What is Venafi?

Venafi is a cybersecurity company that specializes in protecting and securing cryptographic keys and digital certificates used by organizations to secure their data, applications, and communication. The company provides solutions that help organizations manage, automate, and secure their cryptographic assets, including SSL/TLS certificates, SSH keys, code signing certificates, and more. Venafi’s products and services are designed to address the challenges associated with the increasing complexity and volume of cryptographic assets in modern IT environments.
Overall, Venafi’s solutions play a critical role in helping organizations maintain the confidentiality, integrity, and availability of their digital assets by effectively managing and securing their cryptographic keys and certificates. This is essential in today’s complex and rapidly evolving cybersecurity landscape.
Top 10 use cases of Venafi:
Here are the top 10 use cases for Venafi’s solutions:
- Certificate Lifecycle Management: Venafi helps organizations manage the entire lifecycle of digital certificates, from issuance and renewal to revocation and decommissioning, ensuring that certificates are always up-to-date and compliant with security policies.
- Automated Certificate Discovery: Venafi can automatically discover and inventory all digital certificates within an organization’s network, including those that may have been forgotten or left unmanaged.
- Private Key Protection: Protecting the private keys associated with digital certificates is crucial. Venafi helps secure and manage these keys to prevent unauthorized access or misuse.
- SSL/TLS Certificate Management: Venafi assists in the management of SSL/TLS certificates, ensuring that websites and applications are always encrypted and secure. This is essential for maintaining trust with customers and partners.
- SSH Key Management: Secure Shell (SSH) keys are used for secure remote access to servers and systems. Venafi helps manage SSH keys to prevent unauthorized access and maintain security.
- Code Signing Certificate Management: Organizations often use code signing certificates to verify the authenticity and integrity of software. Venafi helps manage these certificates to prevent malicious code from being distributed.
- Compliance and Policy Enforcement: Venafi enables organizations to enforce security policies and compliance requirements related to digital certificates, ensuring that certificates adhere to industry standards and internal guidelines.
- Security Analytics: Venafi’s solutions can provide insights and analytics into the usage and behavior of cryptographic assets, helping organizations identify potential security threats and vulnerabilities.
- Cloud and DevOps Integration: As organizations adopt cloud and DevOps practices, Venafi can integrate with these environments to ensure that cryptographic assets are properly managed and secured in dynamic, automated infrastructure.
- Threat Detection and Response: Venafi can detect abnormal certificate activity that may indicate a security threat, allowing organizations to respond quickly to potential breaches or unauthorized certificate use.
What are the feature of Venafi?
Venafi offers a range of features and capabilities designed to help organizations effectively manage and secure their cryptographic keys and digital certificates. While the specific features may vary depending on the product or solution within the Venafi portfolio, here are some common features and functionalities associated with Venafi’s offerings:
- Certificate Lifecycle Management: Venafi provides tools for the complete management of certificates throughout their lifecycle, from issuance and deployment to renewal and eventual retirement.
- Certificate Discovery: Venafi can automatically discover all digital certificates across an organization’s network, including certificates issued by both public and private certificate authorities.
- Policy Enforcement: Venafi allows organizations to define and enforce security policies related to certificates, ensuring compliance with industry standards and internal guidelines.
- Key Protection: Venafi helps protect private keys associated with certificates, safeguarding them from unauthorized access and potential misuse.
- Automated Renewal: Venafi can automate the renewal process for certificates, ensuring that certificates are always up-to-date and preventing unexpected expirations.
- Inventory and Reporting: Venafi provides inventory and reporting capabilities to track and monitor the status and usage of certificates, helping organizations maintain visibility and control.
- Integration with Certificate Authorities (CAs): Venafi can integrate with both public and private CAs to streamline the certificate issuance and management process.
- Security Analytics: Venafi offers insights and analytics into certificate usage and behavior, helping organizations detect and respond to security threats and anomalies.
