What is Veracode?

Veracode is a leading application security (AppSec) platform that helps organizations identify and remediate vulnerabilities in their software throughout the development lifecycle. By integrating seamlessly with DevOps workflows, Veracode empowers developers and security teams to build secure applications from the ground up.
Top 10 use cases of Veracode?
Top 10 Use Cases of Veracode:
- Static Application Security Testing (SAST): Scan source code for vulnerabilities like SQL injection and cross-site scripting (XSS) early in the development process.
- Dynamic Application Security Testing (DAST): Simulate attacks to uncover runtime vulnerabilities in web applications and APIs.
- Software Composition Analysis (SCA): Identify and manage security risks within open-source and third-party software dependencies.
- Interactive Application Security Testing (IAST): Monitor deployed applications for real-time attack attempts and suspicious activity.
- Penetration Testing: Engage expert security professionals to manually test applications for complex vulnerabilities.
- Compliance Management: Ensure adherence to industry security standards like PCI DSS, HIPAA, and GDPR.
- DevSecOps Integration: Integrate security scanning tools into development pipelines for continuous code improvement.
- Security Education and Training: Empower developers and security teams with knowledge and best practices for building secure software.
- Threat Intelligence: Provide actionable insights into the latest security threats and vulnerabilities to proactively protect applications.
- Application Security Risk Management: Gain centralized visibility and reporting on application security risks across the organization.
Benefits of Using Veracode:
- Reduced Time to Market: Find and fix vulnerabilities early in the development process, speeding up software delivery.
- Improved Software Quality: Build more secure and reliable applications, boosting user trust and confidence.
- Reduced Security Costs: Proactive vulnerability detection can prevent costly data breaches and reputation damage.
- Streamlined Workflows: Integrate seamlessly with existing development tools and practices for efficient security analysis.
- Compliance Assurance: Demonstrate compliance with industry regulations and standards.
If you’re looking to:
- Secure your software
- Protect your data
- Build trust with your users
Veracode can be a valuable partner in your cybersecurity journey.
What are the feature of Veracode?
Here are some of the key features of Veracode:
Testing Approaches:
- Static Application Security Testing (SAST): Analyzes source code to identify vulnerabilities like SQL injection, cross-site scripting (XSS), and buffer overflows.
- Dynamic Application Security Testing (DAST): Simulates attacks against running applications to uncover vulnerabilities in web applications and APIs.
- Software Composition Analysis (SCA): Scans open-source and third-party libraries for known vulnerabilities and license compliance issues.
- Interactive Application Security Testing (IAST): Monitors application behavior during testing to provide more accurate results.
- Penetration Testing: Offers manual testing by security experts for in-depth vulnerability assessment.
Integration and Automation:
- DevSecOps Integration: Integrates seamlessly with popular development tools and CI/CD pipelines for continuous security testing and feedback.
- API Integration: Supports integration with third-party tools for ticketing systems, issue trackers, and governance platforms.
- Automation: Automates vulnerability scanning and reporting processes for efficient workflows.
Vulnerability Management:
- Centralized Vulnerability Tracking: Provides a centralized dashboard to track and manage vulnerabilities across applications.
- Prioritization and Remediation Guidance: Helps prioritize vulnerabilities based on their severity and provides clear remediation guidance for developers.
- Remediation Tracking: Monitors remediation progress and ensures vulnerabilities are fixed effectively.
Compliance:
- Compliance Reporting: Generates reports to demonstrate compliance with industry standards like PCI DSS, HIPAA, and GDPR.
- Compliance Frameworks: Supports various compliance frameworks to streamline compliance processes.
Additional Features:
- Threat Intelligence: Leverages threat intelligence to identify and prioritize emerging threats.
- Security Education and Training: Offers security training resources for developers and security teams.
- Application Security Risk Management: Provides a holistic view of application security risks across the organization.
- Customizable Dashboards: Allows users to create custom dashboards and reports to visualize security data in a way that suits their needs.
- Scalability: Can be scaled to meet the needs of organizations of all sizes.
Veracode continuously updates its features and capabilities to address evolving security threats and industry requirements.
How Veracode works and Architecture?
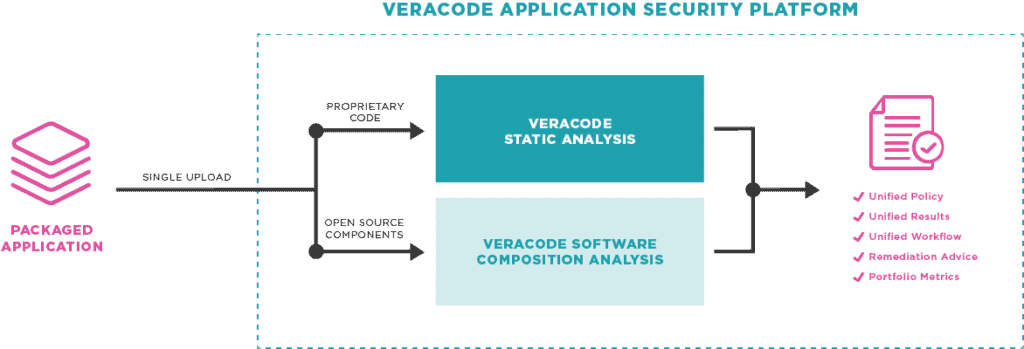
Veracode’s architecture revolves around a cloud-based platform delivering various AppSec services. Here’s a breakdown of how it works:
Components:
- Veracode Platform: The central hub that orchestrates all security analyses and manages data. It includes:
- Scanners: Engines for different analysis types like SAST, DAST, and SCA.
