What is Litmus Chaos?
Litmus Chaos is an end-to-end Chaos Engineering platform specifically designed for cloud-native environments. It empowers you to inject controlled chaos into your applications and infrastructure, uncovering weaknesses and building resilience against real-world disruptions.
Think of it as a stress test on steroids, simulating various failure scenarios like:
- Pod crashes: Simulate unexpected terminations of your application containers.
- Network disruptions: Introduce packet loss, latency, or even complete network partitions.
- Resource limitations: Deplete CPU, memory, or storage resources to test resource handling.
- Chaos at platform level: Inject chaos into services like Kubernetes nodes, disks, and network resources.
- Application-specific faults: Trigger specific errors or exceptions within your application code.
Top 10 use cases of Litmus Chaos?
Top 10 Use Cases of Litmus Chaos:
- Identify Single Points of Failure: Pinpoint critical components that cause cascading failures when disrupted.
- Validate Disaster Recovery Plans: Test your recovery procedures and identify areas for improvement.
- Strengthen System Scalability: Uncover bottlenecks and ensure your system can handle increased load.
- Enhance Security Posture: Simulate cyberattacks and assess your system’s vulnerability.
- Boost Team Collaboration: Foster communication and understanding of system behavior under stress across teams.
- Continuous Improvement: Regularly inject chaos to proactively identify and mitigate potential issues.
- Develop Fault-Tolerant Systems: Design systems that can gracefully handle failures and maintain service.
- Practice Incident Response: Train your team on handling real-world disruptions through simulated scenarios.
- Validate Infrastructure Stability: Test the resilience of your underlying cloud infrastructure.
- Measure System Resilience: Quantify the impact of failures and track improvements over time.
Litmus Chaos offers several advantages:
- Cloud-Native Focus: Specifically designed for Kubernetes and cloud-native applications, integrating seamlessly with existing architectures.
- Diverse Fault Injection: Supports various fault types at both application and platform levels for comprehensive testing.
- Easy to Use: Provides a user-friendly web interface and CLI for experiment design and execution.
- Open-source and Community-driven: Continuously evolving with active community contributions and readily available resources.
Note: Chaos Engineering is a powerful tool, but it’s crucial to use it responsibly and start with small, controlled experiments. By embracing controlled chaos, you can proactively build stronger, more resilient cloud-native systems that can withstand unexpected challenges.
What are the feature of Litmus Chaos?
Litmus Chaos, a popular open-source Chaos Engineering platform, boasts a diverse set of features designed to help you test and strengthen your systems:
Chaos Experimentation:
- Declarative Chaos Experiments: Define chaos scenarios using Kubernetes custom resources (CRs) for easy configuration and management.
- Chaostypes and Fault Injection: Choose from various chaos types like network chaos, pod chaos, resource chaos, and inject faults to simulate real-world failures.
- Chaos Schedules and Automation: Schedule chaos experiments to run periodically or integrate them into CI/CD pipelines for continuous testing.
- Chaos Scenarios and Templates: Build complex chaos scenarios by chaining multiple Chaostypes or utilize pre-built templates for common testing needs.
Observability and Analytics:
- Resilience Probes: Define custom probes to monitor system behavior during chaos experiments and measure their impact.
- Chaos Reports and Analytics: Generate detailed reports summarizing experiment results, including visualizations and analysis of system behavior.
- Integration with Prometheus and Grafana: Export metrics and dashboards for deeper analysis and integration with existing monitoring tools.
- Experiment History and Comparison: Track past experiments, compare results, and identify patterns for effective testing strategies.
Collaboration and Ease of Use:
- GitOps Support: Manage chaos experiments using Git for version control and collaboration.
- Role-Based Access Control: Define user roles and permissions for secure access and management of experiments.
- Intuitive UI and CLI: Leverage a user-friendly web interface and command-line interface for convenient experiment configuration and execution.
- Community and Support: Access a vibrant community of users and developers for support, collaboration, and sharing best practices.
Additional Features:
- Chaos Hub: Discover and share pre-built chaos experiments for various platforms and applications.
- Chaos Engine API: Integrate Litmus Chaos with other tools and platforms through a robust API.
- Custom Scripting: Extend functionality by writing custom scripts for specific chaos scenarios.
- Platform Agnostic: Run chaos experiments on Kubernetes, bare-metal environments, and other platforms.
These are just highlights, and Litmus Chaos offers a comprehensive set of features and functionalities.
