What is Tripwire Enterprise?

Tripwire Enterprise is a leading solution for IT configuration control, helping businesses achieve robust security and compliance postures. It’s packed with features like:
- File Integrity Monitoring (FIM): Detects unauthorized changes to critical system files, protecting against malware and security breaches.
- Security Configuration Management (SCM): Enforces baseline configurations for your systems, ensuring they adhere to security best practices and internal policies.
- Vulnerability Management: Identifies and prioritizes vulnerabilities across your IT infrastructure, allowing you to patch them before attackers exploit them.
- Compliance Automation: Streamlines compliance reporting for various regulations like PCI, SOX, HIPAA, and more.
- Continuous Threat Detection: Provides real-time insights into suspicious activity and potential threats, minimizing your attack surface.
In short, Tripwire Enterprise delivers an all-in-one platform for:
- Proactive security: Identifying and mitigating risks before they cause damage.
- Continuous compliance: Maintaining adherence to regulations and internal policies.
- Automated workflow: Reducing manual tasks and streamlining security operations.
- Deep system visibility: Gaining comprehensive understanding of your IT environment.
Top 10 use cases of Tripwire Enterprise?
Top 10 Use Cases of Tripwire Enterprise:
- Securing critical infrastructure: Protect servers, databases, and applications from unauthorized changes and vulnerabilities.
- Meeting compliance requirements: Achieve and maintain compliance with PCI, SOX, HIPAA, FISMA, and other regulations.
- Enforcing security policies: Ensure consistent security configurations across your IT environment.
- Detecting and responding to threats: Identify suspicious activity and potential security incidents quickly.
- Patching vulnerabilities: Prioritize and efficiently patch vulnerabilities before they can be exploited.
- Hardening systems: Configure systems to be more resistant to attacks.
- Investigating security incidents: Analyze logs and evidence to understand the root cause of security incidents.
- Improving security awareness: Provide training and reporting to users to raise awareness of security risks.
- Streamlining security operations: Automate tasks and workflows to improve efficiency and reduce costs.
- Demonstrating security posture: Provide comprehensive reports and evidence to auditors and stakeholders.
Tripwire Enterprise offers a powerful set of tools that can be customized to address the specific needs of your organization. Whether you’re a small business or a large enterprise, Tripwire can help you improve your security posture, meet compliance requirements, and reduce your risk of cyberattacks.
What are the feature of Tripwire Enterprise?
Tripwire Enterprise boasts a comprehensive suite of features, but to personalize my response to your specific needs, could you tell me what aspects of its functionality you’re most interested in? For example, would you like to know about:
1. Core functionalities:
- File Integrity Monitoring (FIM): Deeply scan and monitor critical system files for unauthorized changes, alerting you to potential threats.
- Security Configuration Management (SCM): Enforce baseline configurations across your systems, ensuring they adhere to best practices and internal policies.
- Vulnerability Management: Identify and prioritize vulnerabilities in your IT infrastructure, mitigating them before attackers exploit them.
2. Advanced features:
- Continuous Threat Detection and Response: Leverage real-time intelligence and analytics to detect suspicious activity and respond proactively to emerging threats.
- Compliance Automation: Streamline compliance reporting for various regulations like PCI, SOX, HIPAA, and more, reducing manual effort.
- Privileged User Management: Monitor and control privileged user activity, minimizing the risk of insider threats.
3. Specific capabilities:
- Log Management and Correlation: Aggregate and analyze logs from various sources to gain deeper insights into system activity and potential threats.
- Endpoint Security: Extend Tripwire’s protection to endpoints to secure laptops, desktops, and mobile devices.
- Cloud Security: Integrate with cloud platforms to monitor and secure cloud-based workloads and resources.
4. Integration and extensibility:
- Integration with existing security tools: Tripwire seamlessly integrates with various SIEM and SOAR solutions to enhance your overall security posture.
- Customizable workflows and reporting: Tailor Tripwire to your specific needs with customizable workflows and reports.
- API access: Extend Tripwire’s capabilities with its open API for custom integrations and automation.
By understanding your specific interests, I can provide you with a more targeted and relevant explanation of Tripwire Enterprise’s features, tailoring my information to your security goals and challenges.
How Tripwire Enterprise works and Architecture?
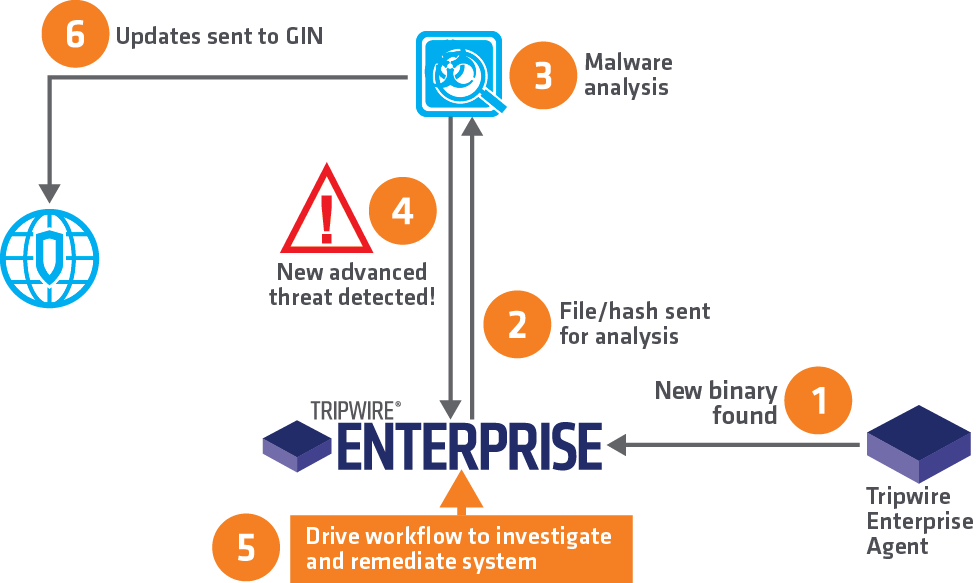
Tripwire Enterprise operates via a distributed architecture designed for scalability and real-time monitoring. Following is a breakdown of its key components:
1. Agents:
- Installed on endpoints (servers, desktops, etc.), continuously monitor files, configurations, and registry settings.
