What is Skyhigh Networks?
Skyhigh Networks, now known as Skyhigh Security, is a cloud security company offering comprehensive services to protect your organization’s cloud applications, data, and devices. It has transitioned from focusing solely on network security to a broader scope encompassing data protection and cloud-native application security.
Here’s a breakdown of its key offerings:
1. Cloud Access Security Broker (CASB):
- Secures access to cloud applications and protects against data leakage.
- Provides granular access controls, data loss prevention (DLP), and threat detection for cloud apps.
- Offers cloud-to-cloud data protection and integrates with existing security tools.
2. Secure Web Gateway (SWG):
- Filters web traffic to block malware, phishing attacks, and malicious websites.
- Enforces web security policies and protects users from online threats.
- Provides secure remote access and content filtering for various devices.
3. Zero Trust Network Access (ZTNA):
- Enables secure access to internal resources from any device or location.
- Verifies user identities and device posture before granting access.
- Simplifies remote work and enhances security for distributed workforces.
4. Data Loss Prevention (DLP):
- Prevents unauthorized data exfiltration from cloud applications and devices.
- Identifies and classifies sensitive data, enforces encryption, and blocks data leaks.
- Complies with data privacy regulations like GDPR and HIPAA.
5. Endpoint Protection Platform (EPP):
- Protects devices from malware, ransomware, and other threats.
- Provides endpoint encryption, vulnerability management, and intrusion detection.
- Integrates with cloud security solutions for holistic protection.
6. Cloud-Native Application Security Platform (CNAPP):
- Secures your organization’s cloud-native applications and microservices.
- Offers vulnerability management, container security, and API security.
- Provides comprehensive protection for modern application development and deployment.
Top 10 use cases of Skyhigh Networks?
Top 10 Use Cases of Skyhigh Security:
- Securely access and manage cloud applications: Gain visibility and control over cloud app usage, enforce access policies, and prevent data breaches.
- Protect against malware and phishing attacks: Filter web traffic to block malicious websites and protect users from online threats.
- Enable secure remote work: Provide safe access to internal resources for remote employees regardless of location or device.
- Prevent data loss and comply with regulations: Implement DLP to secure sensitive data, prevent exfiltration, and meet data privacy compliance requirements.
- Secure endpoints and devices: Protect devices from malware, ransomware, and other threats, minimizing cybersecurity risks.
- Secure cloud-native applications: Protect modern applications and microservices against vulnerabilities and ensure secure development and deployment.
- Simplify security management: Consolidate various security tools into a single platform for centralized management and reporting.
- Improve user experience: Provide a seamless and secure user experience for accessing cloud applications and resources.
- Gain insights into cloud activity: Generate comprehensive reports and logs to track user behavior, identify threats, and improve security posture.
- Respond to security incidents: Streamline incident response with automated workflows and forensics tools for faster mitigation of threats.
These are just a few examples, and Skyhigh Security can be tailored to meet various security needs across your organization. It can be an invaluable tool for securing your cloud environment, protecting sensitive data, and ensuring compliance with data privacy regulations.
What are the feature of Skyhigh Networks?
While Skyhigh Networks is now renamed and operates as Skyhigh Security, the features remain fundamentally the same. Here’s a breakdown of its key capabilities:
1. Cloud Access Security Broker (CASB):
- Visibility and Control: Gain deep insights into cloud app usage, user activity, and data flows. Enforce granular access controls to regulate user permissions and secure sensitive data.
- Data Loss Prevention (DLP): Prevent unauthorized data exfiltration across cloud apps and devices through content inspection, encryption, and watermarking.
- Threat Protection: Protect against advanced threats like malware, phishing, and insider threats with continuous monitoring and real-time detection.
- Compliance Management: Streamline compliance with regulations like GDPR, HIPAA, and PCI DSS by automating assessments and reporting.
2. Secure Web Gateway (SWG):
- Web filtering: Block access to malicious websites and unwanted content like gambling, violence, or social media to ensure safe and productive browsing.
- Advanced Threat Protection: Block malware, phishing attacks, and ransomware before they reach endpoints, safeguarding devices and data.
- Secure Remote Access: Enable secure access to internal resources for remote employees regardless of their location or device.
- URL Rewriting and Encryption: Enhance security and user experience by rewriting unsafe URLs and encrypting web traffic between users and websites.
3. Zero Trust Network Access (ZTNA):
- Least Privilege Access: Grant users access to specific applications and resources based on their role and need-to-know basis, minimizing attack surface.
- Continuous Authentication: Continuously verify user identities and device posture to enforce real-time access control and prevent unauthorized access.
- Session Recording and Replay: Record user sessions for auditing and forensics purposes to enhance security investigations and incident response.
- Device Security: Enforce device security policies, including endpoint encryption and malware protection, to secure access from unmanaged devices.
4. Data Loss Prevention (DLP):
- Content Inspection: Identify and classify sensitive data across cloud apps, emails, and files using advanced content inspection techniques.
