What is Nmap?
Nmap, also known as Network Mapper, is a powerful open-source tool used for network exploration and security auditing. It is designed to scan and map networks, discover hosts, and identify open ports and services running on those hosts. Nmap provides a wealth of information about networked devices, which can be invaluable for network administrators, security professionals, and penetration testers.
However, it’s essential to use it responsibly and with proper authorization, as aggressive or unauthorized scanning can be disruptive or even illegal in certain contexts.
Top 10 use cases of Nmap:
Here are the top 10 use cases for Nmap:
- Network Discovery: Nmap can be used to discover devices and hosts on a network. By scanning a range of IP addresses, it identifies which devices are online and reachable.
- Port Scanning: It’s widely used for port scanning to determine which ports on a target system are open and listening for incoming connections. This is crucial for assessing the attack surface of a network.
- Service Identification: Nmap not only identifies open ports but also attempts to determine which services are running on those ports. This helps in understanding the software and versions running on target systems.
- Vulnerability Assessment: Security professionals can use Nmap to identify known vulnerabilities in the services and software running on scanned hosts. Tools like NSE (Nmap Scripting Engine) can automate vulnerability checks.
- Network Mapping: Nmap can create visual maps of network topologies, showing the relationships between devices and their interconnections. This is useful for network administrators to understand their network structure.
- Firewall Testing: By scanning a network from an external perspective, Nmap can help assess the effectiveness of firewalls and other security measures. It can identify which ports and services are accessible from the outside.
- OS Fingerprinting: Nmap can attempt to determine the operating system of a target host based on how it responds to certain probes. This information is valuable for understanding the network environment.
- Scriptable Automation: Nmap comes with a scripting engine (NSE) that allows users to write custom scripts to automate various tasks, such as advanced scanning, data collection, or even exploitation.
- Penetration Testing: Ethical hackers and penetration testers use Nmap to assess the security of a network and discover potential entry points for attacks. Nmap can identify weak points that need attention.
- Network Monitoring: In addition to active scanning, Nmap can be used for passive network monitoring. By listening to network traffic, it can analyze and report on the devices and services communicating on the network.
What are the feature of Nmap?
Nmap, or Network Mapper, is a highly versatile and feature-rich open-source network scanning tool that can be used for a variety of network exploration and security auditing purposes. Here are some of the key features of Nmap:
- Port Scanning: Nmap excels at port scanning, allowing users to discover open ports on target systems. It can identify both TCP and UDP ports, providing a comprehensive view of the services running on a host.
- Service Detection: Nmap goes beyond port scanning by attempting to identify the services and applications associated with open ports. It can often determine the software version and additional information about these services.
- OS Fingerprinting: Nmap can perform operating system fingerprinting by analyzing responses from the target system to specific probes. This helps in determining the type and version of the operating system running on a host.
- Scripting Engine (NSE): Nmap includes a powerful scripting engine called the Nmap Scripting Engine (NSE). It allows users to write custom scripts to automate tasks, such as vulnerability scanning, network enumeration, and more.
- Vulnerability Scanning: With the help of NSE scripts and other plugins, Nmap can be used for vulnerability scanning to identify known security issues on target systems.
- Network Mapping: Nmap can create visual network maps, illustrating the relationships between devices and how they are interconnected. This is useful for network administrators and security professionals.
- Ping Scanning: Nmap can use various ping techniques to determine the online status of hosts, even if they don’t respond to traditional ICMP ping requests.
- Proxy Support: Nmap can be used through proxy servers, allowing users to scan targets indirectly through a proxy.
- Output Formats: Nmap supports multiple output formats, including plain text, XML, and various interactive interfaces. This flexibility makes it suitable for different reporting and analysis needs.
- Performance Optimization: Nmap includes various performance optimization options to control the speed and aggressiveness of scans, allowing users to balance scan speed with network impact.
How Nmap works and Architecture?
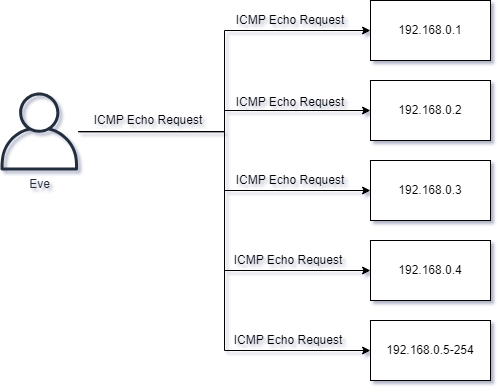
As for how Nmap works and its architecture, here’s a simplified overview:
- Host Discovery: Nmap starts by identifying which hosts are alive and responsive on the network. It does this through techniques like ICMP ping, TCP ping, or ARP scanning, depending on the specified options.
