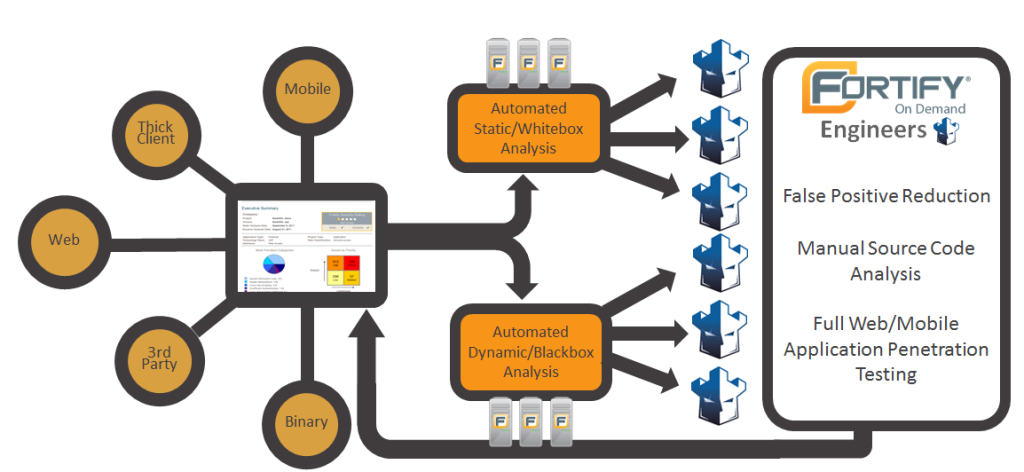
Fortify works through a multi-layered approach to application security, utilizing different tools and techniques to analyze your software comprehensively. Here’s a breakdown of its key elements and workflow:
1. Security Analysis:
- SAST: Scans source code for vulnerabilities using static analysis engines that identify security issues based on predefined rules and patterns.
- DAST: Simulates real-world attacks by crawling web applications and APIs, searching for exploitable vulnerabilities like XSS or SQL injection.
- SCA: analyzes software components like libraries and frameworks to identify known vulnerabilities and potential license conflicts.
- IAST: Integrates with developer workflows, providing real-time feedback and guidance during coding to prevent vulnerabilities from being introduced.
2. Vulnerability Identification and Prioritization:
- Each tool identifies potential vulnerabilities and assigns them severity levels based on their exploitability and potential impact.
- Fortify consolidates findings from different tools into a central vulnerability database.
- Advanced algorithms prioritize vulnerabilities based on factors like exploitability, potential impact, and ease of remediation.
3. Reporting and Remediation:
- Fortify generates detailed reports summarizing vulnerabilities, their severity, and recommended remediation steps.
- The platform integrates with issue tracking systems to facilitate assignment and tracking of remediation tasks.
- Developers can leverage built-in code fix suggestions and secure coding guidance to address vulnerabilities efficiently.
4. Continuous Monitoring and Improvement:
- Fortify can be integrated into CI/CD pipelines to automate security scans throughout the development lifecycle.
- This enables continuous monitoring for vulnerabilities and ensures security remains a core consideration throughout the development process.
- Organizations can track progress and measure the effectiveness of their AppSec initiatives using reports and dashboards.
Architecture:
Fortify employs a modular architecture consisting of:
- Core Platform: Provides the foundation for managing users, projects, scans, and vulnerability data.
- Scanners: Different scanners dedicated to SAST, DAST, SCA, and IAST functionalities.
- Integrations: Connectors to IDEs, CI/CD pipelines, and other security tools.
- Reporting and Analytics: Generates reports, dashboards, and insights for vulnerability management and security posture assessment.
This modular design allows for:
- Scalability: Adapts to organizations of all sizes by adjusting the number and configuration of scanner instances.
- Extensibility: Integrates seamlessly with existing development and security tools.
- Customization: Tailors vulnerability analysis and reporting to specific security needs and compliance requirements.
Benefits of Fortify Architecture:
- Comprehensive Analysis: Combines different security techniques for a holistic view of software vulnerabilities.
- Streamlined Workflow: Integrates with development and security processes for efficient vulnerability management.
- Continuous Improvement: Enables continuous monitoring and proactive vulnerability detection throughout the SDLC.
Note: Fortify is a powerful tool, but a successful AppSec strategy requires more than just technology. Implementing secure coding practices, promoting security awareness among developers, and having a robust incident response plan are crucial aspects of building and maintaining secure software.
