What is Policy?
A policy is any type of rule, condition, or instruction that governs IT operations or processes. A policy could be a rule that defines which conditions must be met in order for a code to pass a security control and be deployed, for example. Or, it could be a set of procedures that are executed automatically in response to a security event.
Operation and security teams can’t possibly administer all cloud instances and workloads manually to ensure adherence to operational best practices, security rules, and organizational standards. Manual administration will slow your innovation cadence, and it won’t scale.
Codifying and automating your operational best practices, security rules, and organizational standards is a must to ensure a healthy balance between an organization’s rate of innovation and its risk posture.
Types of Policies
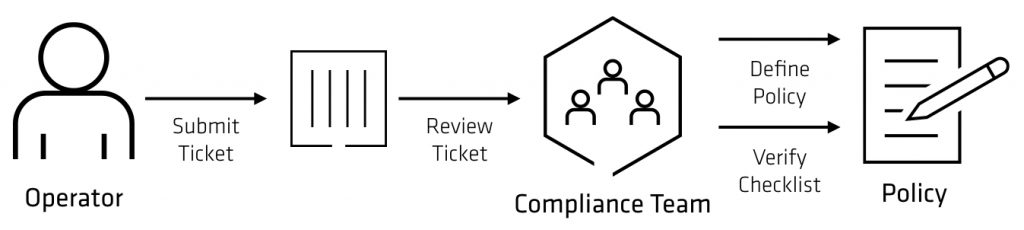
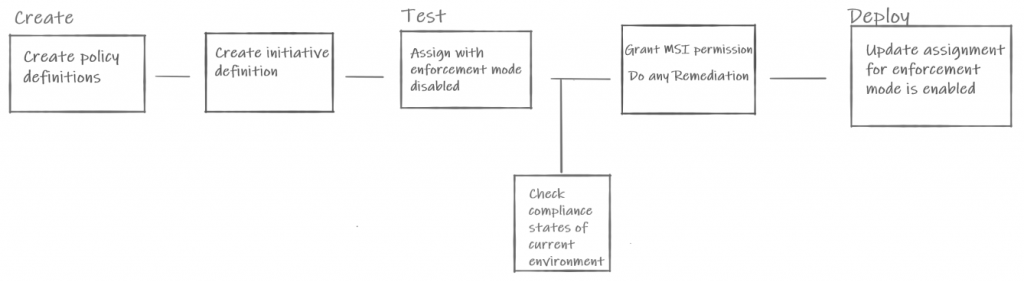
- Compliance Policies: Ensure compliance standards like PCI-DSS, SOC, or GDPR.
- Security Policies: Internal Security Policies for security and infrastructure principles and data.
- Operational Excellence: Policies for service interruption or degradation.
What is Policy as Code?
Policy-as-code is an approach to policy management in which policies are defined, updated, shared, and enforced using code. Policy as code is the idea of writing code in a high-level language to manage and automate policies. By leveraging code-based automation instead of relying on manual processes to manage policies, policy-as-code allows teams to move more quickly and reduce the potential for mistakes due to human error. By representing policies as code in text files, proven software development best practices can be adopted such as version control, automated testing, and automated deployment.
Many existing policy or ACL systems do not practice policy as code. Many policies are set by clicking in a GUI, which isn’t easily repeatable nor versionable. They usually don’t provide any system for testing policies other than testing an action that would violate the policy. This makes it difficult for automated testing. And the policy language itself varies by product.
Policy-as-code is the use of code to define and manage rules and conditions. Under a policy-as-code approach, teams write out policies using some type of programming language, such as Python, YAML, or Rego. The specific language usually depends on which policy-as-code management and enforcement tools you are using.
Policy as Code is the writing code plan as a high-level language to manage and automate the policies. Similar to the concept of Infrastructure-as-Code (IaC), Policy-as-Code (PaC) is the concept of codification of your policies.
Benefits of Policy as code
Sandboxing
Policies provide the guardrails for other automated systems. As the number of automated systems grow, there is also a growing need to protect those automated systems from performing dangerous actions. Manual verification is too slow; policies need to be represented as code to keep up with other automated systems.
Codification
By representing policy logic as code, the information and logic about a policy is directly represented in code and can be augmented with comments rather than relying on oral tradition to learn about the reason for policies.
Speed
The ability to automate policy enforcement also means that policy-as-code results in faster operations than a manual approach.
