What is Nikto?

Nikto is an open-source web server scanner and vulnerability assessment tool. It is designed to help identify potential security issues in web servers and web applications by scanning them for known vulnerabilities and misconfigurations. Nikto is often used by web developers, security professionals, and penetration testers to perform security assessments and audits.
Nikto is a valuable tool for identifying potential security issues, but it should be used responsibly and with proper authorization. Unauthorized scanning of web servers or applications can be disruptive and may even violate legal and ethical guidelines. Always obtain the necessary permissions before using Nikto or any other security assessment tool on a target system.
Top 10 use cases of Nikto:
Here are the top 10 use cases of Nikto:
- Web Server Vulnerability Scanning: Nikto scans web servers for a wide range of vulnerabilities and security issues, including outdated software, missing patches, and misconfigurations.
- Web Application Security Testing: It can be used to assess the security of web applications by looking for common web application vulnerabilities such as SQL injection, cross-site scripting (XSS), and directory traversal.
- Banner Grabbing: Nikto can retrieve banners and version information from web servers and web applications. This information can be useful for understanding the technology stack in use and identifying known vulnerabilities associated with specific versions.
- Identification of Outdated Software: Nikto checks web server software, plugins, and extensions for known vulnerabilities and outdated versions. This is crucial for ensuring that systems are running up-to-date software.
- Detection of Default Files and Directories: The tool identifies common default files and directories that may be exposed unintentionally on a web server, such as backup files, login pages, and configuration files.
- SSL/TLS Vulnerability Scanning: Nikto checks for SSL/TLS vulnerabilities and misconfigurations, ensuring that secure communication is properly implemented.
- Identification of Insecure Permissions: It scans for files and directories with insecure permissions that could be exploited by an attacker to gain unauthorized access.
- CGI Vulnerability Assessment: Nikto is particularly useful for identifying vulnerabilities in CGI scripts and programs commonly used on web servers. It checks for known CGI vulnerabilities and misconfigurations.
- Server Misconfigurations: The tool looks for common server misconfigurations that might expose sensitive information or create security weaknesses.
- Security Audits and Compliance Checks: Nikto can be used to conduct security audits and compliance checks against web servers and applications to ensure they meet security standards and best practices.
What are the feature of Nikto?
Nikto is a web server scanner and vulnerability assessment tool known for its simplicity and effectiveness in identifying security issues in web servers and web applications. Here are some of the key features of Nikto:
- Vulnerability Scanning: Nikto scans web servers and web applications for known vulnerabilities, misconfigurations, and security issues.
- Comprehensive Database: It maintains a comprehensive database of known vulnerabilities and security checks, which it uses to compare against the target system’s configuration.
- Cross-Platform: Nikto is cross-platform and can be run on various operating systems, including Linux, Windows, and macOS.
- HTTP Method Support: It supports various HTTP methods, including GET, POST, and HEAD, allowing users to test different aspects of web servers and applications.
- SSL/TLS Support: Nikto can be used to test the security of SSL/TLS configurations and certificates on web servers.
- Configurable: Users can customize Nikto’s behavior and output through various command-line options, including the ability to specify which tests to perform or skip.
- Integration: Nikto can be integrated into scripts and automation workflows, making it useful for continuous security monitoring.
- Reporting: It generates detailed reports in various formats, including plain text, XML, and HTML, making it easy to share results and findings.
- Authentication Support: Nikto can handle web server authentication, allowing users to test authenticated areas of web applications.
- Multiple Scan Profiles: It offers different scan profiles with different levels of aggressiveness, allowing users to choose the appropriate level of testing.
How Nikto works and Architecture?
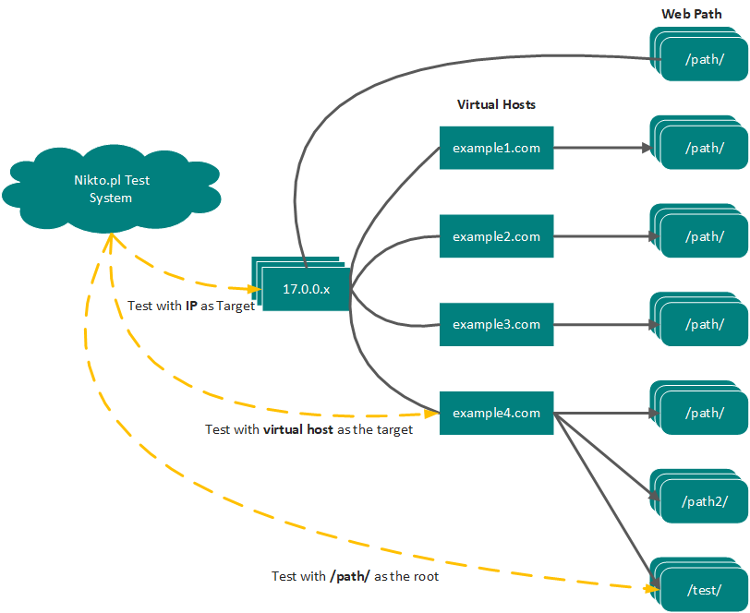
Now, let’s explore how Nikto works and its architecture:
- Target Specification: The user specifies the target web server or web application to be tested using Nikto. This can be done through the command-line interface along with various options and flags.
