What is nCipher?

nCipher Security, a division of Thales Group, specializes in providing hardware security modules (HSMs) and cryptographic key management solutions to protect sensitive data, secure applications, and manage cryptographic keys. nCipher’s products and services are designed to help organizations enhance their data security, ensure compliance, and protect critical assets.
These use cases reflect nCipher’s role in helping organizations protect sensitive data, secure applications, and manage cryptographic assets effectively. nCipher’s products are widely used across various industries, including finance, healthcare, government, and critical infrastructure, to enhance security and maintain compliance with industry regulations.
Top 10 use cases of nCipher:
Here are the top 10 use cases for nCipher’s solutions:
- Cryptographic Key Management: nCipher HSMs are widely used for secure generation, storage, and management of cryptographic keys, ensuring the integrity and confidentiality of sensitive data.
- Data Encryption: nCipher HSMs provide hardware-based encryption for data at rest, in transit, and in use, safeguarding critical information from unauthorized access.
- Digital Signatures: nCipher solutions enable organizations to create and verify digital signatures, ensuring the authenticity and integrity of electronic documents and transactions.
- Payment Card Security: nCipher’s HSMs are used in the financial industry to secure payment transactions, including point-of-sale (POS) systems, card issuance, and payment processing.
- Secure Certificate Authorities (CAs): nCipher HSMs are used to secure and manage certificate issuance, protecting the trustworthiness of digital certificates in public key infrastructure (PKI) environments.
- Tokenization: nCipher solutions support tokenization to replace sensitive data with tokens, reducing the risk of data breaches while maintaining functionality.
- Secure Cloud Encryption: nCipher helps organizations secure data and workloads in cloud environments, ensuring data privacy and control.
- IoT Device Security: nCipher solutions address the security challenges associated with the Internet of Things (IoT), protecting data and device identities in IoT deployments.
- Secure Code Signing: nCipher HSMs are used to sign and verify the authenticity and integrity of software, ensuring that code is not tampered with during distribution.
- Compliance and Regulatory Compliance: nCipher solutions assist organizations in achieving compliance with industry regulations and standards such as GDPR, HIPAA, PCI DSS, and more by implementing necessary security controls.
What are the feature of nCipher?
nCipher Security provides a range of features and capabilities through its hardware security modules (HSMs) and cryptographic key management solutions to enhance data security and protect cryptographic keys. The specific features may vary depending on the product or solution within the nCipher portfolio, but here are some common features and functionalities associated with nCipher’s offerings:
- Hardware-Based Security: nCipher HSMs leverage dedicated hardware security to provide robust protection for cryptographic keys and sensitive data.
- Key Generation and Management: nCipher solutions offer secure key generation, storage, and lifecycle management, ensuring the confidentiality and integrity of cryptographic keys.
- Data Encryption: nCipher HSMs support encryption for data at rest, in transit, and in use, ensuring that sensitive information remains confidential.
- Digital Signatures: nCipher solutions enable organizations to create and verify digital signatures to authenticate documents and transactions.
- Tokenization: nCipher supports tokenization, which replaces sensitive data with tokens to reduce the risk of data breaches while preserving functionality.
- Payment Card Security: nCipher’s HSMs are designed to secure payment transactions, including point-of-sale (POS) systems, card issuance, and payment processing.
- Secure Certificate Authorities (CAs): nCipher HSMs are used to secure and manage the issuance of digital certificates, ensuring trustworthiness in PKI environments.
- Secure Code Signing: nCipher solutions protect the integrity of software by signing and verifying code to prevent tampering during distribution.
- Cloud Security: nCipher helps organizations secure data and workloads in cloud environments, supporting multi-cloud and hybrid cloud deployments.
- IoT Device Security: nCipher solutions address the security challenges associated with IoT by securing data and device identities.
How nCipher works and Architecture?
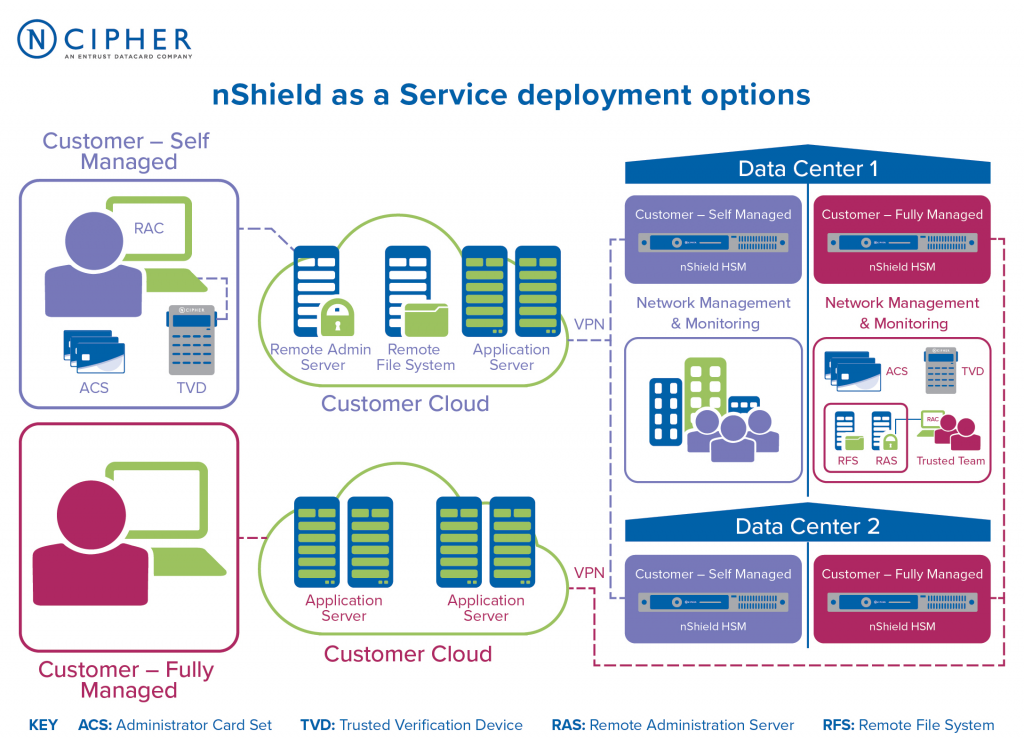
nCipher’s architecture and how it works can vary depending on the specific product or solution being used, but here’s a general overview of how nCipher solutions typically operate:
- HSM Deployment: nCipher HSMs are hardware devices that are integrated into an organization’s IT infrastructure. They can be deployed on-premises or in cloud environments, depending on the deployment model.
