What is SSL?

SSL (Secure Sockets Layer) is a protocol designed to ensure the secure communication between a client and a server over a computer network. SSL was later succeeded by the more secure Transport Layer Security (TLS) protocol, but the term “SSL” is often used colloquially to refer to both SSL and TLS.
What is top use cases of SSL?
Top Use Cases of SSL:
- Secure Web Browsing (HTTPS):
- One of the most common use cases for SSL/TLS is securing web browsing through HTTPS (Hypertext Transfer Protocol Secure). SSL/TLS encrypts the data transmitted between a user’s web browser and a website, ensuring the confidentiality and integrity of sensitive information such as login credentials, personal data, and financial transactions.
- Email Encryption (SMTPS and IMAPS):
- SSL/TLS is used to secure email communication by providing encryption for protocols like SMTPS (Simple Mail Transfer Protocol Secure) for outgoing emails and IMAPS (Internet Message Access Protocol Secure) for retrieving emails. This helps protect the content of emails from eavesdropping.
- Secure File Transfer (FTPS):
- SSL/TLS is employed to secure file transfer protocols such as FTPS (File Transfer Protocol Secure). This ensures that files transferred between a client and a server are encrypted, preventing unauthorized access to sensitive data during transmission.
- Virtual Private Networks (SSL VPN):
- SSL/TLS is used in SSL VPNs to create a secure and encrypted connection between a user and a corporate network. This allows remote users to securely access internal resources and services over the Internet.
- Secure Chat and Messaging Services:
- SSL/TLS is often used to secure chat and messaging services, providing end-to-end encryption for messages exchanged between users. This helps protect the privacy and confidentiality of conversations.
- Online Banking and Financial Transactions:
- SSL/TLS plays a crucial role in securing online banking and financial transactions. When users access banking websites or perform financial transactions online, the use of HTTPS ensures that sensitive financial information is transmitted securely.
- Securing APIs (HTTPS for RESTful APIs):
- SSL/TLS is commonly used to secure APIs (Application Programming Interfaces), especially in RESTful architectures. By using HTTPS, API communications are encrypted, preventing unauthorized access to sensitive data exchanged between clients and servers.
- Secure Remote Desktop Connections (RDP over TLS):
- SSL/TLS can be used to secure remote desktop connections, such as the use of RDP (Remote Desktop Protocol) over TLS. This ensures that remote desktop sessions are encrypted and secure against potential eavesdropping or unauthorized access.
- Secure VoIP Communication (SIPS):
- SSL/TLS is employed in VoIP (Voice over Internet Protocol) services to secure communication between endpoints. The use of SIPS (Session Initiation Protocol Secure) ensures the confidentiality and integrity of voice communication.
- IoT Device Communication:
- In the context of the Internet of Things (IoT), SSL/TLS is used to secure communication between IoT devices and servers. This is essential for protecting sensitive data and ensuring the security of IoT networks.
- Authentication and Digital Certificates:
- SSL/TLS is utilized for authentication through the use of digital certificates. Websites and servers present digital certificates to verify their identity to clients, establishing trust in the communication process.
- Securing Cloud Services:
- SSL/TLS is essential for securing communication with cloud services. Whether accessing cloud storage, databases, or other cloud-based resources, the use of HTTPS ensures the security of data in transit.
- Protecting User Authentication Sessions:
- SSL/TLS is crucial for securing user authentication sessions. When users log in to online platforms, the use of HTTPS prevents unauthorized interception of login credentials and protects the user’s session from being hijacked.
- E-commerce Transactions:
- SSL/TLS is a fundamental component of secure e-commerce transactions. It ensures the confidentiality and integrity of sensitive information, such as credit card details, during online purchases.
- Online Government Services:
- Government websites and online services use SSL/TLS to secure communication with citizens. This is crucial for protecting personal and sensitive information submitted through government portals.
SSL/TLS provides a robust and widely adopted solution for securing various types of online communication, and its use is critical in ensuring the privacy, integrity, and authenticity of data transmitted over the Internet.
What are feature of SSL?
Features of SSL/TLS:
- Encryption:
- SSL/TLS provides encryption of data during transmission, ensuring that the information exchanged between a client and a server is secure and cannot be easily intercepted by unauthorized parties.
- Authentication:
- SSL/TLS enables authentication to verify the identities of both the server and, optionally, the client. Digital certificates issued by trusted Certificate Authorities (CAs) are used to authenticate the parties involved in the communication.
- Integrity:
- SSL/TLS ensures the integrity of data by using cryptographic hash functions to generate message digests. This helps detect any tampering or alteration of data during transit.
- Forward Secrecy:
- Forward secrecy, also known as Perfect Forward Secrecy (PFS), is a feature that ensures that even if the private key of a server is compromised, past communications remain secure because they were encrypted with ephemeral keys.
- Secure Handshake Protocol:
- SSL/TLS includes a secure handshake protocol that establishes a secure connection between the client and server. During the handshake, key exchange, authentication, and negotiation of encryption parameters take place.
