What is Informatica Persistent Data Masking?
Informatica Persistent Data Masking is a data masking solution that helps organizations protect sensitive data in production, test, and development environments. It can be used to mask data in a variety of formats, including databases, files, and applications.
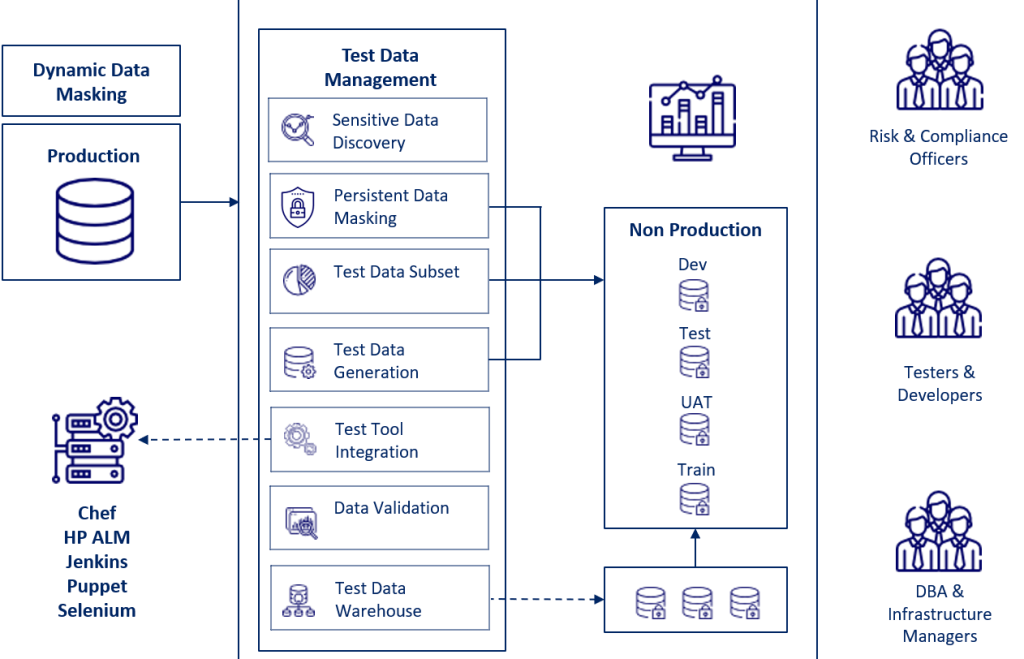
Top 10 use cases of Informatica Persistent Data Masking:
- Protecting sensitive data in production: Informatica Persistent Data Masking can be used to mask sensitive data in production databases, files, and applications. This helps to protect data from unauthorized access and misuse.
- Creating realistic test data: Informatica Persistent Data Masking can be used to create realistic test data that is masked to protect sensitive information. This helps to ensure that test data is accurate and reliable.
- Securing development environments: Informatica Persistent Data Masking can be used to secure development environments by masking sensitive data in development databases and files. This helps to prevent sensitive data from being leaked during the development process.
- Complying with regulations: Informatica Persistent Data Masking can be used to comply with regulations that require sensitive data to be masked. This involves regulations such as PCI DSS, HIPAA, and GDPR.
- Protecting intellectual property: Informatica Persistent Data Masking can be used to protect intellectual property by masking sensitive data in databases and files. This helps to prevent intellectual property from being stolen or leaked.
- Enhancing data privacy: Informatica Persistent Data Masking can be used to enhance data privacy by masking sensitive data in databases and files. This helps to protect the privacy of individuals whose data is stored in an organization’s systems.
- Improving data quality: Informatica Persistent Data Masking can be used to improve data quality by masking sensitive data in databases and files. This aids to verify that data is accurate and reliable.
- Reducing the risk of data breaches: Informatica Persistent Data Masking can be used to reduce the risk of data breaches by masking sensitive data in databases and files. This aids to hamper unauthorized access to sensitive data.
- Saving money: Informatica Persistent Data Masking can save organizations money by reducing the need to purchase and maintain expensive data security solutions.
- Improving compliance with industry standards: Informatica Persistent Data Masking can help organizations comply with industry standards such as PCI DSS and HIPAA by masking sensitive data in databases and files.
What are the features of Informatica Persistent Data Masking?
Informatica Persistent Data Masking offers a number of features that make it a powerful and versatile data masking solution, including:
- Scalability: Informatica Persistent Data Masking can be scaled to meet the needs of even the largest organizations.
- Performance: Informatica Persistent Data Masking can mask data quickly and efficiently, without impacting the performance of production systems.
- Flexibility: Informatica Persistent Data Masking offers a variety of masking techniques, so you can choose the right technique for your specific needs.
- Security: Informatica Persistent Data Masking is highly secure, with features to protect your data from unauthorized access.
- Compliance: Informatica Persistent Data Masking is compliant with a variety of regulations, so you can be sure that your data is protected.
- Integration: Informatica Persistent Data Masking can be integrated with a variety of other Informatica products, as well as third-party products.
How Informatica Persistent Data Masking works and Architecture?