How to Install Fortify it?
Installing Fortify can vary depending on the specific product and desired deployment model (on-premises, cloud, containerized). Here’s an overview of the general steps:
1. System Requirements:
- Ensure your system meets the hardware and software requirements specified for your chosen Fortify product.
- This typically includes details on operating system versions, supported databases, and specific software dependencies.
2. License and Download:
- Obtain a valid license for the Fortify product you wish to install.
- Contact Micro Focus or your authorized reseller for license acquisition and download instructions.
3. Deployment Method:
- On-premises installation:
- Download the installation package and follow the detailed installation guide provided by Micro Focus.
- This typically involves manual configuration of server components, databases, and application settings.
- Cloud deployment:
- Micro Focus offers several Fortify products as cloud-hosted services.
- Follow the specific setup instructions provided for your chosen cloud service (e.g., AWS Marketplace, Azure Marketplace).
- Containerized deployment:
- Some Fortify components are available as Docker containers.
- Utilize container orchestration tools like Docker Compose or Kubernetes to deploy and manage the containerized environment.
4. Configuration and Testing:
- Once installed, configure the Fortify application according to your needs.
- This includes setting up user accounts, projects, scan settings, and integrations with other systems.
- Perform test scans and verify proper functionality before relying on the system for actual vulnerability assessments.
Tip: Installing Fortify can be complex and require technical expertise, especially for on-premises deployments. Consider consulting with Micro Focus support or authorized partners for assistance if needed.
Basic Tutorials of Fortify: Getting Started

Fortify offers various tools and workflows for security analysis, but let’s dive into some basic tutorials to get you started:
1. Static Application Security Testing (SAST):
a. Setting Up:
- Download and install Fortify SCA (Static Code Analyzer) based on your chosen platform (Windows, macOS, Linux).
- Configure your IDE plugin (optional) for seamless integration with your development environment.
b. Scanning a Project:
- Import your project source code into Fortify SCA.
- Define the scan scope (e.g., specific files, directories, or entire project).
- Choose the desired scan profile (e.g., basic, advanced, custom).
c. Analyzing Results:
- Fortify SCA will scan your code and identify potential vulnerabilities.
- Review the reported vulnerabilities, including severity levels, descriptions, and remediation guidance.
- Prioritize vulnerabilities based on their risk and impact.
d. Fix and Re-scan:
- Address the identified vulnerabilities by fixing the code according to the provided remediation advice.
- Re-scan your project to verify if the vulnerabilities have been fixed successfully.
2. Software Composition Analysis (SCA):
a. Integrating with Build Pipeline:
- Integrate Fortify SCA with your build pipeline to automate security checks during development and deployment.
- Configure SCA to scan third-party libraries and dependencies used in your project.
b. Detecting Vulnerable Dependencies:
- SCA will analyze your dependencies and identify any known vulnerabilities associated with them.
- Review the reported vulnerabilities and their potential impact on your application.
c. Managing Dependencies:
- Update vulnerable dependencies to patched versions recommended by Fortify SCA.
- Consider alternative libraries or implement mitigation strategies if updates are not available.
3. Web Application Security Testing (WAST):
a. Setting Up Scanner:
- Configure Fortify WebInspect, the WAST tool, to target your web application URL.
- Define the scan scope (e.g., specific pages, functionalities, or entire website).
b. Scanning for Vulnerabilities:
- WebInspect will crawl your website and identify potential security vulnerabilities like SQL injection, cross-site scripting, and insecure configurations.
c. Analyzing Results:
- Review the reported vulnerabilities, including their exploitability and potential impact.
- Prioritize vulnerabilities based on their severity and focus on patching the most critical ones first.
d. Fix and Re-scan:
- Implement security patches or apply mitigation strategies to address the identified vulnerabilities.
- Re-scan your website to verify if the vulnerabilities have been fixed successfully.
Bonus Tips:
- Utilize Fortify’s reporting and dashboard features to track progress, visualize trends, and measure security improvement.
- Consider leveraging Fortify’s DAST (Dynamic Application Security Testing) capabilities for deeper vulnerability analysis.
- Remember, Fortify is a powerful tool, but it’s crucial to understand security concepts and interpret results effectively.
These basic tutorials provide a starting point for your Fortify journey. Remember, continuous security testing and vulnerability management are crucial for building and maintaining secure software systems.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

