What is ToxiProxy?

ToxiProxy is an open-source tool that acts as a TCP proxy server. Its primary purpose is to simulate various network conditions and failures during testing and development. This allows you to test the resilience and behavior of your applications under controlled, realistic scenarios.
Think of it like a stress test for your network connections! ToxiProxy injects controlled faults like latency, packet loss, bandwidth limitations, and even connection drops to mimic real-world network challenges. By observing how your application reacts to these simulated issues, you can:
- Identify single points of failure: Find critical dependencies on specific network aspects.
- Validate error handling: Test how your application handles network errors and recovers.
- Improve fault tolerance: Build applications that can gracefully handle disruptions and maintain functionality.
- Boost confidence in production: Minimize the risk of outages due to unexpected network issues.
Top 10 use cases of ToxiProxy?
Top 10 Use Cases of ToxiProxy:
- Testing Microservices: Inject network faults between microservices to assess their isolation and impact on the overall system.
- Simulating Network Outages: Introduce controlled disconnections to test failover mechanisms and disaster recovery plans.
- Stress Testing Cloud Applications: Simulate resource constraints and network limitations in cloud environments to optimize performance and resilience.
- Validating API Resilience: Inject faults in API calls to test their responsiveness and error handling under network stress.
- Testing Mobile Apps: Emulate unreliable mobile network conditions (latency, packet loss) to improve app behavior and user experience.
- Chaos Engineering Experiments: Integrate ToxiProxy into chaos engineering experiments to proactively discover and address system vulnerabilities.
- Developing Network-Aware Applications: Build applications that adapt their behavior based on network conditions using ToxiProxy insights.
- Performance Benchmarking: Compare application performance under different network scenarios to identify bottlenecks and optimize communication.
- Training Developers and Testers: Use ToxiProxy to educate teams about real-world network challenges and improve testing practices.
- Continuous Integration/Continuous Delivery (CI/CD): Integrate ToxiProxy into CI/CD pipelines to perform automated resilience testing at each stage of development.
By proactively injecting network faults with ToxiProxy, you can build applications that are robust, adaptable, and better prepared for the unpredictable nature of real-world networks.
Alwyas keep in mind, ToxiProxy is just one tool in a broader strategy for testing and improving system resilience. It’s crucial to have well-defined objectives and metrics for your tests to gain meaningful insights and drive continuous improvement.
What are the feature of ToxiProxy?
ToxiProxy boasts a rich feature set designed to inject controlled chaos into your system and test its behavior under various stress conditions. Here’s a breakdown of some key functionalities:
Chaos Injection:
- Network: Simulate latency, jitter, packet loss, bandwidth throttling, and even complete disconnections to test your system’s network resilience.
- Latency: Introduce specific delays on requests and responses to analyze your system’s performance under increased latency.
- Errors: Inject HTTP errors like timeouts, connection resets, and specific status codes to test error handling mechanisms.
- Transformation: Modify request and response body content, headers, and even protocol to analyze your system’s adaptability to unexpected data.
- Replay: Record real-world traffic and replay it with custom modifications to test specific scenarios.
Target Control:
- Granular Targeting: Inject chaos towards specific applications, paths, protocols, or even individual requests for precise testing.
- Whitelisting and Blacklisting: Exclude specific requests or resources from chaos injections to isolate testing areas.
- Routing Control: Redirect traffic to different backends or simulate service outages for deeper analysis.
Observability and Analysis:
- Real-time Statistics: Monitor injected chaos patterns, affected requests, and overall system behavior in real-time.
- Logging and Recording: Capture detailed logs of injected chaos and system responses for further analysis and debugging.
- Visualization Tools: Utilize built-in dashboards and integrations with external tools to visualize test results and gain insights.
Additional Features:
- Docker and Kubernetes Integration: Seamless integration with Docker and Kubernetes environments for easy deployment and management.
- Scripting and Automation: Extend ToxiProxy capabilities through scripting and automation for complex testing scenarios.
- Open-source and Community-driven: Actively developed and supported by a vibrant open-source community.
Benefits of using ToxiProxy:
- Proactive resilience testing: Identify and address vulnerabilities before they occur in production environments.