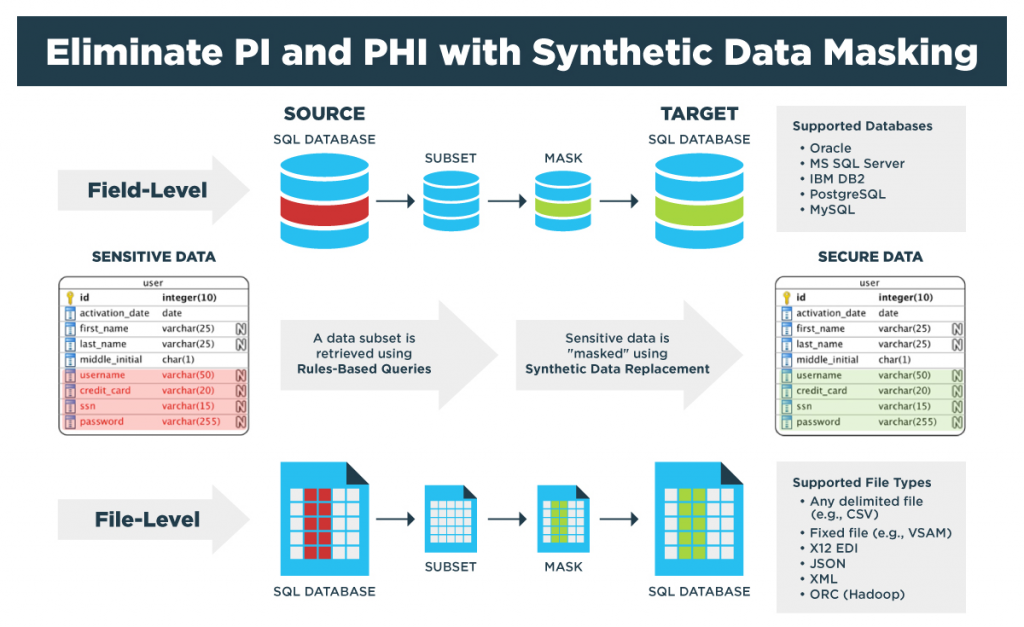
Informatica Persistent Data Masking works by creating a copy of the original data and then masking the sensitive data in the copy. The masked data can then be used for testing, development, or other purposes without compromising the security of the original data.
The architecture of Informatica Persistent Data Masking is as follows:
- Data Source: The data source is the original data that needs to be masked.
- Masking Engine: The masking engine is responsible for masking the sensitive data in the data source.
- Masked Data: The masked data is the copy of the original data with the sensitive data masked.
- Target: The target is the location where the masked data will be stored.
How to Install Informatica Persistent Data Masking?
To install Informatica Persistent Data Masking, you will need to follow these steps:
- Download the Informatica Persistent Data Masking installation package from the Informatica website.
- Run the installation package and follow the on-screen instructions.
- Once the installation is complete, you will need to configure Informatica Persistent Data Masking.
- You can then start masking data using Informatica Persistent Data Masking.
Basic Tutorials of Informatica Persistent Data Masking: Getting Started
Sure, here’s a basic step-by-step tutorial for setting up Informatica Persistent Data Masking. This tutorial assumes you have the necessary software and licenses installed.

Step 1: Prerequisites:
- Install Informatica PowerCenter: Ensure you have Informatica PowerCenter installed and configured on your system.
- Obtain Informatica Persistent Data Masking: Acquire the Informatica Persistent Data Masking module, which is an add-on to Informatica PowerCenter.
Step 2: Connect to PowerCenter:
- Launch Informatica PowerCenter Designer or Workflow Manager.
- Connect to the PowerCenter repository where you want to create your masking project.
Step 3: Create a Masking Project:
- In the Designer or Workflow Manager, create a new project for your masking activities.
- Define the source and target databases for your masking process. These databases will contain the original sensitive data and the masked data, respectively.
Step 4: Define Sensitive Columns:
- Import or manually define the source tables and columns that contain sensitive data.
- For each sensitive column, define the data masking algorithm to be used. Informatica offers various built-in algorithms like random, lookup-based, or custom algorithms.
Step 5: Configure Data Masking:
- Create a Data Masking transformation within your project.
- Configure the transformation to use the previously defined masking algorithms for the sensitive columns.
Step 6: Create a Masking Workflow:
- In the Workflow Manager, create a new workflow for your masking project.
- Add the Data Masking transformation to the workflow.
- Configure connections to the source and target databases for the workflow.
Step 7: Run the Masking Workflow:
- Validate your workflow to ensure there are no errors.
- Run the workflow to execute the data masking process.
- Monitor the workflow’s progress and check for any errors in the execution.
Step 8: Verify Masked Data:
- Access the target database to verify that the sensitive data has been successfully masked according to your defined algorithms.
- Perform data quality checks and comparisons to ensure the masked data retains its integrity while protecting sensitive information.
Step 9: Schedule and Automate:
- If required, configure the Informatica Scheduler or an external scheduler to automate the execution of the data masking workflow at specific intervals.
- Monitor scheduled runs to ensure data masking continues to work as expected.
Step 10: Documentation and Reporting:
- Document your data masking processes, including the masking algorithms used, workflow configurations, and any scheduling details.
- Create reports or documentation that can be used for compliance and audit purposes.
Remember, this is a simplified overview of the process, and the actual implementation may involve additional steps and considerations based on your specific use case. Always refer to the official Informatica documentation and support resources for accurate and detailed instructions.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

