What is Mimecast?

Mimecast is a leading provider of cloud-based email security, continuity and archiving solutions. They help organizations protect their inboxes and data from a range of threats, ensuring business continuity and regulatory compliance.
Here’s what makes Mimecast stand out:
- Multi-layered security: Mimecast employs advanced algorithms and AI to filter out spam, malware, phishing attacks, and other threats before they reach users’ inboxes.
- Comprehensive archiving: They provide a secure and centralized repository for all emails, ensuring regulatory compliance and easy retrieval of historical data.
- Business continuity: Mimecast guarantees email access and functionality even during outages or disasters, minimizing disruptions to business operations.
- Cloud-based delivery: Their scalable and elastic cloud infrastructure offers easy deployment, flexible deployment options, and eliminates the need for costly on-premises hardware.
- Compliance focus: Mimecast helps organizations comply with various data privacy regulations, including GDPR, HIPAA, and SOX.
Top 10 use cases of Mimecast?
Top 10 Use Cases of Mimecast:
- Blocking email-borne threats: Stopping spam, malware, phishing, and ransomware attacks before they reach user inboxes, reducing security risks and data breaches.
- Enhancing email security: Strengthening email infrastructure with features like sandboxing, advanced threat detection, and data loss prevention.
- Meeting compliance requirements: Simplifying adherence to data privacy regulations with secure email archiving and eDiscovery capabilities.
- Protecting against targeted attacks: Mitigating sophisticated spear phishing and social engineering attempts through AI-powered detection and response.
- Ensuring business continuity: Minimizing downtime and maintaining email access even during cyberattacks, natural disasters, or technical failures.
- Improving email usability: Simplifying email management with features like search, archiving, and eDiscovery, facilitating access to historical data.
- Protecting sensitive data: Encrypting emails at rest and in transit, preventing unauthorized access and data leaks.
- Streamlining email archiving: Eliminating the need for costly on-premises storage with secure, centrally-managed cloud archives.
- Gaining insights into email usage: Analyzing email patterns and user behavior to identify potential security threats and improve email management practices.
- Simplifying email management: Reducing IT workloads by centralizing email security, archiving, and continuity functions in the cloud.
By leveraging Mimecast’s comprehensive solutions, organizations can significantly enhance their email security posture, safeguard their data, and guarantee uninterrupted business operations.
Remember: Mimecast offers a flexible suite of solutions tailored to meet the specific needs of different organizations. Whether you’re a small business or a large enterprise, they have a solution to help you protect your inboxes and data.
What are the feature of Mimecast?
Mimecast boasts a rich array of features designed to safeguard your email environment from diverse threats and ensure business continuity. Here are some key highlights:
Security Features:
- Advanced Threat Detection: AI-powered algorithms and sandboxing technology analyze emails for malware, phishing attacks, and other threats, blocking them before reaching your inbox.
- DMARC Analyzer and Enforcement: Gain control of your email domain, prevent spoofing, and protect your brand reputation with DMARC implementation and monitoring.
- Web Security Gateway: Filter out malicious websites and protect employees from online threats even when browsing through emails.
- Data Loss Prevention (DLP): Prevent sensitive data from leaking through emails with content inspection and policy enforcement.
- Advanced Spam Filtering: Eliminate unwanted emails with multi-layered spam filtering techniques, ensuring a clutter-free inbox.
Archiving and Compliance Features:
- Secure Email Archiving: Store all emails securely in the cloud, ensuring regulatory compliance and easy retrieval of historical data.
- eDiscovery and Legal Hold: Streamline legal case investigations and litigation processes with advanced search and discovery tools.
- Compliance Management: Simplify adhering to data privacy regulations like GDPR, HIPAA, and SOX with automated compliance features and reporting.
- Email Continuity: Maintain email access and functionality even during outages or disasters with email redundancy and cloud-based infrastructure.
Additional Features:
- User Awareness Training: Enhance employee security awareness with interactive training modules and simulations to reduce the risk of falling victim to phishing attacks.
- Brand Protection: Protect your brand identity from domain spoofing and unauthorized use with comprehensive brand protection solutions.
- Reporting and Analytics: Gain insights into email usage and security threats with detailed reports and dashboards.
- Cloud-Based Delivery: Enjoy easy deployment, scalability, and zero-maintenance benefits with Mimecast’s cloud-based platform.
- Integration with Existing Systems: Integrate Mimecast seamlessly with your existing email system, security tools, and productivity applications.
