What is RSA Archer?

RSA Archer is a powerful integrated risk management (GRC) platform that helps organizations manage compliance, risk, and governance in a unified and proactive manner. It allows them to:
Centralize data and processes: Streamline risk management activities by bringing together data from various sources into a single platform. Identify and assess risks: Facilitate proactive risk identification, assessment, and prioritization, enabling informed decision-making. Automate tasks and workflows: Automate manual tasks and processes, saving time and improving efficiency. Improve decision-making: Provide visibility into risks and compliance gaps, supporting data-driven decision-making. Enhance collaboration: Foster collaboration between different departments involved in risk management and compliance.
Top 10 use cases of RSA Archer?
Here are the top 10 use cases of RSA Archer:
- IT Risk Management: Identify and manage IT risks like cyber threats, data breaches, and system failures.
- Compliance Management: Automate compliance workflows, track progress, and demonstrate adherence to regulations like HIPAA, GDPR, and SOX.
- Operational Risk Management: Assess and mitigate operational risks related to processes, people, and third parties.
- Regulatory Reporting: Generate compliance reports easily and efficiently for various regulatory bodies.
- Internal Controls Management: Design, implement, and monitor internal controls to mitigate risks and ensure financial accuracy.
- Vendor Risk Management: Evaluate and manage risks associated with third-party vendors.
- Business Continuity and Disaster Recovery: Plan for and respond to disruptive events like natural disasters and cyberattacks.
- Enterprise Risk Management: Gain a holistic view of all enterprise risks and make informed strategic decisions.
- Audit Management: Streamline the audit process, improve audit readiness, and address audit findings effectively.
- Security Incident Response: Manage security incidents efficiently by automating workflows, collaborating with stakeholders, and documenting response actions.
Tip: RSA Archer is a versatile platform that can be customized to address specific needs of various industries and organizations. Its comprehensive features and functionalities can significantly improve risk management, compliance adherence, and overall organizational resilience.
What are the feature of RSA Archer?
RSA Archer boasts a rich suite of features designed to empower organizations through comprehensive GRC functionalities. Here’s a breakdown of its key capabilities:
Data Management and Integration:
- Centralized Data Repository: Consolidate risk, compliance, and audit data from diverse sources into a single platform for holistic analysis and reporting.
- Data Quality Management: Ensure data accuracy and consistency through automated validation, cleansing, and standardization tools.
- Integrations: Connect seamlessly with existing IT systems, security tools, and data warehouses for real-time updates and data exchange.
Risk Management:
- Risk Identification and Assessment: Utilize built-in libraries and methodologies to identify threats, assess their impact and likelihood, and prioritize risks effectively.
- Scenario Modeling and Impact Analysis: Simulate potential risk scenarios and their consequences to inform mitigation strategies and resource allocation.
- Risk Tracking and Reporting: Monitor risk status, track progress on mitigation plans, and generate comprehensive risk reports for stakeholders.
Compliance Management:
- Compliance Mapping and Gap Analysis: Map regulations and internal policies to relevant controls and processes, identifying compliance gaps and areas for improvement.
- Compliance Workflow Automation: Automate compliance tasks like policy updates, control testing, and reporting, reducing manual effort and improving efficiency.
- Audit Trail and Evidence Management: Maintain a record of compliance activities and audit findings for complete transparency and regulatory readiness.
Governance and Collaboration:
- Policy and Procedure Management: Centralize and manage policies, procedures, and controls across the organization, ensuring consistency and adherence.
- Workflow Management: Design and execute customized workflows for risk management, compliance, and audit processes, fostering collaboration and accountability.
- Reporting and Analytics: Generate comprehensive reports and dashboards that provide insights into risk landscape, compliance status, and overall GRC performance.
Additional Features:
- User Access and Role Management: Define granular access controls to ensure data security and user accountability.
- Business Intelligence and Data Visualization: Leverage advanced analytics tools and dashboards to gain deeper insights from GRC data.
- Mobile App: Access key features and data on the go through the RSA Archer mobile app.
