What is Microsoft Identity Manager?

Microsoft Identity Manager (MIM) is an identity and access management (IAM) solution developed by Microsoft. It helps organizations manage user identities, access to resources, and ensure security and compliance.
Microsoft Identity Manager can be particularly valuable for organizations that have a hybrid IT environment with both on-premises and cloud-based systems, as it provides synchronization and management capabilities across various platforms and services. It helps organizations improve security, streamline user management, and enhance the user experience while ensuring compliance with regulatory requirements.
Top 10 use cases of Microsoft Identity Manager:
I have listed the top 10 use cases for Microsoft Identity Manager:
- User Provisioning and De-Provisioning: Automate the creation, modification, and removal of user accounts and access rights based on predefined policies and workflows.
- Identity Synchronization: Synchronize user identities and attributes across on-premises and cloud-based systems, ensuring consistency and accuracy.
- Single Sign-On (SSO): Implement SSO to allow users to access multiple applications with a single set of credentials, improving user productivity and security.
- Access Control and Role-Based Access Control (RBAC): Define and enforce access policies to ensure users have the appropriate permissions to access specific resources and data.
- Multi-Factor Authentication (MFA): Enhance security by requiring users to provide multiple authentication factors, such as passwords and one-time codes, during login.
- Password Management: Implement password policies, including complexity requirements, password reset processes, and self-service password reset options.
- Identity Federation: Enable identity federation to allow users to use their credentials from trusted identity providers to access applications and resources.
- Audit and Compliance Management: Log and monitor user activities, access events, and changes to identities to meet auditing and compliance requirements.
- Behavioral Analysis and Threat Detection: Analyze user behavior and access patterns to detect suspicious activities and potential security threats.
- Self-Service Portals: Provide users with self-service portals to manage their own identities, passwords, and access preferences, reducing administrative overhead.
- Guest Access Management: Manage access for external users, partners, vendors, and guests while ensuring they meet security and compliance requirements before granting access.
- Identity Governance and Compliance: Enforce access policies, regulatory requirements, and auditing to ensure that user access is in compliance with organizational policies.
What are the feature of Microsoft Identity Manager?
Microsoft Identity Manager (MIM) is an identity and access management (IAM) solution developed by Microsoft. It provides a range of features for managing user identities, access to resources, and ensuring security and compliance within organizations. Here are key features of MIM, along with an overview of how it works and its typical architecture:
Key Features of Microsoft Identity Manager (MIM):
- User Lifecycle Management: MIM automates user provisioning, modification, and de-provisioning processes, ensuring that user accounts and access rights are managed throughout their lifecycle.
- Identity Synchronization: Synchronize user identities and attributes across heterogeneous systems, including on-premises and cloud-based directories, ensuring consistency and accuracy.
- Single Sign-On (SSO): Implement SSO to allow users to access multiple applications and services with a single set of credentials, improving user productivity and security.
- Multi-Factor Authentication (MFA): Enhance security by requiring users to provide multiple authentication factors, such as passwords and one-time codes, during login.
- Access Control and Role-Based Access Control (RBAC): Define and enforce access policies based on user roles, ensuring users have the appropriate permissions for their responsibilities.
- Password Management: Implement password policies, including password complexity requirements, password reset processes, and self-service password reset options.
- Identity Federation: Enable identity federation to allow users to use their credentials from trusted identity providers to access applications and resources.
- Audit and Compliance Management: Log and monitor user activities, access events, and changes to identities to meet auditing and compliance requirements.
- Behavioral Analysis and Threat Detection: Analyze user behavior and access patterns to detect suspicious activities and potential security threats.
- Self-Service Portals: Provide users with self-service portals to manage their own identities, passwords, and access preferences, reducing administrative overhead.
How Microsoft Identity Manager works and Architecture?
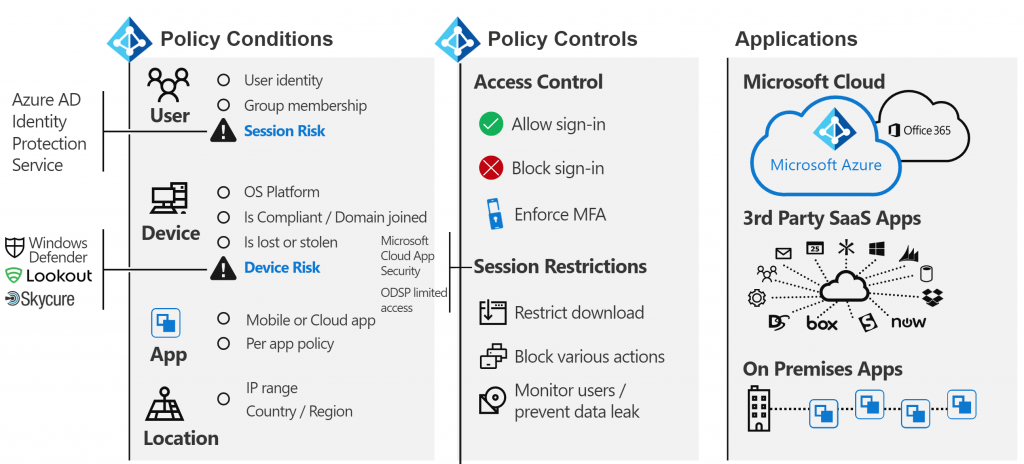
- User Registration: Users are registered within the MIM system, typically involving the creation of digital identities, personal information, and authentication credentials.
- Identity Synchronization: MIM synchronizes user identities, attributes, and passwords across various systems, ensuring that identity data is consistent and up to date.
- Authentication and Authorization: MIM authenticates users and verifies their access rights based on defined access policies, roles, and permissions.
- Access Control: Access control mechanisms within MIM enforce policies that govern user access to resources and data based on identity and role.