- Improved fault tolerance: Develop systems that can gracefully handle various network issues and unexpected events.
- Enhanced confidence and reliability: Ensure your systems deliver consistent performance even under challenging conditions.
Whether you’re building robust microservices, testing critical infrastructure, or simply curious about simulating real-world network chaos, ToxiProxy offers a valuable toolset for pushing your systems to their limits and ensuring their resilience.
How ToxiProxy works and Architecture?
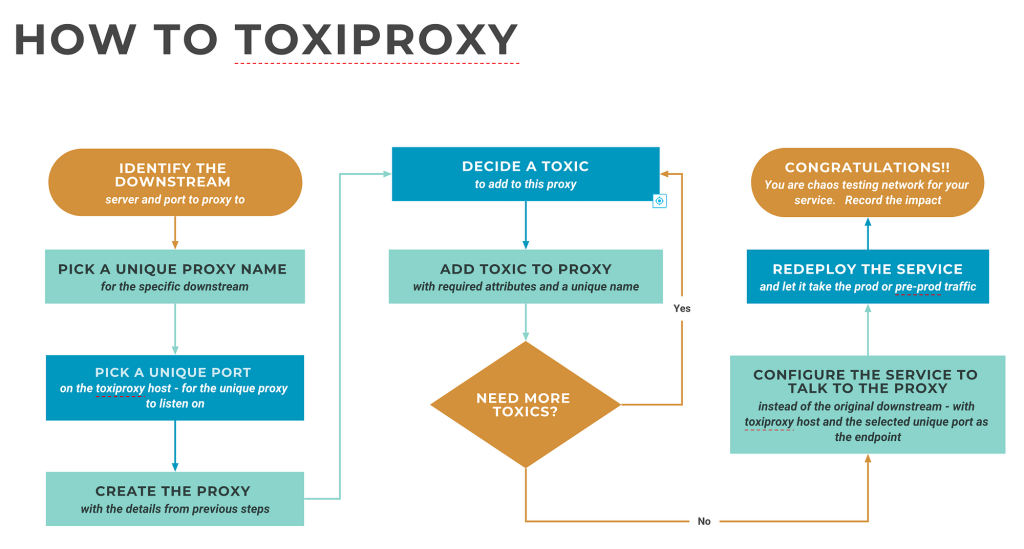
ToxiProxy’s magic lies in its flexible and distributed architecture, designed to inject controlled chaos without impacting your production environment. Let’s explore the key components:
Client-side:
- ToxiProxy client library: Integrated into your application or testing framework, it communicates with the ToxiProxy server to define and activate chaos experiments.
- Proxy configuration: Specifies the desired chaos types, target paths, and injection parameters for each experiment.
Server-side:
- ToxiProxy server: Runs as a standalone process or container (e.g., Docker), listening for client connections and managing chaos injections.
- Proxy instances: Spawned dynamically per experiment, intercepting traffic based on the target configuration.
- Chaos injectors: Built-in modules implementing various chaos types like latency, errors, and data manipulation.
- Metrics and logging: Gather data on injected chaos and system responses for real-time monitoring and analysis.
Core Functionality:
- Client sends instructions: The client library transmits the experiment configuration to the ToxiProxy server.
- Server spawns a proxy: Based on the target, the server launches a dedicated proxy instance to handle the specific traffic.
- Proxy intercepts traffic: The proxy acts as a man-in-the-middle, capturing inbound and outbound requests and responses.
- Chaos injection: Relevant injectors within the proxy modify the intercepted traffic according to the experiment configuration.
- Modified traffic forwarded: The altered requests and responses are forwarded to the actual backend service or client.
- Metrics and logging: The server and proxy gather data on injected chaos and system behavior for analysis.
Key benefits of this architecture:
- Scalability: Dynamically spawns proxies based on demand, handling even large traffic volumes.
- Isolation: Experiments are confined to specific proxies, protecting production environments from unintended chaos.
- Flexibility: Supports various chaos types and allows fine-grained targeting for precise testing.
- Observability: Provides metrics and logs for monitoring experiments and analyzing system behavior.
Notes:
- ToxiProxy integrates seamlessly with Docker and Kubernetes for easy deployment and management.
