What is Keyfactor?

Keyfactor is a cybersecurity company that specializes in digital identity and security solutions, particularly focusing on the management and security of digital certificates, cryptographic keys, and digital identities. Keyfactor’s products and services are designed to help organizations safeguard their digital assets, ensure compliance with security policies, and protect against cybersecurity threats.
Overall, Keyfactor’s solutions play a critical role in helping organizations manage and secure their digital identities, certificates, and cryptographic keys, which are essential components of modern cybersecurity and data protection strategies. These solutions provide visibility, control, and automation to mitigate risks and enhance the security posture of organizations.
Top 10 use cases of Keyfactor:
Here are the top 10 use cases for Keyfactor’s solutions:
- Certificate Lifecycle Management: Keyfactor helps organizations manage the complete lifecycle of digital certificates, including issuance, renewal, revocation, and retirement. This ensures certificates are always up-to-date and compliant.
- Key Management: Protecting cryptographic keys is crucial for securing sensitive data and applications. Keyfactor assists in the secure generation, storage, and management of cryptographic keys.
- PKI (Public Key Infrastructure) Management: Keyfactor can serve as a central platform for managing all aspects of a PKI, including certificate authorities (CAs), certificate issuance, and certificate policies.
- Identity and Access Management: Keyfactor helps organizations manage digital identities and access controls, ensuring that only authorized individuals or devices can access critical systems and data.
- IoT Device Security: As the Internet of Things (IoT) grows, securing IoT device identities and ensuring their trustworthiness becomes crucial. Keyfactor provides solutions for managing and securing IoT device identities and keys.
- Code Signing Certificate Management: Organizations use code signing certificates to authenticate the source and integrity of software. Keyfactor assists in managing code signing certificates to prevent the distribution of malicious code.
- Compliance and Audit: Keyfactor’s solutions help organizations enforce security policies and maintain compliance with industry regulations, such as GDPR, HIPAA, or industry-specific standards.
- Cloud and DevOps Integration: In cloud and DevOps environments, Keyfactor integrates seamlessly to ensure that cryptographic assets are managed and secured as part of automated workflows.
- Secure Communication: Keyfactor helps organizations secure communication channels, such as SSL/TLS encryption, ensuring that data transmitted over networks is protected from eavesdropping.
- Threat Detection and Response: Keyfactor’s solutions can detect unusual certificate or key activity that may indicate a security threat, allowing organizations to respond promptly to potential breaches or misuse.
What are the feature of Keyfactor?
Keyfactor offers a range of features and capabilities designed to help organizations manage and secure their digital identities, certificates, and cryptographic keys. While the specific features may vary depending on the product or solution within the Keyfactor portfolio, here are some common features and functionalities associated with Keyfactor’s offerings:
- Certificate Lifecycle Management: Keyfactor provides tools to manage the entire lifecycle of digital certificates, including issuance, renewal, revocation, and retirement, ensuring certificates are always up-to-date and compliant.
- Key Management: Keyfactor helps organizations securely generate, store, and manage cryptographic keys, protecting them from unauthorized access or misuse.
- PKI (Public Key Infrastructure) Management: Keyfactor can serve as a central platform for managing PKI components, including CAs, certificate issuance, and policy enforcement.
- Identity and Access Management: Keyfactor offers solutions to manage digital identities, enforce access controls, and ensure that only authorized users or devices can access critical resources.
- IoT Device Security: Keyfactor helps secure IoT device identities and keys, ensuring the trustworthiness of devices connected to the network.
- Code Signing Certificate Management: Keyfactor assists in the management of code signing certificates, helping to verify the authenticity and integrity of software.
- Compliance and Audit: Keyfactor helps organizations enforce security policies and maintain compliance with industry regulations through policy enforcement and reporting.
- Cloud and DevOps Integration: Keyfactor seamlessly integrates with cloud environments and DevOps pipelines, ensuring that cryptographic assets are managed and secured in dynamic, automated infrastructures.
- Secure Communication: Keyfactor helps secure communication channels, such as SSL/TLS encryption, protecting data transmitted over networks.