- User Lifecycle Management: MIM automates the management of user accounts, including provisioning, modification, and de-provisioning, based on predefined policies and workflows.
- Audit and Compliance: MIM logs and monitors user activities, access events, and changes to identities, providing visibility and compliance reporting.
- MFA and Password Management: MIM supports MFA and password management to enhance security and ease password-related tasks.
The architecture of MIM typically includes the following components:
- MIM Synchronization Service: This component handles identity synchronization across heterogeneous systems, such as directories, databases, and applications.
- MIM Service and Portal: The MIM Service is responsible for user authentication, authorization, and access management. The MIM Portal provides a user interface for administration and self-service.
- Identity Database: This database stores user identity data, attributes, and access control policies.
- Connectors: Connectors are used to integrate MIM with various systems, including directories, databases, and applications, enabling identity synchronization.
- Password Management: MIM includes password management components for enforcing password policies and enabling self-service password reset.
- Audit and Reporting: MIM logs user activities, access events, and changes to identities for auditing and reporting purposes.
- Integration with Other Microsoft Services: MIM can integrate with other Microsoft services like Azure Active Directory (Azure AD) and Active Directory Federation Services (ADFS).
Microsoft Identity Manager is designed to be a flexible and scalable solution for managing identities and access within organizations. It helps improve security, streamline user management, and ensure compliance with regulatory requirements across on-premises and hybrid IT environments.
How to Install Microsoft Identity Manager?
To install Microsoft Identity Manager (MIM), you can follow these steps:
- Download the MIM installation package. You can download the MIM installation package from the Microsoft Volume Licensing Center.
- Prepare the server for MIM installation. The server must meet the following requirements:
- Windows Server 2016 or later
- SQL Server 2016 or later
- .NET Framework 4.7.2 or later
- Install the MIM Service and Portal.
- Run the MIM installation package.
- On the Welcome page, click Next.
- Review the license terms and click Next to accept them.
- On the Custom Setup screen, select the Service and Portal feature and click Next.
- On the Sync Service database configuration screen, select the appropriate option for your SQL Server database.
- Press Install to begin the installation.
- Configure the MIM Service and Portal.
- After the installation is complete, open the MIM Service and Portal.
- On the Welcome page, click Next.
- Enter the name of the MIM Service and Portal server and click Next.
- Enter the database name and click Next.
- Enter a password for the MIM Service and Portal database and click Next.
- Click Finish to complete the configuration.
Once you have installed and configured the MIM Service and Portal, you can start using MIM to manage your identity and access.
Some additional tips for installing MIM:
- Make sure that you have the latest version of your operating system and SQL Server installed.
- Close all other applications before installing MIM.
- If you are having trouble installing MIM, contact your IT administrator for assistance.
Note: MIM is a complex product, and the installation process can be involved. If you are not comfortable installing MIM yourself, you may want to consider hiring a consultant to help you.
Basic Tutorials of Microsoft Identity Manager: Getting Started

The following steps are the basic tutorials of Microsoft Identity Manager (MIM):
Creating a User
- Log in to the MIM Service and Portal.
- Click the Users tab.
- Click the Add User button.
- Enter the user’s information, such as their name, email address, and password.
- Click the Save button.
Assigning a User to a Group
- Log in to the MIM Service and Portal.
- Click the Groups tab.
- Select the group you want to assign the user to.
- Click the Add User button.
- Select the user you want to add.
- Click the Add button.
Assigning a User to a Role
- Log in to the MIM Service and Portal.
- Click the Roles tab.
- Select the role you want to assign the user to.
- Click the Add User button.
- Select the user you want to add.
- Click the Add button.
Creating a Custom Role
- Log in to the MIM Service and Portal.
- Click the Roles tab.
- Click the Add Role button.
- Enter a name for the new role and click Next.
- Select the permissions you want to assign to the new role and click Next.
- Review the permissions you have selected and click Finish.
Resetting a Password
- Log in to the MIM Service and Portal.
- Click the Users tab.
- Select the user whose password you want to reset.
- Click the Reset Password button.
- Enter a new password for the user and click Reset.
Provisioning a User Account
- Log in to the MIM Service and Portal.
- Click the Users tab.
- Select the user account you want to provision.
- Click the Provision User button.
- Select the resources you want to provision the user account to and click Provision.
Deprovisioning a User Account
- Log in to the MIM Service and Portal.
- Click the Users tab.
- Select the user account you want to deprovision.
- Click the Deprovision User button.
- Select the resources you want to deprovision the user account from and click Deprovision.
Troubleshooting Common MIM Problems
- MIM installation problems: If you are having trouble installing MIM, you can check the MIM installation log file for more information. The MIM installation log file is located at
%ProgramData%\Microsoft Identity Manager Service\Logs\InstallLog.txt. - MIM configuration problems: If you are having trouble configuring MIM, you can check the MIM configuration log file for more information. The MIM configuration log file is located at
%ProgramData%\Microsoft Identity Manager Service\Logs\ConfigLog.txt. - MIM runtime problems: If you are having trouble using MIM, you can check the MIM runtime log file for more information. The MIM runtime log file is located at
%ProgramData%\Microsoft Identity Manager Service\Logs\RuntimeLog.txt.
If you are still having trouble after checking the log files, you can contact your IT administrator or post a question on the MIM forum or the MIM Stack Overflow page.
Additional Tips
- MIM is a complex product, and there is a lot to learn. If you are new to MIM, I recommend that you start by taking some training courses or reading some of the documentation that is available online.
- The MIM community is very helpful. If you have any questions, you can post them on the MIM forum or on the MIM Stack Overflow page.
- There are a number of good third-party resources available for MIM. These resources can be helpful for learning about MIM and for troubleshooting problems.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

