What is Linkerd?

Linkerd is an open-source service mesh platform designed to simplify and secure service-to-service communication in your cloud native applications. It operates as a lightweight sidecar proxy deployed alongside your microservices, providing critical functionalities like:
- Traffic management: Route traffic between services, implement load balancing, and control how requests flow.
- Security: Enforce authorization policies, encrypt communication, and authenticate services for enhanced security.
- Observability: Collect telemetry data about service behavior and make it readily accessible for monitoring and troubleshooting.
Top 10 use cases of Linkerd?
Top 10 Use Cases of Linkerd:
- Effortless service mesh adoption: Linkerd boasts a straightforward installation and configuration process, minimizing complexity for microservice environments.
- Streamlined traffic management: Easily define routing rules, implement load balancing strategies, and manage service dependencies through intuitive controls.
- Robust security by default: Linkerd enforces mutual TLS (mTLS) encryption and zero-trust security principles across all service communication, reducing security risks.
- Detailed observability: Gain deep insights into service behavior through comprehensive telemetry data collection, aiding in performance optimization and issue identification.
- Simplified debugging and troubleshooting: Linkerd’s transparent architecture and rich diagnostics facilitate efficient debugging and problem resolution within the service mesh.
- Resilience and fault tolerance: Linkerd enables configuring retries, timeouts, and circuit breaker patterns to enhance service resilience and handle failures gracefully.
- Platform-agnostic deployment: Linkerd operates consistently across diverse cloud environments and on-premises infrastructure, offering flexibility and portability.
- Developer experience focus: Linkerd prioritizes developer experience with features like automatic proxy injection and clear documentation, reducing development overhead.
- Cost-effective solution: Linkerd is an open-source project with a focus on efficiency and resource optimization, minimizing infrastructure costs.
- Active community and support: A vibrant community and ample resources provide assistance and best practices for successful Linkerd adoption and troubleshooting.
Note:
- Linkerd is particularly beneficial for organizations with microservice architectures seeking a lightweight and efficient service mesh solution.
- While providing significant advantages, it’s essential to evaluate its suitability for your specific needs and infrastructure setup.
What are the feature of Linkerd?
Linkerd offers a comprehensive set of features designed to manage and secure service communication in a cloud native environment through a service mesh architecture here are some key highlights of its capabilities and features include but may not be limited to the following :
Traffic Management and Routing Strategies
- Traffic routing based on various attributes: Linkerd allows you to route traffic based on different attributes such as source and destination service identities or versions or based on specific application tags .
- Advanced routing with rate limiting and timeouts: You can implement rate limiting and timeouts to control the flow of traffic and enforce specific quality of service requirements for different workloads or services within the mesh
- Canary deployments and A / B testing: Linkerd can be used to facilitate canary deployments and A / B testing by routing traffic to different versions of a service in a controlled manner .
- Layer – seven traffic management: It is capable of managing traffic at layer seven , meaning it can make routing decisions based on application layer details like HTTP path or method .
Security and Authentication
- **Automatic mutual TLS ( mTLS ): Linkerd enforces mutual TLS ( mTLS ) by default , meaning that all communication between services within the service mesh is encrypted .
- **Policy based access control : It allows you to implement policy – based access control to restrict access to certain services or resources based on specific criteria .
- Integration with external security systems: Linkerd can be integrated with external security systems like firewalls and intrusion detection systems to provide additional layers of security .
Observability and Monitoring
- Automatic metrics and tracing collection: Linkerd automatically collects metrics and traces from all services within the mesh , which can be used for monitoring , troubleshooting , and performance optimization .
- Integration with Prometheus and Grafana: It can be integrated with Prometheus and Grafana to collect , store , and visualize these metrics and traces at scale .
- Canary analysis and service fault injection:It allows you to perform canary analysis and fault injection to simulate failures and test how your services would behave in such situations .
Additional Features
- Multiple language and platform support: Linkerd is language and platform – agnostic , meaning it can be used with various programming languages and deployed on different cloud platforms .
- Automatic sidecar injection: It can automatically inject its sidecar proxy onto your services without requiring any code changes , simplifying adoption and management .
- Service discovery and registration: Services can automatically register themselves with Linkerd , and it takes care of service discovery for you .