How Litmus Chaos works and Architecture?
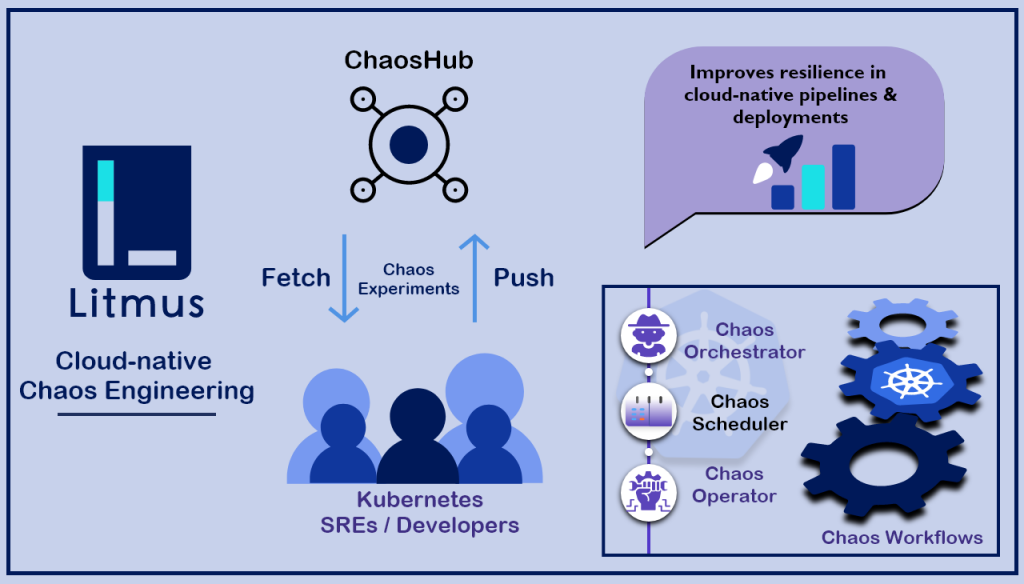
Litmus Chaos works through a well-defined architecture that orchestrates chaos injection and analyzes its impact on your system. Here’s a breakdown:
Components:
- Control Plane:
- ChaosCenter: Web interface for creating, scheduling, and monitoring chaos experiments.
- API Server: Handles API requests from the ChaosCenter and other components.
- Experiment Runner: Responsible for interpreting chaos experiment definitions and scheduling their execution.
- Execution Plane:
- Chaos Runner: Runs on target resources and injects faults based on the experiment definition.
- Chaos Probes: Monitor system behavior during the experiment and collect data.
- Report Generator: Analyzes collected data and generates reports on experiment results.
Workflow:
- Define Chaos Experiment: You configure the desired chaos scenario using Kubernetes custom resources (CRs) through the ChaosCenter.
- Experiment Scheduling: You schedule the experiment to run at a specific time or integrate it into CI/CD pipelines.
- Chaos Injection: The Experiment Runner interprets the CR and instructs the Chaos Runner on the target resources to inject faults according to the specified ChaosTypes (e.g., network disruptions, pod terminations).
- Monitoring and Data Collection: Chaos Probes monitor system behavior during the experiment, gathering metrics and logs.
- Analysis and Reporting: The Report Generator analyzes the collected data and generates detailed reports summarizing the experiment results and system behavior.
- User Insights: You can access the reports and visualizations through the ChaosCenter to gain insights into your system’s resilience and identify potential weaknesses.
Key Architectural Aspects:
- Declarative Chaos Experiments: CRs provide a standardized and readable way to define chaos scenarios.
- Kubernetes-native: Tightly integrates with Kubernetes for seamless deployment and management.
- Scalable and Distributed: Architecture can be scaled to handle large deployments and complex experiments.
- Extensible: Supports custom scripting and integrations for tailored testing needs.
- Open-source: Encourages community contributions and fosters innovation.
This is a high-level overview. The actual architecture might have additional components and functionalities depending on specific configurations and integrations.
How to Install Litmus Chaos it?
Installing Litmus Chaos offers several options to cater to your environment and preferences. Here’s a breakdown of the available methods:
1. Helm:
- Recommended for most users, offering ease of installation and management.
- Add the Litmus Chaos Helm repository:
Bash
helm repo add litmuschaos https://litmuschaos.github.io/litmus-helm/
helm repo update
- Install Litmus Chaos with your desired configuration:
Bash
helm install chaos litmuschaos/litmus --namespace litmus --values values.yaml
- Modify the
values.yamlfile for customizations like namespace, image registry, and resource requests.