- Send changes and potential threats to the central server in real-time.
- Can be passive (only report) or active (enforce baseline configurations).
2. Central Server:
- Acts as the brain of the operation, receiving data from agents.
- Analyzes data for discrepancies, vulnerabilities, and suspicious activity.
- Generates alerts and reports based on defined policies and rules.
- Provides a web-based interface for managing the system and reviewing security insights.
3. Databases:
- Store configuration baselines, security policies, vulnerabilities, and historical data.
- Different databases manage specific aspects, like file attributes, configuration settings, and vulnerability information.
4. Integrators:
- Connect Tripwire Enterprise to other security tools like SIEM, SOAR, and vulnerability scanners.
- Enable automated workflows and exchange of security data for a unified security posture.
5. Reporting and Dashboards:
- Visualize security posture through customizable dashboards and reports.
- Track trends, verify areas of concern, and demonstrate compliance with regulations.
Work Flow:
- Agents continuously monitor systems and compare them to baselines.
- Any changes or anomalies are sent to the central server in real-time.
- The server analyzes the data and triggers alerts based on pre-defined rules and policies.
- Security analysts investigate alerts and take appropriate actions, like remediation or further investigation.
- Reports and dashboards provide insights into overall security posture and compliance status.
Benefits of this Architecture:
- Scalability: Easily add more agents to monitor larger infrastructures.
- Real-time monitoring: Detect threats and changes immediately for faster response.
- Centralized management: Simplify administration and policy enforcement from a single platform.
- Integrations: Enhance security by combining Tripwire with other tools.
- Visibility and reporting: Gain insights into your security posture and demonstrate compliance.
Tripwire Enterprise offers a robust and flexible architecture that adapts to various security needs. Whether you’re a small business or a large enterprise, its functionality can help you maintain a secure IT environment and mitigate security risks effectively.
How to Install Tripwire Enterprise it?
Installing Tripwire Enterprise involves specific steps depending on your environment and desired deployment method. To guide you efficiently, I need some details:
1. Choose your deployment method:
- Software Appliance: Easiest option for most environments. Download the appliance ISO and follow the on-screen installation wizard.
- Manual Installation: For advanced users or specific deployment needs. Requires manual configuration of server components and databases.
- Cloud Deployment: Available on AWS Marketplace and Azure Marketplace for cloud-based infrastructure.
2. Prepare your environment:
- Hardware: Ensure sufficient resources (CPU, RAM, storage) are available for the server and agents.
- Software: Verify compatibility with your operating system and any required pre-installed software.
- Networking: Configure firewall rules and network access for communication between server and agents.
3. Follow the installation guide:
- Download the relevant documentation based on your chosen deployment method.
- Each guide provides detailed instructions for each step of the installation process.
- You’ll configure the server, databases, agents, and security policies.
Tip: Before installation, consider consulting with Tripwire Support or a qualified IT professional if you need assistance or have specific requirements.
Basic Tutorials of Tripwire Enterprise: Getting Started

While offering specific commands and menus is difficult due to customization options, I can provide a step-by-step process for common basic tasks in Tripwire Enterprise, adapting them to your specific environment:
1. Installing Tripwire Enterprise:
- 1.1 Choose installation method:
- Agent-based: Download and install agents on each system. Follow platform-specific instructions.
- Virtual Appliance: Download and deploy the pre-configured VM image.
- Cloud Deployment: Follow vendor cloud platform instructions for Tripwire Enterprise deployment.
- 1.2 License Activation:
- Enter your license key in the web console or relevant installer prompt.
- 1.3 Verify Installation:
- Confirm successful installation and agent connectivity in the web console.
2. Basic Configuration:
- 2.1 Policy Management:
- Open the Policy Editor.
- Create a new policy:
- Define a name and description.
- Select “File Integrity Monitoring” (FIM) as the main module.
- Add files/directories to monitor:
- Use wildcards for broader coverage.
- Exclude temporary or irrelevant directories.
- Save the policy.
- 2.2 User Accounts:
- Create user accounts and assign roles:
- Admin: Full access to configuration and reports.
- User: View reports and initiate basic tasks.
- Create user accounts and assign roles:
- 2.3 Scheduled Scans:
- Configure automated scans:
- Define scan frequency and timing.
- Assign target systems and policies.
- Choose report generation and email notification options.
- Configure automated scans:
3. Basic Usage:
- 3.1 Manual Scan:
- Select target systems and policies.
- Initiate a scan.
- Monitor progress and view real-time results.
- 3.2 Reviewing Reports:
- Navigate to the Reports tab.
- View recent scan reports for different systems and policies.
- Analyze identified changes and potential vulnerabilities.
- Prioritize issues based on severity and impact.
- 3.3 Basic Remediation:
- Investigate reported changes, verifying suspicious activity.
- Revert unauthorized changes using Tripwire rollback capabilities.
- Update vulnerable software or patch system configurations.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