By understanding the features of Linkerd and how they can be applied in your environment , you can leverage its capabilities to manage traffic , enforce security , and gain valuable insights into your service mesh , ultimately improving the control , observability , and performance of your distributed applications .
How Linkerd works and Architecture?
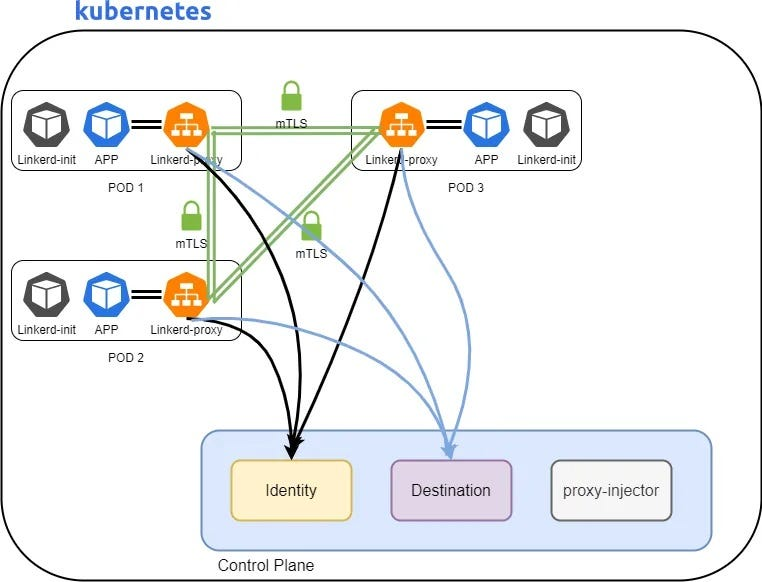
Linkerd operates as a service mesh, providing transparent management and security for service-to-service communication in your cloud-native applications. Here’s a breakdown of its architecture and how it functions:
Core Components:
- Data Plane:
- Consists of lightweight Linkerd proxies deployed as sidecars alongside each microservice within the mesh.
- These proxies intercept and manage all network traffic between services, handling routing, security, and observability tasks.
- Think of them as intelligent traffic managers ensuring smooth and secure communication.
- Control Plane:
- Comprises several components responsible for centralized configuration, policy enforcement, and service discovery.
- Key parts include:
- buoyant: Manages service discovery, routing rules, and load balancing strategies.
- citadel: Handles authentication, authorization, and identity management for secure communication.
- tap: Collects telemetry data about service interactions for observability and monitoring.
- Telemetry:
- Gathers comprehensive data about service interactions through the data plane proxies.
- Includes metrics, logs, and traces to provide deep insights into service behavior and communication patterns.
- Enables effective monitoring, troubleshooting, and performance optimization.
Functioning Process:
- Service Deployment:
- Linkerd automatically injects its sidecar proxy alongside each microservice during deployment.
- This transparent injection requires minimal code changes, simplifying adoption.
- Service Discovery and Registration:
- Services automatically register themselves with Linkerd, eliminating manual configuration and facilitating communication within the mesh.
- Traffic Routing:
- The control plane instructs the data plane proxies on how to route traffic based on defined rules and policies.
- This can involve load balancing, routing based on service versions, or implementing A/B testing strategies.
- Security Enforcement:
- Linkerd enforces mutual TLS (mTLS) encryption by default, securing all communication between services within the mesh.
- Citadel manages service identities and authorization policies, preventing unauthorized access.
- Observability:
- Telemetry data collected by the data plane is sent to the control plane for processing and analysis.
- This data empowers developers and operators with insights into service performance, potential issues, and communication patterns.
Architecture Highlights:
- Decentralized data plane: Sidecar proxies handle traffic management and enforcement at the service level, offering scalability and resilience.
- Centralized control plane: Manages configuration, policies, and service discovery globally for consistent control and governance.
- Language and platform-agnostic: Operates across various programming languages and cloud platforms, providing flexibility and portability.
- Automatic and transparent: Minimizes manual configuration and overhead for a streamlined adoption experience.
