What is ThreatConnect?

ThreatConnect is a popular threat intelligence platform that offers a wide range of capabilities to help organizations gather, analyze, and act upon threat intelligence data effectively. It assists security teams in understanding and responding to cyber threats, vulnerabilities, and incidents.
ThreatConnect’s flexibility and extensive capabilities make it a valuable tool for security teams aiming to improve their overall cybersecurity posture and respond effectively to cyber threats and incidents. The platform’s features may evolve over time to address emerging threats and challenges in the cybersecurity landscape.
Top 10 use cases of ThreatConnect:
Here are the top 10 use cases of ThreatConnect:
- Threat Intelligence Gathering: ThreatConnect collects, aggregates, and normalizes threat intelligence data from various sources, including open-source feeds, commercial providers, and internal sources, to provide a comprehensive view of the threat landscape.
- Incident Response: It assists organizations in responding to security incidents by providing contextual information about threats, indicators of compromise (IOCs), and suggested response actions. This accelerates incident investigation and resolution.
- Vulnerability Management: ThreatConnect integrates threat intelligence into vulnerability management processes, helping organizations identify and prioritize vulnerabilities that are actively being exploited or targeted by threat actors.
- Threat Detection and Analysis: Security teams can use ThreatConnect to detect and analyze threats by correlating incoming threat intelligence data with their network and endpoint data. It helps in identifying potential threats early.
- Phishing Detection and Mitigation: The platform aids in the detection and mitigation of phishing attacks by identifying phishing-related indicators and providing real-time alerts about phishing campaigns.
- Threat Hunting: Security teams can proactively hunt for threats within their network by leveraging threat intelligence data to search for anomalous or suspicious activity.
- Security Orchestration and Automation: ThreatConnect supports security orchestration and automation efforts by providing tools for automating security workflows and response actions based on threat intelligence.
- Dark Web Monitoring: It monitors activity on the dark web and underground forums to identify emerging threats and cybercriminal activity.
- Compliance and Reporting: ThreatConnect offers compliance management features by providing reports and documentation needed for compliance audits, such as PCI DSS, HIPAA, and GDPR.
- Custom Threat Feeds: Organizations can create custom threat intelligence feeds tailored to their specific needs and infrastructure. ThreatConnect allows users to manage and share these custom feeds.
What are the feature of ThreatConnect?
ThreatConnect is a comprehensive threat intelligence platform with a wide range of features designed to help organizations gather, analyze, and act upon threat intelligence effectively. While the specifics may evolve over time with updates and new versions, here are some of the key features typically associated with ThreatConnect:
Key Features of ThreatConnect:
- Threat Intelligence Aggregation: ThreatConnect collects and aggregates threat intelligence data from various sources, including open-source feeds, commercial providers, and internal sources.
- Normalization and Enrichment: The platform normalizes and enriches threat intelligence data, ensuring consistency and adding contextual information to provide deeper insights.
- Incident Response Support: ThreatConnect offers support for incident response efforts by providing contextual information about threats, indicators of compromise (IOCs), and suggested response actions. It helps accelerate incident investigation and resolution.
- Vulnerability Management Integration: ThreatConnect integrates threat intelligence into vulnerability management processes, helping organizations identify and prioritize vulnerabilities actively being exploited or targeted by threat actors.
- Real-time Threat Detection and Analysis: Security teams can use ThreatConnect to detect and analyze threats by correlating incoming threat intelligence data with their network and endpoint data. It helps in identifying and responding to potential threats quickly.
- Phishing Detection and Mitigation: The platform aids in the detection and mitigation of phishing attacks by identifying phishing-related indicators and providing real-time alerts about phishing campaigns.
- Threat Hunting: Security teams can proactively hunt for threats within their network by leveraging threat intelligence data to search for anomalous or suspicious activity.
- Security Orchestration and Automation: ThreatConnect supports security orchestration and automation efforts by providing tools for automating security workflows and response actions based on threat intelligence.
- Custom Threat Feeds: Organizations can create custom threat intelligence feeds tailored to their specific needs and infrastructure. ThreatConnect allows users to manage and share these custom feeds.
- Dark Web Monitoring: It monitors activity on the dark web and underground forums to identify emerging threats and cybercriminal activity.
- Collaboration and Information Sharing: ThreatConnect facilitates collaboration among security teams and enables information sharing with trusted partners and industry peers.
How ThreatConnect works and Architecture?
