What is Istio?
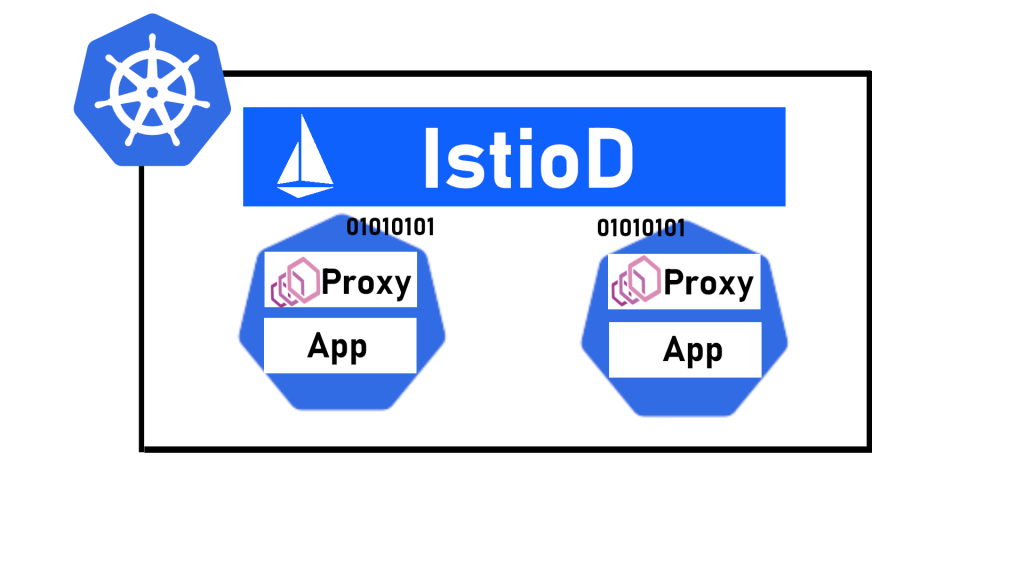
Istio is an open-source service mesh technology that provides a powerful way to manage and control communication between microservices in a distributed environment. It acts as a transparent layer on top of your existing services, enabling features like:
- Traffic management: Route traffic between services, implement load balancing, and control request flows.
- Security: Enforce authorization policies, encrypt communication, and authenticate services.
- Observability: Collect telemetry data about service behavior and make it easily accessible for monitoring and troubleshooting.
Top 10 use cases of Istio?
Top 10 Use Cases of Istio:
- Simplify microservice communication: Abstract away complex networking concerns like service discovery, routing, and load balancing, allowing developers to focus on business logic.
- Enhance security: Implement consistent authentication, authorization, and encryption across all services, mitigating security risks.
- Improve observability: Gain deep insights into service behavior through detailed telemetry data, aiding in debugging, performance optimization, and troubleshooting.
- Implement traffic management strategies: Control how traffic flows between services, enabling A/B testing, canary deployments, and blue-green deployments.
- Enforce rate limiting and quotas: Prevent service overload and manage resource usage effectively.
- Enable policy-driven control: Define and enforce policies across services for things like access control, fault tolerance, and retries.
- Simplify multi-cloud and hybrid deployments: Istio operates consistently across different cloud environments and on-premises infrastructure.
- Facilitate service discovery and registration: Services automatically discover and register themselves with Istio, simplifying service interactions.
- Promote platform-agnostic development: Developers can focus on service logic without worrying about specific underlying infrastructure details.
- Integrate with diverse tools and technologies: Istio offers extensive integrations with popular monitoring, logging, and tracing tools.
Tips:
- Istio is primarily beneficial for organizations with complex microservice architectures requiring robust traffic management, security, and observability.
- While offering significant advantages, adopting Istio introduces additional complexity. Careful evaluation and planning are crucial before implementation.
Istio can be a valuable tool for managing and optimizing microservice communication, but its value depends on your specific architectural needs and development practices.
What are the feature of Istio?
Istio boasts a comprehensive set of features designed to manage and secure communication between microservices in a distributed environment. Following is a breakdown of some key functionalities:
Traffic Management:
- Traffic routing: Rule-based routing for directing traffic to specific services based on various criteria (e.g., service version, workload, time of day).
- Load balancing: Efficient distribution of traffic across multiple instances of a service for high availability and scalability.
- Fault injection: Simulation of service failures to test resilience and preparedness for various scenarios.
