What is SailPoint?

SailPoint is a leading identity and access management (IAM) platform that offers a comprehensive set of solutions for managing digital identities, controlling access to applications and data, and ensuring security and compliance. SailPoint provides a wide range of features and capabilities to address various IAM needs.
SailPoint’s platform is designed to help organizations manage user identities, streamline access controls, improve security, and ensure compliance with regulatory requirements. It offers a wide range of features and capabilities to support these use cases, making it a valuable tool for IAM in various industries and use cases.
Top 10 use cases of SailPoint:
Here are the top 10 use cases of SailPoint:
- Identity Governance: Implement identity governance solutions to establish a centralized repository for user identities, access privileges, and entitlements, ensuring that users have the right level of access.
- Access Request and Approval: Enable users to request access to applications and resources, and automate the approval process based on predefined policies and workflows.
- User Provisioning and De-Provisioning: Automate the process of granting and revoking access to applications and systems, ensuring that users have the necessary access privileges throughout their lifecycle.
- Role-Based Access Control (RBAC): Define roles and entitlements within the organization and assign users to appropriate roles, streamlining access management and reducing the risk of unauthorized access.
- Single Sign-On (SSO): Implement SSO to allow users to access multiple applications with a single set of credentials, improving user experience and security.
- Access Certification and Recertification: Regularly review and certify user access rights to identify and remediate excessive or inappropriate access permissions.
- Privileged Access Management (PAM): Manage and secure privileged accounts, ensuring that privileged users have controlled access and activity monitoring.
- Identity Analytics: Utilize identity analytics to detect unusual user behavior and identify potential security threats or policy violations.
- Password Management: Implement self-service password reset and change policies to reduce helpdesk calls and improve user productivity.
- Compliance and Audit Reporting: Generate compliance reports and audit logs to demonstrate adherence to regulatory requirements and internal security policies.
- Identity Federation: Establish trust relationships with external identity providers (IdPs) to enable secure SSO and collaboration with partners and external organizations.
- IoT Device Identity: Securely manage identities and access for Internet of Things (IoT) devices to ensure that only authorized devices can interact with your systems.
- Data Access Governance: Monitor and control data access, ensuring that sensitive data is accessed only by authorized users and applications.
What are the feature of SailPoint?
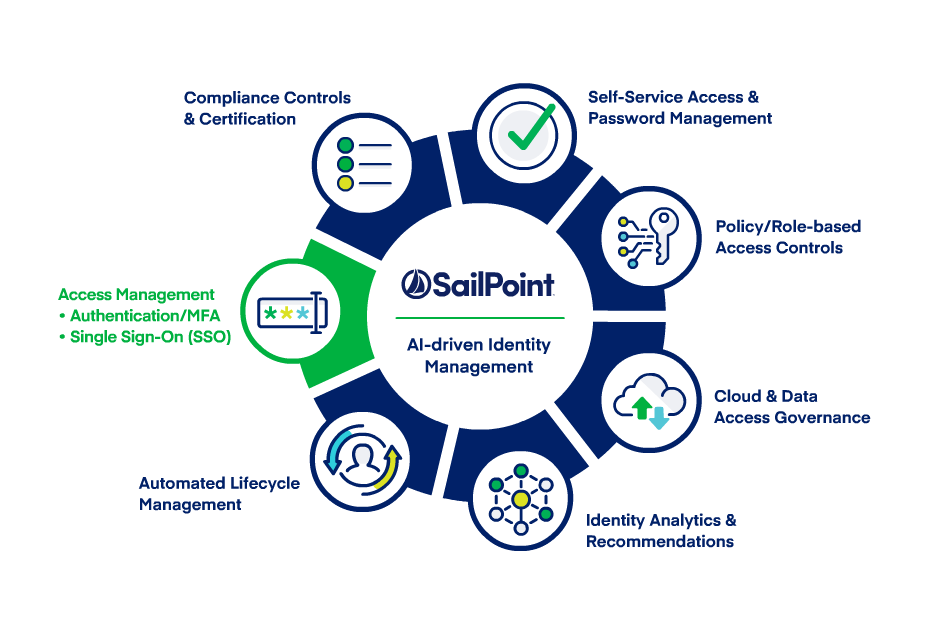
SailPoint is a comprehensive identity and access management (IAM) platform that provides a wide range of features and capabilities for managing digital identities, securing access to applications and data, and ensuring compliance. Here are the key features of SailPoint, along with an overview of how it works and its architecture:
Key Features of SailPoint:
- Identity Governance: SailPoint offers robust identity governance capabilities for managing user identities, access privileges, and entitlements.
- Access Request and Approval: Enable users to request access to applications and resources, and automate the approval process based on predefined policies and workflows.