- Data Encryption: Encrypt sensitive data at rest and in transit to ensure confidentiality even in case of breaches.
- Data Leakage Prevention: Block unauthorized data exfiltration through email, cloud apps, and device channels.
- Data Discovery and Classification: Automatically discover and classify sensitive data across all data stores to simplify DLP implementation.
5. Endpoint Protection Platform (EPP):
- Anti-Malware and Antivirus: Protect devices from malware, ransomware, and other threats through signature-based and behavior-based detection.
- Endpoint Patch Management: Automate endpoint patching to ensure timely vulnerability mitigation and prevent exploit attempts.
- Device Control and Encryption: Secure devices by enforcing device usage policies, including endpoint encryption and peripheral control.
- Endpoint Visibility and Reporting: Gain insights into endpoint activity and security posture through detailed reports and logs.
Additional Features:
- Advanced Analytics and Reporting: Gain insights into user behavior, app usage, and security threats through comprehensive analytics and reporting tools.
- API Integration: Integrate Skyhigh with existing security tools and workflows for seamless coordination and threat detection.
- Incident Response: Streamline incident response with automated workflows, forensics tools, and threat containment capabilities.
- User Education and Training: Provide users with security awareness training and education to promote safer cloud usage.
Remember, Skyhigh Security offers a modular platform, so you can choose the features you need to build your ideal security posture.
How Skyhigh Networks works and Architecture?
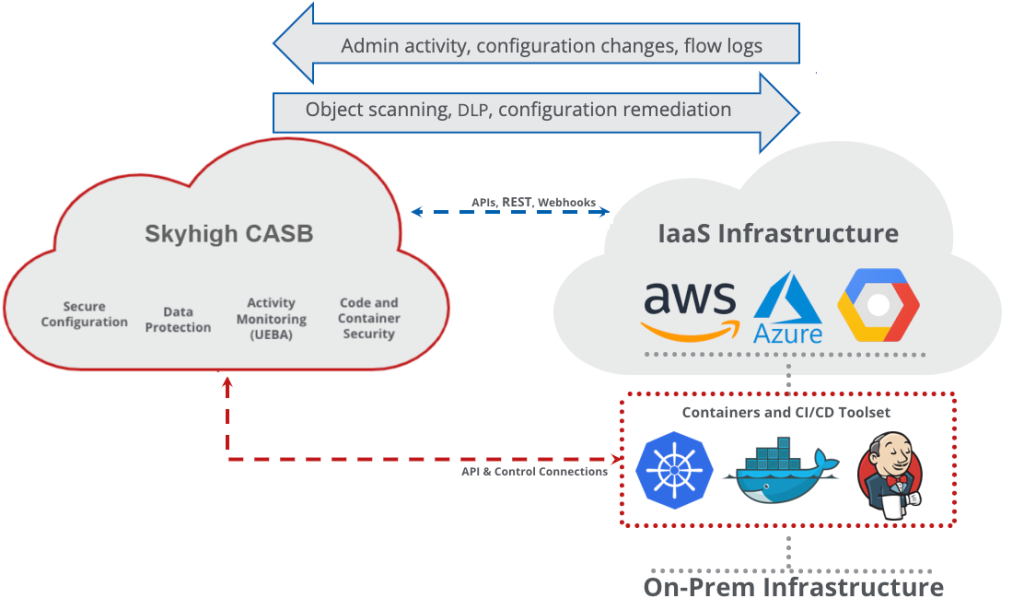
While Skyhigh Networks is now known as Skyhigh Security, its underlying functionalities and architecture haven’t changed significantly. Here’s how it works and its architectural strengths:
1. Global Network of Data Centers:
- Skyhigh boasts a geographically distributed network of data centers strategically located around the world. This ensures low latency and optimal performance for users regardless of their location.
- Each data center houses all core components of the platform, including databases, DLP scanning engines, malware engines, and access control modules.
2. Reverse Proxy and Data Inspection:
- When a user accesses a cloud application, the request is routed through a Skyhigh reverse proxy.
- This proxy intercepts the traffic and performs various security checks:
- DLP: Scans data for sensitive information and applies configured policies.
- Threat Detection: Analyzes traffic for malware, phishing attacks, and other threats.
- Access Control: Enforces granular access controls based on user roles, policies, and context.
- If the inspection passes, the request is forwarded to the cloud application, and the response is returned to the user through the reverse proxy.
3. Data Security and Encryption:
- Skyhigh offers various data security features, including:
- Data Encryption: Sensitive data is encrypted at rest and in transit using robust encryption algorithms.
- Tokenization: Sensitive data can be replaced with non-reversible tokens to further minimize risk.
- Data Loss Prevention (DLP): Prevents unauthorized data sharing and exfiltration through various techniques.
4. Scalability and Resilience:
- Skyhigh’s architecture is designed for automatic scaling and high availability.
