What is Sonatype?

Sonatype, previously known for the Nexus platform, is now a broad software supply chain management (SSCM) company with various solutions to secure and optimize your software development process. Here’s a breakdown of Sonatype’s essence and its top 10 use cases:
Sonatype empowers organizations to build secure and compliant software through its comprehensive suite of tools:
- Software Composition Analysis (SCA): Identifies and manages open-source dependencies within your codebase, revealing vulnerabilities and license risks.
- Application Lifecycle Management (ALM): Streamlines and secures your software development process by automating artifact storage, build management, and deployment.
- Container Security: Scans container images for vulnerabilities and misconfigurations, ensuring secure deployments in cloud environments.
- DevSecOps Integration: Bridges the gap between development and security teams, fostering collaboration and shared responsibility for secure software.
- Compliance Management: Helps organizations achieve and maintain compliance with various security and privacy regulations.
Top 10 use cases of Sonatype?
Top 10 Use Cases of Sonatype:
- Proactive Vulnerability Detection: Identify and mitigate vulnerabilities within your code and open-source dependencies before they can be exploited.
- Reduce Open-Source License Risks: Gain complete visibility into open-source dependencies and manage license compliance effectively.
- Automate Security Checks: Integrate security scans throughout your CI/CD pipeline for continuous monitoring and automated vulnerability reporting.
- Improve Software Quality: Secure your software artifacts and build releases with greater confidence, enhancing overall software quality.
- Streamline Software Delivery: Automate build and deployment processes, accelerating your time to market and boosting developer productivity.
- Strengthen DevSecOps Collaboration: Facilitate seamless communication and collaboration between development and security teams, breaking down silos and fostering a culture of shared security responsibility.
- Reduce Security Costs: Proactive vulnerability detection and compliance management can prevent costly security breaches and non-compliance fines.
- Build Trust with Customers: Demonstrating a commitment to software security and compliance builds trust and strengthens your brand reputation.
- Improve Code Review Efficiency: Leverage automated dependency analysis and vulnerability information to focus code reviews on critical issues.
- Enhance Cloud Security: Secure your containerized applications and ensure secure deployments in cloud environments.
Sonatype goes beyond just vulnerability scanning and offers a holistic approach to secure software development. Its user-friendly platform and diverse integration options make it suitable for organizations of all sizes looking to build secure, reliable, and compliant software.
What are the feature of Sonatype?
Sonatype, now encompassing the Nexus platform and various solutions, boasts a powerful feature set for securing and optimizing your software development process. Here’s a closer look at its key offerings:
Software Composition Analysis (SCA):
- Dependency Mapping and Identification: Visualize all open-source dependencies used in your projects, their origin, and version usage.
- Vulnerability Detection: Scans dependencies for known vulnerabilities across various languages and frameworks, prioritizing them based on severity and exploitability.
- License Compliance Management: Identifies licenses associated with each dependency and assesses potential compliance risks, preventing legal issues.
- Dependency Upgrade Recommendations: Suggests compatible and secure dependency upgrades to mitigate vulnerabilities and address license conflicts.
- Policy Enforcement: Define and enforce custom policies for acceptable open-source licenses and library versions within your organization.
Application Lifecycle Management (ALM):
- Artifact Repository Management: Securely store, manage, and distribute software artifacts like binaries, libraries, and container images throughout your development lifecycle.
- Build Automation: Automate build processes, including integration, continuous delivery, and deployments, for faster and more efficient software releases.
- Release Management: Control and streamline software releases with customizable workflows, approvals, and rollbacks.
- Repository Governance: Implement role-based access control and security policies to ensure proper access and management of artifacts.
Container Security:
- Container Image Scanning: Scans container images for vulnerabilities and misconfigurations, safeguarding your cloud deployments.
- Image Signing and Verification: Digitally sign container images to ensure authenticity and integrity throughout the supply chain.
- Compliance Checks: Verify container images adhere to industry standards and organizational security policies.
DevSecOps Integration:
- CI/CD Pipeline Integration: Integrates seamlessly with popular CI/CD pipelines like Jenkins, GitLab, and Azure DevOps for automated security checks and remediation workflows.
- IDE Plugins: Offers plugins for popular IDEs like VS Code and IntelliJ IDEA, providing developers with real-time feedback on dependencies and vulnerabilities.
- API Access: Provides robust APIs for custom integrations with your existing tools and workflows.
Compliance Management:
- Predefined Compliance Profiles: Supports compliance with various regulations like PCI-DSS, HIPAA, and GDPR, simplifying compliance efforts.
- Automated Reporting and Auditing: Generates comprehensive reports on security posture and compliance adherence, facilitating regulatory audits.
- Policy Management: Define and enforce customized security policies aligned with your compliance requirements.
Additional Features:
- Supply Chain Security: Gain visibility and control over software components throughout your supply chain, mitigating risks from compromised dependencies.
