What is IBM Data Privacy Passports?

IBM Data Privacy Passports is a data security platform that enables organizations to protect their sensitive data throughout its lifecycle. It does this by providing a way to encrypt sensitive data and control how it is accessed and used.
Top 10 use cases of IBM Data Privacy Passports:
- Protecting sensitive data in transit: IBM Data Privacy Passports can be used to encrypt sensitive data as it is transferred between systems. This helps to protect the data from unauthorized access or interception.
- Protecting sensitive data in storage: IBM Data Privacy Passports can be used to encrypt sensitive data as it is stored in a database or file system. This helps to protect the data from unauthorized access or disclosure.
- Protecting sensitive data in use: IBM Data Privacy Passports can be used to encrypt sensitive data as it is used by applications. This aids to protect the data from modification or unauthorized access.
- Revoking access to sensitive data: IBM Data Privacy Passports can be used to revoke access to sensitive data after it has been shared with a third party. This helps to protect the data from unauthorized access or use.
- Managing consent for data sharing: IBM Data Privacy Passports can be used to manage consent for data sharing. This helps organizations to ensure that they are only sharing data with third parties who have the appropriate permissions.
- Providing audit trails: IBM Data Privacy Passports can be used to provide audit trails of data access and usage. This helps organizations to track who has accessed sensitive data and how it has been used.
- Complying with regulations: IBM Data Privacy Passports can help organizations to comply with a variety of data privacy regulations, such as GDPR, CCPA, and HIPAA.
- Protecting data in the cloud: IBM Data Privacy Passports can be used to protect data in the cloud. This helps organizations to ensure that their data is protected even when it is stored in a third-party cloud environment.
- Protecting data in hybrid environments: IBM Data Privacy Passports can be used to protect data in hybrid environments. This helps organizations to ensure that their data is protected even when it is stored in a mix of on-premises and cloud-based systems.
- Providing a single point of control: IBM Data Privacy Passports provides a single point of control for managing data privacy. This helps organizations to simplify their data privacy management processes and reduce the risk of data breaches.
What are the feature of IBM Data Privacy Passports?
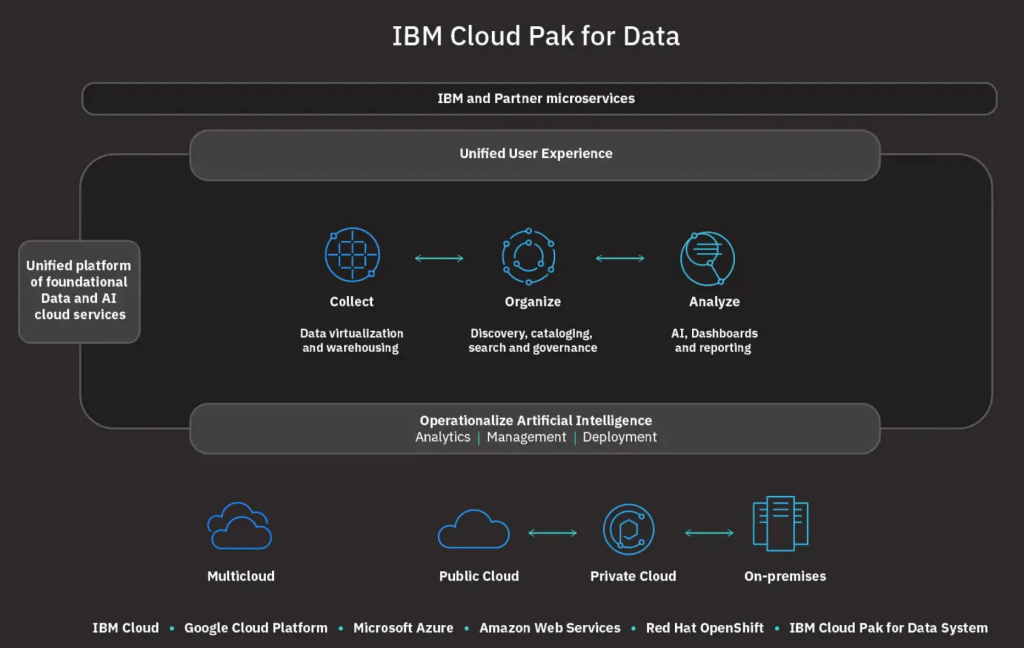
- Encryption: IBM Data Privacy Passports uses strong encryption algorithms to protect sensitive data.
- Access control: IBM Data Privacy Passports provides fine-grained access control to sensitive data.
- Auditing: IBM Data Privacy Passports provides audit trails of data access and usage.
- Compliance: IBM Data Privacy Passports helps organizations to comply with a variety of data privacy regulations.
- Ease of use: IBM Data Privacy Passports is easy to use and manage.
- Scalability: IBM Data Privacy Passports is scalable to meet the needs of organizations of all sizes.
- Security: IBM Data Privacy Passports is a secure solution that meets the highest security standards.
