What is QualysGuard Policy Compliance?

QualysGuard Policy Compliance (PC) is a comprehensive cloud-based solution that helps organizations automate and simplify compliance with various security regulations and internal policies. It goes beyond the basics of vulnerability management and security configuration assessment, offering robust features and benefits:
- Automated Assessment and Reporting: Automatically scans systems for misconfigurations, policy violations, and vulnerabilities, providing detailed reports for audit purposes.
- Extensive Knowledge Base: Leverages a vast knowledge base of regulations, industry standards, and compliance frameworks, simplifying mapping and adherence.
- Continuous Monitoring and Remediation: Continuously monitors systems for changes and potential compliance issues, prompting remediation actions when necessary.
- Streamlined Compliance Reporting: Generates comprehensive compliance reports with drill-down capabilities, simplifying audit preparation and demonstrating compliance effectively.
- Integration with QualysGuard Suite: Integrates seamlessly with other QualysGuard modules like Vulnerability Management and Patch Management, offering a unified security posture view.
Top 10 use cases of QualysGuard Policy Compliance?
Top 10 Use Cases of QualysGuard Policy Compliance:
- Achieving and Maintaining Compliance: Manage compliance for various regulations like PCI-DSS, HIPAA, SOX, GDPR, and more.
- Reducing Risks and Penalties: Proactively identify and address compliance gaps before audits and minimize potential penalties.
- Enhancing Security Posture: Improve overall security posture by enforcing consistent security configurations across your IT infrastructure.
- Simplifying Security Operations: Automate routine compliance tasks and reporting, freeing up IT resources for other activities.
- Gaining Visibility and Insights: Gain comprehensive visibility into your compliance status and identify areas for improvement.
- Improving Decision-Making: Make informed security decisions based on real-time data and actionable insights.
- Demonstrating Due Diligence: Provide evidence of compliance efforts to auditors and stakeholders.
- Reducing Manual Work: Automate tasks like policy mapping, configuration assessment, and reporting generation.
- Scaling Compliance Efforts: Efficiently manage compliance across large and complex IT environments.
- Adapting to Changing Regulations: Stay updated on evolving regulations and adjust compliance management processes accordingly.
Benefits of using QualysGuard Policy Compliance:
- Reduced Time and Cost: Save time and resources by automating compliance tasks and streamlining reporting.
- Improved Security Posture: Proactively identify and address security risks to enhance your overall security posture.
- Simplified Compliance Management: Simplify compliance with various regulations and internal policies.
- Increased Visibility and Control: Gain greater visibility into your compliance status and control over your IT environment.
- Reduced Risk of Penalties: Minimize the risk of penalties from non-compliance by proactively addressing issues.
What are the feature of QualysGuard Policy Compliance?
To best explain the features of QualysGuard Policy Compliance (PC), you need to understand your specific interests. What aspects of its functionality are you most curious about? Would you like to know about:
1. Core functionalities:
- Automated configuration and vulnerability assessments: Understand how PC scans systems for misconfigurations, policy violations, and vulnerabilities.
- Extensive compliance coverage: Explore the vast library of pre-built compliance policies mapped to industry standards and regulations.
- Continuous monitoring and remediation: Learn how PC continuously monitors systems for changes and automatically prompts remediation actions for non-compliance.
- Streamlined reporting and dashboards: Discover how PC generates comprehensive reports and customizable dashboards to visualize your compliance posture.
2. Advanced features:
- Threat intelligence integration: Learn how PC integrates with threat intelligence feeds to prioritize vulnerabilities and address emerging threats.
- Endpoint security integration: Explore how PC extends compliance checks to endpoints for holistic IT security management.
- Customization and scripting: Understand how you can customize policies and utilize scripting for enhanced control.
- API access and automation: Discover PC’s open API and how it enables custom integrations and automation of workflows.
3. Specific capabilities:
- File integrity monitoring (FIM): Learn how PC verifies the integrity of critical system files to detect unauthorized changes.
- Security configuration management (SCM): Explore how PC enforces consistent security configurations across your systems.
- Vulnerability management: Understand how PC identifies and prioritizes vulnerabilities for patching and remediation.
4. Integration and extensibility:
- Integration with other QualysGuard modules: Learn how PC seamlessly integrates with other QualysGuard solutions for a unified security platform.
- Third-party integrations: Explore how PC connects with other security tools and data sources for holistic visibility.