- Data centers can dynamically scale up or down based on resource demands, ensuring optimal performance and resource utilization.
- If a data center experiences an outage, traffic is automatically redirected to other healthy data centers, minimizing downtime and service disruptions.
5. Centralized Management and Reporting:
- Skyhigh provides a centralized management console to configure security policies, monitor user activity, and generate reports.
- This centralized view allows organizations to manage their entire cloud security posture from a single location.
Benefits of Skyhigh Security Architecture:
- Global Accessibility: Users around the world experience low latency and fast performance.
- Enhanced Security: Comprehensive data security features protect against various threats.
- Scalability and Reliability: Automatic scaling and resilience ensure high availability and optimal performance.
- Centralized Management: Simplified management and reporting for efficient security administration.
This high-level overview provides a basic understanding of how Skyhigh works and its architectural advantages.
How to Install Skyhigh Networks it?
Installing Skyhigh Security (formerly Skyhigh Networks) depends on your chosen deployment method and desired features. To provide the most accurate instructions, I need some additional information:
1. Deployment Method:
- Cloud-based: This is the simplest and most common option, requiring minimal configuration and no on-premise installation.
- Hybrid: This combines cloud services with on-premise components for additional control and customization.
- API Integration: This integrates Skyhigh Security with existing security tools for unified management.
2. Desired Features:
- Cloud Access Security Broker (CASB): Secures access to cloud apps and protects against data leakage.
- Secure Web Gateway (SWG): Filters web traffic and blocks threats.
- Zero Trust Network Access (ZTNA): Enables secure remote access to internal resources.
- Data Loss Prevention (DLP): Prevents unauthorized data exfiltration.
- Endpoint Protection Platform (EPP): Protects devices from malware and threats.
3. Technical Expertise:
- Comfortable with basic IT tasks: You can follow detailed instructions independently.
- Prefer expert guidance: I can offer additional support and troubleshooting.
Once I have this information, I can create a tailored installation guide with specific steps, including:
- Account Setup: Registering for a Skyhigh Security trial or subscription and accessing the administration console.
- Configuration for your chosen deployment method: Cloud requires minimal setup, hybrid needs on-premise agent installation, and API integration follows specific documentation.
- Feature Activation and Configuration: Enabling desired features and configuring specific settings according to your needs.
- Integration with Cloud Applications and Directories (Optional): Connecting Skyhigh Security to cloud apps and user directories for seamless security workflow.
- User Management and Access Control: Defining user roles, assigning permissions, and implementing security policies.
- Monitoring and Reporting: Accessing dashboards and reports to track user activity, identify threats, and ensure compliance.
Note: The provided steps are a general outline, and specific instructions will vary depending on your chosen features, configurations, and deployment method.
Basic Tutorials of Skyhigh Networks: Getting Started

To offer the most helpful and accurate stepwise tutorials for Skyhigh Security (previously Skyhigh Networks). Now, it time to look at step-by-step basic tutorials of Skyhigh Networks :
1. Deployment Method:
- Cloud-based: Easiest and most common, requires minimal configuration.
- Hybrid: Combines cloud services with on-premise components for more control.
- API Integration: Connects Skyhigh Security with existing security tools.
2. Desired Features:
- Cloud Access Security Broker (CASB): Secure access and protect data in cloud apps.
- Secure Web Gateway (SWG): Filter web traffic and block threats.
- Zero Trust Network Access (ZTNA): Enable secure remote access.
- Data Loss Prevention (DLP): Prevent unauthorized data exfiltration.
- Endpoint Protection Platform (EPP): Protect devices from malware and threats.
3. Technical Expertise:
- Comfortable with basic IT tasks: You can follow detailed instructions independently.
- Prefer expert guidance: I can offer additional support and troubleshooting.
Once you have this information, you can create a customized stepwise guide encompassing:
1. Account Setup:
- Registering for a Skyhigh Security trial or subscription.
- Accessing the administration console.
2. Configuration for your chosen deployment method:
- Cloud-based: Minimal setup, activate desired features in the console.
- Hybrid: Install on-premise agents following specific documentation.
- API Integration: Follow Skyhigh Security’s API integration guide.
3. Feature Activation and Configuration:
- Enabling chosen features (CASB, SWG, ZTNA, DLP, EPP) in the console.
- Configuring specific settings for each feature according to your needs.
4. Integration with Cloud Applications and Directories (Optional):
- Connecting Skyhigh Security to cloud apps and user directories for seamless security.
- Following Skyhigh Security’s documentation for specific integrations.
5. User Management and Access Control:
- Defining user roles and assigning permissions in the console.
- Implementing security policies for access control.
6. Monitoring and Reporting:
- Accessing dashboards and reports to track user activity and identify threats.
- Utilizing Skyhigh Security’s reporting tools for compliance assurance.
Remember, these are general steps, and specific instructions will vary depending on your chosen features, configurations, and deployment method.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

