What is Qualys?

Qualys is a cloud-based cybersecurity and vulnerability management platform that offers a wide range of security and compliance solutions to help organizations identify, prioritize, and remediate security vulnerabilities in their networks, systems, and applications. It is known for its scalability, comprehensive coverage, and ease of use.
Top 10 use cases of Qualys?
Here are the top 10 use cases of Qualys:
- Vulnerability Management: Qualys provides automated vulnerability scanning and assessment to identify and prioritize vulnerabilities in an organization’s IT infrastructure.
- Asset Inventory: It helps organizations maintain an up-to-date inventory of all assets, including servers, workstations, network devices, and applications.
- Patch Management: Qualys assists in patch management by identifying missing patches and helping organizations prioritize and apply critical security updates.
- Compliance Monitoring: It offers compliance scanning against various security standards and regulations, such as PCI DSS, HIPAA, and GDPR, to ensure organizations meet their compliance requirements.
- Web Application Scanning: Qualys can scan web applications for common vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure authentication.
- Network Security: It helps organizations assess and secure their network infrastructure by identifying misconfigurations, weak passwords, and potential attack vectors.
- Container Security: Qualys provides container security solutions to scan and secure containerized applications and orchestration platforms, such as Kubernetes.
- File Integrity Monitoring (FIM): It offers FIM capabilities to monitor and detect unauthorized changes to critical files and directories.
- Security Information and Event Management (SIEM) Integration: Qualys can integrate with SIEM platforms to provide real-time threat detection and incident response capabilities.
- Cloud Security Posture Management (CSPM): Qualys helps organizations secure their cloud environments by identifying misconfigurations, compliance violations, and security risks in cloud services like AWS, Azure, and Google Cloud.
Additional use cases for Qualys may include vulnerability assessment of IoT devices, mobile application security testing, and continuous monitoring of an organization’s security posture.
Qualys is suitable for organizations of all sizes and is particularly valuable for those looking for a cloud-based, scalable, and comprehensive solution for managing cybersecurity and compliance. It streamlines vulnerability management processes, enhances security, and facilitates compliance efforts.
What are the feature of Qualys?
Qualys is a robust cloud-based cybersecurity and vulnerability management platform with a wide range of features designed to help organizations identify, prioritize, and remediate security vulnerabilities. Here are the key features of Qualys:
- Vulnerability Assessment: Qualys offers automated vulnerability scanning and assessment across an organization’s IT infrastructure, including networks, systems, and applications.
- Asset Inventory: It provides a comprehensive asset inventory that helps organizations maintain an up-to-date view of all devices and software across their network.
- Patch Management: Qualys helps organizations identify missing patches and prioritize the deployment of critical security updates to address vulnerabilities.
- Compliance Management: It offers compliance scanning and reporting against various security standards and regulations, facilitating compliance efforts like PCI DSS, HIPAA, and GDPR.
- Web Application Scanning: Qualys can scan web applications for common vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure authentication.
- Network Security Assessment: It assists organizations in identifying network misconfigurations, weak passwords, and potential attack vectors to enhance overall network security.
- Container Security: Qualys provides container security solutions to scan and secure containerized applications and container orchestration platforms like Kubernetes.
- File Integrity Monitoring (FIM): FIM capabilities enable organizations to monitor and detect unauthorized changes to critical files and directories.
- Security Information and Event Management (SIEM) Integration: Qualys can integrate with SIEM platforms to provide real-time threat detection and incident response capabilities.
- Cloud Security Posture Management (CSPM): It helps organizations secure their cloud environments by identifying misconfigurations, compliance violations, and security risks in cloud services such as AWS, Azure, and Google Cloud.
How Qualys works and Architecture?
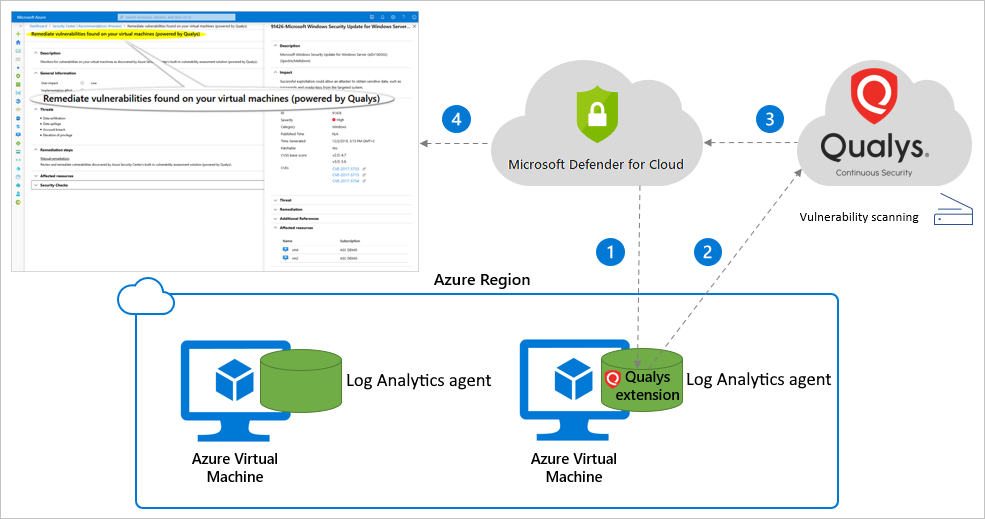
Qualys operates as a cloud-based platform, which simplifies deployment and management. Here’s a simplified overview of how Qualys works:
- Deployment: Organizations subscribe to Qualys as a cloud-based service. No on-premises hardware or software installation is required.
