What is Informatica Secure@Source?

Informatica Secure@Source is a comprehensive data security solution designed to discover, analyze, and protect sensitive data across an organization’s data landscape. It helps organizations identify where sensitive data resides, understand its risk exposure, and implement appropriate data protection measures. Secure@Source provides data discovery, classification, risk assessment, and data protection capabilities.
Top 10 Use Cases of Informatica Secure@Source:
- Sensitive Data Discovery: Discover and identify sensitive data across various data sources, databases, file systems, and applications.
- Data Classification: Automatically classify sensitive data based on predefined or custom policies to ensure consistent protection measures.
- Risk Assessment: Evaluate the level of risk associated with sensitive data, considering factors like data exposure, access patterns, and data lineage.
- Data Governance: Enhance data governance efforts by understanding data ownership, usage, and access patterns.
- Compliance: Facilitate compliance with data protection regulations (e.g., GDPR, HIPAA) by identifying and securing sensitive data.
- Data Lifecycle Management: Manage the lifecycle of sensitive data, including its creation, usage, movement, and archival.
- Data Protection Strategies: Implement data protection strategies such as data masking, encryption, and tokenization based on the identified risk level.
- Security Incident Response: Quickly respond to security incidents by identifying impacted data and taking appropriate actions to mitigate risks.
- Cloud Data Security: Extend Secure@Source’s capabilities to cloud environments to safeguard sensitive data stored or processed in the cloud.
- Data Privacy: Support data privacy initiatives by ensuring that only authorized individuals have access to sensitive data.
What are the feature of Informatica Secure@Source?
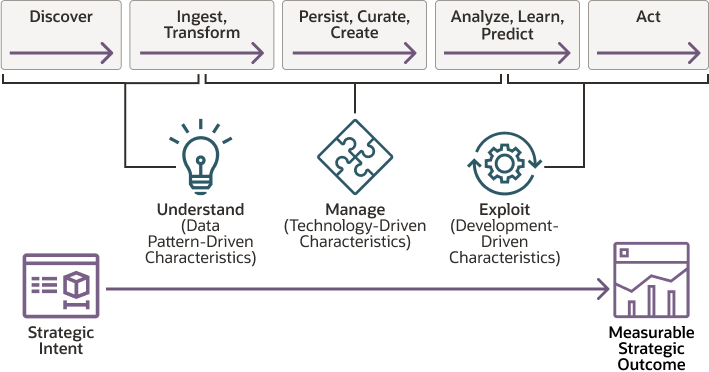
- Data Discovery and Classification: Discover and classify sensitive data based on content, context, and metadata analysis.
- Risk Assessment: Evaluate the risk level of sensitive data by analyzing data exposure and access patterns.
- Data Protection: Implement data protection measures such as data masking, encryption, and tokenization.
- Data Lineage: Understand the flow of sensitive data across systems to determine potential vulnerabilities.
- Compliance Reporting: Generate reports to demonstrate compliance with data protection regulations.
- Data Anonymization: Protect data while maintaining its usefulness for analytics and testing through data anonymization.
- User Access Monitoring: Monitor user access to sensitive data and detect unauthorized activities.
- Integration with Other Security Solutions: Integrate with other security tools and platforms for a comprehensive security ecosystem.
How Informatica Secure@Source works and Architecture?
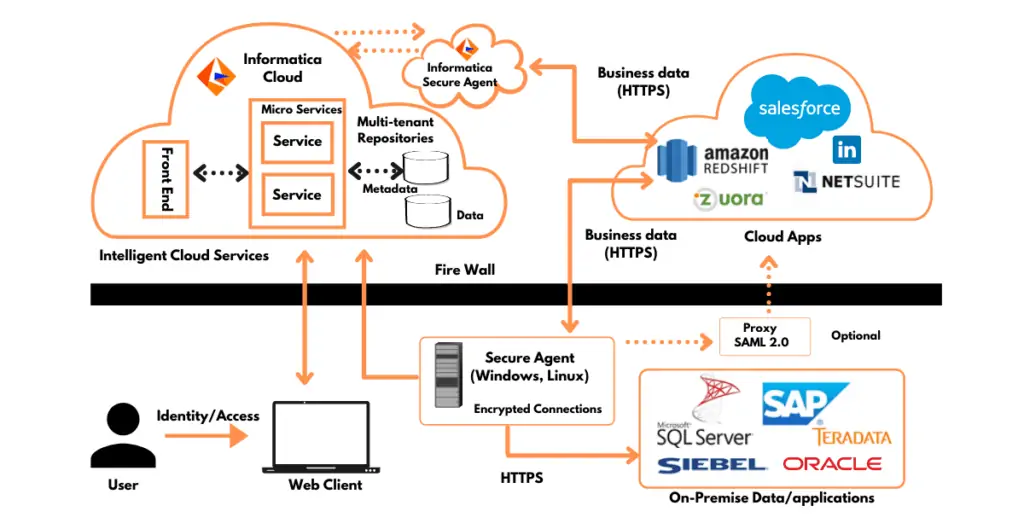
The architecture of Informatica Secure@Source involves several components:
- Data Discovery Agents: These agents scan various data sources, databases, and files to discover sensitive data. They collect metadata and content information for analysis.
