What is OpenVAS?

OpenVAS, short for Open Vulnerability Assessment System, is an open-source vulnerability scanning and vulnerability management tool designed to help organizations identify security vulnerabilities in their networks, systems, and applications. OpenVAS is similar in purpose to commercial vulnerability assessment tools like Nessus.
Top 10 use cases of OpenVAS?
Here are the top 10 use cases of OpenVAS:
- Vulnerability Scanning: OpenVAS scans networks, hosts, and applications to identify known vulnerabilities, misconfigurations, and potential security weaknesses.
- Plugin-Based Architecture: OpenVAS utilizes a plugin-based system that allows it to support a wide range of vulnerability checks and security tests. New plugins can be added and updated to keep up with the latest vulnerabilities.
- Compliance Auditing: It can be used to assess compliance with various security standards and regulatory requirements, such as PCI DSS, HIPAA, and CIS benchmarks.
- Network Discovery: OpenVAS helps organizations identify and catalog all devices and systems connected to their network, helping maintain an up-to-date inventory.
- Web Application Scanning: OpenVAS can scan web applications for common vulnerabilities, including SQL injection, cross-site scripting (XSS), and insecure authentication.
- Customizable Scans: Users can configure OpenVAS scans by specifying target hosts, scan policies, and other parameters to tailor scans to their specific needs.
- Credentials-Based Scanning: OpenVAS supports scanning with credentials, allowing for more in-depth assessments of hosts, including software inventory and configuration checks.
- Prioritization of Vulnerabilities: OpenVAS assigns severity levels to identified vulnerabilities, helping organizations prioritize remediation efforts based on risk.
- Integration: OpenVAS can integrate with other security tools and platforms, such as SIEM systems, to provide a comprehensive security ecosystem.
- Reporting: It generates detailed reports that include vulnerability descriptions, severity ratings, and recommendations for mitigation. These reports can be customized for different stakeholders.
OpenVAS is particularly useful for organizations that require a cost-effective, open-source solution for vulnerability assessment and management. It can help organizations proactively identify and address vulnerabilities, strengthen their security posture, and comply with security standards and regulations.
What are the feature of OpenVAS?
The following are the key features of OpenVAS:
- Vulnerability Scanning: OpenVAS performs scans to identify vulnerabilities, misconfigurations, and security weaknesses in hosts, systems, and applications.
- Plugin-Based Architecture: OpenVAS uses a plugin-based system that allows it to support a wide range of vulnerability checks and security tests. New plugins can be added and updated to keep up with the latest vulnerabilities.
- Compliance Auditing: OpenVAS can assess compliance with various security standards and regulatory requirements, such as PCI DSS, HIPAA, and CIS benchmarks.
- Network Discovery: It helps organizations identify all devices and systems connected to their network, assisting in maintaining an accurate inventory.
- Web Application Scanning: OpenVAS can scan web applications for common vulnerabilities, including SQL injection, cross-site scripting (XSS), and insecure authentication.
- Customizable Scans: Users can configure OpenVAS scans by specifying target hosts, scan policies, and other parameters to tailor scans to their specific needs.
- Credentials-Based Scanning: OpenVAS supports scanning with credentials, allowing for more in-depth assessments of hosts, including software inventory and configuration checks.
- Prioritization of Vulnerabilities: OpenVAS assigns severity levels to identified vulnerabilities, helping organizations prioritize remediation efforts based on risk.
- Integration: OpenVAS can integrate with other security tools and platforms, such as SIEM systems, to provide a comprehensive security ecosystem.
- Reporting: It generates detailed reports that include vulnerability descriptions, severity ratings, and recommendations for mitigation. Reports can be customized for different stakeholders.
How OpenVAS works and Architecture?
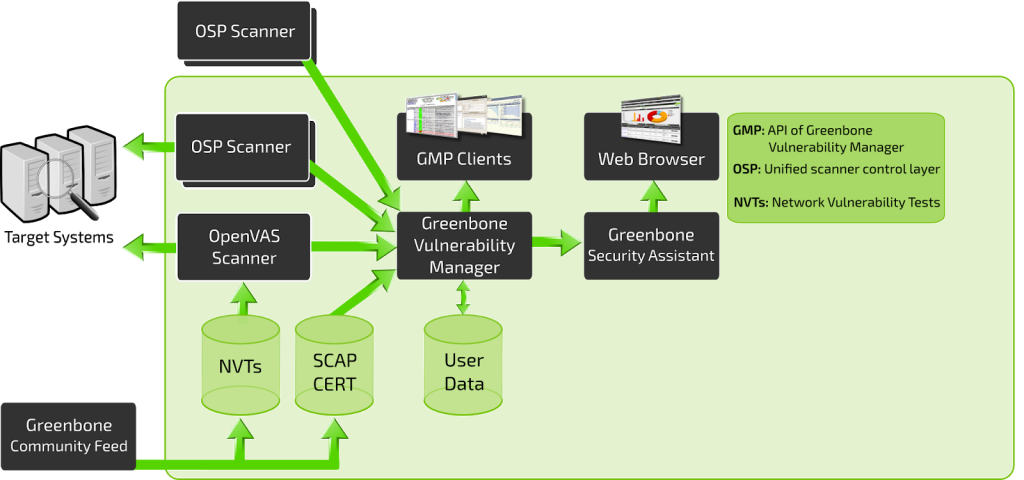
OpenVAS works by conducting scans on target systems and analyzing the results to identify vulnerabilities and potential security issues. Here’s a simplified overview of how OpenVAS works:
- Scan Configuration: Users configure OpenVAS scans by defining target hosts, specifying scan policies (e.g., which types of vulnerabilities to check), and setting other scan parameters.
