What is SolarWinds Security Event Manager?

SolarWinds Security Event Manager (SEM) is a centralized SIEM (Security Information and Event Management) solution that helps organizations:
- Collect and aggregate logs from various sources, including network devices, servers, applications, and security tools.
- Correlate and analyze these logs to identify potential security threats and incidents.
- Prioritize and investigate identified threats to effectively respond and remediate them.
- Comply with security regulations by providing centralized logging and reporting capabilities.
SEM offers features like:
- Real-time event monitoring and alerting: Receive immediate notifications for suspicious activity based on pre-defined rules and threat intelligence.
- Log parsing and normalization: Transform diverse log formats into a unified format for efficient analysis.
- Advanced search and filtering: Quickly find specific events based on various criteria.
- Threat intelligence integration: Leverage external threat feeds to enhance detection capabilities.
- Compliance reporting: Generate reports for regulations like PCI DSS, HIPAA, and SOX.
Top 10 use cases of SolarWinds Security Event Manager?
Top 10 Use Cases for SolarWinds SEM:
- Threat Detection and Investigation: Identify, prioritize, and investigate potential security incidents like malware infections, unauthorized access attempts, and data breaches.
- Vulnerability Management: Track vulnerabilities in network devices, applications, and systems, and prioritize patching efforts based on severity and exploitability.
- Insider Threat Detection: Monitor user activity for suspicious behavior that could indicate malicious intent.
- Compliance Reporting and Auditability: Demonstrate compliance with security regulations by generating comprehensive reports and audit logs.
- Log Management and Optimization: Centralize log collection and storage, reducing the strain on individual systems and streamlining analysis.
- Security Incident Response: Automate incident response workflows and escalate critical events to designated personnel.
- User Activity Monitoring: Monitor user access and privilege changes to detect unauthorized activity.
- Fraud Detection: Identify suspicious financial transactions and other potentially fraudulent activities.
- Network Security Monitoring: Monitor network traffic for anomalies and potential threats like denial-of-service attacks.
- Application Security Monitoring: Monitor application logs for security vulnerabilities and prevent data breaches.
SolarWinds SEM can be a valuable tool for organizations of any size looking to improve their security posture and incident response capabilities. By centralizing log management, automating threat detection, and providing actionable insights, SEM can help organizations stay ahead of cyber threats and protect their critical data.
What are the feature of SolarWinds Security Event Manager?
SolarWinds SEM boasts a range of features designed to enhance your security posture through centralized log management, threat detection, and incident response. Following is a breakdown of some key features:
Log Management:
- Centralized log collection: Gather logs from diverse sources like network devices, servers, applications, and security tools.
- Log parsing and normalization: Transform various log formats into a unified format for efficient analysis.
- Log rotation and archive: Manage log storage with customizable rotation policies and long-term archival options.
- Real-time log monitoring: Keep tabs on incoming logs and identify suspicious activity as it happens.
Threat Detection and Analysis:
- Correlation and analysis: Analyze log data from multiple sources to identify patterns and potential threats.
- Pre-defined and custom rules: Leverage pre-configured rules for common threats and create custom rules based on your specific needs.
- Threat intelligence integration: Utilize external feeds to stay informed about emerging threats and vulnerabilities.
- Advanced search and filtering: Quickly find specific events based on various criteria like time, event type, source, and severity.
Incident Response and Remediation:
- Real-time alerting: Receive immediate notifications for high-priority events based on configured rules.
- Incident ticketing and workflow automation: Streamline incident response with automated ticketing and escalation workflows.
- Forensic investigation tools: Analyze logs and system data to investigate root causes of incidents.
- Reporting and auditing: Generate reports for compliance purposes and track incident response effectiveness.
Additional Features:
- Compliance reporting: Generate reports for regulations like PCI DSS, HIPAA, and SOX.
- User activity monitoring: Track user access and privilege changes to detect unauthorized activity.
- Vulnerability management: Track vulnerabilities in network devices, applications, and systems, and prioritize patching efforts.
- Dashboard and reporting: Visualize important security metrics and generate customizable reports for deeper insights.
- Integration with other security tools: Integrate SEM with existing security tools for a more comprehensive security ecosystem.
It’s important to note that the specific features and functionalities available may vary depending on your chosen edition of SolarWinds SEM. Be sure to explore the different license options and compare features to find the one that best fits your needs and budget.
How SolarWinds Security Event Manager works and Architecture?
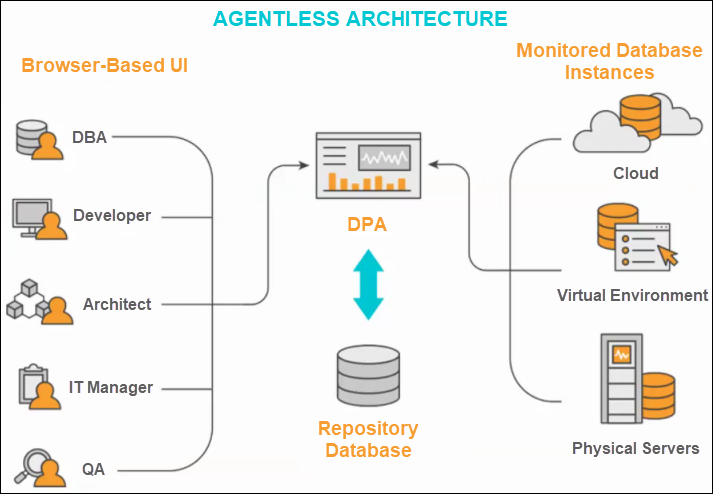
1. Data Collection:
- Agents: Lightweight agents deployed on various devices gather system logs, event data, and security tool output.
