What is Palo Alto Networks ?

Palo Alto Networks, a multinational leader in cybersecurity, delivers innovative solutions that protect users, applications, and data across cloud, network, and mobile environments. Their focus lies on simplifying security while delivering comprehensive protection.
Top 10 use cases of Palo Alto Networks?
Top 10 Use Cases of Palo Alto Networks:
- Next-Generation Firewalls (NGFWs): Their flagship offering, NGFWs provide deep inspection, threat prevention, application control, and sandboxing for advanced security at the network edge.
- Cloud Security: Protects cloud workloads and applications with security posture management, workload protection, and threat detection across various cloud platforms.
- Endpoint Security: Safeguards endpoints from malware, ransomware, and other threats with real-time protection, behavioral analysis, and endpoint detection and response (EDR).
- SASE (Secure Access Service Edge): Combines network security and security services like CASB and zero-trust network access (ZTNA) for unified, cloud-delivered security.
- Zero Trust Network Access (ZTNA): Verifies all users and devices before granting access to resources, implementing a “never trust, always verify” approach.
- Data Loss Prevention (DLP): Prevents sensitive data leaks and exfiltration with content inspection, activity monitoring, and data encryption.
- IoT Security: Secures Internet of Things (IoT) devices with dedicated security solutions and integration with broader security posture.
- Network Function Virtualization (NFV): Offers virtualized security functions for agility and scalability in cloud and hybrid environments.
- Managed Security Services (MSS): Provides 24/7 monitoring, threat detection, and incident response by security experts for comprehensive protection.
- Threat Intelligence: Delivers real-time threat feeds and insights to stay informed about emerging threats and proactively adapt security measures.
Notes:
- Palo Alto Networks acquired CloudGenix in 2020, and Prisma Cloud products leverage the acquired technology. Ensure you consult the correct resources and documentation specific to your chosen product, whether a legacy Palo Alto Networks offering or an acquired CloudGenix solution.
- Specific use cases and features can vary depending on the chosen product and configuration.
What are the feature of Palo Alto Networks?
Palo Alto Networks boasts a diverse range of features across its product portfolio, addressing various security needs for organizations of all sizes. Here’s a breakdown of some key areas and features:
Network Security:
- Next-Generation Firewalls (NGFWs):
- Deep packet inspection for comprehensive traffic analysis.
- Threat prevention against known and unknown threats.
- Application control for granular application visibility and control.
- WildFire sandboxing for advanced threat detection and detonation.
- Panorama central management for simplified policy management and visibility.
- Prisma Cloud:
- Cloud security posture management for continuous cloud security assessment.
- Workload protection for securing cloud workloads across various platforms.
- Network security for securing cloud network traffic and enforcing security policies.
- Prisma SASE:
- Secure Access Service Edge (SASE) combining network security, CASB, and ZTNA for unified cloud-delivered security.
- Zero Trust Network Access (ZTNA) for verifying all users and devices before access.
Endpoint Security:
- Cortex XDR:
- Endpoint detection and response (EDR) for comprehensive endpoint threat detection and investigation.
- Behavioral analysis for identifying suspicious activity and potential threats.
- Prevention capabilities to block malicious activity before it impacts systems.
- Prisma Endpoint:
- Next-generation endpoint protection against malware, ransomware, and other threats.
- Real-time protection with continuous monitoring and threat detection.
- Integration with Cortex XDR for broader threat context and response.
Data Security:
- Prisma Data Loss Prevention (DLP):
- Prevents sensitive data leaks and exfiltration with content inspection and activity monitoring.
- Data encryption for protecting sensitive data at rest and in transit.
- Cloud and endpoint deployment options for flexibility.
Additional Features:
- IoT Security: Secures Internet of Things (IoT) devices with dedicated security solutions and integration with broader security posture.
- Network Function Virtualization (NFV): Offers virtualized security functions for agility and scalability in cloud and hybrid environments.
- Threat Intelligence: Delivers real-time threat feeds and insights to stay informed about emerging threats and proactively adapt security measures.
How Palo Alto Networks works and Architecture?
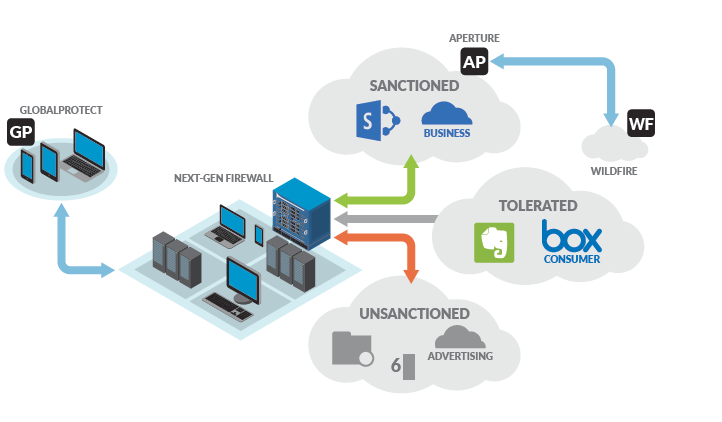
Palo Alto Networks delivers robust security solutions backed by a sophisticated yet adaptable architecture. Understanding its key components and functionalities can help you appreciate its effectiveness.
Core Architectural Principles:
- Single Pass Architecture: Analyzes all traffic in a single pass, efficiently combining multiple security functions without performance impact.