Mimecast’s features go beyond basic email security. They offer a comprehensive package for enhanced email management, data protection, and business continuity. The specific features available may vary depending on your chosen subscription plan.
How Mimecast works and Architecture?
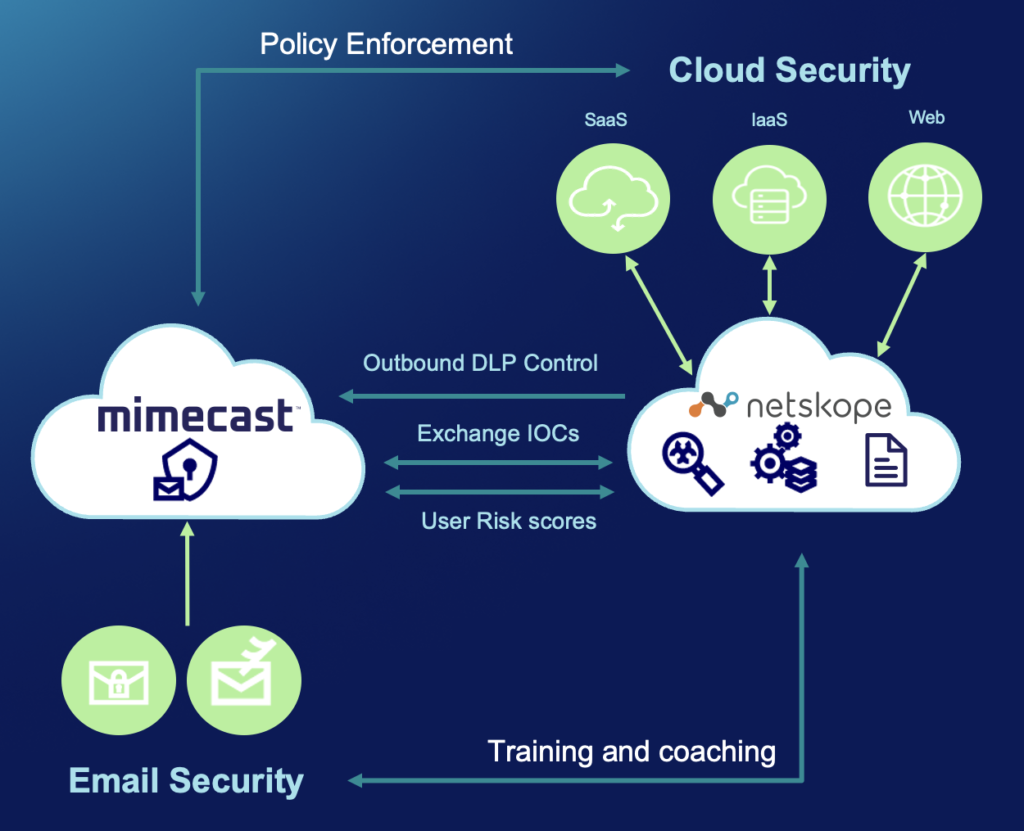
Mimecast operates through a multi-layered cloud-based architecture designed to safeguard your email environment and ensure efficient, uninterrupted communication. Here’s a breakdown of its key aspects:
Email Ingestion and Routing:
- All inbound and outbound emails flow through Mimecast’s secure cloud infrastructure.
- Advanced algorithms and AI analyze emails for potential threats, including spam, malware, phishing attempts, and data leaks.
- Suspicious emails are quarantined or further analyzed in sandboxes, while clean emails are delivered to your inbox or archived automatically.
Threat Detection and Filtering:
- Mimecast utilizes various technologies like sandboxing, URL and attachment analysis, content inspection, and threat intelligence feeds to identify and block malicious emails.
- AI-powered algorithms continuously learn and evolve to stay ahead of emerging threats and ensure the highest level of protection.
Archiving and Continuity:
- All emails are automatically archived in Mimecast’s secure cloud repository for long-term storage and legal compliance purposes.
- This cloud-based archive ensures email access even during outages or disasters, guaranteeing business continuity.
- Advanced eDiscovery features enable easy retrieval of historical emails for legal investigations or internal audits.
Management and Reporting:
- Administrators can access a comprehensive dashboard to monitor email traffic, threat detection activities, user behavior, and compliance statistics.
- Detailed reports provide insights into email usage, security trends, and potential vulnerabilities.
- Administrators can configure policies, manage user settings, and integrate Mimecast with existing IT systems.
Key Architectural Benefits:
- Scalability: The cloud-based architecture effortlessly scales to handle email volumes regardless of your organization’s size.