- Threat Intelligence: Leverage threat intelligence feeds to stay ahead of emerging security threats and proactively address vulnerabilities.
- Software Bill of Materials (SBOM) Generation: Generate comprehensive SBOMs for improved transparency and security throughout your software ecosystem.
Sonatype goes beyond just static analysis and offers a comprehensive suite of features that address various aspects of software security and development. From managing dependencies and automating builds to ensuring compliance and secure deployments, Sonatype empowers organizations to build secure, reliable, and compliant software with confidence.
How Sonatype works and Architecture?
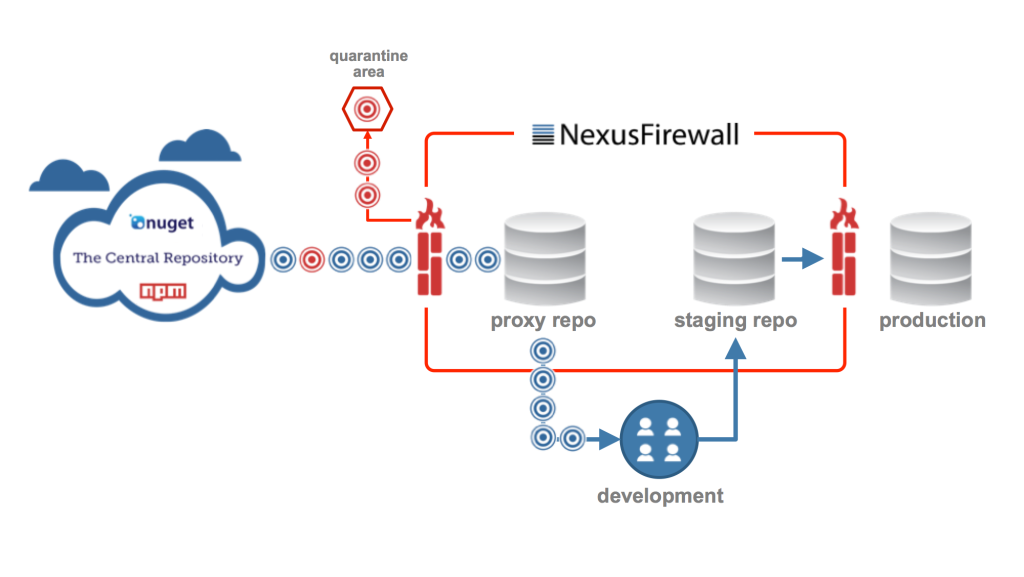
Sonatype, formerly known for the Nexus platform, has evolved into a more comprehensive software supply chain management (SSCM) company. Understanding its architecture and how it works will give you a deeper appreciation for its capabilities.
Sonatype Architecture:
- Frontend: Provides user interface for interacting with repositories, vulnerabilities, policies, and reports.
- API Gateway: Manages API interactions and routes requests to appropriate backend services.
- Scanning Layer: Utilizes various engines for different scan types (SCA, container, artifact):
- SCA Engine: Analyzes dependencies for known vulnerabilities and license compatibility.
- Container Scanner: Scans container images for vulnerabilities and misconfigurations.
- Artifact Scanner: Analyzes software artifacts for specific criteria based on policies.
- Vulnerability Database: Houses a continuously updated database of known vulnerabilities from diverse sources.
- Analysis and Prioritization Engine: Analyzes vulnerabilities based on severity, exploitability, potential impact, and context.
- Remediation Recommendations Engine: Suggests potential solutions for resolving vulnerabilities and license conflicts.
- Policy and Compliance Engine: Ensures adherence to predefined security policies and compliance regulations.
- Repository Manager: Securely stores, distributes, and manages software artifacts like binaries, libraries, and container images.
- Build/Release Management: Streamlines and automates build and release processes for efficient software delivery.
- Reporting and Monitoring System: Generates comprehensive reports and visualizes security posture and compliance adherence for continuous monitoring.
Workflow Overview:
- Integration: Sonatype integrates with your development environment through plugins, SDKs, or APIs.
- Triggering Scans: Scans can be triggered manually, automatically upon code changes, or integrated into CI/CD pipelines.
- Scanning and Analysis: Relevant engine(s) based on scan type analyze target resources (dependencies, container images, artifacts).
- Vulnerability Detection and Analysis: Sonatype identifies vulnerabilities and analyzes them based on severity, exploitability, and context.
- Prioritization and Recommendations: Vulnerabilities are prioritized based on severity and context, and mitigation options like dependency upgrades or configuration changes are proposed.
- Policy and Compliance Checks: Sonatype verifies adherence to defined security policies and compliance regulations, flagging any potential violations.
- Artifact Management: Software artifacts are securely stored, distributed, and versioned within the repository.
- Build/Release Automation: Build and release processes are automated for faster and more consistent software delivery.
- Reporting and Monitoring: Comprehensive reports and dashboards are generated to visualize security posture, compliance adherence, and development progress.