- Database Checks: Nikto uses its extensive database of known vulnerabilities, security checks, and misconfigurations to perform a series of HTTP requests and checks against the target.
- HTTP Requests: Nikto sends a variety of HTTP requests to the target, including GET, POST, and HEAD requests, to interact with the web server or application.
- Response Analysis: Nikto analyzes the responses received from the target to identify potential vulnerabilities, security issues, or misconfigurations. It compares the responses to its database of known issues.
- Reporting: Nikto generates a detailed report summarizing its findings, including the vulnerabilities and issues discovered during the scan. Users can specify the format and location of the report.
Nikto’s architecture is relatively straightforward, as it is designed to be a simple yet effective vulnerability scanner. It primarily consists of the following components:
- User Interface: Nikto is primarily used through its command-line interface (CLI). Users interact with the tool by specifying command-line options, flags, and the target to be scanned.
- Database: Nikto maintains a database of known vulnerabilities, security checks, and misconfigurations. This database is used to compare against the target system during the scan.
- HTTP Engine: Nikto includes an HTTP engine responsible for sending HTTP requests to the target web server or application and receiving and analyzing the responses.
- Reporting Module: After the scan is completed, Nikto generates detailed reports in various formats, such as plain text, XML, and HTML, based on the findings.
Overall, Nikto’s architecture is designed for simplicity and ease of use, making it a valuable tool for security professionals and web administrators to quickly assess the security of web servers and applications.
How to Install Nikto?
To install Nikto on Kali Linux, follow these steps:
- Open a terminal window.
- Update the software repositories:
sudo apt update- Install Nikto:
sudo apt install nikto- Verify that Nikto is installed by running the following command:
nikto --versionThis should output the version number of Nikto that is installed on your system.
Some additional tips for installing Nikto:
- If you are using a different Linux distribution, you may need to install Nikto from a different package repository.
- You can also install Nikto from source code. To do this, download the Nikto source code from the Nikto website and then follow the instructions in the README file to compile and install Nikto.
Once Nikto is installed, you can start using it to scan websites for vulnerabilities. To learn more about how to use Nikto, type nikto --help in a terminal window.
Basic Tutorials of Nikto: Getting Started

Following is the step-by-step basic tutorial for Nikto:
- Install Nikto.
If you are using Kali Linux, Nikto is already pre-installed. Otherwise, you can install Nikto on your Linux distribution using the package manager. For example, on Debian or Ubuntu, you would use the following command:
sudo apt install nikto2. Navigate to the directory where Nikto is installed.
You can use the cd command to navigate to the directory where Nikto is installed. For example, on Kali Linux, Nikto is installed in the /usr/share/nikto directory.
3. Run a Nikto scan.
To run a Nikto scan, use the following command:
nikto <target website>For example, to scan the website example.com, you would use the following command:
nikto example.com4. View the scan results.
Once the scan is complete, Nikto will output a report that lists the vulnerabilities that were found. The report will also include information on how to fix the vulnerabilities.
5. Save the scan results.
To save the scan results to a file, use the -o option. For example, to save the scan results to a file named scan.txt, you would use the following command:
nikto -o scan.txt example.comSome additional tips for using Nikto:
- Scan for specific vulnerabilities. You can use the
-pluginsoption to scan for specific vulnerabilities. For example, to scan for vulnerabilities in the WordPress content management system, you would use the following command:nikto -plugins wordpress example.com - Scan multiple websites. You can scan multiple websites by specifying a range of IP addresses or website addresses. For example, to scan the websites from
example.comtoexample.org, you would use the following command:nikto example.com-org - Use Nikto responsibly. Nikto is a powerful tool, but it is important to use it responsibly. Do not use Nikto to scan websites that you are not authorized to scan. Be careful when sharing Nikto scan results, as they may contain sensitive information. Do not use Nikto to scan websites that contain personal or confidential information.
Nikto is a valuable tool for security researchers and web developers. By following these basic steps, you can start using Nikto to scan websites for vulnerabilities and to improve the security of your websites.
- Building a DevOps Culture: Tips and Strategies - April 4, 2024
- Why Understanding DevOps Could Be Your Key To Success In The Music Industry - April 4, 2024
- Top Picks: The Best Laptops for Graphic Designers in 2024 - March 31, 2024