Visibility
When policies are defined in code, it’s easy for all stakeholders to use the code to understand what is happening within a system. They can review alerting or remediation rules simply by checking which code-based policies are in place, for example, instead of having to ask other engineers and wait for a response.
Version Control
Policies are encouraged to be stored as simple text files managed by a version control system. This lets you gain all the benefits of a modern VCS such as history, diffs, pull requests, and more.
Testing
Policies are just code. Their syntax and behavior can be easily validated with Sentinel. This also encourages automated testing such as through a CI. Paired with a VCS system, this allows a pull request workflow to verify that a policy keeps the system behavior as expected before merging.
Automation
With all policies as code in simple text files, various automation tools can be used. For example, it is trivial to create tools to automatically deploy the policies into a system.
Compliance as Code
Over the past few years, organizations worldwide are now concerned about security and compliance to the requirement of several compliance standards such as GDPR, ISO 27001, HIPAA, PCI DSS, etc., which currently holds business importance. Compliance with the standard has led to introducing security and compliance in the early phases of the software development lifecycle, impacting the whole process. Security is not the same as compliance.
Compliance-as-Code means using programmatic methods (code) for automating the implementation, validation, remediation, monitoring, and reporting of the required compliance standards that an organization needs to be compliant with across the entire organization’s ecosystem.
Policy-as-Code vs. Infrastructure as Code
The concept of policy-as-code may sound similar to Infrastructure as Code, or IaC. IaC, which uses code-based files to automate infrastructure setup and provisioning, has been a common practice for IT operations teams for years.
Whereas IaC is beneficial to IT operations teams who need to provision infrastructure, policy-as-code can improve security operations, compliance management, data management, and far beyond.
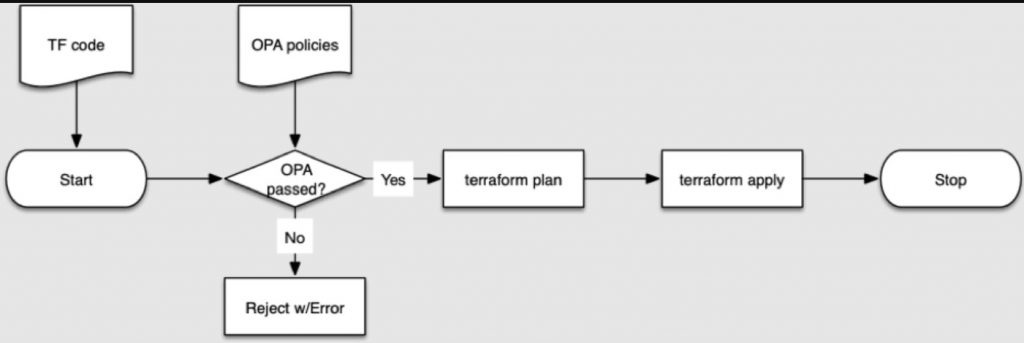
How Does Policy-as-Code Work?
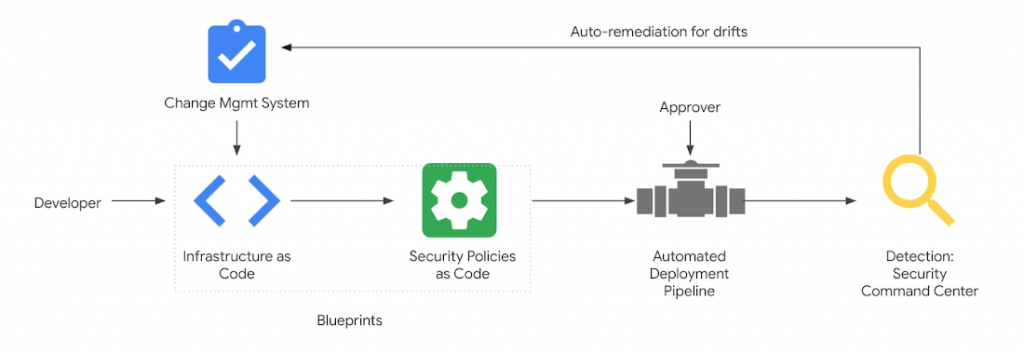
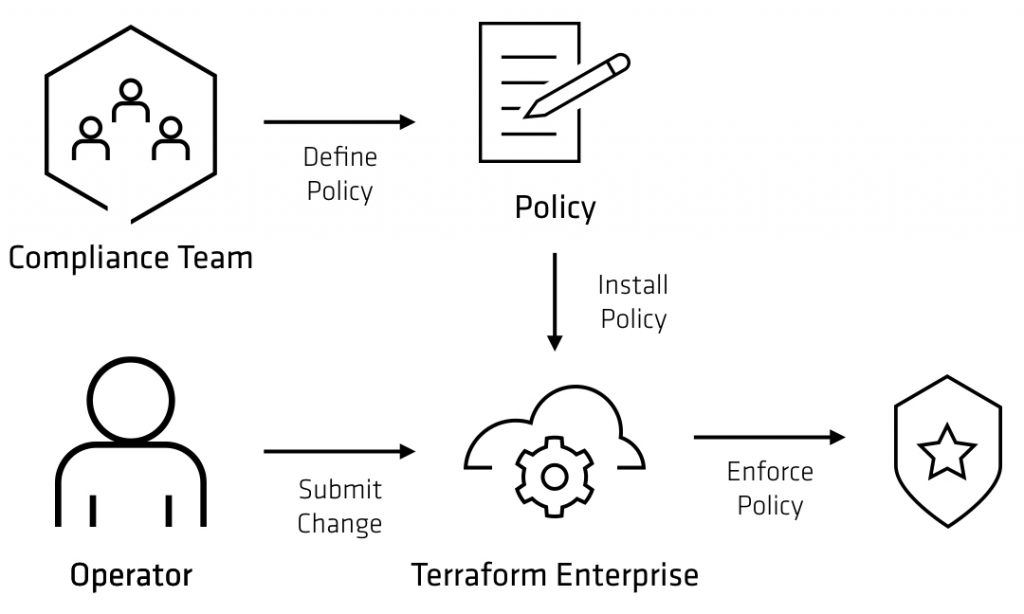
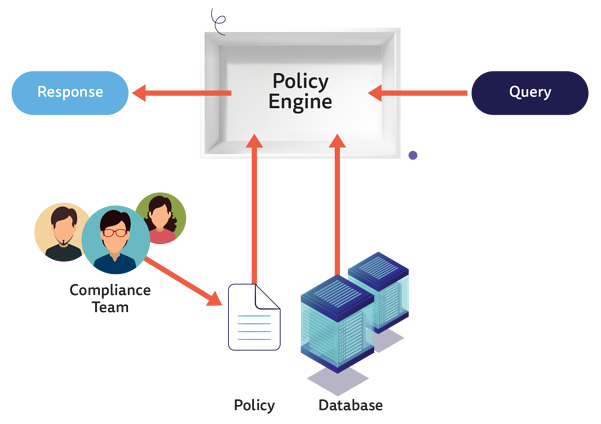
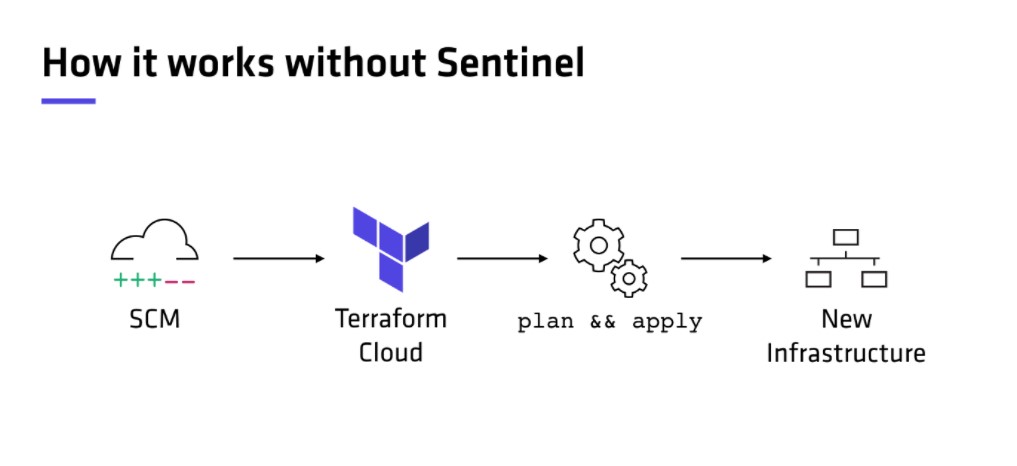
These policies are based on code and reside in text files. These policies foster well-established proven software development best practices that include version control, continuous integration, automated testing, and continuous deployment. Figure 1 illustrates how Policy-as-code works.