- Cloud and DevOps Integration: Venafi is designed to integrate with cloud environments and DevOps pipelines, ensuring that cryptographic assets are managed and secured in these dynamic environments.
- Threat Detection: Venafi can detect unusual certificate activity that may indicate security threats, such as unauthorized certificate issuance or suspicious key usage.
How Venafi works and Architecture?
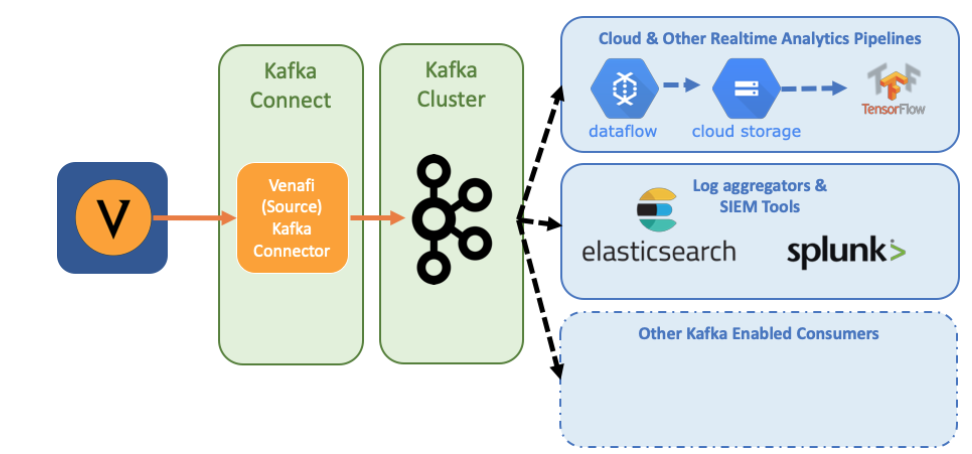
Venafi’s architecture and how it works can vary depending on the specific product or solution being used, but here’s a general overview of how Venafi typically operates:
- Agent-Based Discovery: Venafi often deploys agents or collectors across an organization’s network to automatically discover and inventory digital certificates. These agents periodically scan the network and collect certificate information.
- Policy Enforcement: Organizations define security policies within the Venafi platform, specifying rules and criteria that certificates must meet to remain compliant. Venafi enforces these policies and alerts administrators when violations occur.
- Certificate Management: Venafi centralizes the management of certificates, allowing administrators to request, issue, renew, and revoke certificates as needed. This includes integration with certificate authorities for automated certificate issuance and renewal.
- Key Protection: Venafi safeguards private keys associated with certificates, encrypting and storing them securely to prevent unauthorized access.
- Monitoring and Analytics: Venafi continuously monitors certificate usage and behavior, providing insights and alerts for potential security threats or policy violations.
- Reporting and Compliance: Venafi generates reports and audit trails to demonstrate compliance with industry regulations and internal security policies.
- Integration: Venafi integrates with various systems and tools within an organization’s IT infrastructure, including CA systems, cloud platforms, DevOps pipelines, and security information and event management (SIEM) systems.
- Alerting and Response: Venafi can trigger alerts and responses when it detects suspicious or non-compliant certificate activity, allowing organizations to take action promptly.
Overall, Venafi’s architecture is designed to provide centralized visibility, control, and security for an organization’s cryptographic assets, helping to mitigate risks associated with certificates and keys while ensuring compliance with security policies and industry standards. Specific implementations may vary depending on an organization’s needs and the Venafi products in use.
How to Install Venafi?
To install Venafi, you can follow these steps:
- Download the Venafi installation package. You can download the Venafi installation package from the Venafi customer portal.
- Prepare your environment for the Venafi installation. The following requirements must be met:
- A supported operating system
- A supported database
- A supported web server
- A supported load balancer (optional)
- Install the Venafi Trust Protection Platform (TPP).
- Run the Venafi installation package.
- Follow the on-screen instructions to fulfill the installation.
- Configure the Venafi TPP.
- Open the Venafi Configuration Console.
