What is Sysdig?

Sysdig is a container and cloud-native security platform that provides monitoring, security, and compliance solutions for containerized and cloud-native applications. It offers a range of features to ensure the performance, security, and reliability of modern cloud environments.
Sysdig is a versatile platform that addresses the monitoring, security, and compliance needs of containerized and cloud-native environments. It helps organizations ensure the performance, security, and reliability of their applications while maintaining compliance with regulatory requirements and industry standards.
Top 10 use cases of Sysdig:
Here are the top 10 use cases of Sysdig:
- Container and Microservices Monitoring: Sysdig provides real-time monitoring and visibility into containerized applications, microservices, and orchestration platforms like Kubernetes, allowing organizations to troubleshoot issues and optimize performance.
- Security Monitoring: It offers security monitoring and threat detection for container environments, helping organizations detect and respond to security incidents, malware, and vulnerabilities.
- Compliance and Audit Trail: Sysdig assists organizations in maintaining compliance with industry standards and regulations by providing audit trails, compliance checks, and reporting capabilities.
- Incident Response: In the event of security incidents or operational issues, Sysdig enables incident response by providing detailed insights into container activities and events.
- Vulnerability Management: Sysdig scans container images and running containers for vulnerabilities, offering recommendations for remediation and vulnerability prioritization.
- Container Forensics: It provides forensics capabilities to investigate incidents, identify root causes, and trace the activity of containers and processes.
- CI/CD Pipeline Integration: Sysdig integrates with CI/CD pipelines to ensure that container images meet security and compliance requirements before deployment.
- Threat Detection: Sysdig detects and alerts on suspicious activities, anomalies, and threats in real-time, helping organizations prevent security breaches.
- Network Visibility: Sysdig offers deep network visibility into container communications, allowing organizations to monitor and control network traffic and segment containers.
- Application Performance Monitoring (APM): Sysdig provides APM capabilities to monitor application performance, trace requests, and diagnose performance bottlenecks in containerized applications.
- Log Analysis: Organizations can analyze logs from containerized applications and infrastructure to gain insights into system behavior and troubleshoot issues.
- Capacity Planning: Sysdig assists with capacity planning by providing insights into resource utilization, allowing organizations to optimize infrastructure and control costs.
- Forensic Analysis: It offers comprehensive forensic analysis capabilities to investigate security incidents and performance problems, including the ability to trace system calls and activities.
- Dynamic Threat Intelligence: Sysdig leverages dynamic threat intelligence feeds to identify and block known malicious IPs and domains, enhancing security.
What are the feature of Sysdig?
Sysdig is a container and cloud-native security and monitoring platform that offers a comprehensive set of features to monitor, secure, and troubleshoot containerized and cloud-native applications. Below are the key features of Sysdig, along with an overview of how it works and its architecture:
Key Features of Sysdig:
- Container Monitoring: Sysdig provides real-time monitoring and visibility into containerized applications, microservices, and orchestration platforms like Kubernetes. It collects performance and behavioral data from containers and hosts.
- Security Monitoring: It offers security monitoring and threat detection for container environments, helping organizations detect and respond to security incidents, malware, and vulnerabilities.
- Compliance and Audit Trails: Sysdig assists organizations in maintaining compliance with industry standards and regulations by providing audit trails, compliance checks, and reporting capabilities.
- Incident Response: Sysdig enables incident response by providing detailed insights into container activities and events, making it easier to investigate and mitigate incidents.
- Vulnerability Management: Sysdig scans container images and running containers for vulnerabilities, offering recommendations for remediation and vulnerability prioritization.
- Container Forensics: It provides forensics capabilities to investigate incidents, identify root causes, and trace the activity of containers and processes.
- CI/CD Pipeline Integration: Sysdig integrates with CI/CD pipelines to ensure that container images meet security and compliance requirements before deployment.
- Threat Detection: Sysdig detects and alerts on suspicious activities, anomalies, and threats in real-time, helping organizations prevent security breaches.
- Network Visibility: Sysdig offers deep network visibility into container communications, allowing organizations to monitor and control network traffic and segment containers.
- Application Performance Monitoring (APM): Sysdig provides APM capabilities to monitor application performance, trace requests, and diagnose performance bottlenecks in containerized applications.
How Sysdig works and Architecture?
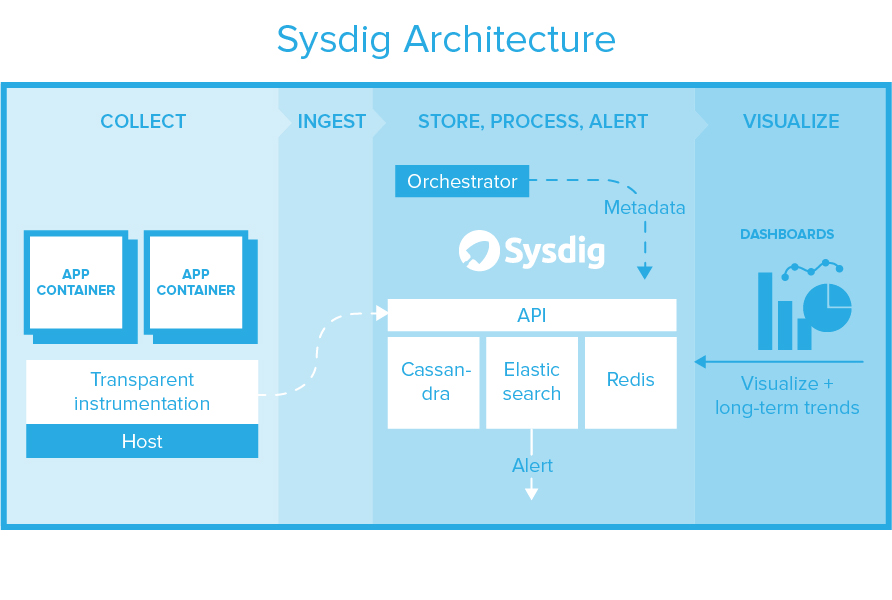
- Data Collection: Sysdig agents are deployed on container hosts and nodes in the environment. These agents collect performance metrics, events, and security-related data from containers, hosts, and orchestration platforms.