- Central Repository: Discovered data and metadata are stored in a central repository for analysis, classification, and reporting.
- Data Classification Engine: This engine evaluates the discovered data against predefined or custom classification policies to determine its sensitivity level.
- Risk Assessment Engine: The risk assessment engine analyzes data exposure, access patterns, and other factors to assess the risk associated with sensitive data.
- Data Protection Engine: Based on risk assessment, the data protection engine recommends and applies appropriate data protection measures, such as data masking or encryption.
- User Interface: Secure@Source provides a user interface for administrators and analysts to configure policies, view reports, and manage data protection measures.
How to Install Informatica Secure@Source?
Installing and configuring Informatica Secure@Source involves the following steps:
- Preparation: Review the system requirements and ensure you have the necessary hardware and software prerequisites.
- Installation: Obtain the Secure@Source installation package and follow the provided installation instructions.
- Configuration: Configure the components, including connecting data sources, setting up classification policies, and defining risk assessment criteria.
- Data Discovery: Run data discovery agents to scan and collect data from various sources.
- Classification and Risk Assessment: Analyze the collected data to classify it and assess its risk level.
- Data Protection: Configure and apply appropriate data protection measures based on risk assessment.
- Reporting and Monitoring: Utilize the user interface to generate reports, monitor sensitive data access, and respond to security incidents.
Keep in mind that Informatica Secure@Source is an enterprise-level solution, and its installation and configuration might require specialized expertise. Always refer to the official Informatica documentation for detailed instructions and best practices: https://docs.informatica.com/secure-source.html
Basic Tutorials of Informatica Secure@Source: Getting Started

Here’s a simplified step-by-step guide to help you understand the basic concepts of Informatica Secure@Source.
Step 1: Installation and Setup
- Prepare Environment: Ensure your system meets the hardware and software requirements specified by Informatica.
- Download Installation Package: Obtain the Secure@Source installation package from the Informatica website.
- Install Secure@Source: Run the installation package and follow the provided instructions to install Secure@Source components.
Step 2: Configure Secure@Source
- Access Management Console: Open the Informatica Secure@Source Management Console using a web browser.
- Initial Configuration: Configure basic settings such as admin credentials, server addresses, and database connections.
Step 3: Data Discovery and Classification
- Connect Data Sources: Configure connections to various data sources, databases, and applications that you want to scan for sensitive data.
- Run Data Discovery: Start data discovery jobs to scan and collect metadata and content information from the connected data sources.
- Data Classification: Use Informatica Secure@Source’s classification engine to automatically classify sensitive data based on predefined policies or custom rules.
Step 4: Risk Assessment and Protection
- Risk Assessment: Leverage Secure@Source’s risk assessment capabilities to evaluate the level of risk associated with the classified sensitive data. This assessment considers factors like data exposure, access patterns, and other contextual information.
- Data Protection Measures: Based on the risk assessment results, consider implementing data protection measures like data masking, encryption, or tokenization to secure the sensitive data.
Step 5: Reporting and Monitoring
- Generate Reports: Use the reporting functionalities of Secure@Source to generate reports that provide insights into data discovery, classification, risk assessment, and data protection measures.
- Monitor Sensitive Data Access: Continuously monitor user access to sensitive data, detecting and responding to unauthorized activities.
Please note that Secure@Source is a complex product, and the actual implementation might require more in-depth configuration, integration with other security tools, and considerations for compliance regulations. Always refer to the official Informatica Secure@Source documentation.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