- Key Generation: nCipher HSMs securely generate cryptographic keys using a random number generator and store them within the HSM’s secure hardware.
- Key Management: nCipher solutions include key management features that help organizations securely manage keys throughout their lifecycle, including key generation, rotation, and destruction.
- Encryption and Decryption: nCipher HSMs perform hardware-based encryption and decryption operations to protect data and ensure its confidentiality.
- Digital Signatures: nCipher HSMs support the creation and verification of digital signatures, ensuring the authenticity and integrity of electronic documents and transactions.
- Tokenization: nCipher solutions tokenize sensitive data, replacing it with tokens to protect it from unauthorized access.
- Access Control: nCipher HSMs enforce access controls to ensure that only authorized users and applications can access cryptographic keys and perform operations.
- Audit and Compliance: nCipher solutions often include auditing and reporting capabilities to help organizations demonstrate compliance with security policies and regulatory requirements.
- Integration: nCipher integrates with various systems and applications within an organization’s IT environment to provide seamless security controls and cryptographic operations.
Overall, nCipher’s architecture is designed to provide hardware-based security and robust cryptographic operations for protecting data, digital identities, and cryptographic keys. Specific implementations may vary based on an organization’s needs and the nCipher products in use.
How to Install nCipher?
To install nCipher software, you will need to download the installer package from the Thales eSecurity website. The specific steps involved in the installation process will vary depending on your operating system, but the general steps are as follows:
Windows
- Download the nCipher installer package from the Thales eSecurity website.
- Double-click on the installer package to start the installation process.
- Implement the on-screen instructions to complete the installation.
Linux
- Download the nCipher installer package from the Thales eSecurity website.
- Place the installation media in the optical disc drive, and mount the drive.
- Open a terminal window, and change to the root directory.
- Extract the required .tar files to install all the software bundles by running commands of the form:
tar xf disc-name/linux/ver/<file>.tar.gzmacOS
- Download the nCipher installer package from the Thales eSecurity website.
- Double-click on the installer package to start the installation process.
- Implement the on-screen instructions to complete the installation.
Once the installation is complete, you will need to configure nCipher before you can start using it. For more information on how to configure nCipher, please refer to the nCipher documentation.
Some additional things to keep in mind when installing nCipher software:
- Make sure that your system meets the minimum requirements for nCipher. You can find the minimum requirements on the nCipher product page on the Thales eSecurity website.
- If you are installing nCipher on a Windows system, make sure that you are running as an administrator.
- If you are installing nCipher on a Linux system, make sure that you have root privileges.
- If you are installing nCipher on a macOS system, make sure that you have administrator privileges.
Basic Tutorials of nCipher: Getting Started

The following are the stepwise basic tutorials of nCipher:
How to create a new nCipher partition
- Open the nShield Connect Management Console.
- In the left-hand pane, expand the Partitions node.
- Right-click on the Partitions node and select New Partition.
- In the New Partition dialog box, enter a name for the new partition and select the HSM where you want to create the partition.
- Click OK to create the new partition.
How to add a user to an nCipher partition
- Open the nShield Connect Management Console.
- In the left-hand pane, expand the Partitions node and select the partition where you want to add the user.
- Right-click on the partition and select Manage Users.
- In the Manage Users dialog box, click the Add button.
- In the Add User dialog box, enter the username and password for the new user.
- Click OK to add the new user to the partition.
How to generate a new key pair
- Open the nShield Connect Management Console.
- In the left-hand pane, expand the Partitions node and select the partition where you want to generate the key pair.
- Right-click on the partition and select Generate Key Pair.
- In the Generate Key Pair dialog box, select the type of key pair you want to generate and enter a name for the key pair.
- Click OK to generate the new key pair.
How to encrypt a file
- Open the nShield Connect Management Console.
- In the left-hand pane, expand the Partitions node and select the partition where the key pair you want to use to encrypt the file is stored.
- Right-click on the partition and select Encrypt File.
- In the Encrypt File dialog box, select the file you want to encrypt and select the key pair you want to use to encrypt the file.
- Click OK to encrypt the file.
How to decrypt a file
- Open the nShield Connect Management Console.
- In the left-hand pane, expand the Partitions node and select the partition where the key pair you want to use to decrypt the file is stored.
- Right-click on the partition and select Decrypt File.
- In the Decrypt File dialog box, select the file you want to decrypt and select the key pair you want to use to decrypt the file.
- Click OK to decrypt the file.
Additional tips:
- When creating a new nCipher partition, be sure to choose a strong password for the partition.
- When adding a user to an nCipher partition, be sure to assign the user the appropriate permissions.
- When generating a new key pair, be sure to choose a strong algorithm and key size.
- When encrypting a file, be sure to choose a strong key pair.
- When decrypting a file, be sure to use the correct key pair.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