- Data Analysis and Storage: The collected data is sent to the Sysdig back end, where it is processed, analyzed, and stored. Sysdig’s analytics engine correlates data to provide insights into container and application behavior.
- Monitoring and Alerting: Sysdig offers real-time monitoring and alerting capabilities, allowing organizations to set up alerts based on predefined conditions or custom criteria.
- Security Scanning: Sysdig scans container images and running containers for vulnerabilities, misconfigurations, and security issues. It provides detailed reports and recommendations for remediation.
- Compliance and Audit: Sysdig helps organizations maintain compliance by providing audit trails and compliance checks, enabling organizations to demonstrate adherence to regulatory requirements.
- Incident Response: In the event of a security incident or operational issue, Sysdig provides the necessary data and insights to investigate, diagnose, and respond effectively.
Sysdig’s architecture consists of several components working together to provide monitoring, security, and compliance capabilities:
- Sysdig Agents: Agents are lightweight components deployed on container hosts and nodes. They collect data on system calls, performance metrics, network traffic, and security events from containers and host operating systems.
- Sysdig Back End: The back end receives and processes data from agents, running analytics, and storing data for querying and analysis.
- Alerting Engine: Sysdig’s alerting engine allows organizations to configure alerts based on predefined conditions or custom criteria. Alerts can be sent to various notification channels.
- User Interface: Sysdig provides a web-based user interface that allows users to visualize monitoring data, review security findings, configure policies, and manage alerts.
- Integration Points: Sysdig integrates with container orchestration platforms like Kubernetes and container registries. It also offers integrations with other security tools and SIEM systems.
- Data Storage: Sysdig stores collected data in a scalable storage layer, making it accessible for historical analysis and reporting.
Sysdig’s architecture is designed to provide end-to-end container monitoring and security capabilities, enabling organizations to ensure the performance, security, and compliance of their containerized and cloud-native applications. The platform offers flexibility, scalability, and a unified view of containerized environments, making it a valuable tool for modern cloud-native deployments.
How to Install Sysdig?
To install Sysdig, you can use one of the following methods:
Using the Sysdig agent package:
- Download the Sysdig agent package for your operating system from the Sysdig website.
- Install the Sysdig agent package.
- Restart your system.
Using the Sysdig Helm chart:
- Add the Sysdig Helm repository:
helm repo add sysdig https://helm.sysdig.com- Update the Helm repository index:
helm repo update- Install the Sysdig Helm chart:
helm install sysdig sysdig/sysdig --namespace sysdigUsing the Sysdig Docker image:
- Pull the Sysdig Docker image:
docker pull sysdig/sysdig- Run the Sysdig Docker image:
docker run -d --name sysdig -p 8080:8080 sysdig/sysdigOnce Sysdig is installed, you can access the Sysdig Monitor UI at the following URL:
http://localhost:8080Additional tips:
- You can install Sysdig on-premises or in the cloud.
- Sysdig supports a variety of operating systems and cloud platforms.
- You can integrate Sysdig with your CI/CD pipeline to automate security checks.
- Sysdig provides a variety of features to help you monitor and troubleshoot your containerized applications, such as:
- Container monitoring: Sysdig monitors your running containers for performance, security, and compliance.
- Container troubleshooting: Sysdig helps you troubleshoot container problems quickly and efficiently.
- Container security: Sysdig helps you secure your containerized applications from cyber threats.
Basic Tutorials of Sysdig: Getting Started

The following steps are the basic tutorial of Sysdig:
1. Install Sysdig:
Follow the instructions in my previous response to install Sysdig.
2. Access the Sysdig Monitor UI:
Once Sysdig is installed, you can access the Sysdig Monitor UI at the following URL:
http://localhost:8080
3. Create a dashboard:
A dashboard is a customizable view of your containerized applications. You can add different widgets to your dashboard to track the performance, security, and compliance of your applications.
To create a dashboard:
- Click Dashboards in the left-hand menu.
- Click Create Dashboard.
- Give your dashboard a name and click Create.
- Add widgets to your dashboard by dragging and dropping them from the widget library.
- Configure the widgets to display the data that you want to see.
4. View the health of your applications:
The Sysdig Monitor UI provides a variety of views that you can use to view the health of your containerized applications.
To view the health of your applications:
- Click Containers in the left-hand menu.
- Click the name of the container that you want to view.
- View the different metrics and graphs to assess the health of your container.
5. Troubleshoot container problems:
Sysdig Monitor provides a variety of tools to help you troubleshoot container problems.
To troubleshoot container problems:
- Click Troubleshooting in the left-hand menu.
- Select the type of problem that you want to troubleshoot.
- Use the tools provided by Sysdig Monitor to troubleshoot the problem.
6. Secure your containerized applications:
Sysdig Monitor provides a variety of features to help you secure your containerized applications.
To secure your containerized applications:
- Click Security in the left-hand menu.
- View the different security metrics and graphs to assess the security posture of your applications.
- Use the tools provided by Sysdig Monitor to remediate any security vulnerabilities.
Additional tips:
- You can integrate Sysdig Monitor with your CI/CD pipeline to automate security checks and troubleshooting.
- Sysdig Monitor provides a variety of other features, such as compliance reporting and incident response.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