- Follow the on-screen instructions to configure the Venafi TPP.
Once you have installed and configured the Venafi TPP, you can start using it to manage your machine identities.
Some additional tips for installing Venafi:
- Make sure that your environment meets the Venafi system requirements.
- Close all other applications before installing Venafi.
- If you are having trouble installing Venafi, contact Venafi support for assistance.
Some additional tips for using Venafi:
- Venafi supports a variety of machine identity types, including certificates, SSH keys, and API keys.
- Venafi can be used to manage machine identities for a variety of platforms, including on-premises servers, cloud servers, and IoT devices.
- Venafi can be integrated with a variety of third-party products, such as CI/CD tools and orchestration platforms.
Basic Tutorials of Venafi: Getting Started

The following steps are the basic Tutorials of Venafi:
Venafi is a leading provider of machine identity management solutions. It helps organizations automate, manage, and protect their machine identities, including digital certificates, TLS keys, SSH keys, and API keys.
Venafi offers a variety of basic tutorials to help you get started with its solutions. These tutorials cover a wide range of topics, including:
- How to create and manage digital certificates
- How to manage SSH keys
- How to manage API keys
- How to integrate Venafi with other security solutions
To access Venafi’s basic tutorials, follow these steps:
- Go to the Venafi website: https://venafi.com/
- Click on the Support tab
- Click on the Tutorials link
- Under the Basic Tutorials section, click on the topic you want to learn about
How to Create and Manage Digital Certificates
To create and manage digital certificates using Venafi, follow these steps:
- Go to the Venafi Certificates page
- Click on the New Certificate button
- Select the type of certificate you want to create
- Enter the required information, such as the certificate subject, common name, and validity period
- Click on the Create Certificate button
To manage your digital certificates, you can use the Venafi Certificates page. This page allows you to view all of your certificates, renew certificates, and revoke certificates.
How to Manage SSH Keys
To manage SSH keys using Venafi, follow these steps:
- Go to the Venafi SSH Keys page
- Click on the New SSH Key button
- Enter the required information, such as the SSH key name and type
- Click on the Create SSH Key button
To manage your SSH keys, you can use the Venafi SSH Keys page. This page allows you to view all of your SSH keys, rotate keys, and disable keys.
How to Manage API Keys
To manage API keys using Venafi, follow these steps:
- Go to the Venafi API Keys page
- Click on the New API Key button
- Enter the required information, such as the API key name and description
- Click on the Create API Key button
To manage your API keys, you can use the Venafi API Keys page. This page allows you to view all of your API keys, rotate keys, and revoke keys.
How to Integrate Venafi with Other Security Solutions
Venafi can be integrated with a variety of other security solutions, such as firewalls, intrusion detection systems, and security information and event management (SIEM) systems.
To integrate Venafi with another security solution, you will need to consult the documentation for both solutions.
Example Step-by-step Basic Tutorial: How to Create and Manage Digital Certificates
To create a digital certificate using Venafi, follow these steps:
- Go to the Venafi Certificates page
- Click on the New Certificate button
- Choose the type of certificate you want to create. For example, to create a web server certificate, select the Web Server Certificate option.
- Enter the required information, such as the certificate subject, common name, and validity period.
- Click on the Create Certificate button.
To view your digital certificates, go to the Venafi Certificates page.
To renew a digital certificate, go to the Venafi Certificates page, click on the certificate you want to renew, and then click on the Renew Certificate button.
To revoke a digital certificate, go to the Venafi Certificates page, click on the certificate you want to revoke, and then click on the Revoke Certificate button.
Venafi offers a variety of basic tutorials to help you get started with its solutions. These tutorials cover a wide range of topics, including how to create and manage digital certificates, SSH keys, and API keys.
- Why Can’t I Make Create A New Folder on External Drive on Mac – Solved - April 28, 2024
- Tips on How to Become a DevOps Engineer - April 28, 2024
- Computer Programming Education Requirements – What You Need to Know - April 28, 2024