- Scanning: OpenVAS performs scans on the target systems based on the configured policies. It sends various probes and checks to detect vulnerabilities, misconfigurations, and potential security risks.
- Vulnerability Detection: During the scan, OpenVAS identifies vulnerabilities by comparing its findings with a constantly updated database of vulnerability checks (plugins).
- Data Analysis: OpenVAS analyzes the scan results and assigns severity levels to each identified vulnerability, helping organizations prioritize remediation efforts.
- Reporting: OpenVAS generates detailed reports that include a list of vulnerabilities, their descriptions, severity ratings, and recommendations for mitigation.
OpenVAS Architecture:
OpenVAS typically consists of several components that work together to provide vulnerability scanning and management capabilities:
- OpenVAS Scanner: This component conducts the actual scanning of target hosts and collects scan results. It communicates with the OpenVAS Manager to fetch scan configurations and report results.
- OpenVAS Manager: The manager coordinates the scanning process, manages scan policies, and stores scan results. It acts as the central control point for managing and scheduling scans.
- OpenVAS CLI and GUI: These are the user interfaces for interacting with OpenVAS. The CLI provides a command-line interface, while the GUI offers a graphical user interface for configuring scans, viewing results, and generating reports.
- OpenVAS Greenbone Security Assistant (GSA): GSA is a web-based interface that allows users to manage and configure OpenVAS scans through a web browser.
- OpenVAS Knowledge Base (NVTs): The knowledge base contains a vast collection of Network Vulnerability Tests (NVTs), which are plugins used to detect vulnerabilities.
- OpenVAS OpenVAS Transfer Protocol (OTP): OTP is used for communication between various components of OpenVAS.
OpenVAS can be deployed on a single server or in a distributed architecture for scalability. Communication between these components is secured to protect sensitive scan data.
OpenVAS is a powerful tool for vulnerability assessment and management and is particularly valuable for organizations looking for an open-source solution to identify and address security vulnerabilities in their infrastructure.
How to Install OpenVAS?
There are two ways to install OpenVAS:
- Using a package manager: OpenVAS is available in the package repositories of many popular Linux distributions. To install OpenVAS using a package manager, simply search for the “openvas” package and install it.
- From source: You can also install OpenVAS from source. To do this, you will need to download the OpenVAS source code from the Greenbone Security website. Once you have downloaded the source code, you can compile and install OpenVAS by following the instructions in the OpenVAS documentation.
Once OpenVAS is installed, you will need to start the OpenVAS service. To do this, on Linux, run the following command:
sudo service openvas-manager startOn Windows, open the Windows Services console and start the OpenVAS Manager service.
Once the OpenVAS service is started, you can access the OpenVAS web interface at https://localhost:9392.
If you are installing OpenVAS on a remote server, you will need to replace localhost with the IP address or hostname of the server.
To complete the OpenVAS installation, you will need to create an OpenVAS account and register your OpenVAS instance.
To create an OpenVAS account, click on the “Create Account” link on the OpenVAS login page.
To register your OpenVAS instance, click on the “Register” link on the OpenVAS login page.
Once you have registered your OpenVAS instance, you will be able to start using OpenVAS to scan your networks for vulnerabilities.
Some additional tips for installing OpenVAS:
- Make sure that you have enough disk space to install OpenVAS. OpenVAS requires at least 10 GB of free disk space.
- Make sure that you have the necessary permissions to install OpenVAS. OpenVAS needs to be installed as a root user on Linux and as an administrator on Windows.
- If you are installing OpenVAS on a remote server, you will need to open port 9392 on the server’s firewall.
- If you are having trouble installing OpenVAS, please consult the Greenbone Security documentation for assistance.
Basic Tutorials of OpenVAS: Getting Started
The following is the step-by-step basic tutorial of OpenVAS:
- Log in to the OpenVAS web interface.
Open a web browser and navigate to https://localhost:9392.
Enter your OpenVAS username and password.
- Create a new scan.
Click on the Scans tab.
Click on the New Scan button.
- Select a scan target.
In the Scan Targets section, select the targets that you want to scan. You can select individual targets, target groups, or upload a list of targets.
- Configure the scan settings.
In the Scan Settings section, you can configure the scan settings, such as the scan type, the scan plugins, and the scan credentials.
For a basic scan, I recommend using the Quick Scan scan type and the Default scan profile.
- Start the scan.
Click on the Start Scan button to start the scan.
- Review the scan results.
Once the scan is complete, you can review the scan results by clicking on the Reports tab.
The scan results will show you a list of all the vulnerabilities that were found on the scan targets.
- Remediate the vulnerabilities.
Once you have reviewed the scan results, you can start remediating the vulnerabilities.
OpenVAS provides remediation guidance for each vulnerability.
Some additional tips for using OpenVAS:
- You can use OpenVAS to scan a variety of targets, including networks, hosts, and web applications.
- OpenVAS offers a variety of scan types, such as basic scans, compliance scans, and penetration tests.
- You can use OpenVAS plugins to scan for specific vulnerabilities.
- You can use OpenVAS credentials to scan targets that require authentication.
- OpenVAS generates a variety of reports, such as vulnerability reports, compliance reports, and executive reports.
If you are new to OpenVAS, I recommend starting with a quick scan of your network. This will give you a good overview of the vulnerabilities that are present on your network. You can then use the scan results to prioritize your remediation efforts.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