Note: RSA Archer’s features are scalable and customizable, allowing organizations to tailor the platform to their specific needs and regulatory requirements.
How RSA Archer works and Architecture?
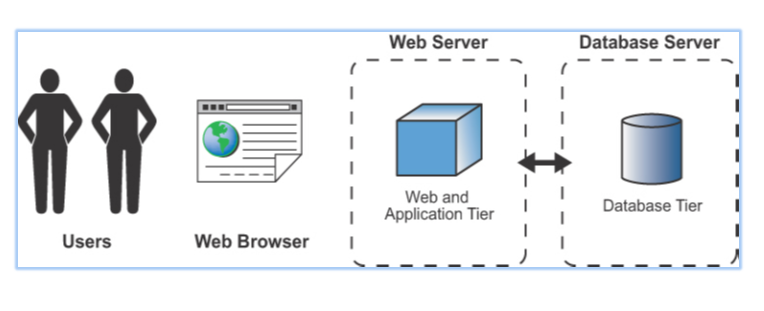
RSA Archer’s powerful capabilities are backed by a well-designed architecture and optimized workflow. Let’s delve into the details:
Architecture:
- Multi-tier Architecture: Archer utilizes a multi-tier architecture for scalability and reliability. This layered approach separates data storage, application logic, and user interface, ensuring efficient performance even with large data volumes.
- Modular Design: The platform is made up of modular components that can be customized and extended to meet specific organizational needs. This allows for flexible integrations and future enhancements.
- Cloud-based Deployment: Archer can be deployed either on-premises or in the cloud, offering organizations greater flexibility and accessibility.
- Security and Compliance: RSA Archer adheres to strict security standards and compliance requirements, protecting sensitive data and ensuring regulatory adherence.
Workflow:
- Data Ingestion and Integration: Data from various sources like databases, spreadsheets, and third-party applications is collected and normalized into Archer’s central repository.
- Risk and Compliance Mapping: Risks, controls, and regulations are mapped to relevant processes and activities within the organization.
- Risk Assessment and Prioritization: Archer facilitates risk identification, assessment, and prioritization using built-in methodologies and user-defined metrics.
- Compliance Management: The platform supports automated workflows for compliance tasks like policy updates, control testing, and gap analysis.
- Governance and Reporting: Archer allows for centralized management of policies and procedures, while generating comprehensive reports and dashboards for stakeholders.
- Continuous Improvement: The platform provides data-driven insights to identify areas for improvement in risk management, compliance, and overall GRC effectiveness.
Benefits of this Architecture and Workflow:
- Scalability and Performance: The multi-tier architecture and cloud-based deployment ensure efficient handling of large data volumes and reliable performance even during peak usage.
- Flexibility and Customization: The modular design and extensive integrations allow organizations to tailor the platform to their specific needs and regulatory requirements.
- Enhanced Efficiency and Automation: Automating compliance tasks and workflows saves time and reduces manual effort, freeing up resources for more strategic initiatives.
- Improved Decision-making: Comprehensive data analysis and reporting provide valuable insights to support informed decision-making and proactive risk mitigation.
- Streamlined Collaboration: The platform fosters collaboration across departments by providing a centralized platform for risk and compliance data and processes.
Note: RSA Archer’s architecture and workflow work together to deliver a powerful and user-friendly GRC solution. By leveraging its capabilities, organizations can significantly improve their risk management, compliance adherence, and overall operational resilience.
How to Install RSA Archer it?
Installing RSA Archer isn’t quite as straightforward as downloading an app due to its complexity and customization needs. There are multiple deployment options and specific requirements to consider before embarking on the installation process. Here’s what you need to know:
Deployment Options:
- On-premises: Requires installation on your own physical servers and infrastructure, offering full control and data security but demanding significant IT resources and expertise.
- Cloud-based: Hosted by RSA in their secure cloud environment, providing easier deployment and maintenance but limiting some customization options and data control.
Installation Requirements:
- Server Hardware and Software: Depending on your chosen deployment option and expected data volume, specific server hardware, operating systems, and database software configurations are required.