Notes:
- Sonatype leverages machine learning and artificial intelligence to enhance vulnerability detection and prioritization.
- The platform offers advanced features like supply chain security, threat intelligence, and software bill of materials (SBOM) generation.
- Sonatype prioritizes data security and privacy, ensuring your data is encrypted at rest and in transit.
Understanding Sonatype’s architecture and workflow allows you to appreciate its powerful capabilities for securing and optimizing your software development process. It’s not just about vulnerability scanning; it’s about managing software artifacts, automating build/release processes, and ensuring compliance throughout the entire software supply chain.
How to Install Sonatype it?
Here’s a general guide on how to install Nexus Repository Manager and the version of Nexus Repository Manager you are installing.
Prerequisites:
- JDK (Java Development Kit ) installed on your system.
Steps for Installing Nexus Repository Manager:
1. Download Nexus Repository Manager:
- Visit the Sonatype Nexus Repository Manager download page.
- Choose the edition you need (OSS or Pro) and download the appropriate package for your operating system.
2. Extract the Archive (Linux/Mac) or Install (Windows):
- For Linux/Mac:
bash tar -zxvf nexus-x.y.z.tar.gz cd nexus-x.y.z - For Windows, follow the installer wizard.
3. Configure Nexus Repository Manager (Optional):
- (Optional) Open the
nexus-x.y.z/bin/nexus.vmoptionsfile to configure JVM options if needed.
4. Start Nexus Repository Manager:
- For Linux/Mac:
bash ./bin/nexus run - For Windows, execute
nexus.exeor use the service manager.
5. Access Nexus Repository Manager:
- Open your web browser and navigate to http://localhost:8081 (default Nexus URL).
- The first time you access Nexus, you’ll need to complete the setup wizard, which includes creating an admin user and specifying the data directory.
6. Secure Nexus Repository Manager (Optional):
- Follow best practices for securing Nexus Repository Manager.
- Set up HTTPS to encrypt the communication with Nexus.
7. Integrate Nexus with Build Tools (Optional):
- Integrate Nexus with your build tools (Maven, Gradle, etc.) by configuring your project’s build settings to use Nexus as a repository.
8. Configure Proxy Repositories (Optional):
- Set up proxy repositories to cache artifacts from external repositories, improving build performance.
9. Backup and Restore (Optional):
- Implement backup and restore procedures for your Nexus installation.
10. Upgrade Nexus Repository Manager (Optional):
- If you need to upgrade Nexus, follow the upgrade instructions provided by Sonatype.11. Monitor and Maintain:
- Regularly monitor Nexus Repository Manager for performance and health.
- Keep an eye on disk space, log files, and system resources.Basic Tutorials of Sonatype: Getting Started

Sonatype offers various solutions for software supply chain management and security, including Nexus Repository Manager. Here are step-by-step basic tutorials for two common use cases:
1. Setting Up Nexus Repository Manager OSS (Open Source Software):
1.1. Download and Installation:
- Download the appropriate installer for your operating system from Sonatype official website.
- Install Java Runtime Environment (JRE) 8 or later if not already present.
- Run the installer and use the live screen instructions.
1.2. Start and Access Nexus:
- Open a terminal and navigate to the
bindirectory within your Nexus installation folder. - Run
nexus startto start the Nexus service. - Access the Nexus web UI by opening http://localhost:8081 in your browser.
1.3. Create a Repository:
- Login to the Nexus UI using the default username (
admin) and password (admin123). - Navigate to the “Repositories” tab.
- Click “Create repository” and choose the type (e.g., Maven2 repository).
- Configure the repository name, resource URL, and other settings.
- Click “Create” to finalize the repository creation.
1.4. Upload Artifacts:
- Download a sample Maven artifact (e.g., from Maven Central).
- Navigate to the “Repositories” tab and select your repository.
- Click “Upload” and choose the downloaded artifact file.
- Click “Upload” again to upload the artifact to your Nexus repository.
2. Integrating Sonatype Nexus with your CI/CD Pipeline:
2.1. Prerequisites:
- Have a CI/CD platform like Jenkins, GitLab CI, or Bamboo configured.
- Understand basic CI/CD concepts and your platform’s configuration options.
2.2. Install Plugin:
- Install the appropriate Nexus plugin for your CI/CD platform.
- Configure the plugin to connect to your Nexus instance (URL, username, password).
2.3. Define CI/CD Pipeline Steps:
- In your CI/CD pipeline, define steps to:
- Build and package your application.
- Deploy the artifacts to your Nexus repository using the plugin.
- Run security scans and vulnerability checks on uploaded artifacts.
- Approve or reject deployments based on scan results and other criteria.
Bonus Tip: Explore Nexus features beyond artifact hosting, like security policies, access control, and repository group management.
- Buy TikTok Followers: In the Sense of Advertising - May 25, 2024
- Understanding the Key Principles of PhoneTrackers - May 23, 2024
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024