- User Provisioning and De-Provisioning: Automate user onboarding and offboarding processes, ensuring that users have the right level of access throughout their lifecycle.
- Role-Based Access Control (RBAC): Define roles and entitlements within the organization, assign users to appropriate roles, and manage access based on roles.
- Access Certification and Recertification: Regularly review and certify user access rights to identify and remediate excessive or inappropriate access permissions.
- Single Sign-On (SSO): Implement SSO to allow users to access multiple applications with a single set of credentials, improving user experience and security.
- Privileged Access Management (PAM): Manage and secure privileged accounts, ensuring that privileged users have controlled access and activity monitoring.
- Identity Analytics: Utilize identity analytics to detect unusual user behavior and identify potential security threats or policy violations.
- Password Management: Implement self-service password reset and change policies to reduce helpdesk calls and improve user productivity.
- Compliance and Audit Reporting: Generate compliance reports and audit logs to demonstrate adherence to regulatory requirements and internal security policies.
- Identity Federation: Establish trust relationships with external identity providers (IdPs) to enable secure SSO and collaboration with partners and external organizations.
How SailPoint works and Architecture?
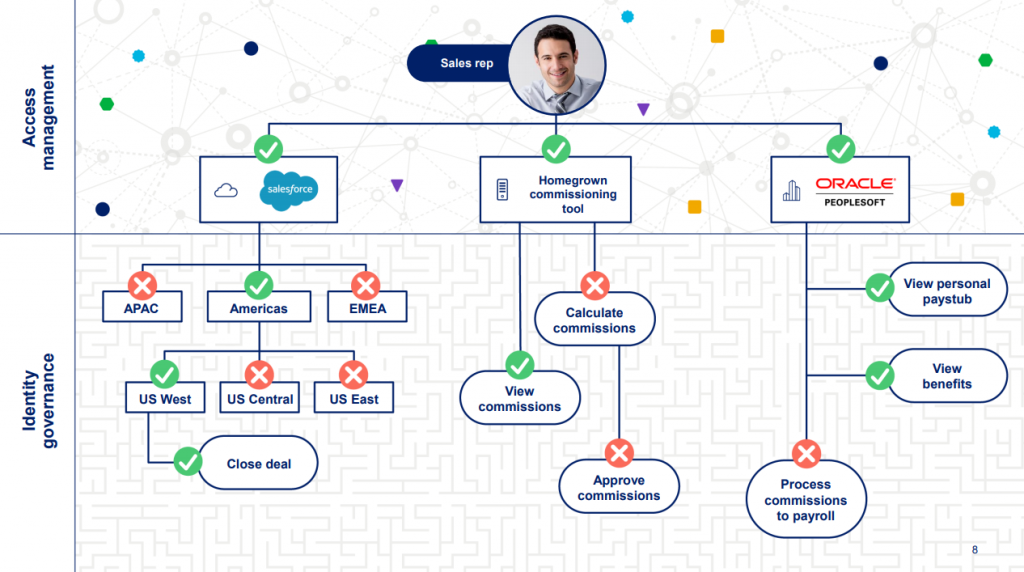
SailPoint operates as a centralized IAM platform, providing a comprehensive solution for managing identities and access. Here’s an overview of how it works:
- Identity Repository: SailPoint maintains a centralized repository of user identities, roles, access entitlements, and policies.
- Access Request: Users initiate access requests for applications and resources through SailPoint’s self-service portal.
- Policy-Based Approval: Access requests are subject to predefined policies and workflows that determine whether access should be granted or denied.
- Provisioning and De-Provisioning: Based on approval, SailPoint automates the provisioning or de-provisioning of access, ensuring that users have the appropriate access rights.
- Access Certification: SailPoint conducts access certification campaigns to review and certify user access rights, identifying and addressing access anomalies.
- Identity Analytics: Identity analytics continuously monitor user behavior and access patterns, identifying risks and policy violations.
- Compliance and Reporting: SailPoint generates compliance reports and audit logs to demonstrate compliance with regulatory requirements and internal security policies.
SailPoint’s architecture is designed to provide scalability, flexibility, and security. It comprises several key components:
- Identity Cube: This component serves as the identity repository, storing user identities, roles, access entitlements, and policy definitions.
- Identity Governance: This component includes features for identity governance, including access request management, access certification, and policy enforcement.
- Access Management: Access management features include SSO, access provisioning, de-provisioning, role management, and privileged access management.
- Identity Analytics: Identity analytics capabilities continuously analyze user behavior and access patterns, identifying risks and anomalies.
- Workflow and Policy Engine: SailPoint’s workflow and policy engine orchestrates access request approvals, provisioning, de-provisioning, and certification processes.
- User Interface: SailPoint provides a user-friendly interface for administrators, managers, and end-users to manage identities, access requests, and certifications.