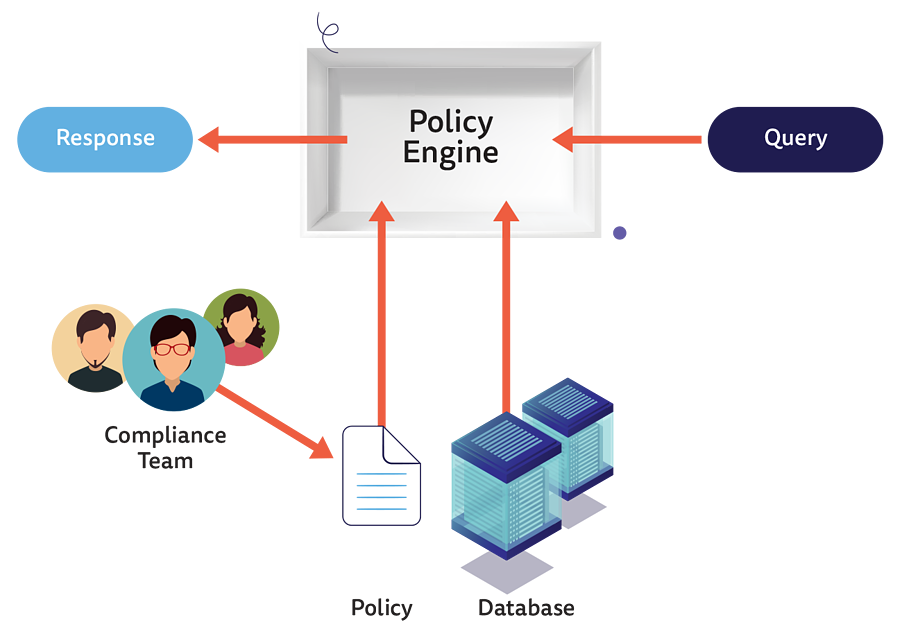
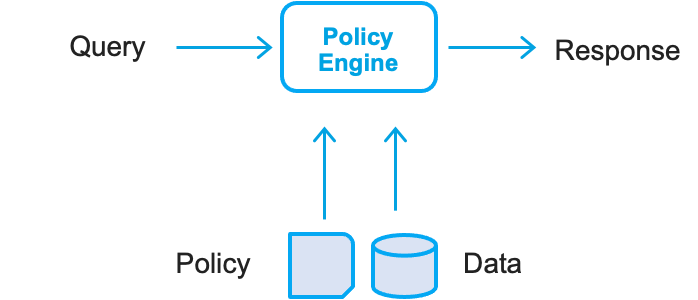
Policy-as-code entails writing policies in a high-level language to administer and automate policies. It takes advantage of a policy engine that accepts a query and some data and policy as an input, processes it all, and generates a query result.
There are open-source policy engines available in the market. There are also policy enforcement platforms available such as Magalix which simplifies the entire process end-to-end.
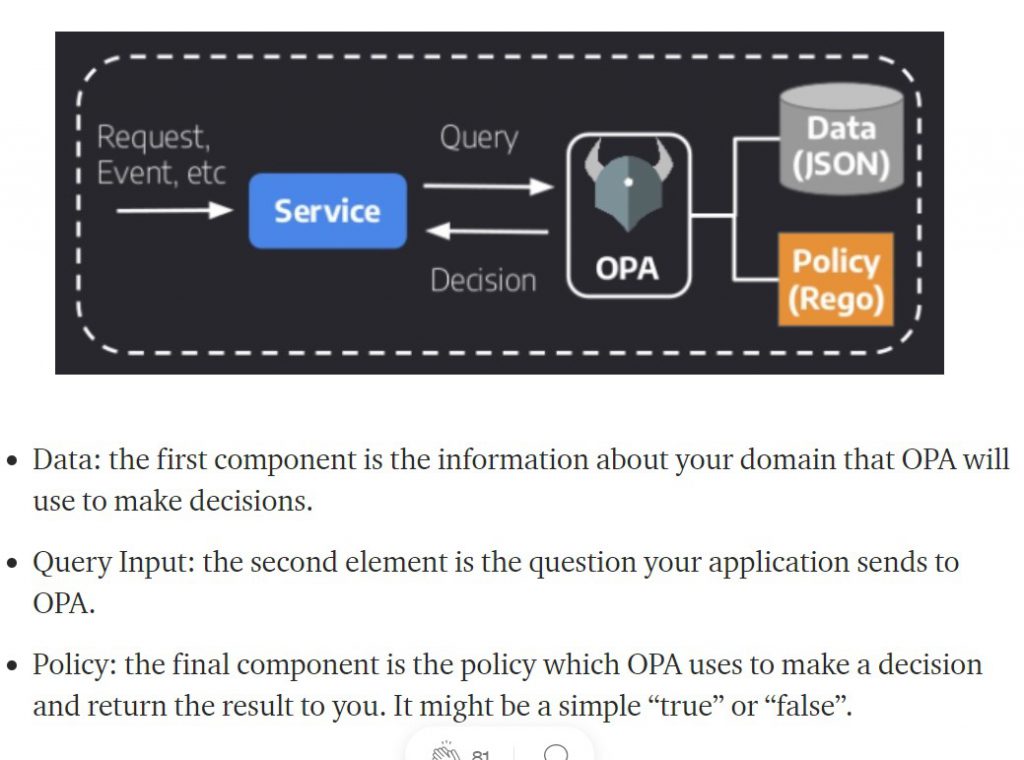
Policy-as-code uses three elements to work. The first of those elements is the policy itself that contains the necessary code that models the decision-making process. The second is data that comprises information about an application, a service, or the environment. Finally, the Query is responsible for triggering the decision-making process based on the data available and the policy provided and uploaded to the policy engine.
How to choose the right PaC solution
Several aspects need to be considered in order to select the right policy framework. Some of these aspects include:
- How community accepted and adopted this particular solution
- How complex the solution is
- How this solution allies to the organization’s capabilities and strategies
- How it satisfies the use cases in your enterprise
- What is the support model
- What is the scalability option
- How it integrates with other (local) tools.
Best Tools for Policy as Code
Planning phase
In the planning phase, organizations can use the SecurityRAT open-source tool provided by OWASP. It lets the team create security requirements as code integrated into every project as an auditable artifact.
Build phase
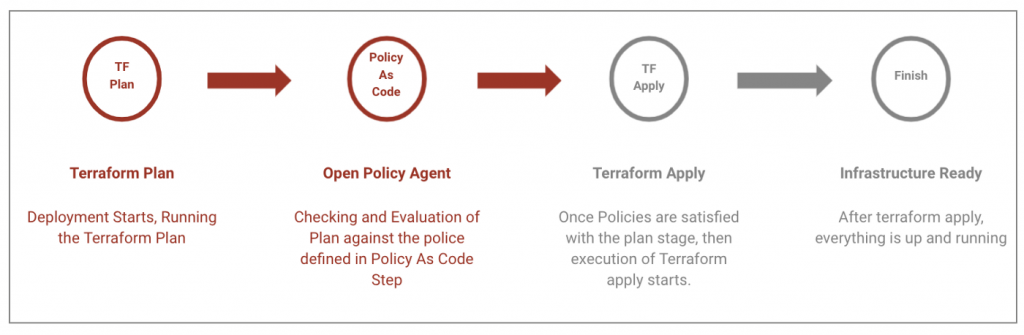