- Asset Discovery: Qualys begins by discovering all assets within an organization’s environment, including devices, servers, applications, and services.
- Vulnerability Scanning: Automated scans are performed according to predefined policies or schedules. Qualys scans for known vulnerabilities, misconfigurations, and security weaknesses across the entire infrastructure.
- Data Analysis: The scan results are collected and analyzed. Qualys assigns severity levels to vulnerabilities to help organizations prioritize remediation efforts based on risk.
- Reporting and Remediation: Qualys generates detailed reports that include vulnerability descriptions, severity ratings, and recommendations for mitigation. Organizations can use this information to address vulnerabilities and strengthen their security posture.
Qualys follows a cloud-native architecture:
- Qualys Cloud Platform: This is the central cloud-based platform that hosts all the services and components required for vulnerability management, including asset discovery, scanning engines, and data analysis.
- Qualys Scanners: These are distributed scanning appliances that can be deployed on-premises or in cloud environments to perform scans on target systems and devices. Scanners send scan data to the Qualys Cloud Platform for analysis.
- Qualys Agents: Agents are lightweight software components that can be installed on individual hosts. They collect data locally and report it back to the Qualys Cloud Platform, allowing for asset inventory and vulnerability assessment on systems that may not be reachable by scanners.
- Qualys Knowledge Base: It contains a vast collection of vulnerability checks and signatures that are used during scans to identify vulnerabilities and misconfigurations.
Qualys is designed to be scalable, flexible, and easy to use, making it suitable for organizations of all sizes. Its cloud-based nature allows for quick deployment and updates, making it a popular choice for managing cybersecurity and compliance efforts.
How to Install Qualys?
To install the Qualys Cloud Agent, you can follow these steps:
- Log in to the Qualys Cloud Platform.
- Go to Assets > Cloud Agents.
- Click Download Cloud Agent.
- Select the operating system for the host where you want to install the agent.
- Click Download.
- Copy the installer to the host where you want to install the agent.
- Run the installer and follow the on-screen instructions.
To install the Qualys Cloud Agent on Windows:
- Copy the installer to the Windows host where you want to install the agent.
- Click Double to the installer to begin the installation process.
- Follow the on-screen instructions.
To install the Qualys Cloud Agent on Linux:
- Copy the installer to the Linux host where you want to install the agent.
- Open a terminal window.
- Navigate to the directory where you copied the installer.
- Run the following command to install the agent:
“
sudo dpkg -i qualys-cloud-agent–debian6_amd64.deb
“
- Follow the on-screen instructions.
Once the agent is installed, it will automatically start collecting data about your host and sending it to the Qualys Cloud Platform. You can view the data collected by the agent in the Qualys Cloud Platform console.
Some additional tips for installing the Qualys Cloud Agent:
- Make sure that the host where you are installing the agent has a working internet connection.
- Make sure that the host where you are installing the agent meets the minimum requirements for the Qualys Cloud Agent.
- If you are installing the Qualys Cloud Agent on a Windows host, you must have administrator privileges.
- If you are installing the Qualys Cloud Agent on a Linux host, you must have root privileges.
Basic Tutorials of Qualys: Getting Started
The following is the step-by-step basic tutorial of Qualys:
1. Log in to the Qualys Cloud Platform.
2. Create a new scan.
- Go to Assets > Scans.
- Click New Scan.
3. Select the scan type.
For a basic scan, I recommend using the Basic Scan scan type.
4. Select the scan targets.
You can select individual targets, target groups, or upload a list of targets.
5. Configure the scan settings.
For a basic scan, I recommend using the Default scan profile.
6. Start the scan.
Click Start Scan.
7. Review the scan results.
Once the scan is complete, you can review the scan results by clicking on the Reports tab.
8. Remediate the vulnerabilities.
Once you have reviewed the scan results, you can start remediating the vulnerabilities. Qualys provides remediation guidance for each vulnerability.
Some additional tips for using Qualys:
- You can use Qualys to scan a variety of targets, including networks, hosts, and web applications.
- Qualys offers a variety of scan types, such as basic scans, compliance scans, and penetration tests.
- You can use Qualys to create custom scans and scan profiles.
- You can use Qualys to schedule scans and generate reports.
- Qualys offers a variety of integrations with other security products.
If you are new to Qualys, I recommend starting with a basic scan of your network. This will give you a good overview of the vulnerabilities that are present on your network. You can then use the scan results to prioritize your remediation efforts.
Please note that Qualys is a commercial product, so you will need to purchase a license in order to use it.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