- Resilience: Redundancy and disaster recovery features ensure business continuity even in the event of service disruptions.
- Flexibility: Choose from various deployment options and customize features to meet your specific needs.
- Security: Multi-layered protection and continuous threat intelligence updates guarantee a robust security posture.
- Centralized Management: Manage email security, archiving, and continuity from a single, easy-to-use platform.
Mimecast’s architecture offers a secure and reliable foundation for protecting your email and ensuring seamless communication. By leveraging its robust features and intelligent systems, you can enhance your organization’s email security posture, comply with regulations, and maintain uninterrupted business operations.
How to Install Mimecast it?
Unlike traditional software, Mimecast doesn’t involve a typical installation process with downloadable files and local setup. It’s a cloud-based service accessed through your web browser, requiring configuration rather than installation. Here’s how you get started with Mimecast:
1. Sign Up and Planning:
- Visit the Mimecast website and explore their plans and features.
- Contact their sales team or discuss your requirements with a reseller.
- Choose a suitable plan based on your organization’s size, email volume, and desired features.
2. Domain Authentication and Routing:
- Mimecast will guide you through the process of authenticating your email domain(s) using DMARC and other protocols.
- This ensures emails received through Mimecast originate from your authorized domain, preventing spoofing and phishing attempts.
- You’ll configure your mail server to direct inbound and outbound email traffic through Mimecast’s secure cloud infrastructure.
3. User Configuration and Training:
- Mimecast integrates seamlessly with most email systems. The process may involve minor configuration changes depending on your existing setup.
- Mimecast offers user guides and training materials to help employees familiarize themselves with the new email environment.
- Consider providing employee training on Mimecast’s features, especially security functionalities like anti-phishing tools to increase awareness and engagement.
4. Ongoing Management and Support:
- Mimecast provides a dedicated portal for administrators to manage user accounts, configure policies, monitor email traffic, and access reports.
- Their support team is available for assistance throughout the onboarding process and beyond.
- Mimecast regularly updates its features and technologies to ensure you always have the latest protection against evolving threats.
Notes:
- The specific configuration steps may vary depending on your chosen plan and existing email infrastructure.
- Mimecast offers flexible deployment options and integration with various productivity and security tools.
- Consider scheduling downtime for email routing changes during the initial setup to minimize disruption for users.
Remember: Deploying Mimecast is more about configuration and integration than installation. Their team will guide you through the process and provide ongoing support to ensure a smooth transition and optimal security posture for your email environment.
Basic Tutorials of Mimecast: Getting Started

Mimecast offers a comprehensive suite of email security and productivity tools, but it can be daunting to know where to start. To help you navigate the basics, I’ve outlined some step-by-step tutorials for essential Mimecast features:
1. Accessing Your Mimecast Admin Portal:
- Go to Mimecast’s website and log in using your administrator credentials.
- You’ll arrive at the Mimecast Admin Portal, your hub for managing all Mimecast settings and features.
2. Securing Your Inbox with Mimecast Policies:
- Select “Policies” from the left-hand menu.
- Click on “Anti-Spam” to configure spam filtering rules. You can adjust sensitivity levels, whitelisted and blacklisted sender domains, and reporting settings.
- Navigate to “Anti-Virus” to manage virus and malware scanning configurations. Define scanning engines, file types to scan, and quarantine actions.
- Explore other policies like “URL Protection” to block malicious links and “Brand Protection” to prevent domain spoofing.
3. Managing Users and Groups:
- Choose “Users & Groups” from the left-hand menu.
- Click on “Users” to manage individual accounts. You can create new users, edit existing ones, and assign licenses and permissions.
- Navigate to “Groups” to organize users into categories. This simplifies policy assignment and bulk user management.
4. Exploring Mimecast Threat Center:
- Select “Threat Center” from the left-hand menu.
- The “Dashboard” provides an overview of recent email threats, quarantined messages, and overall security posture.
- Click on “Quarantine” to review suspicious emails and decide to release, delete, or report them.
- Explore other sections like “Phishing Reports” and “Threat Intelligence” to gain deeper insights into potential security risks.
5. Utilizing Mimecast Features for Productivity:
- In the “Settings” section, explore features like “Archiving & Vaulting” for long-term email storage and legal compliance.
- Check out “Continuity & Archiving” to ensure continuous email access even during outages or disruptions.
- Discover “Information Archiving” for managing non-email data like file shares and instant messages.
This journey into Mimecast basics will equip you with essential knowledge to secure your email environment and enhance your productivity. Keep exploring, experimenting, and learning to become a Mimecast master!
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