In the build phase, organizations can use TruffleHog, Gitty Leaks, or Git-Secrets to check for secrets in source code. In this phase, tools such as OWASP Dependency-Check, or retireJS can check for vulnerabilities in known components and vulnerable dependencies. Organizations can use InSpec by Chef and Open Policy Agent (OPA) tools in the testing phase. For CI/CD, another tool called Conftest, based on OPA, can validate various requirements. Conftest helps you write tests against structured configuration data. Using Conftest, you can write tests for your Kubernetes configuration, Tekton pipeline definitions, Terraform code, Serverless configs, or any other config files. In the case of Kubernetes, Gatekeeper tool is built on top of OPA to validate and audit kubernetes resources both pre and post-deployment.
Deployment phase
In the deployment phase, organizations prefer CIS benchmarks to harden the industry best practices’ systems/services. IT automation frameworks such as IT Chef, Puppet, or Ansible can be used for this purpose.
SecurityRAT
TruffleHog
Gitty Leaks
Git-Secrets
OWASP Dependency-Check
retireJS
InSpec
Open Policy Agent (OPA)
Open Policy Agent (OPA), a Cloud Native Computing Foundation incubating project, is designed to automate policy tests. OPA provides a unified framework and language for declaring, implementing, and controlling the policies of various components in cloud native solutions. Stop using a different policy language, policy model, and policy API for every product and service you use. Use OPA for a unified toolset and framework for policy across the cloud native stack. Whether for one service or for all your services, use OPA to decouple policy from the service’s code so you can release, analyze, and review policies (which security and compliance teams love) without sacrificing availability or performance.