By understanding Linkerd’s architecture and core functions, you can effectively leverage its capabilities to manage, secure, and gain valuable insights into your service mesh, ultimately enhancing the performance, reliability, and security of your distributed application landscape.
How to Install Linkerd it?
Installing Linkerd involves deploying its components onto your Kubernetes cluster. The specific method you choose depends on your familiarity with the platform and desired level of control. Here are the main options:
1. Installer (Recommended):
- The recommended approach for most users.
- Uses a single command to download and configure Linkerd components.
- Offers various installation profiles (e.g., “basic”, “production”) catering to different needs.
- Requires administrative access to your Kubernetes cluster and basic understanding of command-line operations.
- Refer to Linkerd official site for detailed instructions and configuration options.
2. Helm Charts:
- Suitable for experienced users comfortable with Helm package manager.
- Leverages pre-built Helm charts to deploy Linkerd with specific configurations.
- Provides more flexibility than the installer but requires manual configuration and understanding of Helm concepts.
- Refer to Linkerd official site for Helm chart details and usage instructions.
3. Platform-Specific Methods:
- Some cloud providers offer managed Linkerd services or simplified installation methods.
- These options typically involve following provider-specific guides and using their management consoles or tools.
- Check your cloud provider’s documentation for specific instructions and compatibility details.
Additional Considerations:
- Environment: Choose the installation method that aligns with your environment (Kubernetes cluster version, cloud provider, etc.).
- Complexity: The installer offers simplicity but less customization. Helm charts provide more flexibility but require more configuration.
- Security: Ensure proper security configurations and access control during installation and subsequent management.
- Testing and validation: After installation, thoroughly test Linkerd functionality and validate its integration with your services.
By choosing the right installation method and following best practices, you can successfully deploy Linkerd and leverage its capabilities to manage and secure service-to-service communication within your cloud-native applications.
Basic Tutorials of Linkerd: Getting Started

Linkerd is another powerful service mesh, and like Istio, it can seem complex at first. Here are two beginner-friendly step-by-step tutorials to get you started:
Scenario 1: Deploying Hello World with Linkerd on Minikube
This scenario guides you through deploying a simple “Hello World” application with Linkerd on a local Minikube cluster.
Prerequisites:
- kubectl configured for your Minikube cluster
- Linkerd CLI installed and configured
Steps:
- Download the Hello World Deployment:
wget <invalid URL removed>
2. Deploy the application:
kubectl apply -f hello-world.yaml
3. Install Linkerd:
linkerd install --set global.istio.operator.manifestsPath=linkerd-cni
4. Verify Linkerd installation: linkerd check
5. Access the Hello World service:
kubectl get svc hello-world
Note the external IP address and port. Open a browser and access http://<IP_ADDRESS>:<PORT>. You should see “Hello, world!”.
6. Explore Linkerd features:
- Use
linkerd dep listto view deployed applications. - Use
linkerd stat dep/hello-worldto see application metrics. - Access the Linkerd dashboard at
http://localhost:9990(may require port forwarding).
7. Clean up:
kubectl delete -f hello-world.yaml linkerd uninstall minikube delete
Scenario 2: Traffic Splitting with Linkerd
This scenario demonstrates basic traffic splitting between two versions of a deployed application.
Prerequisites:
- kubectl configured for your Minikube cluster
- Linkerd CLI installed and configured
Steps:
- Deploy two versions of the Hello World application:
kubectl apply -f hello-world-v1.yaml kubectl apply -f hello-world-v2.yaml
2. Configurate traffic splitting: Create a TrafficSplit resource: YAML
apiVersion: linkerd.io/v1alpha1
kind: TrafficSplit
metadata:
name: hello-world-split
spec:
selector:
app: hello-world
backends:
- service: hello-world-v1
weight: 50
- service: hello-world-v2
weight: 50 3. Verify traffic splitting:
- Access the
hello-worldservice endpoint. You should see a mix of v1 and v2 responses. - Monitor access logs of both
hello-world-v1andhello-world-v2pods to see traffic distribution.
4. Clean up:
kubectl delete -f hello-world-v1.yaml
kubectl delete -f hello-world-v2.yaml
kubectl delete -f traffic-split.yaml # … (continue cleanup from Scenario 1)
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