- Network Infrastructure: Strong and secure network connectivity is crucial for smooth data flow and system performance.
- Technical Expertise: Installing and configuring RSA Archer demands expertise in IT infrastructure, security, and the platform itself.
Recommended steps:
- Contact RSA Archer Sales: Discuss your specific needs and determine the most suitable deployment option for your organization.
- System Requirements Assessment: RSA will analyze your IT infrastructure and recommend necessary hardware and software upgrades to meet the platform’s requirements.
- Installation Services: Consider leveraging RSA’s professional installation services to ensure a smooth and successful setup.
- Configuration and Customization: After installation, configure the platform to align with your organizational policies, workflows, and risk management framework.
- Training and Support: Ensure adequate training for your team on using and managing the platform effectively.
Important Tips:
- Start with a clear understanding of your risk management and compliance goals to align them with the platform’s functionalities.
- Consult the RSA Archer installation documentation and available resources for detailed technical information and step-by-step guides.
- Consider partnering with RSA certified consultants or solution providers for expert guidance and assistance throughout the installation and configuration process.
Always keep in mind, Installing RSA Archer involves intricate planning, infrastructure considerations, and technical expertise. It’s crucial to consult with RSA and evaluate your specific needs before embarking on the installation process.
Basic Tutorials of RSA Archer: Getting Started

Due to the complexity and customization nature of RSA Archer, providing a single step-by-step tutorial wouldn’t be feasible. The specific functionalities and workflows vary greatly depending on your organization’s needs and chosen modules. However, I can offer some general guidance and basic steps to get you started on your RSA Archer journey:
1. Getting Familiar with the Interface:
- Log in: Use your credentials to access the RSA Archer web interface.
- Explore navigation: Familiarize yourself with the main navigation bar, menus, and dashboards.
- Review user documentation: Consult the RSA Archer user guide and available training materials for detailed explanations of features and functionalities.
2. Configuring Your Environment:
- Manage users and roles: Define user access levels and assign roles based on individual responsibilities and permissions.
- Configure data sources: Connect RSA Archer to your existing data repositories like databases, spreadsheets, and security applications.
- Customize dashboards and reports: Tailor dashboards and reports to visualize key risk and compliance metrics relevant to your organization.
3. Basic Risk Management:
- Identify risks: Utilize built-in libraries or create custom libraries to identify potential threats and vulnerabilities.
- Assess risks: Evaluate the likelihood and impact of identified risks to prioritize risk mitigation efforts.
- Develop mitigation plans: Define actions and resources needed to address and mitigate identified risks.
- Track and monitor risks: Monitor the status of risks and update mitigation plans as needed.
4. Introduction to Compliance Management:
- Map regulations: Map relevant regulations and internal policies to controls and processes within your organization.
- Conduct gap analysis: Identify gaps between existing controls and compliance requirements.
- Develop compliance plans: Define actions and timelines for achieving compliance with specific regulations.
- Automate workflows: Automate compliance tasks like policy updates, control testing, and reporting for improved efficiency.
5. Continuous Improvement:
- Analyze data and reports: Regularly review risk and compliance data to identify trends and areas for improvement.
- Update policies and procedures: Refine your risk management and compliance processes based on data-driven insights.
- Engage stakeholders: Foster collaboration and information sharing across departments to enhance overall GRC effectiveness.
Note: These are just basic steps to get you started. RSA Archer offers a vast array of features and functionalities beyond these introductory examples.
It’s crucial to:
- Define your specific goals: Clearly understand your risk management and compliance needs before attempting specific actions within the platform.
- Consult with RSA and experts: Consider seeking guidance from RSA technical teams or certified consultants to tailor the platform to your specific needs and ensure successful implementation.
- Leverage training and resources: Utilize RSA’s training materials, workshops, and online resources to gain a deeper understanding of the platform and its capabilities.
With dedication and proper guidance, you can leverage RSA Archer to significantly improve your organization’s risk management, compliance adherence, and overall governance efficiency.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