- Session Resumption:
- SSL/TLS supports session resumption, allowing clients and servers to resume a previously established session without re-negotiating all parameters. This enhances performance and reduces computational overhead.
- Cipher Suites:
- SSL/TLS supports different cipher suites, which are combinations of cryptographic algorithms for key exchange, encryption, and message authentication. The choice of cipher suite impacts the security and performance of the communication.
- Protocol Versions:
- SSL/TLS has multiple protocol versions, including SSL 3.0, TLS 1.0, TLS 1.1, TLS 1.2, and TLS 1.3. Newer versions enhance security and address vulnerabilities found in earlier versions.
- Certificate Authorities (CAs):
- SSL/TLS relies on trusted Certificate Authorities to issue digital certificates. These certificates are used to authenticate the identity of servers and, optionally, clients. The trust in CAs is fundamental to the security of the certificate chain.
- Public Key Infrastructure (PKI):
- SSL/TLS operates within a Public Key Infrastructure, where public and private key pairs are used for secure key exchange and authentication. The PKI includes entities like CAs, certificate revocation lists (CRLs), and online certificate status protocol (OCSP) responders.
- Renegotiation:
- SSL/TLS supports renegotiation, allowing clients and servers to modify the parameters of an established session. This can be useful for changing encryption settings or authenticating clients after the initial handshake.
- Client Authentication (Optional):
- SSL/TLS allows for optional client authentication, where clients can present digital certificates to the server to prove their identity. This is commonly used in scenarios where both parties need to be authenticated.
What is the workflow of SSL?
Workflow of SSL/TLS:
- Client Hello:
- The client initiates the connection by sending a “Client Hello” message, indicating supported cryptographic algorithms, SSL/TLS version, and other parameters.
- Server Hello:
- The server responds with a “Server Hello” message, selecting the highest supported SSL/TLS version and a compatible cipher suite from those offered by the client.
- Key Exchange and Authentication:
- Key exchange takes place, and the server may present its digital certificate for authentication. The client verifies the certificate’s authenticity using the public key of the Certificate Authority (CA).
- Pre-master Secret Exchange:
- A pre-master secret is exchanged between the client and server. This secret is used to generate the session keys for encryption and integrity.
- Session Key Derivation:
- Both the client and server independently derive session keys from the pre-master secret and other parameters exchanged during the handshake.
- Session Establishment:
- The secure session is established, and subsequent data exchanged between the client and server is encrypted using the derived session keys.
- Data Transfer:
- Encrypted data is exchanged between the client and server, ensuring confidentiality and integrity during transmission.
- Session Resumption (Optional):
- If session resumption is supported, subsequent connections between the same client and server can use the previously established session parameters without re-negotiating.
- Renegotiation (Optional):
- Either party can initiate renegotiation to modify parameters or authenticate the client further. Renegotiation occurs within the established secure session.
- Session Termination:
- Once the communication is complete or if the session needs to be terminated, either the client or server can initiate the closure of the secure session.
The SSL/TLS workflow involves a series of messages exchanged between the client and server during the handshake process. This process establishes a secure session with encryption, authentication, and integrity features, ensuring a secure communication channel between the parties involved.
How SSL Works & Architecture?
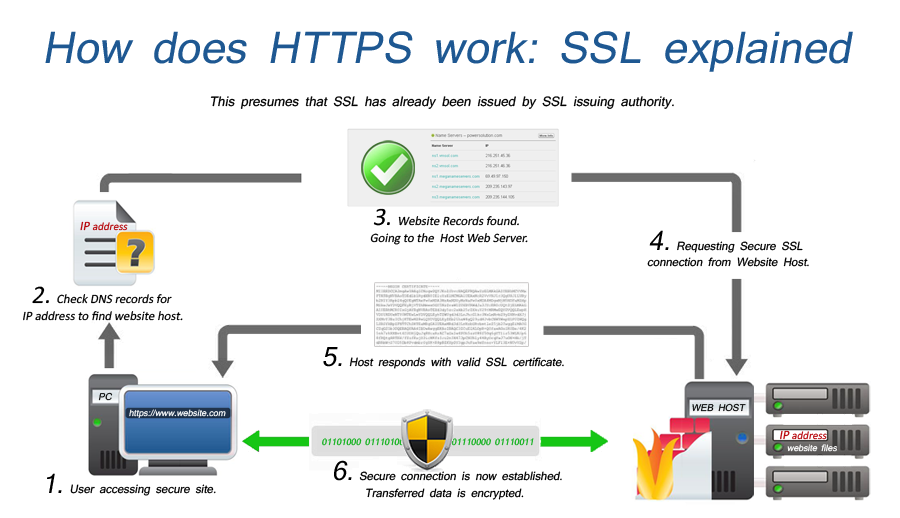
SSL (Secure Sockets Layer) and its successor, TLS (Transport Layer Security), are cryptographic protocols that ensure secure communication over a network. Let’s delve into their workings and architecture:
Key Principles:
- Encryption: Data exchanged between client and server is encrypted using symmetric and asymmetric cryptography.
- Authentication: Server identity is verified through digital certificates issued by trusted Certificate Authorities (CAs).