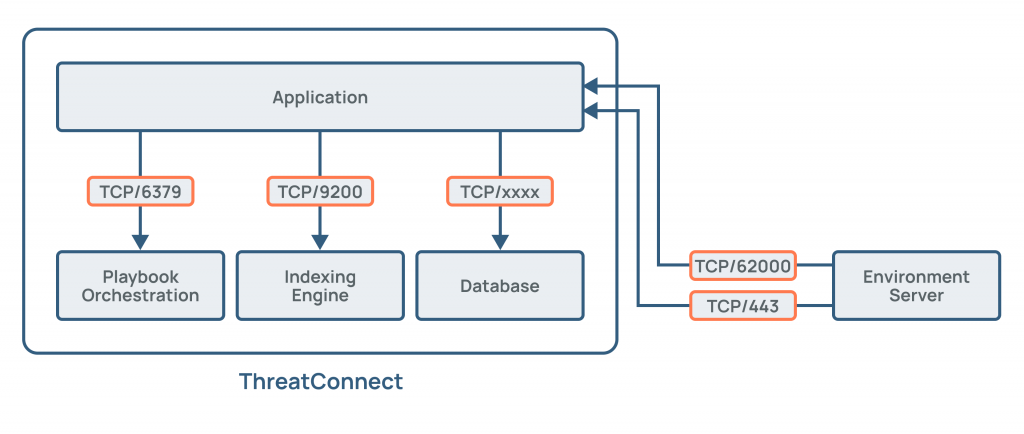
ThreatConnect’s architecture and functionality can be summarized in the following steps:
- Data Collection: ThreatConnect collects threat intelligence data from various sources, including open-source feeds, commercial providers, and internal sources.
- Normalization and Enrichment: The collected data is normalized to ensure consistency and enriched with contextual information, such as threat actor profiles, tactics, techniques, and procedures (TTPs), and associated indicators.
- Data Storage and Management: Threat intelligence data is stored in a centralized repository that is accessible for analysis. The platform allows users to manage and organize threat intelligence feeds and data.
- Correlation and Analysis: ThreatConnect employs analytics and correlation capabilities to identify patterns, trends, and correlations within the data. It helps in identifying potential threats and vulnerabilities.
- Alerting and Reporting: The platform generates alerts and notifications based on predefined criteria or custom configurations. It also offers reporting and visualization capabilities to help organizations understand and communicate threat insights effectively.
- Integration: ThreatConnect can be integrated with other security solutions, such as SIEM, SOAR, and endpoint security tools, to enhance threat detection and response capabilities with threat intelligence.
- Customization: Organizations can customize and tailor ThreatConnect to meet their specific needs, including the creation of custom threat feeds and workflows.
- Collaboration: ThreatConnect fosters collaboration and information sharing among security teams, helping them work together to defend against cyber threats effectively.
ThreatConnect’s architecture is designed to facilitate the collection, analysis, and dissemination of threat intelligence data, enabling organizations to make informed decisions and enhance their cybersecurity defenses. The platform’s features and capabilities may evolve to address emerging threats and challenges in the cybersecurity landscape.
How to Install ThreatConnect?
To install ThreatConnect, you will need a Python 2.7+ environment. You can install Python using your operating system’s package manager, or by downloading the Python installer from the Python website.
Once you have installed Python, you can install ThreatConnect using the following steps:
- Open a terminal window.
- Navigate to the directory where you want to install ThreatConnect.
- Run the following command:
pip install threatconnectThis will install the ThreatConnect Python SDK.
Once the ThreatConnect SDK is installed, you can start using it to develop ThreatConnect apps and integrations. For more information, please see the ThreatConnect documentation: https://docs.threatconnect.com/
Some additional tips for installing ThreatConnect:
- If you are using a version of Python older than 2.7, you will need to install the
enum34package using the following command:
pip install enum34- If you are using a proxy server, you will need to set the
HTTP_PROXYandHTTPS_PROXYenvironment variables before installing ThreatConnect. - If you are installing ThreatConnect on a Windows system, you may need to run the
pipcommand with elevated privileges. To do this, open a command prompt window as an administrator and then run thepip install threatconnectcommand.
Once you have installed ThreatConnect, you can start using it to improve your security posture by helping you to identify, assess, and mitigate threats to your organization.
Basic Tutorials of ThreatConnect: Getting Started

The following are the Step-by-Step Basic Tutorials of ThreatConnect:
- Getting Started
- Create a ThreatConnect account.
- Log in to the ThreatConnect web UI.
- Review the Getting Started documentation.
- Building Playbooks
- Identify the security tasks that you want to automate.
- Develop ThreatConnect playbooks to automate your security tasks.
- Use the ThreatConnect playbook editor to create and edit playbooks.
- Test your playbooks to ensure that they are working as expected.
- Deploying Playbooks
- Deploy your playbooks to your ThreatConnect environment.
- Schedule your playbooks to run on a regular basis.
- Trigger your playbooks manually when needed.
- Monitoring Playbooks
- Monitor the execution of your playbooks to ensure that they are running as expected.
- Review the playbooks’ outputs to identify any security threats or incidents.
- Take action to mitigate any security threats or incidents that are identified by your playbooks.
- Improving Playbooks
- Regularly review your playbooks to identify areas for improvement.
- Update your playbooks to reflect new security threats and incidents.
- Share your playbooks with other ThreatConnect users to improve the security community.
Some additional tips for using ThreatConnect:
- Use the ThreatConnect community to get help and support from other ThreatConnect users.
- Take advantage of ThreatConnect’s training resources to learn more about the platform and how to use it effectively.
- Contact ThreatConnect support if you have any questions or problems.
ThreatConnect is a powerful SOAR platform that can help you to improve your security posture by helping you to automate your security operations and respond to threats more quickly and effectively. By following the steps above, you can learn how to use ThreatConnect to build, deploy, monitor, and improve playbooks to automate your security operations and improve your security posture.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

