What is Gemalto?

Gemalto is a global digital security company that provides a wide range of products and services to help organizations and individuals secure their digital identities, data, and transactions. Gemalto’s solutions include encryption, authentication, identity and access management, secure payment technologies, and more. In 2019, Gemalto was acquired by Thales Group and is now part of the Thales Digital Identity and Security business.
These use cases reflect Gemalto’s commitment to providing digital security solutions that address the evolving challenges of data protection, identity management, and secure transactions in today’s digital world. Gemalto’s products and services are used across various industries, including finance, healthcare, government, telecommunications, and more, to enhance security and protect digital assets.
Top 10 use cases of Gemalto:
Here are the top 10 use cases for Gemalto’s solutions:
- Identity and Access Management (IAM): Gemalto offers IAM solutions to manage user identities, control access to systems and data, and ensure secure authentication, helping organizations protect sensitive information.
- Data Encryption: Gemalto’s encryption solutions protect data at rest, in transit, and in use, safeguarding sensitive information from unauthorized access and data breaches.
- Authentication and Single Sign-On (SSO): Gemalto provides strong authentication solutions and SSO capabilities, ensuring that users can securely access systems and applications with ease.
- Mobile Security: Gemalto’s mobile security solutions protect mobile devices, apps, and data, addressing the unique security challenges of the mobile era.
- eGovernment: Gemalto’s solutions enable secure digital identity verification and authentication for government services, including electronic passports, ID cards, and driver’s licenses.
- Secure Payment Technologies: Gemalto is a leader in secure payment technologies, providing solutions for EMV chip cards, contactless payments, mobile payments, and secure payment processing.
- IoT Security: Gemalto helps secure the Internet of Things (IoT) by providing solutions for device authentication, data encryption, and secure connectivity in IoT deployments.
- Cloud Security: Gemalto assists organizations in securing their cloud environments, ensuring data privacy, compliance, and control in cloud-based operations.
- Digital Banking and Financial Services: Gemalto’s solutions support secure digital banking and financial transactions, including mobile banking apps, secure payment processing, and identity verification.
- Government and Enterprise Cybersecurity: Gemalto provides comprehensive cybersecurity solutions for governments and enterprises, including threat detection, incident response, and security analytics.
What are the feature of Gemalto?
Gemalto, now known as Thales Digital Identity and Security, offers a wide range of features and capabilities through its digital security solutions. The specific features may vary depending on the product or solution within the Gemalto (Thales Digital Identity and Security) portfolio, but here are some common features and functionalities associated with their offerings:
- Identity and Access Management (IAM): Gemalto provides IAM solutions for managing user identities, controlling access to systems and data, and enabling secure authentication.
- Data Encryption: Gemalto’s encryption solutions protect data at rest, in transit, and in use, ensuring data confidentiality and integrity.
- Authentication: Gemalto offers strong authentication methods, including multi-factor authentication (MFA) and biometrics, to verify user identities securely.
- Single Sign-On (SSO): SSO solutions simplify user access to multiple applications while ensuring secure authentication.
- Mobile Security: Gemalto addresses mobile security challenges by securing mobile devices, apps, and data.
- eGovernment Solutions: Gemalto provides secure digital identity solutions for government services, such as electronic passports, ID cards, and driver’s licenses.
- Secure Payment Technologies: Gemalto is a leader in secure payment technologies, offering solutions for EMV chip cards, contactless payments, mobile payments, and payment processing security.
- IoT Security: Gemalto’s IoT security solutions protect connected devices, data, and communication in IoT deployments.
- Cloud Security: Gemalto helps organizations secure cloud environments, ensuring data privacy, compliance, and control in cloud-based operations.
- Digital Banking and Financial Services: Gemalto’s solutions support secure digital banking and financial transactions, including mobile banking apps, payment processing, and identity verification.
How Gemalto works and Architecture?
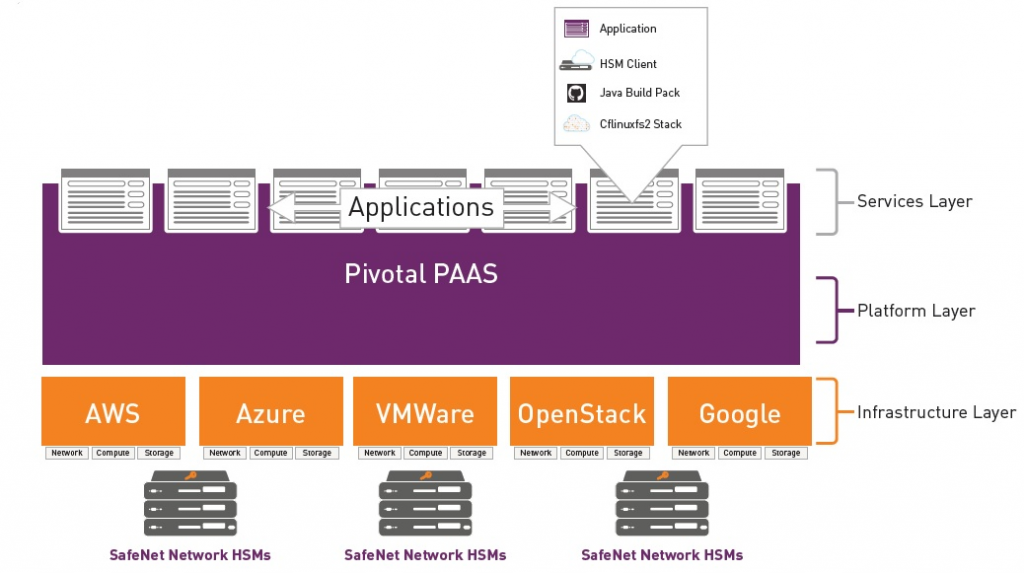
Gemalto’s architecture and how it works can vary depending on the specific product or solution being used, but here’s a general overview of how Gemalto solutions typically operate:
- Deployment: Gemalto solutions can be deployed on-premises or in cloud environments, depending on the specific requirements of the organization.