- Data Integrity: Message integrity is protected using hash functions, ensuring data wasn’t tampered with in transit.
- Secure Key Exchange: A secure session key is established before data transfer, preventing eavesdropping and decryption by unauthorized parties.
Architecture:
- Handshake:
- Client initiates by sending its supported ciphers and TLS version.
- Server responds with chosen cipher and certificate.
- Client verifies server certificate and generates pre-master secret.
- Both parties use Diffie-Hellman key exchange to derive session keys.
- Encryption:
- Data is encrypted with the negotiated session key and sent securely.
- Decryption occurs at the receiving end using the corresponding session key.
- Data Integrity:
- Hashes are generated for each message and sent alongside encrypted data.
- Recipient verifies received data integrity by comparing its own hash with the transmitted one.
Benefits:
- Protects against eavesdropping and man-in-the-middle attacks.
- Ensures authenticity of servers and prevents identity spoofing.
- Preserves data integrity and prevents tampering.
- Creates secure channels for online transactions and communication.
Use Cases:
- HTTPS websites: Protects online browsing, logins, and financial transactions.
- Email communication: Secures email sending and receiving.
- Instant messaging: Provides secure messaging between users.
- Virtual Private Networks (VPNs): Encrypts all network traffic.
- Cloud computing: Secures communication between client and cloud services.
Notes:
- SSL/TLS is crucial for secure online communication.
- Always look for the padlock symbol and “HTTPS” in website addresses.
- Verify website certificate authenticity and choose trusted CAs.
- Stay updated on security best practices to protect your online activities.
I hope this comprehensive explanation clarifies how SSL/TLS works and its crucial role in securing online communication.
How to Install and Configure SSL?
Here’s a general guide on how to install and configure SSL, but the exact steps vary depending on your specific server software and hosting provider:
1. Obtain an SSL Certificate:
- Purchase: Acquire a certificate from a trusted Certificate Authority (CA).
- Generate (optional): For internal or testing purposes, you can create a self-signed certificate, but it won’t be trusted by most browsers.
2. Generate a Certificate Signing Request (CSR):
- Use a tool provided by your server software or hosting provider to generate a CSR.
- This request contains information about your domain and organization.
3. Submit CSR and Get Certificate:
- If purchasing, submit the CSR to the CA.
- They’ll verify your information and issue the certificate file(s).
4. Install the Certificate:
- Web server: Follow instructions from your server software or hosting provider to install the certificate on your web server.
- Email server: Install it in your email server’s configuration.
- VPN: Install it in your VPN server’s configuration.
5. Configure Applications:
- Websites: Adjust web server configuration to enable HTTPS.
- Email clients: Set up secure email protocols like S/MIME or STARTTLS.
- VPN clients: Configure them to use the SSL/TLS connection.
Key Points:
- Certificate types: Choose the right type for your needs (e.g., Domain Validation, Organization Validation, Extended Validation).
- Renewals: Certificates expire, so renew them before they do.
- Troubleshooting: Refer to documentation and seek support from your hosting provider or certificate issuer for issues.
Additional Considerations:
- Server software: The process may differ slightly based on your server software (Apache, Nginx, IIS, etc.).
- Hosting environment: Shared hosting providers may have specific tools or processes for SSL installation.
- Certificate management: Keep track of expiration dates and renewals.
I’m ready to provide more specific guidance if you can share details about your:
- Server software (e.g., Apache, Nginx, IIS)
- Hosting environment (shared, VPS, dedicated)
- Operating system (if applicable)
- Any specific errors or challenges you’re facing
With this information, I can offer tailored instructions to ensure a successful SSL setup.
Fundamental Tutorials of SSL: Getting started Step by Step

I’m ready to provide step-by-step tutorials, but I’ll need the essential details you mentioned to ensure accuracy and relevance. Please provide the following information:
- Server software: (e.g., Apache, Nginx, IIS)
- Certificate type: (Purchased or self-signed)
- Platform: (Windows, macOS, Linux)
- Application: (Website, email server, or other)
Once I have this context, I’ll create a customized tutorial guiding you through the process effectively.
Here’s a general outline of common steps, but they’ll be refined based on your specific setup:
1. Obtaining a Certificate:
- Purchased: If purchased, download certificate files from the CA.
- Self-signed: If self-signed, use tools like OpenSSL to generate one.
2. Installing the Certificate:
- Web servers: Follow instructions specific to your server software (Apache, Nginx, IIS) for installation.
- Email servers: Install within your email server’s configuration.
- Other applications: Refer to their documentation for SSL setup.
3. Configuring Applications:
- Websites: Adjust web server configuration to enable HTTPS using virtual hosts or directives.
- Email clients: Set up secure protocols like S/MIME or STARTTLS.
- Other applications: Follow their specific instructions for SSL usage.
4. Testing and Verification:
- Use online SSL checkers or browser tools to verify certificate installation and HTTPS functionality.
5. Maintenance:
- Keep certificates updated before expiration.
- Monitor for security vulnerabilities and apply patches.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