- Service discovery and registration: Automatic discovery and registration of services within the mesh, streamlining communication.
- Traffic splitting: A/B testing and canary deployments by routing traffic fractions to different service versions.
Security:
- Mutual TLS (mTLS): Encryption of all communication between services for enhanced security and confidentiality.
- Authentication and authorization: Enforcement of role-based access control policies to restrict unauthorized access.
- Policy-based authorization: Define and enforce granular access control policies based on specific attributes or conditions.
- Network security: Integration with security tools like firewalls and intrusion detection systems for additional protection.
Observability:
- Telemetry collection: Gathering detailed metrics, logs, and traces about service behavior and communication.
- Distributed tracing: Tracking requests across multiple services to understand service interactions and performance bottlenecks.
- Monitoring and alerting: Integration with monitoring tools for visualizing telemetry data and receiving alerts for anomalies.
- Debugging and troubleshooting: Leveraging telemetry data to diagnose and resolve issues within the mesh.
Extra Features:
- Policy enforcement: Define and enforce various policies across services, including rate limiting, timeouts, and retries.
- Multi-cluster and hybrid deployments: Consistent operation across different cloud environments and on-premises infrastructure.
- Extensibility: Integration with diverse tools and technologies through plugins and custom configurations.
- Metrics and configuration management: Centralized management of metrics and configurations for all services in the mesh.
Tips:
- Istio offers a vast feature set, but the specific features you utilize will depend on your specific needs and architecture.
- Implementing Istio introduces additional complexity, so careful planning and evaluation are crucial before deployment.
By understanding Istio’s features and how they can be applied, you can leverage its capabilities to effectively manage, secure, and gain insights into your microservice communications, ultimately improving the performance, reliability, and security of your distributed applications.
How Istio works and Architecture?
Istio operates as a service mesh, adding a transparent layer on top of your existing microservices to manage and control their communication. Let’s delve into its architecture and how it functions:
Core Components:
- Data Plane:
- Composed of lightweight Envoy proxies deployed as sidecars alongside each microservice.
- These proxies intercept and manage all network traffic between services, enforcing policies and facilitating communication.
- Envoy acts as the “traffic cop,” routing, securing, and monitoring service interactions.
- Control Plane:
- Comprises multiple components responsible for configuration, management, and policy enforcement.
- Includes:
- Pilot: Manages service discovery, routing rules, and traffic splitting strategies.
- Citadel: Handles authentication, authorization, and identity management.
- Mixer: Enforces policies like access control, rate limiting, and telemetry collection.
- Telemetry:
- Collects comprehensive data about service interactions through the data plane.
- Includes metrics, logs, and traces to provide deep insights into service behavior and communication.
- Enables monitoring, troubleshooting, and performance optimization.
Functioning Process:
- Service Discovery and Registration:
- Services automatically register with the service mesh through Istio, eliminating manual configuration.
- Pilot maintains an up-to-date service registry for efficient communication.
- Traffic Routing:
- Pilot instructs Envoy proxies on how to route traffic based on defined rules and policies.
- This can involve load balancing, routing based on service versions, or A/B testing configurations.
- Policy Enforcement:
- Mixer receives requests from Envoy proxies and applies defined policies for:
- Authentication and authorization (e.g., verifying service identity, enforcing access control).
- Rate limiting and quotas to prevent service overload.
- Fault injection for simulating failures and testing service resilience.
- Telemetry collection for gathering data about service interactions.
- Mixer receives requests from Envoy proxies and applies defined policies for:
- Security:
- mTLS (mutual TLS) encryption secures communication between services within the mesh.
- Citadel manages service identities and authentication, ensuring secure interactions.
- Observability:
- Telemetry data collected by Mixer allows for:
- Monitoring service performance and identifying potential issues.
- Debugging and troubleshooting communication problems.
- Gaining insights into service interactions and dependencies.
- Telemetry data collected by Mixer allows for:
Architecture Highlights:
- Decentralized data plane: Envoy proxies handle traffic management and enforcement at the service level, providing scalability and resilience.
- Centralized control plane: Manages configuration, policies, and service discovery globally for consistent control.
- Platform-agnostic: Operates across various cloud environments and on-premises infrastructure.
- Extensible: Integrates with diverse tools and technologies through plugins and custom configurations.