By understanding your specific interests, I can tailor my explanation of QualysGuard Policy Compliance’s features to be more relevant and informative, ensuring you get the most out of this powerful compliance management solution.
How QualysGuard Policy Compliance works and Architecture?
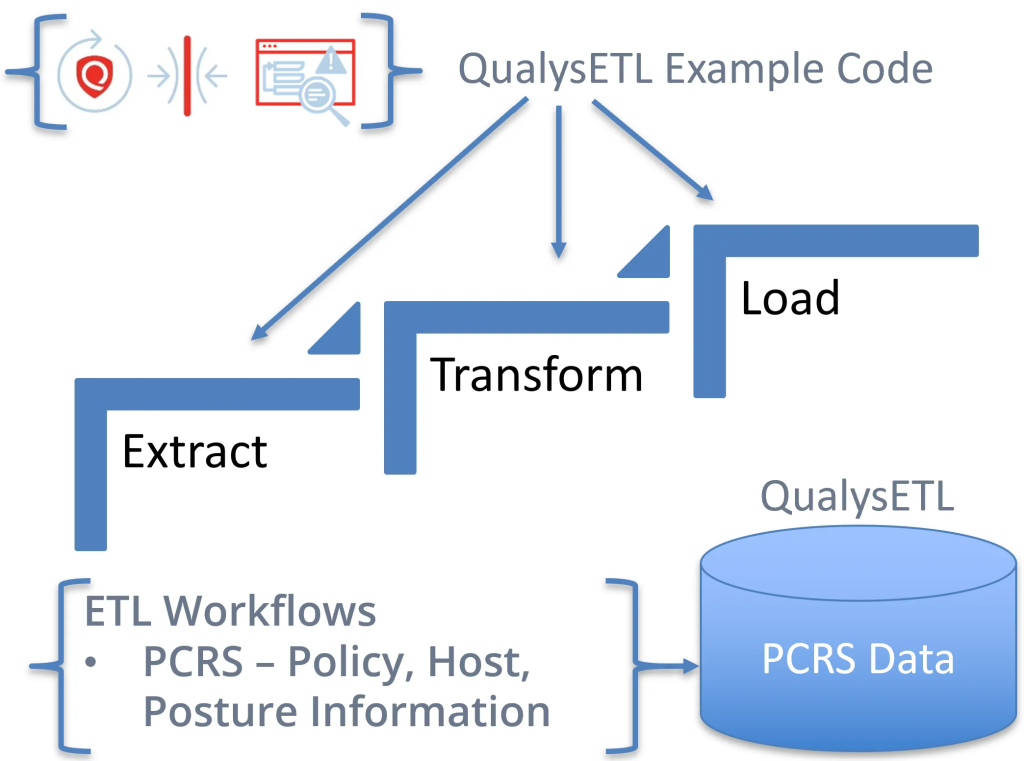
QualysGuard Policy Compliance (PC) functions on a sophisticated cloud-based architecture designed for comprehensive, automated, and scalable compliance management. Let’s dissect its key components:
1. Cloud-based Core:
- Acts as the brain, hosting the main processing engine, databases, and web interface.
- Receives data from scanners and agents deployed across your IT environment.
- Analyzes data against relevant security policies and compliance frameworks.
- Generates reports and alerts.
2. Scanners and Agents:
- Two options to collect data from your systems:
- Scanners: Periodically scan hosts for configuration settings, file integrity, and vulnerabilities.
- Agents: Continuously monitor endpoints for changes and report them to the core.
- Offer flexibility based on your needs and network infrastructure.
3. Databases:
- Store various types of data like system configurations, vulnerabilities, compliance policies, and historical findings.
- Separate databases manage specific data categories for optimized performance and security.
4. Knowledge Base:
- Extensive repository of pre-built compliance policies mapped to various regulations and industry standards.
- Simplifies policy mapping and configuration, saving time and reducing errors.
- Continuously updated to reflect evolving regulations and security threats.
5. Reporting and Dashboards:
- Generate detailed reports with drill-down capabilities, providing insights into compliance status and specific issues.
- Customizable dashboards offer visual representations of your security posture and compliance progress.
- Enable effective communication and reporting to stakeholders and auditors.
6. Integrations:
- Seamlessly integrates with other QualysGuard modules like Vulnerability Management and Patch Management.
- Connects with third-party security tools and data sources for greater visibility and control.