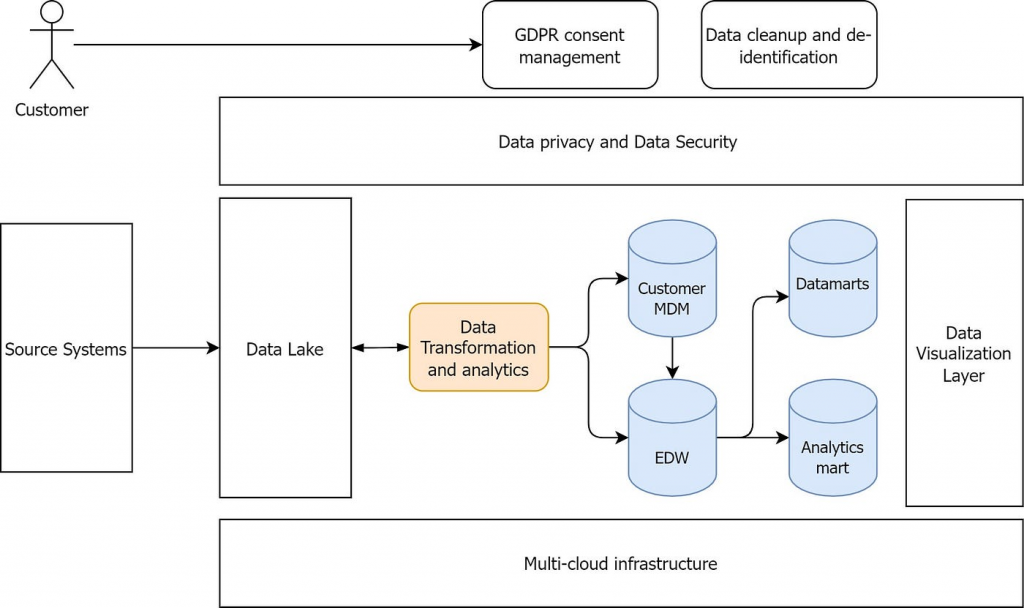
How IBM Data Privacy Passports works and Architecture?
IBM Data Privacy Passports works by creating a secure envelope around sensitive data. This envelope contains the encrypted data, as well as metadata that describes the data and how it can be used. The envelope is then stored in a tamper-evident manner.
When someone wants to access the sensitive data, they must first present a valid passport. The passport contains the credentials that are needed to decrypt the envelope and access the data.
The architecture of IBM Data Privacy Passports is based on a three-tier model:
- The passport controller is responsible for managing the passports and enforcing access control.
- The passport store is responsible for storing the passports and the encrypted data.
- The passport client is responsible for presenting passports and accessing the encrypted data.
How to Install IBM Data Privacy Passports?
Here are the steps on how to install IBM Data Privacy Passports:
- Download the IBM Data Privacy Passports software from the IBM website.
- Install the software on a server that has access to the data that you want to protect.
- Create a user account and configure the software.
- Start using the software to protect your sensitive data.
Here are the detailed steps:
- To download the IBM Data Privacy Passports software, you can go to the IBM website: https://www.ibm.com/products/data-privacy-passports and click on the “Download” button.
- Once you have downloaded the software, you can follow the instructions on the screen to install it.
- To create a user account, you will need to provide a username, password, and email address. You will also choose a role for the user.
- To configure the software, you will need to specify the location of the data that you want to protect, as well as the encryption settings.
- Once you have configured the software, you can start using it to protect your sensitive data.
Here are some of the things to keep in mind when installing IBM Data Privacy Passports:
- The software requires a 64-bit processor and 4 GB of RAM.
- The software needs 10 GB of free disk space.
- The software favors Windows Server 2012 R2 and later.
- The software supports Linux distributions that are based on Red Hat Enterprise Linux 7.
Basic Tutorials of IBM Data Privacy Passports: Getting Started
Here, Let’s have a look at a basic outline of the steps involved in using a data privacy management solution like IBM Data Privacy Passports:

Step-by-Step Basic Tutorial of IBM Data Privacy Passports:
Step 1: Obtain Access to IBM Data Privacy Passports:
- Contact IBM or their authorized sales representative to obtain access to IBM Data Privacy Passports.
- Obtain the necessary credentials to access the platform.
Step 2: Set Up Your Data Privacy Environment:
- Log in to the IBM Data Privacy Passports web application using a supported web browser.
- Configure basic settings for your organization, such as name, language, and privacy policies.
- Define user roles and permissions for data privacy stakeholders within your organization.
Step 3: Connect Data Sources and Systems:
- Connect the data sources and systems that contain personal data to IBM Data Privacy Passports.
- Configure the necessary authentication and authorization settings for each data source.
Step 4: Discover and Classify Personal Data:
- Initiate data discovery and classification scans on the connected data sources.
- IBM Data Privacy Passports will automatically identify and classify personal data based on patterns and rules.
Step 5: Define Privacy Policies and Consent Management:
- Define privacy policies and consent requirements based on regulatory guidelines (e.g., GDPR, CCPA) and internal privacy governance needs.
- Implement consent management processes to handle data subject consent preferences.
Step 6: Data Subject Requests and Privacy Rights:
- Use IBM Data Privacy Passports to handle data subject access requests (DSARs) and other privacy rights requests.
- Ensure compliance with data subject rights requirements and respond to requests within mandated timeframes.
Step 7: Monitor and Report Privacy Metrics:
- Utilize IBM Data Privacy Passports’ monitoring capabilities to track privacy metrics and compliance status.
- Generate reports and dashboards to gain insights into privacy risks and trends.
Step 8: Data Protection Impact Assessments (DPIAs):
- Conduct Data Protection Impact Assessments (DPIAs) to assess and mitigate privacy risks associated with data processing activities.
- Document DPIA outcomes and remediation plans.
Step 9: Data Breach Response:
- In the event of a data breach, use IBM Data Privacy Passports to assess the impact on personal data.
- Take necessary remediation actions to notify affected individuals and regulatory authorities.
Step 10: Continuous Improvement:
- Continuously monitor and improve privacy management practices based on IBM Data Privacy Passports’ insights and recommendations.
- Keep IBM Data Privacy Passports up-to-date with the latest privacy regulations and best practices.
For detailed tutorials and guidance, it is best to refer to IBM’s official documentation, knowledge base, and training resources.