Note:
- Istio’s architecture offers powerful capabilities, but its complexity necessitates careful planning and implementation.
- Understanding how each component interacts is crucial for leveraging its features effectively.
By understanding Istio’s architecture and core functions, you can effectively utilize its capabilities to manage, secure, and gain valuable insights into your service mesh, ultimately enhancing the performance, reliability, and security of your distributed application landscape.
How to Install Istio it?
Installing Istio can involve different approaches depending on your environment and desired setup. Here’s a breakdown of the key methods:
1. Installation with Istioctl:
- Istioctl is the official Istio command-line tool for installation and management.
- It offers various installation profiles (e.g., “demo”, “default”) tailored to different use cases.
- Requires administrative access to your Kubernetes cluster and familiarity with command-line operations.
- Refer to Istio site for detailed instructions and configuration options.
2. Installation with Helm:
- Helm is a popular package manager for Kubernetes, simplifying Istio deployment.
- Istio provides pre-built Helm charts for various platforms and configurations.
- Requires Helm installed on your system and basic understanding of Helm commands.
- Refer to Istio official site for Helm chart details and usage instructions.
3. Platform-specific Installers:
- Some cloud providers (e.g., Google Kubernetes Engine, Azure Kubernetes Service) offer managed Istio services or simplified installation methods.
- These options typically involve following provider-specific guides and using their management consoles or tools.
- Check your cloud provider’s documentation for specific instructions and compatibility details.
4. Additional Considerations:
- Environment: Choose the installation method that aligns with your environment (Kubernetes cluster, bare metal, etc.).
- Complexity: Istioctl offers more flexibility but requires more manual configuration. Helm simplifies deployment but might limit customization.
- Security: Ensure proper security configurations and access control during installation and subsequent management.
- Testing and validation: After installation, thoroughly test Istio functionality and validate its integration with your services.
By understanding the available options and carefully planning your installation approach, you can successfully deploy Istio and leverage its capabilities to manage and secure your distributed application infrastructure.
Basic Tutorials of Istio: Getting Started

Istio is a powerful service mesh technology, but it can seem complex initially. To help you get started, I’ll provide step-by-step tutorials for two beginner-friendly scenarios:
Scenario 1: Exploring Istio with Bookinfo Application
This scenario uses the Bookinfo application, a microservices demo, to understand Istio’s basic functionalities.
Prerequisites:
- Kubernetes cluster (minikube, Docker Desktop, or managed platform)
- Istioctl installed and configured
Steps:
- Deploy Bookinfo application:
- Follow the Istio official site.
- This deploys multiple microservices representing a book recommendation system.
- Install Istio:
- Use Istioctl to install Istio on your Kubernetes cluster. Refer to the Istio official site:
- Explore Istio features:
- Traffic Management:
- Use
istioctl authn tls route ratelimit reviewcommands to explore traffic routing, authentication, authorization, and rate limiting. - View service mesh visualization in the Istio dashboard (usually accessible at http://localhost:19000).
- Use
- Traffic Management:
- Monitor your application:
- Install Prometheus and Grafana through Istio addons.
- Track and visualize application metrics and Istio control plane metrics.
- Clean up:
- Delete the Bookinfo application and Istio deployment using
kubectl delete.
- Delete the Bookinfo application and Istio deployment using
Scenario 2: Simple Traffic Routing with Deployment
This scenario demonstrates basic traffic routing using Istio in a simple deployment.
Prerequisites:
- Kubernetes cluster (minikube, Docker Desktop, or managed platform)
- Istioctl installed and configured
Steps:
- Deploy a simple application:
- Create a simple Deployment (e.g., Nginx container) in your Kubernetes cluster.
- Configure Istio Ingress Gateway:
- Create an Istio IngressGateway resource to expose your application externally.
- Use
istioctl createcommand with appropriate YAML configuration.
- Route traffic:
- Create an Istio VirtualService resource to route traffic to your application.
- Specify rules for routing based on HTTP path, headers, or other criteria.
- Test your application:
- Access your application using the Ingress Gateway’s external IP and configured port.
- Verify traffic routing based on your VirtualService rules.
- Clean up:
- Delete the Deployment, IngressGateway, and VirtualService resources using
kubectl delete.
- Delete the Deployment, IngressGateway, and VirtualService resources using
Always keep in mind, these are basic tutorials. As you explore Istio further, you’ll discover more advanced functionalities and configurations.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

