What is IriusRisk?

IriusRisk is an open threat modeling platform that aims to make secure design the standard practice for every digital team. It stands out with its focus on automation, accessibility, and collaboration. Here’s a breakdown:
- Purpose: Helps developers and security professionals build secure software by design through threat modeling.
- Key features:
- Automated threat model generation: Creates threat models based on your system architecture with real-time analysis.
- Accessible for non-security experts: User-friendly interface and built-in guidance make it usable for developers and product managers.
- Real-time collaboration: Multiple users can work on the same threat model simultaneously.
- Compliance support: Aligns with industry standards like OWASP, NIST, GDPR, and more.
- Integration with existing tools: Connects with your development workflow and issue trackers.
Top 10 use cases of IriusRisk?
Top 10 Use Cases of IriusRisk:
- Rapidly assess security risks for small-scale projects or features.
- Facilitate security discussions and decisions during agile development sprints.
- Empower non-security experts to identify and address security concerns.
- Prioritize mitigation efforts by focusing on the most critical threats.
- Integrate seamlessly into existing development workflows without major disruption.
- Document security considerations early in the design process for future reference.
- Identify potential attack vectors for penetration testing and red teaming exercises.
- Communicate security risks and mitigation strategies effectively to stakeholders.
- Train and educate developers on basic security concepts and threat modeling principles.
- Complement and validate comprehensive threat modeling efforts later in the development lifecycle.
Additional benefits of IriusRisk:
- Shift left security: Ensures security considerations are addressed early in the design phase, saving time and resources compared to fixing vulnerabilities later.
- Improved development efficiency: Helps identify and address security concerns early, reducing code rework and vulnerabilities.
- Increased software security: Leads to more secure and robust software with mitigated risks.
Overall, IriusRisk offers a valuable solution for organizations looking to make secure design a standard practice and empower their teams to build secure software from the ground up.
What are the feature of IriusRisk?
IriusRisk boasts a suite of features designed to facilitate accessible, collaborative, and automated threat modeling. Following is a breakdown of some key features:
Automated Threat Modeling:
- Draw.io integration: Create diagrams using Draw.io and IriusRisk automatically analyzes them to generate threat models.
- Dynamic threat generation: Real-time analysis identifies potential threats as you build your system architecture.
- Scenario-based analysis: Define attack scenarios to focus threat identification and mitigation efforts.
Accessibility for Non-Security Experts:
- User-friendly interface: Drag-and-drop functionality and intuitive design make it easy for beginners to use.
- Built-in guidance: Tutorials, templates, and context-sensitive help provide assistance at every step.
- Threat libraries: Pre-defined libraries of common threats and mitigations for quick reference.
Real-time Collaboration:
- Multi-user editing: Teams can work on the same threat model simultaneously, fostering discussion and collaboration.
- Version control and history: Track changes and revert to previous versions if needed.
- Integration with chat tools: Connect with Slack or Microsoft Teams for real-time communication while collaborating.
Compliance and Integration:
- Compliance mapping: Align your threat models with industry standards like OWASP, NIST, and GDPR.
- Issue tracker integration: Push security tasks identified in threat models directly to your issue tracker (e.g., Jira).
- API access: Automate and customize IriusRisk to fit your specific workflows.
Additional features:
- Scalable threat modeling: Manage threat models for large and complex systems with ease.
- Reporting and visualizations: Generate detailed reports and visualize your threat models for stakeholders.
- Customizable components: Define your own reusable components for specific system functions.
- Nested components: Organize your threat models by grouping related functions and components.
Overall, IriusRisk’s feature set aims to empower all teams, regardless of security expertise, to contribute to building secure software through an accessible, collaborative, and automated threat modeling approach.
How IriusRisk works and Architecture?
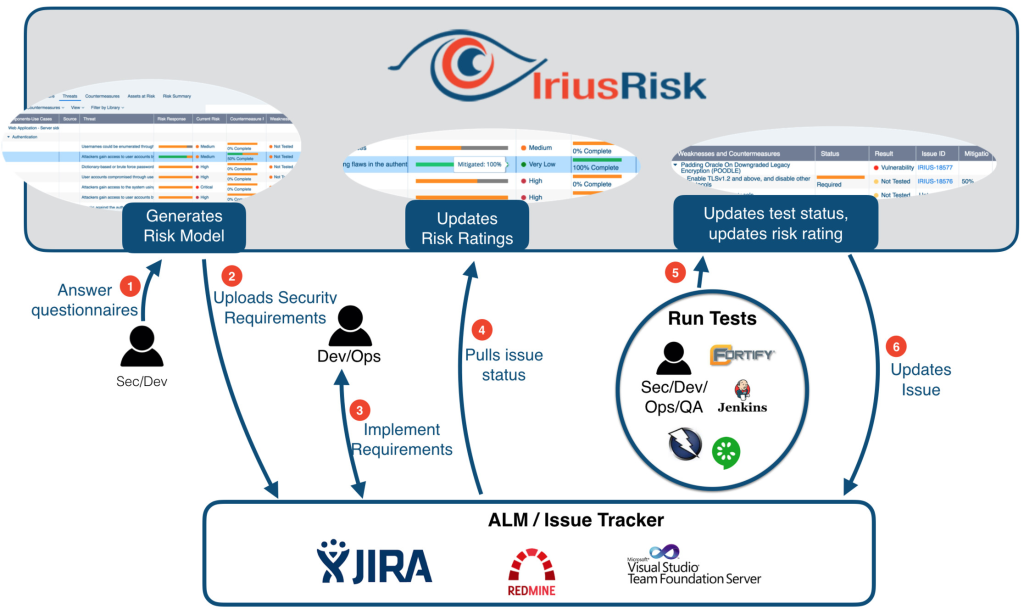
IriusRisk operates through a three-part workflow combining user input, automated analysis, and collaboration tools:
1. User Input:
- Define your system architecture: You can upload or create diagrams using Draw.io or directly within IriusRisk.