- App-ID™ Technology: Identifies applications regardless of port or encryption, enabling granular application control and security policies.
- Dynamic Threat Prevention: Utilizes real-time threat intelligence and machine learning to detect and block emerging threats proactively.
- Centralized Management: Simplifies security management through the Panorama platform, offering policy configuration, visibility, and reporting.
- Open Integration: Integrates with diverse security tools and platforms for broader security ecosystem compatibility.
Key Components:
- Next-Generation Firewalls (NGFWs): The foundation of Palo Alto Networks security, NGFWs inspect and filter traffic based on security policies, leveraging App-ID™ and threat prevention technologies.
- Panorama: Centralized management platform for configuring NGFWs, monitoring security events, and generating reports.
- WildFire Cloud Sandbox: Analyzes suspicious files in a sandbox environment to detect and detonate advanced threats.
- Cortex XDR: Endpoint detection and response platform offering threat detection, investigation, and response capabilities across endpoints.
- Prisma Cloud: Cloud security suite protecting cloud workloads, networks, and data with various security services.
- Prisma SASE: Delivers Secure Access Service Edge (SASE) combining network security, CASB, and ZTNA for cloud-delivered security.
Architectural Benefits:
- Enhanced Security: Comprehensive threat protection with deep inspection, application control, and advanced threat prevention.
- Simplified Management: Centralized management and policy configuration for efficient security administration.
- Performance and Scalability: Single-pass architecture ensures high performance and adaptability to growing needs.
- Flexibility and Openness: Adapts to diverse environments and integrates with existing security tools for broader visibility.
How to Install Palo Alto Networks it?
The installation process for Palo Alto Networks (PAN) devices can vary depending on the specific model and deployment scenario. However, here’s a general overview of the steps involved:
Preparation:
- Review System Requirements: Ensure your environment meets the hardware, software, and network requirements for your PAN model.
- Gather Installation Materials: Make sure you have all necessary cables, licenses, and activation keys readily available.
- Choose an Installation Method: There are different methods for deploying PAN devices, including physical appliances, virtual machines, and containerized deployments.
Hardware Installation (for physical appliances):
- Mount the device: Install the PAN device in a suitable rack location with proper grounding and cooling.
- Connect network interfaces: Connect the appropriate network interfaces (copper or fiber) to your network using compatible cables.
- Connect management interface: Connect the management interface to a dedicated network segment for secure administrative access.
- Connect power supply: Connect the AC power cords to the device and a reliable power source.
Software Installation:
- Power on the device: Wait for the device to boot up fully.
- Access the web interface: Use a web browser to access the PAN web interface on the management interface IP address.
- Follow the initial configuration wizard: The wizard will guide you through setting up basic parameters like hostname, IP address, time zone, and administrator credentials.
- Update software: Download and install the latest PAN-OS software version for your device.
- Configure security policies: Define firewall rules and security policies to control network traffic flow.
Important Notes:
- The installation process can be complex and may require network expertise. Refer to the official documentation and seek professional help if needed.
- Consider security best practices when configuring your PAN device, such as using strong passwords and enabling multi-factor authentication.
- Regularly update your PAN-OS software to benefit from security enhancements and bug fixes.
Basic Tutorials of Palo Alto Networks: Getting Started

Configuring and managing a Palo Alto Networks firewall involves multiple steps, and the exact procedures can vary depending on the specific model and PAN-OS version you are using. Below is a simplified guide for basic firewall setup using Palo Alto Networks.
Prerequisites:
- Palo Alto Networks Device:
- Ensure that your Palo Alto Networks firewall device is physically connected and powered on.
2. Access to the Web Interface:
- Connect to the web interface of the Palo Alto Networks device using a web browser.
Tutorial: Basic Firewall Configuration
Step 1: Accessing the Web Interface
- Open a web browser and enter the IP address assigned to the Palo Alto Networks firewall management interface.
- Log in using the default or configured administrative credentials.
Step 2: Initial Configuration
- Follow the initial setup wizard to configure basic settings such as hostname, management IP, and administrative password.
Step 3: Licensing
- Navigate to the “Device” tab and select “Licenses.”
- Activate the license by entering the license key obtained from Palo Alto Networks.
Step 4: Network Interfaces Configuration
- In the “Network” tab, go to “Interfaces.”
- Configure network interfaces, including management, data, and optional interfaces.
- Assign IP addresses, set zones, and configure interface settings.
Step 5: Security Zones
- Navigate to the “Policies” tab and select “Security.”
- Create security zones for different segments of your network.
Step 6: Security Policies
- Create security policies to control traffic between zones.
- Define source and destination zones, applications, and actions (allow, deny).
- Attach security profiles like antivirus, anti-spyware, and URL filtering.
Step 7: NAT Policies
- Navigate to “Policies” and select “NAT.”
- Create NAT policies to translate source or destination addresses if necessary.
Step 8: Commit Configuration
- Click on “Commit” to apply the changes.
Step 9: Monitor and Logging
- Use the “Monitor” tab to view real-time logs, traffic, and system information.
- Review logs for any blocked or allowed traffic.
Note:
- This tutorial provides a basic overview, and actual configurations might involve more detailed settings based on your organization’s requirements.
- Regularly update your Palo Alto Networks device with the latest software updates and security patches.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