- Threat Detection and Response: Keyfactor can detect unusual certificate or key activity, providing insights and alerts for potential security threats or misuse.
How Keyfactor works and Architecture?
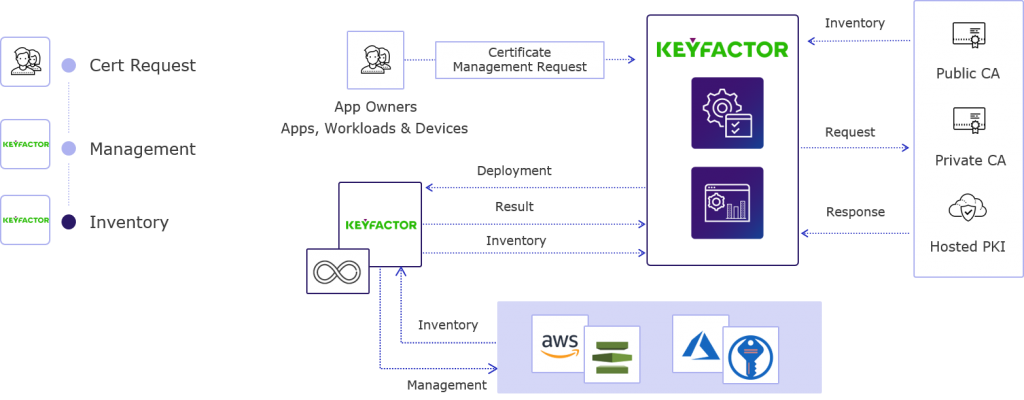
Keyfactor’s architecture and how it works can vary depending on the specific product or solution being used, but here’s a general overview of how Keyfactor typically operates:
- Certificate and Key Discovery: Keyfactor often deploys agents or collectors across an organization’s network to discover and inventory digital certificates and keys. These agents periodically scan the network and collect relevant information.
- Policy Enforcement: Organizations define security policies within the Keyfactor platform, specifying rules and criteria that certificates and keys must adhere to. Keyfactor enforces these policies and alerts administrators when violations occur.
- Certificate and Key Management: Keyfactor centralizes the management of certificates and keys, allowing administrators to request, issue, renew, and revoke certificates as needed. This includes integration with certificate authorities for automated issuance and renewal.
- Key Protection: Keyfactor safeguards private keys associated with certificates, encrypting and storing them securely to prevent unauthorized access.
- Monitoring and Analytics: Keyfactor continuously monitors certificate and key usage and behavior, providing insights and alerts for potential security threats or policy violations.
- Reporting and Compliance: Keyfactor generates reports and audit trails to demonstrate compliance with industry regulations and internal security policies.
- Integration: Keyfactor integrates with various systems and tools within an organization’s IT infrastructure, including CA systems, cloud platforms, DevOps pipelines, and SIEM systems.
- Alerting and Response: Keyfactor can trigger alerts and responses when it detects suspicious or non-compliant certificate or key activity, allowing organizations to take action promptly.
Overall, Keyfactor’s architecture is designed to provide centralized visibility, control, and security for an organization’s digital identities, certificates, and cryptographic keys. This helps mitigate risks associated with certificates and keys while ensuring compliance with security policies and industry standards. Specific implementations may vary depending on an organization’s needs and the Keyfactor products in use.
How to Install Keyfactor?
To install Keyfactor, you will need to download the Keyfactor Universal Orchestrator installer for your operating system. The installer is available from the Keyfactor website.
Once you have downloaded the installer, follow these steps to install Keyfactor:
- Run the installer.
- Select the installation options you want.
- Click Next to continue.
- Enter the required information, such as the database server name and credentials.
- Click Next to continue.
- Review the installation summary and click Finish to install Keyfactor.
Once Keyfactor is installed, you will need to configure it. To do this, open a web browser and go to the Keyfactor Universal Orchestrator web console. The web console URL is typically https://localhost:8443.
At the login screen, type the username and password you generated during the installation process.
Once you are logged in, you can start configuring Keyfactor. For more information on configuring Keyfactor, please refer to the Keyfactor documentation.