- Integration Connectors: SailPoint offers connectors to integrate with various identity repositories, applications, and directories to synchronize and manage user data and access.
- Audit and Reporting: Audit logs and reporting capabilities provide visibility into user activities, access events, and compliance status.
SailPoint’s architecture is designed to support on-premises, cloud, and hybrid deployments, making it suitable for organizations of varying sizes and industries. It plays a critical role in managing user identities, access controls, and compliance, helping organizations enhance security and governance.
How to Install SailPoint?
To install SailPoint IdentityIQ, you will need to download the installation package from the SailPoint website. Once you have downloaded the installation package, you can install it on your server using the following steps:
- Extract the installation package
Extract the SailPoint installation package to a directory on your server.
- Run the installation script
Run the SailPoint installation script to install SailPoint IdentityIQ on your server. The installation script will prompt you for information about your SailPoint IdentityIQ installation, such as the installation directory, the database connection information, and the administrator account information.
- Configure SailPoint IdentityIQ
Once SailPoint IdentityIQ is installed, you will need to configure it. You can configure SailPoint IdentityIQ using the SailPoint IdentityIQ configuration console. The configuration console is a web-based application that allows you to configure SailPoint IdentityIQ and manage your SailPoint IdentityIQ environment.
Example use case:
You want to install SailPoint IdentityIQ to provide identity governance and administration (IGA) services for your organization. You can install SailPoint IdentityIQ on your premises using the following steps:
- Download the SailPoint IdentityIQ installation package from the SailPoint website.
- Extract the installation package to a directory on your server.
- Run the SailPoint IdentityIQ installation script.
- Configure SailPoint IdentityIQ using the SailPoint IdentityIQ configuration console.
Once SailPoint IdentityIQ is installed and configured, you can use it to manage the identities of your users and applications. You can also use SailPoint IdentityIQ to enforce access control policies and to audit user activity.
Additional tips:
- Before you install SailPoint IdentityIQ, make sure that you meet the system requirements.
- Make sure that you have a backup of your data before you install SailPoint IdentityIQ.
- Follow the SailPoint IdentityIQ documentation carefully when you install and configure SailPoint IdentityIQ.
- If you need assistance with installing, configuring, or using SailPoint IdentityIQ, you can contact SailPoint support.
Basic Tutorials of SailPoint: Getting Started

The following steps are the Basic Tutorials of Swimlane:
1. What is a swimlane diagram?
A swimlane diagram is a type of flowchart that visually depicts the flow of a process or workflow, with each step assigned to a specific person or team. It is a useful tool for communicating and documenting complex processes, and for identifying bottlenecks and areas for improvement.
2. How to create a swimlane diagram
To create a swimlane diagram, you can follow these steps:
- Identify the steps in your process or workflow. What are all of the tasks that need to be completed in order to achieve the desired outcome?
- Group the steps into logical swimlanes. Swimlanes can be grouped by department, function, role, or any other criteria that makes sense for your process.
- Draw the swimlanes on your diagram. You can use a drawing tool or a diagram template to create your swimlane diagram.
- Add the steps to the swimlanes in the order in which they occur. Use arrows to connect the steps and indicate the flow of the process.
- Label the swimlanes and steps. Explain what each swimlane and step represents.
- Review and refine your diagram. Once you have completed your swimlane diagram, review it carefully to make sure that it is accurate and easy to understand. You may need to make some changes to improve the clarity and flow of your diagram.
3. Example of a swimlane diagram
The following is an example of a swimlane diagram for a simple customer support process:
Customer Support Process
Customer | Support Agent
----------- | --------------
Create ticket | Assign ticket
| Investigate issue
| Resolve issue
| Close ticket
This diagram shows the two main swimlanes in the customer support process: the customer and the support agent. The steps in the process are assigned to the appropriate swimlane, and arrows connect the steps to indicate the flow of the process.
4. Tips for creating swimlane diagrams
Here are some tips for creating swimlane diagrams:
- Use clear and concise labels for the swimlanes and steps.
- Apply arrows to clearly indicate the flow of the process.
- Use different colors or patterns to distinguish between different swimlanes and steps.
- Keep your diagram decent and easy to read. Avoid using too much text or too many symbols.
- Use a swimlane diagram template to get started quickly and easily.
5. Benefits of using swimlane diagrams
Swimlane diagrams offer a number of benefits, including:
- Improved communication: Swimlane diagrams can help to communicate complex processes in a clear and concise way.
- Increased visibility: Swimlane diagrams can help to identify bottlenecks and areas for improvement in processes.
- Enhanced collaboration: Swimlane diagrams can be used to facilitate collaboration between different departments or teams involved in a process.
- Better documentation: Swimlane diagrams can be used to document processes for future reference.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