- Enables automated workflows and data exchange for a unified security strategy.
Work Flow:
- Scanners or agents continuously gather data from your IT environment.
- Data is sent to the cloud-based core for analysis.
- Core compares data against relevant policies and compliance frameworks.
- Misconfigurations, violations, and vulnerabilities are identified.
- Alerts and reports are generated, notifying administrators of potential issues.
- Remediation actions are taken to address identified non-compliance.
- Dashboards and reports provide ongoing visibility into compliance progress and security posture.
Benefits of this Architecture:
- Centralized Management: Manage compliance across your entire IT environment from a single platform.
- Continuous Monitoring: Gain real-time insights into your compliance status with continuous data collection and analysis.
- Automation and Scalability: Automate routine tasks and easily scale to accommodate larger environments.
- Extensive Knowledge Base: Simplify policy mapping and compliance adherence with pre-built policies.
- Reporting and Visibility: Leverage detailed reports and customizable dashboards for effective communication and decision-making.
- Integrations and Extensibility: Enhance security posture and automate workflows through seamless integrations.
Understanding the architecture behind QualysGuard Policy Compliance empowers you to leverage its functionalities effectively for streamlined compliance management and an enhanced security posture.
How to Install QualysGuard Policy Compliance it?
Installing QualysGuard Policy Compliance (PC) is a straightforward process, but the specific steps might differ slightly depending on your desired deployment method and existing QualysGuard setup. To guide you efficiently, I need some additional information:
1. Choose your deployment method:
- New QualysGuard account: You’re setting up PC for the first time on a new QualysGuard account.
- Existing QualysGuard account: You’re adding PC to an existing QualysGuard subscription without other modules.
- Upgrade: You’re upgrading an existing QualysGuard PC installation to the latest version.
2. Confirm your chosen configuration:
- Scanners: Decide between using scanners or agents for data collection.
- Agent deployment: If using agents, choose your deployment method (manual, group policy, GPO, etc.).
- Network access: Ensure firewall rules and network access are configured for communication between servers, agents, and QualysGuard cloud resources.
3. Follow the appropriate guide:
- Qualys provides detailed installation guides for each deployment scenario and configuration option.
- These guides offer step-by-step instructions for setting up the QualysGuard server, deploying scanners or agents, configuring policies, and connecting to the QualysGuard cloud.
Note: Before installation, consult with Qualys Support or a qualified IT professional if you need assistance or have specific requirements.
Basic Tutorials of QualysGuard Policy Compliance: Getting Started
Now I can tailor the tutorials to your specific needs. let’s have a look at some step-by-step basic tutorials to get you started:
1. Creating a PCI DSS Policy:
- Step 1: Navigate to Compliance > PCI DSS > Manage Policies.
- Step 2: Press “Create Policy” and give a descriptive name.
- Step 3: Select the relevant PCI DSS version you want to comply with.
- Step 4: Configure policy settings under various categories like Authentication, Network Security, Vulnerability Management, etc.
- Step 5: Include specific controls or requirements you want to enforce.
- Step 6: Save the policy.
2. Assigning the Policy to Systems:
- Step 1: Go to Assets > Inventory.
- Step 2: Select the “Scoping Groups” tab and create a group containing systems in scope for PCI compliance.
- Step 3: Navigate to Compliance > PCI DSS > Manage Scopes.
- Step 4: Create a new scope, associating it with the previously created group.
- Step 5: Assign the created PCI DSS policy to the defined scope.
3. Running PCI DSS Scan and Reviewing Results:
- Step 1: Go to Compliance > PCI DSS > Manage Scans.
- Step 2: Click “Create Scan” and choose the assigned scope.
- Step 3: Select the desired scan type (Quick, Full, etc.).
- Step 4: Initiate the scan and wait for completion.
- Step 5: Review the scan results within Compliance > PCI DSS > Scan Results.
- Step 6: Analyze identified vulnerabilities and non-compliance issues.
4. Remediation and Reporting:
- Step 1: Prioritize vulnerabilities and compliance failures based on severity and risk.
- Step 2: Generate reports for internal or external stakeholders using Compliance > Reporting.
- Step 3: Implement remediation actions to address identified issues.
- Step 4: Retest and monitor progress towards PCI compliance.
These are basic steps, and QualysGuard offers advanced features for deeper PCI DSS compliance management.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