- Port Scanning: Once hosts are discovered, Nmap conducts port scanning to determine which ports are open and listening on the target systems. This involves sending TCP and UDP packets to various port numbers.
- Service Detection: For open ports, Nmap sends probes to determine the services running on those ports. It may send specific payloads to elicit responses that reveal information about the services and their versions.
- OS Fingerprinting: If enabled, Nmap can perform OS fingerprinting by analyzing responses from the target systems to certain probes. This helps in identifying the operating system.
- Scripting: The Nmap Scripting Engine (NSE) can execute scripts that perform various tasks, including vulnerability scanning, banner grabbing, and custom network enumeration, among others.
- Output and Reporting: Nmap generates reports in the specified output format, providing information about the discovered hosts, open ports, services, and more.
Nmap’s architecture is modular and extensible, allowing users to customize its behavior through command-line options, scripts, and plugins. It is a command-line tool by default, but there are also graphical user interfaces and third-party frontends available for those who prefer a GUI-based approach.
How to Install Nmap?
To install Nmap, follow these steps:
On Linux:
- Update the package list:
sudo apt update- Install Nmap:
sudo apt install nmapOn macOS:
- Install Nmap using Homebrew:
brew install nmap- Install Nmap using MacPorts:
sudo port install nmapOn Windows:
- Download the Nmap self-installer from the Nmap website:
https://nmap.org/download.html- Run the self-installer and follow the instructions.
Verifying the installation:
Once you have installed Nmap, you can verify the installation by running the following command:
nmap --versionThis should print the version number of Nmap that is installed on your system.
Example:
nmap --version
Nmap 7.92 ( https://nmap.org )Once Nmap is installed, you can start using it to scan networks and identify hosts and services.
Basic Tutorials of Nmap: Getting Started
Following is the step-by-step Basic Tutorials of Nmap
It is a powerful tool that can be used for a variety of purposes, such as network security audits, network discovery, and vulnerability scanning.
To get started with Nmap, follow these steps:
- Open a terminal window.
- Proceed to the directory where the Nmap installation is situated.
- Run the following command to scan a single host:
nmap <hostname or IP address>
For example, to scan the host 192.168.1.100, you would run the following command:
nmap 192.168.1.100
This will scan the host for open ports and services.
- To scan multiple hosts, you can specify a range of IP addresses. For example, to scan the hosts from
192.168.1.100to192.168.1.110, you would run the following command:
nmap 192.168.1.100-110
- To scan specific ports, you can apply the
-poption. For example, to scan the ports 80 and 443, you would run the following command:
nmap -p 80,443 192.168.1.100
- To scan for specific services, you can use the
-sVoption. For example, to scan for the HTTP and SSH services, you would run the following command:
nmap -sV -p 80,22 192.168.1.100
- Nmap also offers a variety of other options that can be used to customize the scan. For example, to scan in stealth mode, you can use the
-sSoption. To scan in aggressive mode, you can use the-Aoption.
To learn more about Nmap and its options, you can type the following command:
nmap --help
Example:
nmap --help
Usage: nmap [Scan Type(s)] [Options] {target specification}
[...]
Examples:
nmap -sP 192.168.1.0/24
nmap -sS -A scanme.nmap.org
nmap -Pn -p 80,22 10.0.0.0-255
nmap -T4 -A 192.168.1.1-10
Once you have run a scan, Nmap will output the results to the terminal window. The output will include information about the hosts and services that were discovered.
Example of Nmap scan output:
Starting Nmap 7.92 ( https://nmap.org ) at 2023-09-19 12:17:35 PST
Nmap scan report for 192.168.1.100
Host is up (0.00028s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
80/tcp open http
443/tcp open https
This output shows that the host 192.168.1.100 is up and running, and that the HTTP and HTTPS services are open.
Nmap is a powerful tool that can be used for a variety of purposes. By following these basic steps, you can start using Nmap to scan networks and identify hosts and services.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