- Its open-source nature allows for customization and extension through scripting and plugins.
ToxiProxy’s architecture empowers you to inject controlled chaos in a predictable and isolated manner, uncovering potential weaknesses and building robust systems that thrive under pressure.
How to Install ToxiProxy it?
Here’s a guide on installing ToxiProxy for different environments:
1. Standalone Installation:
- Download: Grab the latest release from the GitHub repository: https://github.com/Shopify/toxiproxy/releases
- Extract: Unzip the downloaded file to your desired location.
- Run: Execute the
toxiproxy-serverbinary from the extracted directory.
2. Docker Installation:
- Pull the image:
Bash
docker pull shopify/toxiproxy
- Run the container:
Bash
docker run -p 8474:8474 shopify/toxiproxy
3. Kubernetes Installation:
- Use a Helm chart:
Bash
helm repo add toxiproxy https://shopify.github.io/toxiproxy
helm repo update
helm install toxiproxy toxiproxy/toxiproxy
4. Using a Binary Package (if available):
- OS-specific packages: Check your operating system’s package manager (e.g.,
apt,yum) for ToxiProxy packages and install using standard commands.
Once installed, access the ToxiProxy UI:
- Point your browser to
http://localhost:8474(or the configured host and port). - Start defining and running your chaos experiments!
Notes:
- Client libraries: Install the appropriate client library for your programming language to interact with ToxiProxy from your applications or tests.
- Configuration: Customize ToxiProxy behavior using configuration files or environment variables.
Basic Tutorials of ToxiProxy: Getting Started

Welcome to the exciting realm of controlled chaos with ToxiProxy! These tutorials will guide you through basic injections to test your system’s resilience:
1. Simulating Network Latency:
a. Target Selection:
Open the ToxiProxy UI and choose the “Add Proxy” button.
- Name: Provide a name for your experiment (e.g., “Latency Test”).
- Upstream URL: Enter the URL of the service you want to inject latency on.
b. Injecting Latency:
Click the “Chaos” tab and choose “Latency” from the dropdown menu.
- Delay: Set the desired latency delay in milliseconds (e.g., 50ms).
- Percentage: Define the percentage of requests affected by the latency injection (e.g., 100% for all requests).
c. Start & Observe:
Click the “Start” button for your proxy. Monitor your service’s behavior and response times under the induced latency.
d. Clean Up:
When finished, click “Stop” for your proxy. You can delete the proxy entirely for clean slate.
2. Introducing Network Errors:
a. Target and Chaos Selection:
Repeat steps from the previous tutorial for setting up a proxy targeting your desired service.
- Chaos Tab: Navigate to the “Chaos” tab and choose “Error” from the dropdown menu.
b. Error Injection:
- Error Type: Select the desired error type (e.g., “404 Not Found”, “500 Internal Server Error”).
- Percentage: Define the percentage of requests triggering the error injection.
c. Start & Observe:
Start the proxy and observe your service’s response to the injected errors. Analyze error handling mechanisms and potential application behavior.
d. Clean Up:
Stop and delete the proxy as needed.
3. Modifying Request/Response Content:
a. Targeting and Chaos Selection:
Follow steps from the first tutorial to set up a proxy targeting your service.
- Chaos Tab: Navigate to the “Chaos” tab and choose “Transform” from the dropdown menu.
b. Content Manipulation:
- Request or Response: Choose whether to modify the request or response body content.
- Matching: Define matching patterns for specific sections of the content you want to modify (e.g., regular expressions).
- Replacement: Specify the replacement text or data for the matched content.
c. Start & Observe:
Start the proxy and analyze how your service reacts to the modified request/response data.
d. Clean Up:
Stop and delete the proxy as needed.
Bonus Tips:
- Explore various chaos types offered by ToxiProxy, such as packet loss, bandwidth throttling, and service disconnections.
- Combine different chaos injections for more complex testing scenarios.
- Leverage client libraries to integrate ToxiProxy directly into your applications or test frameworks.
Always remember, start with simple experiments in non-critical environments before introducing chaos to production systems. Have fun injecting controlled chaos and building resilient systems with ToxiProxy!
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