Some additional tips for installing Keyfactor:
- Make sure that your server meets the system requirements for Keyfactor.
- If you are installing Keyfactor on a Windows server, you will need to install the Microsoft Visual C++ 2019 Redistributable (x64).
- If you are installing Keyfactor on a Linux server, you will need to install the following packages:
openssh-server
openssh-client
java-11-openjdk-devel- If you are using a database other than MySQL, you will need to install the appropriate JDBC driver.
- If you are using a load balancer, you will need to configure it to forward traffic to the Keyfactor Universal Orchestrator server.
Once you have installed and configured Keyfactor, you can start using it to manage your digital certificates, machine identities, and encryption keys.
Basic Tutorials of Keyfactor: Getting Started
The following steps are the basic Tutorials of Keyfactor:
Keyfactor offers a variety of basic tutorials to help you get started with its solutions. These tutorials cover a wide range of topics, including:
- How to create and manage digital certificates
- How to manage SSH keys
- How to manage API keys
- How to integrate Keyfactor with other security solutions
To access Keyfactor’s basic tutorials, follow these steps:
- Go to the Keyfactor website: https://keyfactor.com/
- Click on the Support tab
- Click on the Tutorials link
- Under the Basic Tutorials section, click on the topic you want to learn about
How to Create and Manage Digital Certificates
To create and manage digital certificates using Keyfactor, follow these steps:
- Go to the Keyfactor Certificates page
- Click on the New Certificate button
- Select the type of certificate you want to create
- Enter the required information, such as the certificate subject, common name, and validity period
- Click on the Create Certificate button
To manage your digital certificates, you can use the Keyfactor Certificates page. This page allows you to view all of your certificates, renew certificates, and revoke certificates.
How to Manage SSH Keys
To manage SSH keys using Keyfactor, follow these steps:
- Go to the Keyfactor SSH Keys page
- Click on the New SSH Key button
- Enter the required information, such as the SSH key name and type
- Click on the Create SSH Key button
To manage your SSH keys, you can use the Keyfactor SSH Keys page. This page allows you to view all of your SSH keys, rotate keys, and disable keys.
How to Manage API Keys
To manage API keys using Keyfactor, follow these steps:
- Go to the Keyfactor API Keys page
- Click on the New API Key button
- Enter the required information, such as the API key name and description
- Click on the Create API Key button
To manage your API keys, you can use the Keyfactor API Keys page. This page allows you to view all of your API keys, rotate keys, and revoke keys.
How to Integrate Keyfactor with Other Security Solutions
Keyfactor can be integrated with a variety of other security solutions, such as firewalls, intrusion detection systems, and security information and event management (SIEM) systems.
To integrate Keyfactor with another security solution, you will need to consult the documentation for both solutions.
Example Step-by-step Basic Tutorial: How to Create and Manage Digital Certificates
To create a digital certificate using Keyfactor, follow these steps:
- Go to the Keyfactor Certificates page
- Click on the New Certificate button
- Select the type of certificate you want to create. For example, to create a web server certificate, select the Web Server Certificate option.
- Enter the required information, such as the certificate subject, common name, and validity period.
- Click on the Create Certificate button.
To view your digital certificates, go to the Keyfactor Certificates page.
To renew a digital certificate, go to the Keyfactor Certificates page, click on the certificate you want to renew, and then click on the Renew Certificate button.
To revoke a digital certificate, go to the Keyfactor Certificates page, click on the certificate you want to revoke, and then click on the Revoke Certificate button.
Keyfactor offers a variety of basic tutorials to help you get started with its solutions. These tutorials cover a wide range of topics, including how to create and manage digital certificates, SSH keys, and API keys.
Additional Tips for Using Keyfactor
- Use Keyfactor’s role-based access control feature to restrict access to Keyfactor to authorized users.
- Use Keyfactor’s audit logging feature to track all activity in Keyfactor.
- Use Keyfactor’s two-factor authentication feature to add an extra layer of security to your Keyfactor account.
- Keep your Keyfactor software up to date with the latest security patches.
By following these tips, you can help to ensure that your digital identities
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