- Identify assets and data flows: Specify sensitive data and its movement within the system.
- Provide system details: Define security objectives, components, and trust boundaries.
2. Automated Analysis:
- Threat generation: IriusRisk leverages its built-in library of risks and vulnerabilities, combined with your system architecture, to automatically generate potential threats.
- Real-time assessment: As you define your system, IriusRisk dynamically analyzes it and updates the threat model in real-time.
- Scenario-based focus: If desired, you can define specific attack scenarios to tailor the threat identification and mitigation focus.
3. Collaboration and Refinement:
- Interactive threat model: Edit and refine the generated threats, prioritizing them based on impact and likelihood.
- Collaborative environment: Multiple users can work on the same threat model simultaneously, fostering discussion and refinement.
- Integration and reporting: Generate detailed reports for sharing with stakeholders or integrate findings with your development workflow and issue trackers.
IriusRisk Architecture:
The platform comprises several key components:
- Client application: Provides the user interface for creating, editing, and collaborating on threat models.
- Threat and mitigation libraries: Contain pre-defined patterns and data based on industry standards and best practices.
- Analysis engine: Utilizes the libraries and your system definition to generate and assess threats in real-time.
- Collaboration system: Enables multi-user access and simultaneous editing of threat models.
- Reporting module: Generates comprehensive reports summarizing the threat model, identified threats, mitigation strategies, and rationale.
- API interface: Allows for integration with other tools and development workflows.
Key characteristics of IriusRisk’s architecture:
- Modular and scalable: Can handle small projects and large, complex systems efficiently.
- Real-time analysis: Offers dynamic adaptation to changes in your system design.
- Automation and accessibility: Empowers non-security experts to participate in threat modeling.
- Collaboration-centric: Facilitates team discussions and shared decision-making.
IriusRisk stands out with its focus on automation, accessibility, and collaboration, making it a valuable tool for organizations looking to streamline and improve their software security posture through user-driven threat modeling.
How to Install IriusRisk it?
Here are the general steps to install IriusRisk:
1. Choose Your Deployment Option:
- Cloud-based SaaS: Access the platform directly through a web browser, with IriusRisk handling setup and maintenance. This is the most common and suitable option.
- On-Premises: Install IriusRisk on your own servers for full control and customization. This requires more technical expertise and resource management.
2. Sign Up for a Free Trial or Request a Demo:
- Visit the IriusRisk official website and create a free account to try the cloud-based version.
- For on-premises installation or a tailored demo, contact IriusRisk’s sales team.
3. Follow the Installation Instructions:
- Cloud-Based: No installation required; simply log in to the web interface.
- On-Premises: Download the installation files and follow the provided documentation for setup, configuration, and integration with your infrastructure.
Specific Steps for On-Premises Installation:
- Environment Requirements:
- Server with Java 8 or higher
- PostgreSQL database
- Docker (optional, for easier setup)
- Download Files: Obtain the installation package from IriusRisk’s website or support team.
- Run Installation Script: Execute the provided script to install the platform components.
- Configure Database: Set up the PostgreSQL database with necessary credentials.
- Start IriusRisk: Launch the application and create an initial administrator account.
- Access the Platform: Access IriusRisk through a web browser using the provided URL and login credentials.
Basic Tutorials of IriusRisk: Getting Started

IriusRisk provides a user-friendly interface and intelligent threat modeling features, making it accessible even for beginners. Following is a step-by-step guide to get you started:
1. Create a Free Account:
Visit the IriusRisk official website and click “Sign Up for Free.” Enter your email and desired password, then validate your account through the confirmation email.
2. Draw or Import your System Architecture:
Click “New Threat Model” and choose “Blank Model.” Alternatively, import an existing diagram through “External Model” or use Draw.io integration directly within IriusRisk.
3. Define Assets and Data Flows:
Identify sensitive data by adding “Data Store” elements and connecting them to relevant components using arrows for data flow. Click on components and data stores to add descriptions and specify assets you want to protect.
4. Generate and Refine Threats:
Click the “Analyze” tab and choose a category from the STRIDE list (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) to automatically generate potential threats based on your system architecture. Review and refine these threats, prioritizing them based on impact and likelihood.
5. Identify Mitigations:
For each threat, IriusRisk suggests potential mitigation strategies. Choose relevant ones or add your own custom countermeasures to address vulnerabilities.
6. Collaborate and Refine:
Invite team members to your threat model using email addresses. They can access and work on the same model simultaneously, facilitating discussion and refining the threat analysis and mitigation strategies.
7. Generate and Share Reports:
Click “Report” to generate a comprehensive HTML document summarizing your threat model, identified threats, chosen mitigations, and rationale behind decisions. Share these reports with stakeholders to communicate security risks and mitigation plans.
8. Continuous Improvement:
Remember, threat modeling is an iterative process. As your system evolves, revisit your model, refine threats and mitigations, and adjust your security posture accordingly.
Bonus Tips:
- Utilize IriusRisk’s built-in tutorials and templates for further guidance.
- Leverage the threat libraries for pre-defined threats and mitigations relevant to common system types.
- Integrate IriusRisk with your development workflow and issue trackers for seamless security integration.
With these basic steps and continued exploration, you can leverage IriusRisk’s powerful features to build secure software by design and improve your overall security posture.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