- Identity and Access Management: Gemalto’s IAM solutions centralize identity management, enabling administrators to manage user identities, access controls, and authentication policies.
- Encryption: Gemalto’s encryption solutions protect data by encrypting it using strong encryption algorithms. Encryption keys are managed securely to ensure data confidentiality.
- Authentication: Gemalto offers various authentication methods, including tokens, smart cards, biometrics, and mobile-based authentication, to verify user identities securely.
- Mobile Security: Gemalto secures mobile devices and apps through solutions that include mobile device management (MDM) and mobile application management (MAM).
- eGovernment Solutions: Gemalto’s eGovernment solutions involve secure issuance and verification of digital identity documents and the use of these documents for government services.
- Payment Technologies: Gemalto’s payment solutions encompass secure card issuance, payment processing, and EMV chip card technology.
- IoT Security: Gemalto’s IoT security solutions protect IoT devices and communication, ensuring the integrity and confidentiality of IoT data.
- Cloud Security: Gemalto helps organizations secure cloud environments by providing encryption, access controls, and identity management solutions tailored to cloud deployments.
- Integration: Gemalto solutions can integrate with existing IT systems, applications, and security infrastructure, providing seamless security controls and operations.
Overall, Gemalto’s architecture is designed to provide robust security and identity management capabilities to help organizations protect digital assets, ensure data privacy, and maintain compliance with security standards and regulations. Specific implementations may vary based on an organization’s needs and the Gemalto products in use.
How to Install Gemalto?
To install Gemalto software, you will need to download the installer package from the Gemalto website. The specific steps involved in the installation process will vary depending on the software product you are installing, but the general steps are as follows:
- Download the installer package from the Gemalto website.
- Double-click on the installer package to start the installation process.
- Follow the on-screen instructions to fulfill the installation.
Some additional things to keep in mind when installing Gemalto software:
- Make sure that your system meets the minimum requirements for the software you are installing. You can find the minimum requirements on the product page for the software on the Gemalto website.
- If you are installing a software product that requires a smart card reader, make sure that the smart card reader is properly installed and configured before you start the installation process.
- If you are installing a software product that will be used in a production environment, be sure to test the software thoroughly before you deploy it.
Some specific instructions for installing some popular Gemalto products:
- SafeNet Authentication Service
To install SafeNet Authentication Service, download the SafeNet Authentication Service installer package from the Gemalto website. Once you have downloaded the installer package, double-click on it to start the installation process. Follow the on-screen instructions to fulfill the installation.
- SafeNet ProtectToolkit
To install SafeNet ProtectToolkit, download the SafeNet ProtectToolkit installer package from the Gemalto website. Once you have downloaded the installer package, double-click on it to start the installation process. Follow the on-screen instructions to fulfill the installation.
- SmartTrust
To install SmartTrust, download the SmartTrust installer package from the Gemalto website. Once you have downloaded the installer package, double-click on it to start the installation process. Follow the on-screen instructions to fulfill the installation.
Basic Tutorials of Gemalto: Getting Started

The following are the basic tutorials for Gemalto’s SafeNet Authentication Service (SAS). The SAS is a two-factor authentication solution that uses smart cards and one-time passwords to protect access to IT resources.
How to log in to SAS
- Insert your smart card into the smart card reader.
- Enter your PIN when prompted.
- Enter the one-time password (OTP) that is displayed on your smart card.
How to change your PIN
- Log in to SAS.
- Click on the Change PIN link.
- Type your current PIN and your new PIN twice.
- Click on the Change PIN button.
How to reset your password
If you forget your PIN, you can reset it by contacting your IT administrator.
How to add a new user to SAS
- Log in to SAS as an administrator.
- Click on the Manage Users link.
- Click on the Add User button.
- Enter the user’s information and click on the Add User button.
How to delete a user from SAS
- Log in to SAS as an administrator.
- Click on the Manage Users link.
- Choose the user you want to delete and press on the Delete User button.
How to enable two-factor authentication for an application
- Log in to SAS as an administrator.
- Click on the Manage Applications link.
- Select the application you want to enable two-factor authentication for and click on the Edit Application button.
- Select the Enable Two-Factor Authentication checkbox and click on the Save button.
How to disable two-factor authentication for an application
- Log in to SAS as an administrator.
- Click on the Manage Applications link.
- Select the application you want to disable two-factor authentication for and click on the Edit Application button.
- Deselect the Enable Two-Factor Authentication checkbox and click on the Save button.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