- Collectors: Dedicated collector servers receive and aggregate log data from agents and other sources like firewalls, routers, and cloud platforms.
- Normalization: Collected data gets parsed and normalized into a unified format for efficient analysis, regardless of the original format or source.
2. Data Processing and Analysis:
- Correlation Engine: Analyzes correlated data from multiple sources to identify potential threats and suspicious activity.
- Threat Intelligence: Integrates external threat intelligence feeds to enrich analysis and detect emerging threats.
- Rule Engine: Applies pre-defined and custom rules to trigger alerts and prioritize events based on severity and potential impact.
3. User Interface and Functionality:
- Web Console: Provides a centralized interface for event monitoring, investigation, reporting, and configuration.
- Real-time Monitoring: Visualizes incoming events and alerts via dashboards and live feed.
- Search and Filtering: Allows for searching and filtering of events based on specific criteria.
- Investigations and Forensics: Offers tools for deep-dive analysis of security incidents to trace activity and identify root causes.
- Reporting and Compliance: Generates customizable reports for audit purposes and adheres to various security regulations.
4. Architecture:
- Tiered Architecture: Typically deployed in a three-tier architecture with agents, collectors, and the central SEM server.
- Scalability: Can be scaled horizontally by adding additional collectors and vertically by upgrading hardware resources on existing components.
- High Availability: Offers clustering options for redundancy and ensures continuous operation even in case of individual server failures.
5. Key Points to Remember:
- SolarWinds SEM provides a centralized platform for collecting, analyzing, and responding to security events from various sources.
- Its real-time monitoring, threat detection, and incident response capabilities help organizations improve their overall security posture.
- Its architecture offers scalability, flexibility, and high availability to meet the needs of organizations of different sizes and security requirements.
How to Install SolarWinds Security Event Manager it?
Installing SolarWinds Security Event Manager (SEM) involves several steps and configuration options, so it’s best to carefully follow the official documentation based on your chosen deployment methods and licensing options. Following is a general outline of the process:
1. System Requirements:
- Ensure your hardware and software meet the minimum requirements specified in the SolarWinds SEM official website.
- Choose your desired deployment method: Agent-based, Virtual Appliance, or Cloud Deployment.
2. Download and Installation:
- Download the appropriate installer file for your chosen deployment method from the SolarWinds website.
- Achieve the installer and apply the on-screen instructions.
- Configure system settings, including ports, user accounts, and database connections.
3. Licensing:
- Enter your valid SolarWinds SEM license key during the installation process.
- Choose the appropriate license edition based on your desired features and functionality.
4. Agent Deployment (if applicable):
- Download and install agents on each system you want to monitor.
- Configure agent settings to specify data collection options and communication with the SEM server.
5. Initial Configuration:
- Configure the SEM server with policies for log collection, analysis, and alerting.
- Create users and assign appropriate permissions within the SEM web console.
- Set up scheduled scanning routines and notification settings.
6. Verification and Testing:
- Verify successful installation and agent connectivity.
- Run test scans and confirm data collection and analysis functionalities.
- Review alert configurations and ensure proper notifications are triggered.
Note: This is a general overview, and specific instructions may vary depending on your chosen environment and license options.
Basic Tutorials of SolarWinds Security Event Manager: Getting Started

To create the perfect step-by-step basic tutorials for SolarWinds Security Event Manager (SEM), let’s personalize your learning path:
1. Define your desired focus:
- Core functionalities: Learn fundamentals like data collection, log parsing, basic event analysis, and initial reporting.
- Specific features: Deep dive into capabilities like threat detection rules, custom dashboards, compliance mapping, or incident response workflows.
- Administration and configuration: Understand user management, system settings, integration with other tools, and basic customization.
2. Choose your preferred learning format:
- Detailed written guides: Step-by-step instructions with screenshots and explanations.
- Interactive tutorials: Hands-on practice with guided exercises and simulated scenarios.
- Video demonstrations: Visual walkthroughs of tasks narrated by experts.
3. Indicate your skill level:
- Complete Beginner: New to SEM, seeking introductory concepts and basic workflows.
- Intermediate User: Have some experience, aiming to refine skills and explore new features.
- Advanced User: Proficient in SEM, looking for deep dives into advanced functionalities and best practices.
4. Consider your goals:
- Improve threat detection: Focus on building rules and analyzing events to identify potential security incidents.
- Enhance compliance: Learn how to configure SEM for specific compliance requirements and generate reports.
- Optimize operations: Understand how SEM can provide insights into system performance and user behavior.
Once you provide these details, I can curate a series of basic tutorials tailored to your chosen focus, preferred format, skill level, and goals. Remember, SEM offers a powerful platform, so starting with the basics and gradually progressing ensures a smooth and successful learning experience.
Perhaps you’re interested in creating specific rules for malware detection, customizing dashboards for operational monitoring, or configuring log forwarding from devices. The more specific you are, the more personalized and relevant your tutorials will be.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