Conftest
Tekton
Terraform
Chef
Puppet
Ansible
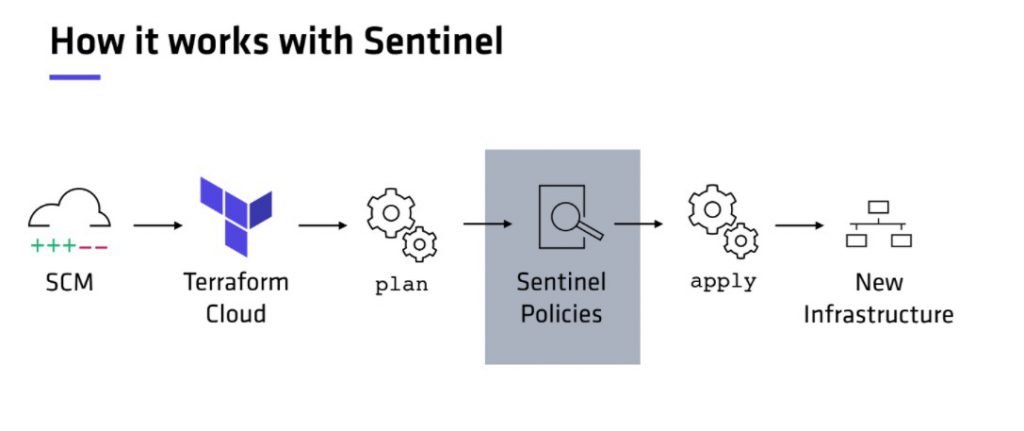
Sentinel
Sentinel is an embeddable policy as code framework to enable fine-grained, logic-based policy decisions that can be extended to source external information to make decisions. Sentinel fully embraces policy as code in a number of ways:
- Language. All Sentinel policies are written using the Sentinel language. This language is made to be inputted directly to text files. As an additional benefit, all Sentinel-enabled applications share the same policy language.
- Development. Sentinel provides a CLI for development and testing. This local CLI can be used to verify policies before deploying them to a system.
- Testing. Sentinel provides a test framework designed specifically for automation. This allows developers and CI systems to further verify policies.
Magalix
Magalix allows you to define and manage these policies, and their lifecycle, in an easy and user-friendly way. Internally, Magalix uses OPA as the policy execution engine. Magalix, by default, will run global policies based on Kubernetes’ best practices for the relevant Kubernetes objects in your cluster.
Pulumi CrossGuard
Pulumi CrossGuard, A PaC engine that works with its other cloud management tools for AWS, Azure, Google Cloud and Kubernetes. Polices are described in Node.js, Go, Python, Open Policy Agent (OPA) or .NET. Policy sets — also called policy packs — are assigned to a particular environment, like AWS, or to a policy group that applies to multiple situations. Policies are enforced centrally by the Pulumi console. Pulumi released the CrossGuard preview last fall. CrossGuard lets you verify, enforce, and apply custom policies on resources in your infrastructure. You can run policies against any Pulumi stack, which means that you can apply policies written in TypeScript to stacks written in any language supported by Pulumi such as Python, Go, and .NET languages. Policy Packs are bundles of policies, and when you run pulumi up, CrossGuard evaluates every resource in the stack against the Policy Pack. CrossGuard works in AWS, Azure, Google Cloud Platform, and Kubernetes.
PacBot
Policy as Code Bot (PacBot) is a platform for continuous compliance monitoring, compliance reporting and security automation for the cloud. In PacBot, security and compliance policies are implemented as code. All resources discovered by PacBot are evaluated against these policies to gauge policy conformance. The PacBot auto-fix framework provides the ability to automatically respond to policy violations by taking predefined actions. PacBot packs in powerful visualization features, giving a simplified view of compliance and making it easy to analyze and remediate policy violations. PacBot is more than a tool to manage cloud misconfiguration, it is a generic platform that can be used to do continuous compliance monitoring and reporting for any domain.
- What is Mobile Virtual Network Operator? - April 18, 2024
- What is Solr? - April 17, 2024
- Difference between UBUNTU and UBUNTU PRO - April 17, 2024


Can we use Checkov custom policies for policy as code?