- Database: Stores information on applications, vulnerabilities, and analysis results.
- Workflow Engine: Automates workflows for scanning, reporting, and remediation.
- User Interface: Provides access to tools, reports, and security insights.
- Integrations: Veracode connects seamlessly with various developer tools and platforms like IDEs, CI/CD pipelines, and issue trackers.
- Applications: Organizations upload their software code, web applications, or dependencies for analysis.
- Analysis Tools: Different tools handle specific tasks:
- SAST: Scans source code for vulnerabilities in programming languages like Java, Python, and C++.
- DAST: Simulates real-world attacks on running applications to detect exploitable weaknesses.
- SCA: Analyzes dependencies to identify known vulnerabilities and licensing issues.
- Vulnerability Management: After analysis, vulnerabilities are identified and classified based on severity and risk.
- Veracode offers features like:
- Prioritization: Ranking vulnerabilities based on potential impact and exploitability.
- Remediation guidance: Providing developers with clear steps to fix vulnerabilities.
- Tracking and reporting: Monitoring progress towards resolving vulnerabilities.
- Veracode offers features like:
Benefits of Veracode’s Architecture:
- Cloud-based: Accessible from anywhere with an internet connection and scales easily.
- Integrated: Seamlessly connects with development workflows for efficiency.
- Automated: Automates scans, reporting, and remediation tasks for faster execution.
- Comprehensive: Offers a range of analysis tools and vulnerability management features.
- Secure: Data is encrypted at rest and in transit.
Veracode provides a comprehensive and well-designed architecture for managing application security throughout the development lifecycle.
How to Install Veracode it?
Veracode is a cloud-based platform, so you don’t install it locally like traditional software. Here’s the general process to get started:
- Sign up for a Veracode account:
- Visit the Veracode official website and create a trial or paid account.
- Provide basic information about your organization and contact details.
- Access the Veracode Platform:
- Once your account is created, you’ll receive login credentials.
- Use those credentials to access the Veracode Platform through a web browser.
- Integrate with Development Tools (Optional):
- If you want to integrate Veracode with your development tools or CI/CD pipeline, follow the specific instructions provided by Veracode.
- This involves setting up plugins or integration points for your chosen tools.
- Upload Applications:
- To start scanning your applications, you’ll need to upload them to the Veracode Platform.
- You can upload source code, binaries, or deployable packages, depending on the types of analysis you want to perform.
- Configure Scans:
- Set up the desired security scans for your applications, such as SAST, DAST, or SCA.
- Choose appropriate scanning options and configurations based on your needs and risk tolerance.
- Initiate Scans:
- Once applications and scans are configured, you can initiate the scanning process.
- Veracode will analyze your applications and identify potential vulnerabilities.
- Review Results:
- Access the Veracode dashboard to view scan results, including identified vulnerabilities, their severity, and remediation guidance.
- Prioritize vulnerabilities based on their risk and work on fixing them.
Basic Tutorials of Veracode: Getting Started

Let’s deep dive into beginner-friendly, web application security overview with a DAST scan, here’s a detailed step-by-step basic tutorial to get you started:
1. Create a Free Trial Account:
- Visit the Veracode official website and click on “Free Trial.”
- Fill out the registration form with your basic information and desired plan.
- Verify your email address and follow the onboarding steps to access the Veracode platform.
2. Upload Your Web Application:
- Click on the “Scan” tab in the dashboard.
- Choose the “Scan a URL” option.
- Enter the public URL of your web application (demo or test site).
- Check the application details and press “Start Scan.”
3. Configure the DAST Scan (Dynamic Application Security Testing):
- Choose the “Dynamic Scan” analysis type.
- Adjust any settings if needed:
- Scan Depth: Decide how thoroughly you want Veracode to explore your application.
- Scan Duration: Limit the scan time if required.
- Crawler Paths: Specify specific URLs or pages to focus on.
- You can leave most settings at default for the initial scan.
4. Initiate the Scan and Monitor Progress:
- Click “Start Scan” to begin the DAST analysis.
- Monitor the progress in the dashboard. This might take a few minutes depending on your application size.
- You can access additional information like crawl progress and resource utilization during the scan.
5. Review the DAST Results:
- Once the scan finishes, access the “Results” tab.
- You’ll see a summary of identified vulnerabilities, categorized by severity and potential impact.
- Click on each vulnerability to learn more about its details, exploitability, and recommended remediation steps.
- Download the full report for further analysis and sharing with your development team.
6. Explore Remediation Guidance:
- Each vulnerability report will provide clear steps to fix it.
- Veracode may offer suggestions like code changes, configuration adjustments, or security best practices.
7. Next Steps:
- Implement the remediation steps for identified vulnerabilities in your web application.
- You can re-scan your application after fixes to verify successful remediation.
- Explore other Veracode features like SAST for deeper code analysis, SCA for third-party library checks, or integrate with your development tools for continuous security.
This is just a basic tutorial. Feel free to experiment with different scan settings, explore additional features, and ask any questions you encounter along the way.
- Mutual of Omaha: Selection and Interview process, Questions/Answers - April 15, 2024
- AES: Selection and Interview process, Questions/Answers - April 15, 2024
- Amphenol: Selection and Interview process, Questions/Answers - April 15, 2024