2. kubectl:
- Download the Litmus Chaos manifest YAML files from the GitHub releases page: https://github.com/litmuschaos/litmus
- Apply the manifests to your Kubernetes cluster using
kubectl apply:
Bash
kubectl apply -f <path-to-manifests>/litmus*.yaml
- Replace
<path-to-manifests>with the directory where you downloaded the manifests.
3. Docker Compose (for testing):
- Download the Litmus Chaos Docker Compose YAML file from their official site.
- Run the Docker Compose command to deploy Litmus Chaos and a sample application:
Bash
docker-compose up -d
4. Cloud Providers:
- Some cloud providers offer managed Litmus Chaos services, simplifying deployment and management.
- Check the documentation for specific instructions on your chosen platform.
Tips:
- Start with a basic installation and gradually expand and configure as needed.
- Choose the method that best suits your skills and environment.
- Always test your installations in a non-production environment before deploying to production.
Basic Tutorials of Litmus Chaos: Getting Started

Welcome to the world of Litmus Chaos! Here are some stepwise tutorials to guide you through basic chaos injections in your Kubernetes environment:
1. Pod Chaos Tutorial:
a. Prerequisites:
- Kubernetes cluster with kubectl access
- Helm v3 installed
b. Install Litmus Chaos:
- Add the Litmus Chaos repository:
Bash
helm repo add litmuschaos https://charts.litmuschaos.io
- Update the repository:
Bash
helm repo update
- Install Litmus Chaos using Helm:
Bash
helm install litmus litmuschaos/litmus
c. Verify Installation:
Bash
kubectl get pods -n litmus
You should see pods running for various Litmus Chaos components.
d. Choose a Chaos Experiment:
Head over to the ChaosHub officialsite to browse pre-built experiments:
- Select the “pod-chaos” experiment and download its YAML manifest.
e. Modify the Experiment (Optional):
The downloaded manifest defines the experiment parameters:
- target_namespaces: Specify the namespace(s) where pods will be crashed (default: all namespaces).
- percentage: Define the percentage of pods to be crashed within the target namespace(s).
- duration: Set the experiment duration in seconds.
Adjust these parameters as needed based on your desired chaos scenario.
f. Apply the Experiment:
Run the following command, replacing pod-chaos-experiment.yaml with your adjusted manifest filename:
Bash
kubectl apply -f pod-chaos-experiment.yaml
g. Observe the Chaos:
- Pods in the specified namespaces will be randomly crashed based on the experiment settings.
- Monitor your application’s behavior and resilience during the experiment duration.
h. Clean Up:
Once the experiment duration is complete, delete the experiment:
Bash
kubectl delete chaosexperiment pod-chaos-experiment
2. Network Loss Tutorial:
a. Choose a Chaos Experiment:
Navigate to the ChaosHub and choose the “network-chaos” experiment. Download its YAML manifest.
b. Modify the Experiment (Optional):
Similar to the pod chaos experiment, adjust the:
- target_namespaces: Specify the namespace(s) where network loss will be injected.
- percentage: Define the percentage of pods affected by network loss within the target namespace(s).
- loss_percentage: Set the desired network loss percentage for affected pods.
- duration: Set the experiment duration in seconds.
Fine-tune these parameters to fit your desired chaos scenario.
c. Apply the Experiment:
Run the following command, replacing network-chaos-experiment.yaml with your adjusted manifest filename:
Bash
kubectl apply -f network-chaos-experiment.yaml
d. Observe the Chaos:
- Pods in the specified namespaces will experience network loss, impacting their communication and functionality.
- Monitor your application’s behavior and resilience under network disruption.
e. Clean Up:
Once the experiment concludes, delete it:
Bash
kubectl delete chaosexperiment network-chaos-experiment
Bonus Tips:
- Explore the ChaosHub for various pre-built experiments targeting different chaos types like disk stress, CPU throttling, and more.
- Consider starting with simple experiments in non-critical environments before introducing chaos to production systems.
- Utilize the Litmus Chaos web UI for a visual overview of your experiments and system behavior under stress.
Always remember, chaos engineering is about proactively testing your system’s resilience. These tutorials provide a stepping stone for your journey with Litmus Chaos. Have fun experimenting and building robust, resilient Kubernetes environments!
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

